Modern development pipelines are powered by open source software. But without proper visibility, your organization may be exposed to license risks, vulnerabilities, and growing compliance pressure. That’s why it’s critical to adopt the best practices for disclosing open source components to customers, and to back those disclosures with action using the best solutions for securing open source components.
In this guide, we’ll walk through how to build a transparent and trustworthy disclosure process with SBOMs, VDRs, and the right open source security scanner. Every step aligns with current regulations and enterprise expectations.
1. Why the Best Practices for Disclosing Open Source Components Matter
Using open source components is standard in nearly all development workflows. However, without clear disclosure, you risk:
- Legal violations from unknown licenses
- Supply chain attacks from malicious packages
- Lost deals due to poor compliance documentation
To avoid these pitfalls, your disclosure strategy must be complete, accurate, and up to date. Adopting the best solutions for securing open source components ensures that transparency is paired with real risk reduction.
2. Automate SBOM and VDR for Open Source Component Transparency
To apply the best practices for disclosing open source components to customers, the most important foundation is automation. Instead of manually compiling package lists, teams should rely on tools that generate a complete and standards-compliant Software Bill of Materials (SBOM) and an accurate Vulnerability Disclosure Report (VDR).
An SBOM details every open source component used in your application, including direct and transitive dependencies, with information like version numbers, licenses, and origin. This is no longer optional. Regulations like NIS2 and Executive Order 14028 demand full visibility across the software supply chain.
However, a list alone is not enough. A VDR gives you and your customers real answers: which components are vulnerable, whether those vulnerabilities are exploitable, and what mitigation steps have been taken. VDRs are especially useful in regulated industries where software vendors must show not only what they use, but also how they manage risk.
With Xygeni, SBOM and VDR generation is built into your development pipeline. The system automatically collects dependency metadata, enriches it with licensing and vulnerability information, and exports it in industry formats like SPDX and CycloneDX. These reports meet the strictest compliance requirements and support trust-based disclosures across customer, audit, and procurement workflows.
3. Scan Dependencies with Ecosystem-Aware Analyzers
A correct disclosure starts with an accurate scan. To ensure completeness, you need analyzers built for each package ecosystem: npm, Maven, PyPI, NuGet, and others.
The Xygeni open source security scanner uses language-specific analyzers to go beyond static manifest parsing. These analyzers detect actual direct and transitive components used in your builds, resolve versions, and gather key metadata such as:
- License types
- Component origins
- Maintainer identity
- Package age or maintenance status
This level of detail is essential for applying the best practices for disclosing open source components to customers. Generic scanners miss critical indicators, like unscoped internal npm packages, which could be accidentally exposed to the public registry.
4. Detect Risky and Suspicious Components Before You Disclose
A high-quality disclosure process goes beyond inventory, it includes risk filtering. That’s where Xygeni’s open source security scanner sets itself apart. It includes specific detectors for:
- Dependency Confusion: Catch internal package names matching public ones.
- Typosquatting: Block lookalike packages designed to deceive.
- Malware: Identify malicious behavior in install-time or runtime scripts.
- Suspicious Scripts: Detect untrusted shell commands or encoded logic.
- Anomalous Packages: Highlight uncommon or out-of-pattern components.
