For teams building secure software, understanding the difference between penetration testing vs vulnerability scanning, or a vulnerability scan vs penetration test, is more than a technical nuance. It’s about choosing the right method at the right time to protect your applications and infrastructure. While these terms are often used interchangeably, they serve different purposes. Vulnerability scanning automates the detection of known flaws in code, infrastructure, and configurations. Penetration testing, on the other hand, simulates real-world attacks to reveal how those flaws could be exploited.
Because of this distinction, knowing when to use each technique helps teams prioritize risks, strengthen the software supply chain, and stay compliant with regulations like DORA and NIS2.
This guide walks through both practices, highlights their differences, and shows how combining them can sharpen your DevSecOps strategy.
What is Vulnerability Scanning?
Vulnerability scanning, also called a vulnerability scan, is an automated process that checks your software, systems, and infrastructure for known security issues. It compares your configurations and dependencies against databases of documented flaws, such as the Common Vulnerabilities and Exposures (CVEs) list.
Key Characteristics of Vulnerability Scanning
- Automated Detection: Scans run on predefined rules to flag misconfigurations, outdated packages, and vulnerable libraries.
- Speed & Scale: Ideal for frequent checks across large environments or integrated into CI/CD pipelines.
- Limited Context: Scanners identify issues but don’t assess whether they’re exploitable in your actual environment.
Take the case of a DevOps team that adds a Software Composition Analysis (SCA) tool to its CI pipeline. Every time someone opens a pull request, the tool scans for outdated or risky dependencies. It flags known CVEs but can’t confirm whether those flaws are reachable or exploitable during runtime.
Vulnerability scanning gives teams early visibility into known risks. However, it can create alert fatigue if used alone. To solve that, modern solutions—like those from Xygeni—prioritize vulnerabilities based on exploitability and reachability, helping teams focus on what truly matters.
What is Penetration Testing?
Penetration testing, often referred to as a penetration test, is a manual, simulated cyberattack that reveals how vulnerabilities can be exploited in real-world conditions. Unlike automated scanning, it mimics attacker behavior to breach systems, escalate privileges, and access sensitive data.
Types of Penetration Tests
- Black-box: The tester has no prior knowledge of the system—simulating an external attacker.
- White-box: The tester has full access to code, architecture, and infrastructure—ideal for detailed analysis.
- Grey-box: The tester has partial knowledge—commonly used in secure SDLC environments to balance realism and efficiency.
Key Characteristics of Penetration Test
- Manual Exploration: Security professionals (or red teams) simulate real attack paths, chaining vulnerabilities and bypassing controls.
- Tactical Depth: Goes beyond individual issues to assess how attackers could pivot and exploit your environment.
- Compliance-Driven: Required by many security standards, including PCI-DSS, DORA, and NIS2.
