To achieve true critical system protection, development teams must adopt shift left security practices that identify vulnerabilities and malicious code before deployment. This proactive approach to secure software development ensures that logic flaws and high-risk dependencies never reach production, protecting the core systems your business relies on.
A single bad commit can compromise your infrastructure and you might not catch it until it’s too late. This is why critical system protection must shift left, starting at the moment code is written, not after it’s deployed.
Critical systems include the software that powers your identity platforms, payment processors, admin portals, and CI/CD orchestrators, the backbone of your business. When these fail, attackers move fast. And you’re already behind if you’re relying solely on runtime defenses.
Take the XZ Utils backdoor: a low-level compression library hijacked by a trusted maintainer. It nearly shipped in major Linux distros — despite all the perimeter defenses in place, because the attack started inside the build pipeline.
This kind of risk demands shift left security. And it requires tools that catch issues in real time, in pull requests, in dependency upgrades, and in your workflows. That’s where Xygeni’s SAST and SCA make the difference.
From logic flaw detection to malicious package blocking and pre-merge guardrails that stop vulnerabilities before they hit production, Xygeni enables truly secure software development, with speed, clarity, and control.
What Does Critical System Protection Mean in Application Security?
In application security, critical system protection refers to securing the parts of your software that manage identity, sensitive data, business logic, and deployment automation. These are the components where a single flaw can lead to privilege escalation, data leaks, or full system compromise.
Key targets include:
- Authentication modules and token validation logic
- Secrets handling and configuration files
- Business-critical APIs that perform transactions or access sensitive data
- CI/CD scripts, runners, and deployment definitions embedded in your codebase
Modern attacks increasingly exploit the application layer. A vulnerable route, a misused dependency, or a misconfigured pipeline is often enough to breach critical systems.
This is why shift left security is a requirement for effective secure software development. You cannot rely on production defenses to detect issues that were introduced in development. The only reliable strategy is to integrate tools like SAST and SCA directly into your development workflow. This prevents issues before they are merged, dependencies before they are installed, and pipelines before they are triggered.
Software Composition Analysis for Secure Software Development
If you’re pulling in open source dependencies, you’re also pulling in someone else’s mistakes or worse, their malware. That’s why software composition analysis (SCA) is a foundational part of shift left security, essential for any team building secure software development pipelines.
How Xygeni’s SCA Enables Critical System Protection Before You Push Code
Xygeni scans dependencies the moment they’re added whether in package.json, requirements.txt, or even inside hardcoded install scripts in CI jobs. But unlike traditional SCA tools, it doesn’t flood you with irrelevant CVEs.
Instead, Xygeni focuses on what really matters:
- Flags malicious packages, even if they’re new and don’t have a CVE yet
- Runs reachability analysis to verify whether risky code paths are actually used in your app
- Scores exploitability, so you don’t waste time on low-impact issues
- Surfaces remediation risks before you patch, so you don’t accidentally introduce regressions
- Blocks dangerous packages before they instal, including in CI containers
As a result, your critical systems are protected at the earliest possible moment: when the dependency is introduced, not after it’s already in production.
Real-World SCA Example: Stopping Malicious Code in Shift Left Security
During a routine update, a developer adds this dependency to a Java project:
<dependency>
<groupId>com.thoughtworks.xstream</groupId>
<artifactId>xstream</artifactId>
<version>1.4.5</version>
</dependency>
It looks stable. No immediate CVE warnings pop up in local tooling.
But Xygeni’s SCA flags it instantly with CVE-2013-7285 a critical Remote Code Execution vulnerability (CVSS 9.8, CWE-78: OS Command Injection).
Reachability Analysis (from Xygeni context panel):
“Xstream API versions up to 1.4.6 and version 1.4.10, if the security framework has not been initialized, may allow a remote attacker to run arbitrary shell commands by manipulating the processed input stream when unmarshaling XML or JSON.”
- The code uses
XStreamfor XML deserialization - Xygeni detects the method is potentially reachable
- The vulnerability may be exploitable if used without defensive initialization
What Xygeni does next:
- Flags the vulnerable version directly in the
pom.xml - Recommends an upgrade to 1.4.7, the first patched version
- Shows remediation risk insights, warning of possible regressions from the upgrade
- Creates an AutoFix PR that safely bumps the version
- Blocks CI builds until the team reviews and approves the change
Result: The team patches the issue before it ever reaches a staging environment. Risk is neutralized. The fix happens at commit time, not after deployment.

