Introduction
Many organizations rely on ISO 27001 to build and maintain secure software development practices. Additionally, Annex A of the standard outlines specific controls designed to strengthen the Secure Development Lifecycle (SDLC). As a result, this article shows how Xygeni helps organizations apply these controls and demonstrate ISO 27001 compliance from an Application Security (AppSec) perspective. Moreover, it maps typical audit evidence to Xygeni’s capabilities, noting where additional tools or processes may be needed.
What Is ISO 27001 in Cybersecurity?
ISO 27001 is the globally recognized standard for information security management systems (ISMS). In this context, it defines best practices and controls that organizations should follow to protect data, systems, and infrastructure against threats. Because of this, it is widely adopted by enterprises pursuing strong ISO 27001 compliance in their software development and IT operations.
A key requirement of ISO 27001 implementation is to integrate security measures throughout the software development process. Therefore, it ensures that security is embedded from the start and maintained across all phases of the secure development lifecycle.
This is especially important in modern DevOps environments, where development speed can sometimes outpace security practices. By contrast, organizations that adopt ISO 27001 Annex A application security requirements ensure a structured, risk-based approach to securing applications, infrastructure, and workflows.
All in all, Annex A of ISO 27001 contains a comprehensive list of controls that directly apply to software development, forming the foundation of a secure development lifecycle and ensuring effective ISO 27001 compliance.
Overview of ISO 27001 Annex A Controls for AppSec
ISO 27001 Annex A application security requirements define specific controls that focus on secure software development and application-level risk mitigation. These controls support ISO 27001 compliance by requiring organizations to embed robust security practices throughout every phase of the secure development lifecycle.
To achieve effective ISO 27001 implementation, organizations must ensure that security is not just a checkbox but an integral part of how software is planned, built, tested, and released. Below is a summary of the most relevant ISO 27001 Annex A controls for application security:
- A.8.25 Secure Development Lifecycle (SDLC): Ensuring all phases of software development embed security practices, from initial design to release.
- A.8.26 Application Security Requirements: Clearly define and embed security requirements within software development processes.
- A.8.27 Secure System Architecture and Engineering: Implementing security by design in the architecture and system engineering practices.
- A.8.28 Secure Coding: Adopting secure coding guidelines and systematically identifying and mitigating insecure coding practices.
- A.8.29 Security Testing and Acceptance: Perform security testing throughout development and before release to find and fix vulnerabilities early.
- A.8.30 Outsourced Development: Oversee and control security risks when working with outsourced teams or third-party developers.
- A.8.31 Separation of Development, Test, and Production: Isolate the different SDLC environments to protect system integrity.
- A.8.32 Secure Coding Guidelines: Develop secure coding standards and ensure the development teams apply them consistently.
- A.8.33 Security in the Software Supply Chain: Manage security risks for third-party software components and dependencies.
- A.8.34 Source Code Access Control: Apply “Least Privilege” to restrict unauthorized change or leak.
- A.8.35 Secure Release of Software: Only tested and secure software versions go to production.
- A.8.36 Information Security During Testing: Protect sensitive data during software testing activities.
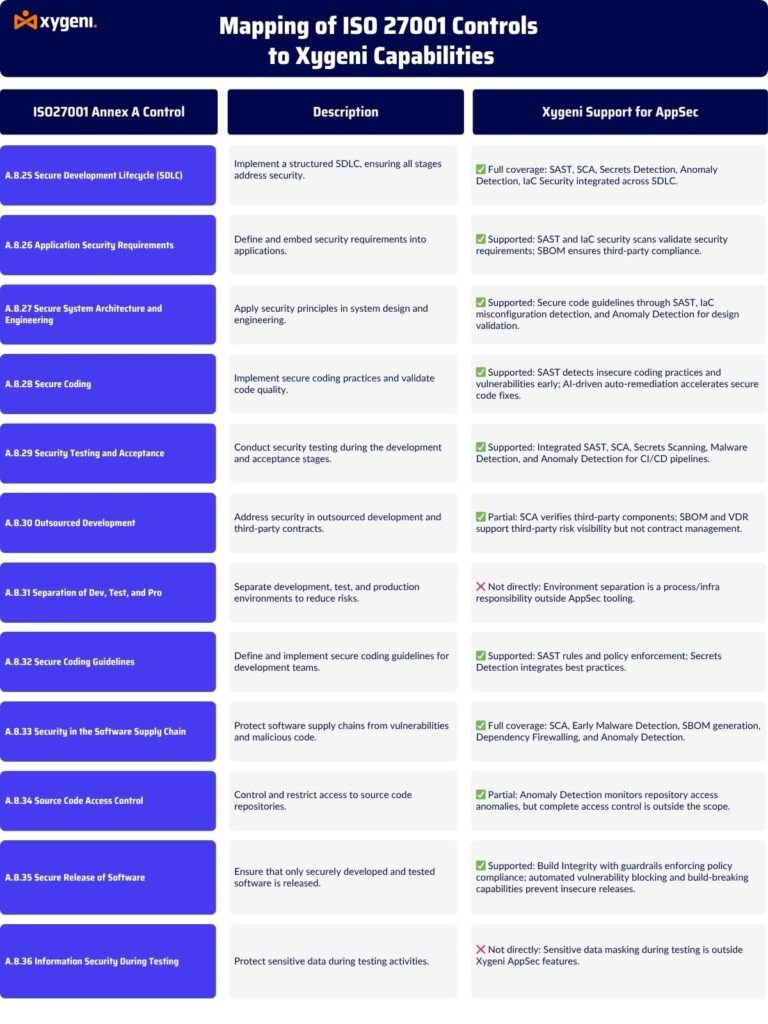
How Xygeni Helps with ISO 27001 Compliance
Xygeni provides an integrated platform that supports organizations in applying and maintaining ISO 27001 controls within their secure development lifecycle. The table below maps each control to relevant Xygeni capabilities:
Typical Audit Evidence vs. Xygeni-Supported Evidence for Application Security
Each capability contributes to both security maturity and audit readiness. Therefore, it helps teams show verifiable evidence of ISO 27001 compliance and control adoption across their software supply chain and CI/CD pipelines.
