The 2025 Verizon Data Breach Investigations Report found that 22% of breaches involved web application vulnerabilities, —highlighting persistent risk at the application layer. Consequently, application security tools are essential for DevOps workflows. Today, attacks target not just production, but the entire software delivery lifecycle. Accordingly, the role of application security testing tools has expanded. Modern AppSec tools now go beyond basic scanners. They help detect insecure code, secure open-source components, and monitor misconfigurations across infrastructure and code.
This guide outlines the main types of application security tools, explains how they work, and provides practical criteria to help you choose the right solutions—without disrupting developer velocity.
What Are Application Security Tools?
Application security tools—often called AppSec tools—help teams find and fix security issues throughout the software development lifecycle. They’re built to secure your code before, during, and after deployment.
So, what is AppSec?
AppSec stands for application security. It includes the tools and practices used to protect software from threats. Unlike traditional security that protects networks or hardware, AppSec focuses on the application itself—your code, APIs, and workflows.
Whether you’re building microservices, shipping containerized apps, or working in a CI/CD pipeline, application security testing tools help you catch issues early, reduce risk, and stay compliant with frameworks like DORA and NIS2.
Moreover, this is not just a passing trend. According to Statista, the Application Security market is projected to hit $8.53 billion in revenue in 2025. That reflects the rising demand for tools that secure every layer of the software supply chain.
Next, let’s look at two core types of application security tools —SAST and DAST—and how they fit into real-world DevSecOps workflows.
Types of Application Security Testing Tools
Static Application Security Testing (SAST)
What is SAST?
SAST (Static Application Security Testing) examines your source code, bytecode, or binaries without executing them. It runs as you write code—typically inside your IDE or during pull requests—to catch unsafe patterns, hardcoded secrets, and logic flaws before you build or ship.
How does SAST work?
SAST tools scan the code’s structure using an Abstract Syntax Tree (AST) and track how data flows through it. This helps spot issues like:
- SQL injection risks
- Hardcoded credentials
- Unsafe API calls
- Weak authorization logic
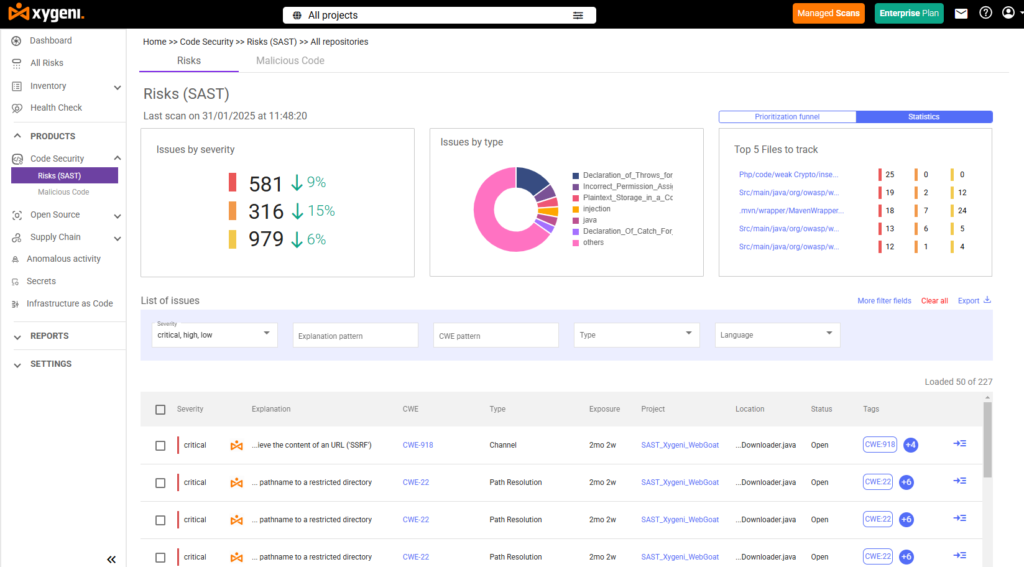
Example: Xygeni SAST
Specifically, Xygeni’s SAST fits directly into your developer workflow. It scans source code and Infrastructure as Code (IaC) across several languages. You get precise alerts via pull request analysis and customizable rules—so nothing blocks your team unnecessarily.
Moreover, Xygeni correlates findings with reachability data and CI/CD context. As a result, it helps you fix what’s actually exploitable—not just what’s technically flawed.
Dynamic Application Security Testing (DAST)
What is DAST?
DAST (Dynamic Application Security Testing) analyzes your application while it’s running. It simulates attacks against live environments—like staging or production—to find:
- Cross-Site Scripting (XSS)
- Broken access controls
- Exposed APIs or endpoints
- HTTP header misconfigurations
How is DAST different from SAST?
To clarify:
- SAST is a white-box test: it reads your code without executing it.
- DAST is a black-box test: it observes behavior without seeing the code.
In essence, SAST stops issues before builds, while DAST finds threats in runtime. Therefore, using both tools together gives you full-spectrum AppSec coverage.
Beyond Testing: The Rise of Integrated AppSec Tools
Traditional application security testing tools are no longer enough. In fact, modern development pipelines demand real-time visibility, automated remediation, and lifecycle-wide protection. Accordingly, application security tools must evolve to detect issues early, before they escalate into production incidents.