Before launching a new financial services platform, a company runs a grey-box penetration test. The security team attempts API abuse, privilege escalation, and injection attacks to see if the app’s defenses hold up under realistic threats.
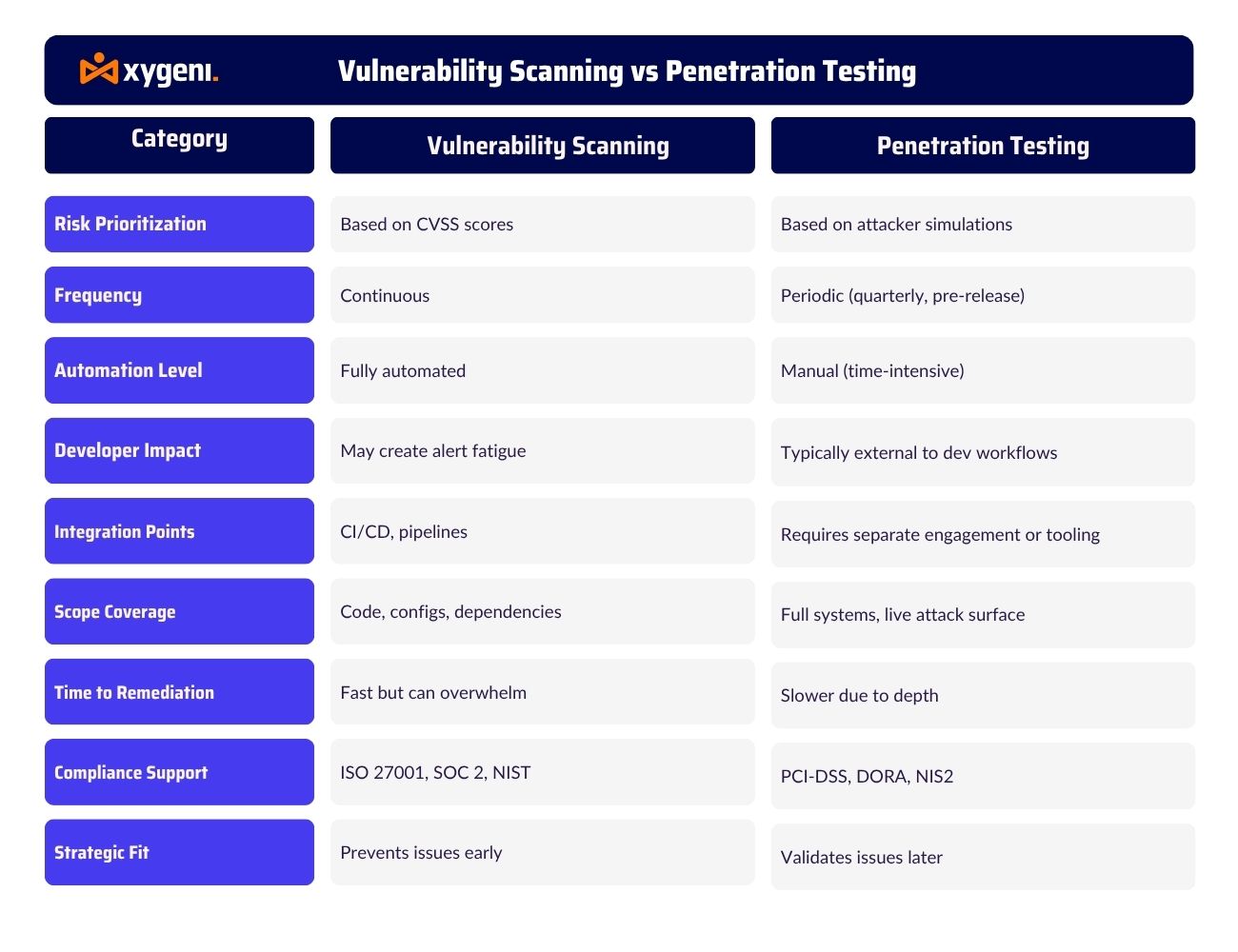
Vulnerability Scanning vs Penetration Testing
While both practices aim to strengthen your security posture, vulnerability scanning vs penetration testing serve very different purposes. Understanding how and when to use each is key to building secure-by-default workflows in modern DevOps environments.
Key Differences of Vulnerability Scan vs Penetration Test at a Glance
- Automated vs. Simulated
Vulnerability scanning runs automatically—typically during builds or overnight pipelines—to identify known flaws. Penetration testing, however, is manual and simulates how an attacker would exploit those flaws in real-world conditions. - Continuous vs. Periodic
You can run vulnerability scans on every commit or pull request using CI/CD integrations like those from Xygeni. In contrast, penetration tests are usually scheduled ahead of major releases, architecture shifts, or compliance milestones. - Depth Matters
A scanner might flag a vulnerable package but can’t tell if that code is reachable. A penetration test goes deeper—it shows whether an attacker can actually exploit the issue to gain access, escalate privileges, or exfiltrate data. - Shift-Left vs. Real-World Simulation
Vulnerability scanning supports shift-left security by empowering developers to catch issues early. Penetration testing provides a reality check later in the lifecycle, validating how well your defenses hold up under pressure.
In short, scanners give you speed and breadth; pen tests give you depth and precision. Together, they paint a full picture of your application’s security posture.
When to Use Penetration Testing vs Vulnerability Scanning in Practice
Knowing when to use vulnerability scanning vs penetration testing is essential for managing risk without slowing down development. Although a vulnerability scan and a penetration test both help secure your software, they serve very different roles.
- Vulnerability scanning provides fast, automated insights into known issues across your codebase, infrastructure, and dependencies.
- Penetration testing offers deep, real-world simulation of how those issues could be chained and exploited by an attacker.
Because they operate at different levels of depth and frequency, choosing between a vulnerability scan vs penetration test isn’t about which one is better—but when to use each in the software lifecycle.
Regular Maintenance: Use Vulnerability Scanning for Continuous Security Hygiene
In DevOps environments, treat vulnerability scanning like a hygiene check. Run it often, automate it, and embed it directly into your CI/CD workflows. This approach keeps your codebase clean and compliant without slowing developers down.
Best used for:
- CI/CD pipelines: Scan every pull request, build, and deployment to catch issues early.
- Scheduled checks: Run daily or weekly to surface outdated packages, insecure configurations, or exposed secrets.
- Compliance audits: Automatically generate proof for ISO 27001, SOC 2, NIST, and other frameworks.