Static Application Security Testing for Secure Software Development
Your team writes business-critical logic every day. If you don’t scan that logic early, flaws will reach production, and runtime tools won’t catch them. That’s why static application security testing (SAST) belongs inside your development workflow from the start.
SAST plays a critical role in shift left security and drives real results for secure software development teams.
How Xygeni’s SAST Supports Critical System Protection in Dev Workflows
Xygeni analyzes source code the moment developers submit a pull request. It tracks execution flow, traces input sources to sinks, and highlights real risks in critical paths, without interrupting the developer experience.
Here’s how it works:
- Scans code diffs for logic flaws like path traversal, SQL injection, and insecure auth checks
- Traces the full flow of each vulnerability from user input to runtime behavior
- Tags issues based on severity, exploitability, and whether they impact critical systems
- Suggests safe fixes automatically inside the PR with AutoFix, so developers can act immediately
- Blocks risky merges, keeping vulnerable code out of main without disrupting the team
Instead of surfacing false positives or generic CVEs, Xygeni focuses on exploitable flaws in the software you actually ship. It empowers your team to catch dangerous bugs early and protect your critical systems long before deployment.
That’s the value of real shift left security, and how you achieve secure software development without sacrificing speed or control.
Real SAST Example: Blocking CWE-22 Before It Reaches Critical Systems
Let’s say a developer updates a legacy Java service that writes to the file system. During a recent sprint, they commit the following code:
File baseDirectory = new File(args[0]);
This line pulls directly from args[], without validation. It seems safe, until you realize it opens the door to path traversal.
What Xygeni SAST Detects
Xygeni’s java.path_traversal check immediately traces this as a CWE-22 vulnerability:
Improper Limitation of a Pathname to a Restricted Directory.
- The source:
args[0], directly from user input - The sink:
new File(args[0])used to setbaseDirectory - The file:
.mvn/wrapper/MavenWrapperDownloader.java, line 50
This kind of bug lets an attacker point your app at unintended paths like ../../etc/passwd, risking unauthorized file access or overwrite.
AutoFix in Action: Secure by Default
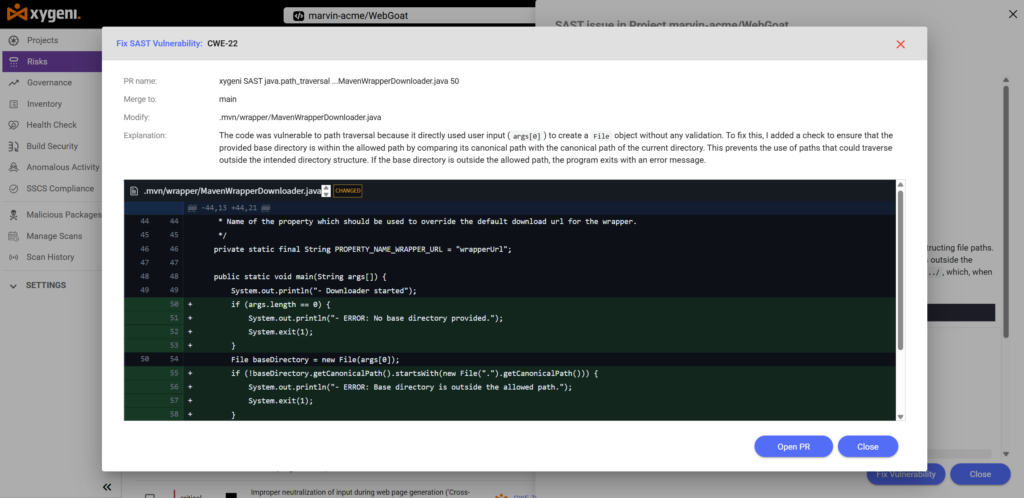
Xygeni suggests and prepares a patch but you stay in control. The fix ensures baseDirectory can’t escape the allowed directory tree:
.mvn/wrapper/MavenWrapperDownloader.java
CHANGED
* Name of the property which should be used to override the default download url for the wrapper.
