Did you know that a single line of faulty code can cost a company millions of dollars? Ensuring the integrity and security of software is crucial. This is where software attestation and build attestation play a key role. These practices provide verifiable proof that software builds comply with strict security standards, fostering trust and reducing threats throughout the development lifecycle. As a game-changer in DevSecOps, attestation strengthens security at every stage of development.
Did you know that a bug in the code of Knight Capital Group, a high-frequency trading firm, led to a loss of $460 million in just 45 minutes in 2012? The faulty code sent out millions of erroneous stock orders, causing market chaos and significant financial losses for the company.
What is Software Attestation in Build Security?
Software attestation in build security is a critical process within DevSecOps that generates verifiable evidence to confirm that software builds comply with predetermined security policies and procedures. This process is vital for protecting software supply chains from cyber threats. Attestation ensures teams follow strict security standards at every stage of the software development lifecycle (SDLC). Many of these standards are outlined in NIST’s comprehensive cybersecurity frameworks.
The Pillars of Build Attestation
Defined pillars support build security attestation, underpinning the software’s integrity, reliability, and trustworthiness within DevSecOps practice. These are the important principles, processes, and components contained in the build security attestation execution and implementation. We shall consider each of the pillars.
Collection of all the necessary evidence across the whole SDLC
The first pillar involves analyzing and collecting logs, configurations, and data from key points in the construction process. By systematically gathering this evidence, organizations maintain transparency, traceability, and accountability throughout the development pipeline.
Secure Storage
It involves using mechanisms for encrypted, access-controlled storage to ensure integrity and confidentiality of attestation data. These mechanisms protect against compromise or unauthorized access. This pillar ensures evidence remains immutable and trustworthy. A reliable source of truth is established through verification.
Attestation Engine
The Attestation Engine assesses whether software builds conform to defined security standards. It produces attestations that document compliance with these standards. At the core of this process, the Attestation Engine automates the attestation to ensure timely, accurate, and consistent security checks. This guarantees the integrity of the build.
Independent Verification
The fourth pillar relies on independent verification to support the role of generated attestations. Impartial verification ensures that attestations align with security policies and procedures. It validates their integrity. This pillar guarantees that the attestation process is objective, accountable, and trustworthy. It reduces the risk of bias or manipulation during attestation.
Reporting and Insights
The final pillar provides full reporting and insight into the attestation process. A dashboard or reporting tool offers visibility into the security posture of software builds. It shows whether compliance with security standards is met or lacking. This helps identify exposures, track performance, and make informed decisions to enhance security.
The strong combination of these pillars forms the foundation for building security attestation. This helps organizations in software development protect against emerging cyber threats. Adopting these principles in processes and technologies fosters a culture of safe, integral, and trusted software builds.
The Software Attestation Workflow: Ensuring Integrity and Trust
The attestation workflow follows a clear process to verify the authenticity of each software component. It begins with setting a contract. This contract outlines the requirements for attestation, such as describing the container image or including a Software Bill of Materials (SBOM) for high-evidentiary attestations. It ensures all build processes follow set standards.
By integrating this workflow into Continuous Integration (CI) pipelines, teams can create attestations seamlessly. These attestations track the software’s progress through development, testing, and deployment. Teams enforce strict security measures and rigorously check the attestations against the contract for accuracy.
The journey of attestation unfolds through several distinct phases, each critical to the integrity of the build security:
- Preparation: Establishing the attestation framework and defining security policies.
- Evidence Collection: Gathering data across the SDLC to ensure a comprehensive security overview.
- Attestation Generation: Evaluating the evidence to produce attestations that affirm compliance with security policies.
- Verification: Independently verifying attestations to confirm the build’s security integrity.
- Reporting and Insight: Analyzing attestation results to provide actionable insights for enhancing build security.
Benefits of Software Attestation in Build Security
Using attestation in build security brings many benefits, important for keeping software development secure and reliable:
- Better Security: Ensures builds are safe and follow security rules.
- Increased Trust: Builds transparency and accountability, creating trust with stakeholders.
- Compliance: Helps meet security standards and follow regulations.
- Risk Reduction: Finds and fixes security risks early in the development process.
- Efficiency: Adds security to the CI/CD pipeline, making the process more efficient.
Software Attestation Formats and Models
Attestation formats and models offer structured ways to represent software components or events. These frameworks let attesters organize metadata clearly, ensuring attestations can be used across different software development environments. This consistency helps keep practices clear and standardized.
Key Elements of Software Attestation Formats and Models
Objective: Attestation formats and models verify the trust and authenticity of software artifacts or events. They include information such as the software’s creation, origin, dependencies, and security attributes.
Standardization: Attestation formats and models aim to standardize processes for consistency and compatibility across tools, platforms, and ecosystems. Industry associations, standard-setting bodies, or communities often define these standards. They provide common schemas, data structures, and protocols to ensure clear communication.