- Unscoped npm Modules: Flag internal code that could be published accidentally.
These capabilities make the open source security scanner a critical part of the best solutions for securing open source components, ensuring your disclosures reflect a security-first approach before reaching your customers.
| Package Manager | Language | Supported Dependency Files |
|---|---|---|
| Maven | Java | pom.xml |
| Gradle | Java, Kotlin | build.gradle, build.gradle.kts, gradle.lockfile, gradle.properties |
| NPM | JavaScript | package.json, package-lock.json |
| Yarn | JavaScript | yarn.lock |
| PNPM | JavaScript | pnpm-lock.yaml |
| Bower | JavaScript | bower.json |
| NuGet | .NET, C# | .nuspec, packages.config, .csproj, project.assets.json, packages.lock.json |
| Pip | Python | requirements.txt, pipfile.toml, pipfile.lock, setup.py, setup.cfg, environment.yml |
| Poetry | Python | requirements.txt, pyproject.toml, poetry.lock |
| Go Modules | Golang (Go) | go.mod, go.sum |
| Composer | PHP | composer.json, composer.lock |
| RubyGems | Ruby | Gemfile, Gemfile.lock |
5. Add Vulnerability Context with Reachability and Exploitability
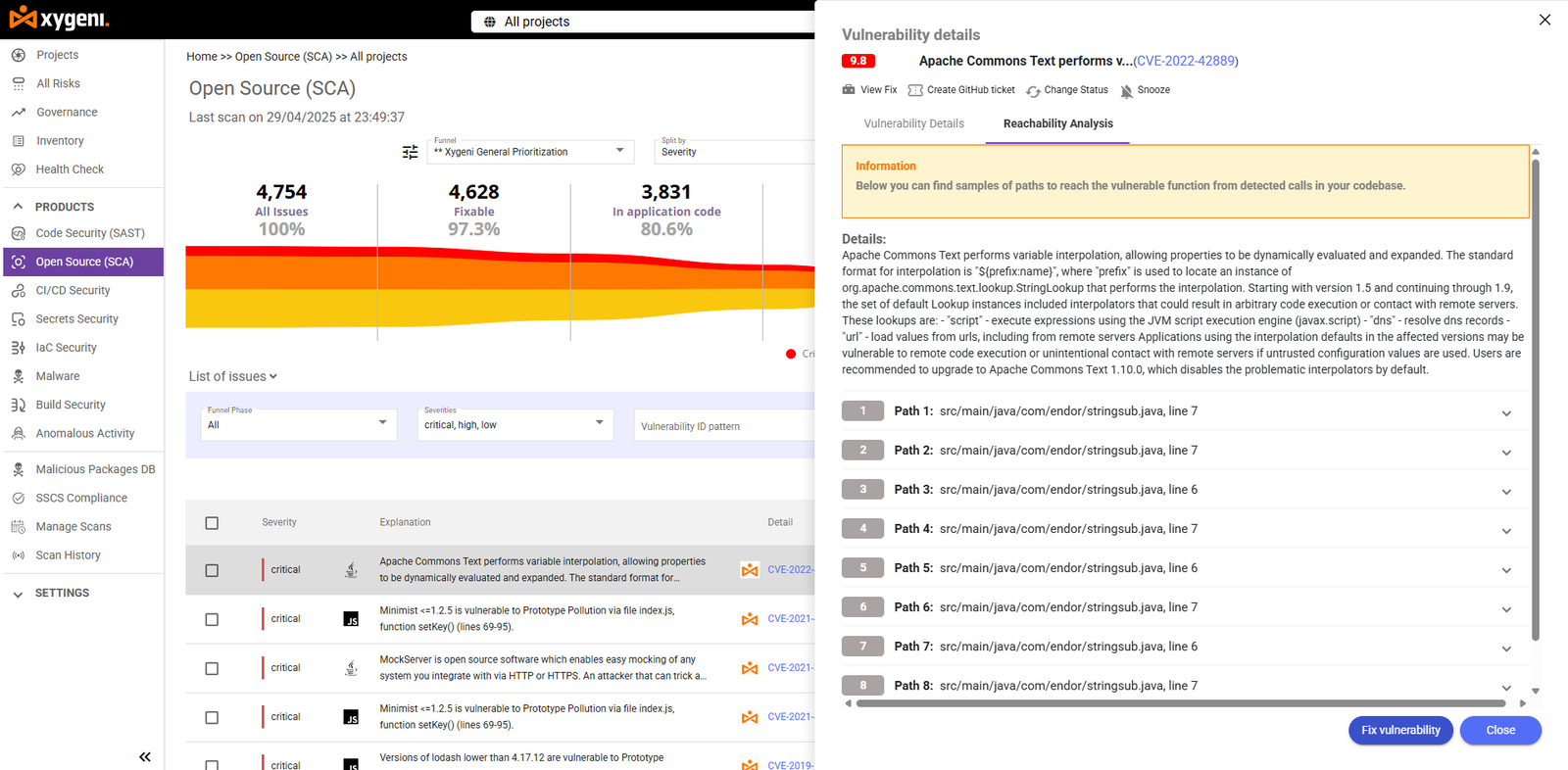
When disclosing vulnerabilities, context is everything. Not all CVEs are equal. A severe vulnerability might never be triggered in your application if the affected code is unreachable.
Xygeni enriches its VDRs with:
- Reachability analysis: Identifies whether the vulnerable function is actually called.
- EPSS scoring: Estimates the likelihood of real-world exploitation.
- Remediation Risk insights: Shows which upgrade options are safest, including breaking changes or new risks introduced in patched versions.
This reduces noise and helps you focus disclosures on what matters. Customers get real security intelligence, not a long, unactionable list.
6. Integrate CI/CD to Keep Disclosures Accurate and Real-Time
Open source components change frequently. That’s why static disclosure documents go stale quickly. To ensure accuracy, your disclosure workflow must integrate with CI/CD.
Xygeni allows you to:
- Automate SBOM and VDR generation during builds
- Set security gates to block unsafe packages
- Receive instant alerts when a clean dependency becomes vulnerable
- Track changes across pull requests and deployments
This real-time integration keeps your disclosures current and aligned with the best practices for disclosing open source components to customers, especially when dealing with enterprise customers or audit frameworks.
7. Deliver Audit-Ready Reports That Build Trust
Your customers and auditors need more than a list, they need clarity and proof. Xygeni makes that easy.
You can:
- Export SBOMs and VDRs with one click
- Filter by severity, license type, or exploitability
- Use our Web UI for compliance dashboards
- Annotate risks and attach remediation notes
These features not only simplify audits, they help you meet the full scope of the best solutions for securing open source components.
Apply the Best Practices for Disclosing Open Source Components to Customers
Successfully managing open source security is no longer just a technical challenge, it’s a competitive advantage. By following the best practices for disclosing open source components to customers, you show that your software is not only functional but also secure, transparent, and compliant.
Disclosing your open source components clearly, along with real-time vulnerability data, builds trust with both users and enterprise clients. It also supports compliance with frameworks like NIS2, DORA, and Executive Order 14028.
Using an open source security scanner like Xygeni gives your team the automation and intelligence it needs to:
- Generate accurate SBOM and VDR reports with every build
- Detect hidden threats in your software supply chain
- Highlight exploitability and license risks in your components
- Deliver actionable, audit-ready reports on demand
These capabilities are part of the best solutions for securing open source components, and they position your team as proactive and reliable partners in security.