Why it matters: Vulnerability scanning detects known flaws before they hit production. However, to avoid alert fatigue, teams need prioritization. That’s why platforms like Xygeni enhance every vulnerability scan with exploitability scoring (e.g., EPSS), reachability analysis, and context—so engineers fix what matters first.
Critical Milestones: Use Penetration Testing for Deep Validation and Real-World Risk
When the risk is higher—such as just before a launch or after an infrastructure overhaul, penetration testing is the right choice. Unlike scanning, a penetration test actively simulates how attackers could exploit vulnerabilities to breach your system.
Best used for:
- Pre-launch testing: Uncover risks in new apps, APIs, or cloud services before they go live.
- Post-migration assessments: Validate security after moving to microservices, containers, or a new cloud environment.
- Audit cycles: Satisfy mandates like PCI-DSS, DORA, or NIS2, or prepare for red team exercises.
- Incident validation: Confirm that fixes hold up after a breach or critical alert.
Why it matters: Scans show you what’s broken; penetration tests show how attackers can break in. If you’re deciding between a vulnerability scan vs penetration test, consider this: scanning finds issues, but testing proves impact. Both are critical—just at different moments.
Why Penetration Testing and vulnerability Scanning Are Critical for Modern DevSecOps
Modern DevSecOps teams don’t just need to detect issues—they need to understand which ones matter, how they might be exploited, and when to act. That’s why understanding the difference between penetration testing vs vulnerability scanning is more than just terminology—it’s about how you build resilient, secure pipelines.
As we’ve seen:
- A vulnerability scan offers speed, breadth, and automation—perfect for routine hygiene and compliance.
- A penetration test delivers depth, context, and real-world simulation—ideal for high-risk changes or validation events.
Together, they form a balanced Defense in Depth strategy. By clearly defining when to use vulnerability scanning vs penetration testing, DevSecOps teams reduce noise, prioritize effectively, and protect both speed and stability.
NIST’s Perspective: Combine Both for Comprehensive Coverage
The National Institute of Standards and Technology (NIST) clearly outlines how both practices support robust security operations.
- Vulnerability Scanning: NIST defines this as a proactive technique to identify hosts, system attributes, and known vulnerabilities—an essential step in early detection.
- Penetration Testing: According to NIST, this method actively challenges system defenses to simulate real-world exploitation paths. It tests how attackers might move laterally through systems and defeat existing protections.
NIST’s Special Publication 800-115 reinforces the importance of running both—a vulnerability scan vs penetration test isn’t an either/or decision. Instead, the combination ensures early detection and late-stage validation.
ENISA’s View: Embed Testing into Threat-Driven Operations
The European Union Agency for Cybersecurity (ENISA) also recommends using both vulnerability scanning and penetration testing. According to its official implementation guidance:
- Organizations should schedule these activities regularly and after major changes.
- For insider threat detection and mitigation, ENISA advocates integrating both into your threat hunting workflows.
Bottom Line: Use Both to Stay Ahead
If your team only performs a vulnerability scan vs penetration test, you’ll miss critical blind spots. Scanners help you move fast and catch known issues early. Pen tests let you explore deeper—validating whether those issues could be exploited in the wild.
🗒️ To sum up: When used together, penetration testing vs vulnerability scanning isn’t a debate, it’s a blueprint. You reduce noise, boost clarity, and secure your pipeline from code to cloud.
How Xygeni Supercharges Vulnerability Scanning (and Complements Penetration Testing)
Vulnerability scanning is powerful—but only when it’s precise, contextual, and seamlessly integrated into your pipeline. That’s where Xygeni stands out.
Instead of flooding teams with noise, Xygeni focuses on what’s exploitable, reachable, and relevant to your code. As a result, your developers can prioritize faster, fix smarter, and reduce security debt without breaking velocity.
Why Xygeni Is Different
- Exploitability-Aware Scanning
Xygeni enriches every vulnerability scan with EPSS scoring, reachability analysis, and business context—so you don’t waste time on what’s not actually dangerous. - Developer-Centric Workflow
Run scans directly in CI/CD or your IDE. Get real-time feedback where developers already work. - Custom Guardrails
Automatically block critical issues based on your policies—without adding friction. - Actionable Insights, Not Alerts
Xygeni correlates vulnerabilities with source code, configs, and infrastructure to surface meaningful risk—not just CVE lists.
Build Resilient DevSecOps with Xygeni
When you combine penetration testing vs vulnerability scanning strategically, you unlock a powerful dual-layer security model. Xygeni helps you own the first layer—bringing intelligence and automation to your scanning strategy—so you can pair it with targeted pen tests where they matter most.
Ready to see it in action? Book a Demo or try it for Free. Discover how Xygeni helps you secure your entire SDLC, from commit to cloud!