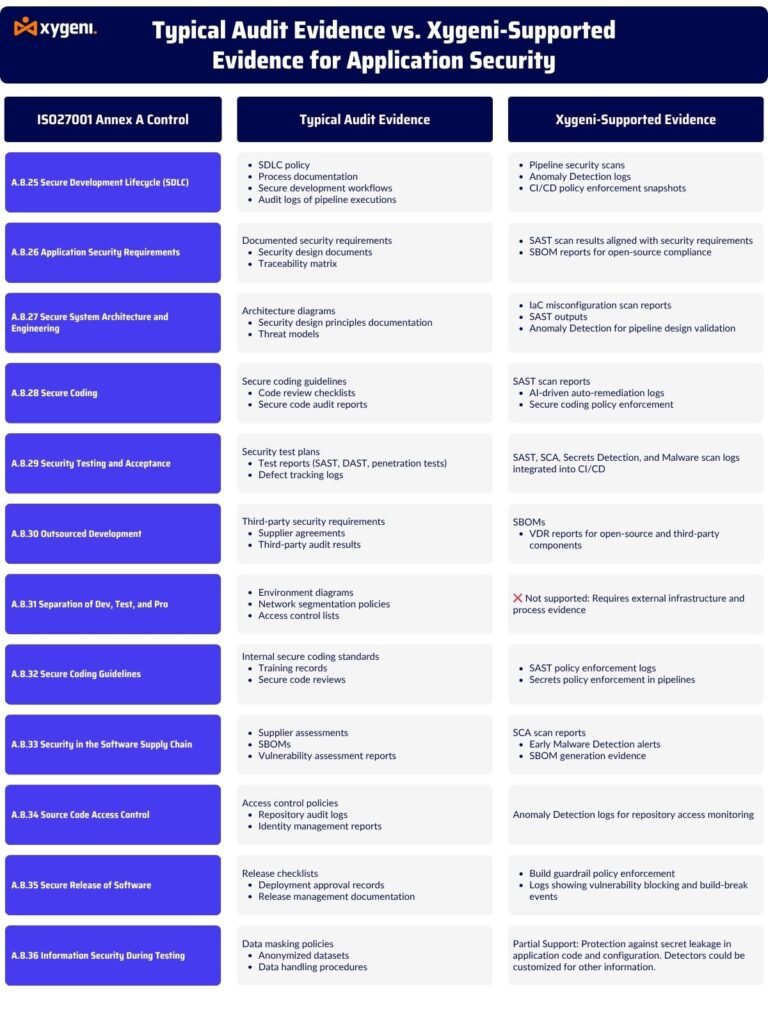
To meet ISO 27001 compliance requirements, organizations must not only implement security controls but also provide evidence during audits that these controls are effective and operational. Auditors typically expect documentation, process artifacts, and system logs to validate implementation.
Xygeni automates and centralizes this evidence collection. It generates audit-ready outputs such as SBOMs, pipeline scan results, policy enforcement logs, and anomaly detection alerts. This helps teams reduce manual effort and ensures continuous compliance throughout the secure development lifecycle.
The following table compares typical audit evidence for each ISO 27001 Annex A application security requirement with the evidence Xygeni provides:
Xygeni Capabilities in Detail
Xygeni simplifies ISO 27001 implementation by embedding a full suite of AppSec controls directly into developer workflows, reducing friction and ensuring auditability:
- Static Application Security Testing (SAST): Identifies vulnerabilities in proprietary code early in the SDLC.
- Software Composition Analysis (SCA): Detects risks in open-source components and maintains up-to-date SBOMs.
- Secrets Detection: Continuously scans for hardcoded credentials and API keys in code and CI/CD pipelines.
- Infrastructure as Code (IaC) Security: Flags security misconfigurations in Terraform, Kubernetes, and CloudFormation.
- Anomaly Detection: Monitors developer and pipeline behavior in real-time to detect unauthorized activity.
- Policy Guardrails: Enforces ISO 27001 controls by blocking builds that fail security checks.
- Early Malware Detection: Prevents malicious open-source packages from being introduced into projects.
- SBOM & VDR Generation: Automates the production of Software Bill of Materials and Vulnerability Disclosure Reports.
- Prioritization Funnels: Focuses remediation on exploitable vulnerabilities using reachability and risk scoring.
Each of these features contributes to continuous ISO 27001 compliance and enhances the overall maturity of the secure development lifecycle.
Conclusion: Strengthen ISO 27001 Compliance with Xygeni
Xygeni enables organizations to operationalize ISO 27001 Annex A application security requirements across their entire secure development lifecycle. In particular, by integrating deeply with CI/CD workflows, Xygeni delivers the tools and evidence needed to sustain ISO 27001 compliance, all while maintaining development velocity.
Key Benefits:
- Proactive risk reduction through SAST, SCA, and Secrets Detection embedded in the SDLC
- Continuous monitoring with anomaly detection and guardrails that enforce ISO policies
- End-to-end supply chain visibility with SBOMs, malware scans, and VDR reports
- Audit-ready evidence automatically generated and mapped to ISO 27001 controls
- Scalable remediation with AI-powered AutoFix and prioritization funnels
With Xygeni, AppSec becomes measurable, enforceable, and audit-ready accelerating both ISO 27001 implementation and long-term security maturity.