Types of Software Attestation Formats
Provenance: The SLSA (Supply Chain Levels of Software Assurance) Provenance format is a widely adopted format in open-source supply chains. It provides detailed information on how software artifacts were built, including the environment, dependencies, and build commands.
Software Bill of Materials (SBOM): SBOM offers a formatted list of software artifacts, along with their dependencies and relationships. It makes the software build composition transparent, enabling stakeholders to assess security, compliance, and license obligations.
Custom Formats: Organizations can customize attestation formats to meet specific compliance needs or industry standards. They can add additional metadata, validation rules based on organizational policies, or cryptographic mechanisms as needed.
Software Attestation Model elements:
Attestation models include several structured elements in a standard way. Different models or forms indicate what is to be included in the attestation and how it should be structured.
- Envelope: Provides authenticity and integrity of the attestation message normally by cryptographic digital signature or certificate.
- Statement: Contains the actual content or statement being attested, i.e., details about the software artifact, its provenance, or compliance status.
- Signature: Denotes the attester who created the attestation, ensuring accountability and authenticity.
- Predicate: It shall contain metadata about the attestation subject; this includes the artifact attributes, the artifact properties, or its compliance status.
- Bundle: A collection of multiple attestations or artifacts that are related in a related manner, facilitating the organization and management of attestation data.
Interoperability and Adoption
By using standardized attestation formats and models, they can easily fit into existing tools, workflows, or security frameworks. This ensures a smooth adoption process. It also allows for automated processing, validation, and verification of different environments during software development and deployment.
Software Attestations Security Best practices
Best practices in attestations refer to the guidelines, methods, and approaches within software development and its supply chain ecosystems, which ensure the effectiveness, security, and reliability of attestation processes. Some of the key best practices to guide the entities to have a sound attestation framework that supports trust, transparency, and accountability include the following:
Representation of the Attestations
Standardization should be adhered to concerning formats, schemas, and protocols for the representation of attestations. Use industry standards where possible to guarantee consistency and compatibility with the tools, platforms, and ecosystems that the resulting solution will interact with.
Authentication and Integrity
Implement strong mechanisms such as cryptographic signs, digital certificates, or hash functions to assure the identity of the attestation and its content not to be altered, protecting against any form of tampering, forging, or other unauthorized modifications to the attested data.
Access Control and Authorization
Enforce access control and authorization rules to limit who can access attestation data, following need-to-know or least-privilege principles. Only the right people or systems should have permission to create, change, or view attestations. This prevents unauthorized access and keeps the data secure.
Storage
Store attestations in secure and tamper-proof containers or repositories, which are encrypted, access-controlled, and have audit trails to maintain data confidentiality and resilience. They should be readily available when needed for verification or audit purposes.
Lifecycle Management
Establish clear processes for attestation lifecycle management, including creation, validation, expiration, and revocation. Regularly update attestations to reflect changes in software builds, dependencies, or security postures.
Auditing and Monitoring
Set up auditing and monitoring mechanisms to track and audit attestation activities, including creation, verification, and consumption. This allows for timely detection and response to security incidents within attestations.
Easily Integrated with Third Parties
Ensure easy integration of attestation processes with third-party tools, services, or platforms used within the software development and supply chain ecosystem, including CI/CD pipelines, artifact repositories, vulnerability scanners, and policy enforcement engines.
Transparency and Documentation
Maintain openness and documentation in attestation processes, policies, and procedures. Document the rationale, criteria, and methodologies for generating, verifying, and interpreting attestations to ensure all parties involved understand and are accountable.
Training and Awareness
Provide training and awareness programs for all personnel involved in the attestation process, such as developers, security practitioners, and auditors, ensuring they understand their roles, responsibilities, and best practices for attestation.
Continuous Improvement
Foster a culture of continuous improvement through feedback, reviews, and iterative enhancements within technology and governance frameworks. Regularly assess and refine attestation practices to adapt to changing risks, regulations, and standards.