*/
private static final String PROPERTY_NAME_WRAPPER_URL = "wrapperUrl";
public static void main(String args[]) {
System.out.println("- Downloader started");
if (args.length == 0) {
System.out.println("- ERROR: No base directory provided.");
System.exit(1);
}
File baseDirectory = new File(args[0]);
if (!baseDirectory.getCanonicalPath().startsWith(new File(".").getCanonicalPath())) {
System.out.println("- ERROR: Base directory is outside the allowed path.");
System.exit(1);
}
System.out.println("- Using base directory: " + baseDirectory.getAbsolutePath());
// If the maven-wrapper.properties exists, read it and check if it contains a custom
// wrapperUrl parameter.
File mavenWrapperPropertyFile = new File(baseDirectory, MAVEN_WRAPPER_PROPERTIES_PATH);
String url = DEFAULT_DOWNLOAD_URL;
The PR is blocked until this fix is merged. Reviewers can see the risk, the trace, the CWE tag, and the resolution, all right in the pull request.
Result
- The path traversal never reached production
- The team avoided a high-risk bug without any slowdowns
- The secure software development lifecycle continued fast and protected
This is how real shift left security works with Xygeni SAST: catching logic flaws early, guiding developers with clear context, and enforcing critical system protection before code merges.
Stop Threats Before They Start
If you wait until production to secure your applications, it’s already too late. Critical system protection starts in your IDE, not your firewall.
With modern attacks targeting source code, dependencies, and CI/CD pipelines, shift left security is no longer optional, it’s the only way to build truly secure software development workflows.
Xygeni gives developers real-time tools to catch logic flaws, block malicious packages, and enforce guardrails without slowing down your pipeline. From PR scans to dependency checks, you stay in control while the platform does the heavy lifting.
Secure faster. Detect earlier. Ship safer.
Checklist: Implement Critical System Protection in Development
You can’t secure critical systems after deployment. Here’s how to build protection into your development workflow with practical, shift left security tactics:
| Step | Action |
|---|---|
| Step 1: Scan PRs with SAST | Run Static Application Security Testing on every pull request to catch logic flaws like path traversal, insecure deserialization, or missing auth checks before code lands in main. |
| Step 2: Analyze Dependencies | Use Software Composition Analysis to detect malicious packages, assess reachability, and prioritize actual exploit paths — not just declared risks. |
| Step 3: Apply AutoFix with Oversight | Let Xygeni generate secure patches for SAST and SCA issues, but keep developers in control — no silent merges. |
| Step 4: Enforce CI/CD Guardrails | Define policies that block builds when vulnerabilities are reachable, exploitable, or malicious. Treat security checks like linting. |
| Step 5: Monitor Exploitability Funnel | Track risks across dev, test, and production. Use dashboards to identify which issues are safe to delay, fix immediately, or monitor. |
Summary Table: Shift Left Security for Critical System Protection
| Capability | SAST | SCA | CI/CD Guardrails |
|---|---|---|---|
| Detects logic flaws in PRs | ✅ | — | — |
| Flags malicious or risky dependencies | — | ✅ | — |
| Analyzes reachability and exploitability | ✅ | ✅ | ✅ |
| Auto-suggests safe fixes (AutoFix) | ✅ | ✅ | — |
| Blocks unsafe merges or builds | ✅ | ✅ | ✅ |
| Tracks risk from dev to prod | ✅ | ✅ | ✅ |
Conclusion: Build Fast with Shift Left Security and Critical System Protection
Critical system protection isn’t just a security concern, it’s a development priority. Attackers don’t wait for your code to hit production. They target dependencies in your repo, logic flaws in your pull requests, and misconfigured pipelines that deploy the rest.
Shift left security is how you beat them.
By integrating SAST and SCA into your development flow, you detect issues before they land. You patch fast, stay in control, and enforce secure software development without slowing your team down.
Xygeni gives you the visibility, automation, and control to protect the systems your business can’t afford to lose, from the first commit to the final deploy.
Want to see what’s lurking in your code?
Run your first shift left scan with Xygeni: no credit card needed.