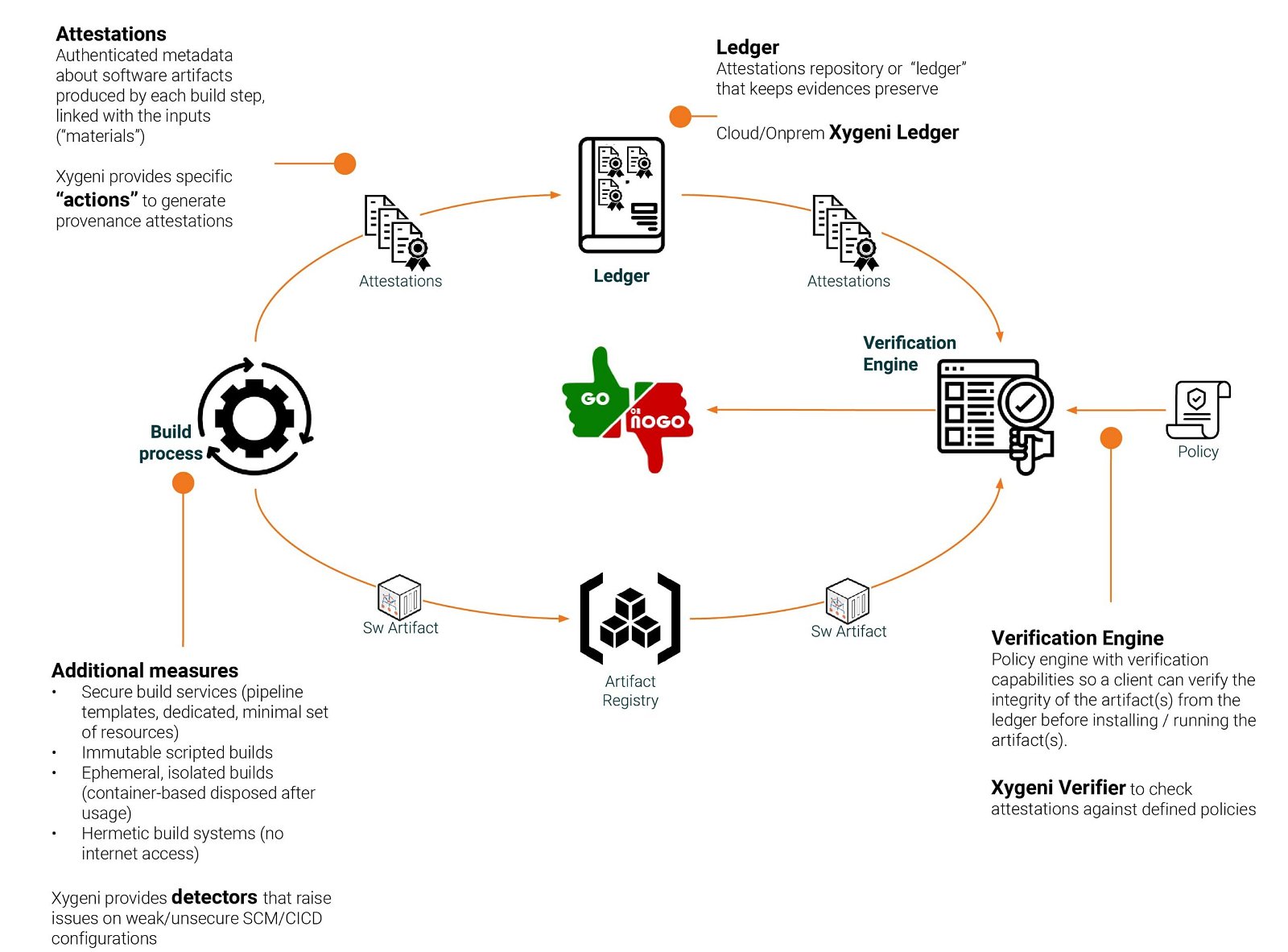
Xygeni’s Software Attestation Solution: Raising the Bar for Cybersecurity
Xygeni’s Software Attestation Solution makes sure that every part of the software development lifecycle (SDLC) follows the highest security and compliance standards. By adding attestation to your CI/CD pipelines, Xygeni provides proof that your software stays secure and intact from build to deployment.
Xygeni’s platform handles secure build attestations through an automated system that creates, stores, and checks attestations. This ensures that your software’s journey—from code to deployment—is monitored, verified, and protected from tampering. Our solution uses Supply Chain Levels for Software Artifacts (SLSA) attestations to build a chain of trust, stopping unauthorized changes or vulnerabilities from entering your code.
Key Features of Xygeni’s Attestation Solution:
- Full Automation: Attestations are automatically generated during the build process, ensuring your software components meet security standards without manual intervention.
- In-toto Attestation Predicate: This standard format for attestations offers a clear, documented narrative of the software’s development process, ensuring transparency.
- Verification Engine: Xygeni’s platform includes a robust verification engine, cross-referencing attestations with predefined policies to ensure compliance and validity.
- Secure Storage: Attestations are encrypted and stored securely, safeguarding them from tampering.
- Provenance and SBOM Integration: Xygeni’s solution integrates with Software Bill of Materials (SBOM) to provide a detailed account of all software components, ensuring full traceability of open-source and proprietary dependencies.
By using Xygeni’s attestation solution, companies can actively improve their security, stay ahead of new threats, and meet changing rules like NIST and SLSA standards. This builds trust in your software supply chain and helps meet strict compliance needs, creating a safe and strong development process.
For organizations looking to adopt Software Supply Chain Security (SSCS), Xygeni’s attestation tools offer unmatched visibility, control, and confidence at every stage of development.