Software Composition Analysis (SCA)
Software Composition Analysis helps identify risks in open-source and third-party components. Unlike basic scanners, advanced application security tools like Xygeni’s SCA go further by:
- Scanning direct and transitive dependencies across multiple registries
- Prioritizing vulnerabilities with reachability analysis and EPSS scoring
- Automatically generating pull requests via AutoFix
- Managing open-source licenses to support compliance efforts
Altogether, this enables teams to focus on what’s exploitable—not just what’s listed in a CVE database.
Secrets Detection
Secrets Detection is about catching hardcoded credentials—like API keys and tokens—before they leak. Xygeni Secrets Security ensures security without slowing developers by:
- Blocking exposed secrets at the pre-commit level
- Detecting credentials in existing code, logs, and histories
- Integrating seamlessly with Git platforms and CI/CD tools
Consequently, this application security testing tool reduces incident response time and avoids downstream risks.
Infrastructure as Code (IaC) Scanning
IaC Scanning targets your infrastructure definitions—written in Terraform, Helm, or Kubernetes—before they go live. Specifically, Xygeni IaC Security flags:
- Misconfigurations like open ports, overly broad permissions, and missing encryption
- Risky default settings across environments
- Policy violations directly in your CI/CD or pre-commit flow
Consequently, these automated application security tools help you enforce security by design—without disrupting your team’s velocity.
How to Choose the Right Applications Security Tools for Your Stack
Choosing the right application security tools isn’t just about checking boxes. Instead, it’s about finding solutions that match your workflow, scale with your team, and reduce risk—without disrupting velocity. Whether you’re moving fast in a startup or juggling compliance in a larger org, these are the criteria that matter.
1. Coverage Across the SDLC
Firstly, the tool must cover the entire software development lifecycle—not just post-deployment. That is, it should secure code from your IDE to production.
Look for:
- IDE plugins and Git pre-commit hooks
- CI/CD pipeline integrations
- Runtime visibility and scanning
2. Prioritization That Reflects Real Risk
Not all vulnerabilities are created equal. Consequently, tools that incorporate real-world context—like EPSS scores and reachability—help teams fix what’s actually exploitable.
Key features:
- EPSS-based vulnerability scoring
- Reachability analysis
- Risk scoring tied to business impact
3. Built-In Automated Remediation
In short, finding issues isn’t enough—fixing them fast is what counts. The best application security testing tools auto-generate fixes and simplify developer response.
Must-haves:
- AutoFix pull requests
- Secure code recommendations
- Dev-friendly dashboards
4. Secrets Detection and IaC Security
Secrets leaks and infrastructure misconfigurations are major breach vectors. Thus, a modern platform must detect both in real-time.
Look for:
- Pre-commit secret blocking
- Terraform, Helm, and Kubernetes IaC scanning
5. Unified Platform Over Fragmented Tools
Otherwise, juggling multiple point tools slows you down. Instead, a unified platform brings scanning, reporting, and remediation under one roof.
Ask yourself:
- Can it reduce tool fatigue?
- Does it support both DevOps and security workflows?
6. Compliance and Governance-Ready
Given that regulations like DORA and NIS2 demand traceability, your tool should automate audit-readiness from day one.
Checklist:
- Real-time compliance dashboards
- Audit trails and evidence logs
- Policy-as-code enforcement
7. Easy Integration with Your Toolchain
Finally, the best application security tools don’t slow teams—they fit in seamlessly. Make sure integrations are lightweight and CI/CD-friendly.
Check for:
- GitHub, GitLab, Bitbucket compatibility
- CI/CD integrations (e.g., Jenkins, GitHub Actions, CircleCI)
- IDE support for VS Code, IntelliJ, etc.
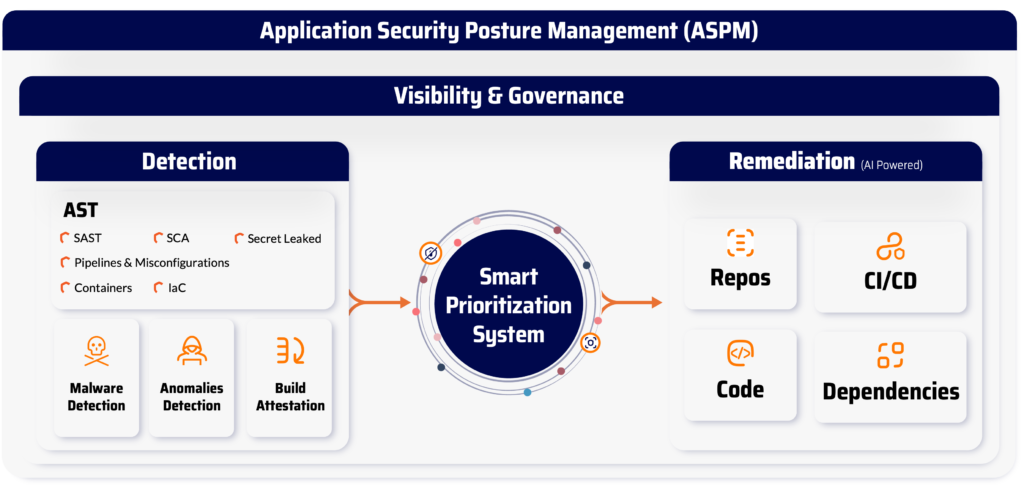
Why Xygeni Offers More Than Traditional AppSec Tools
Most application security tools do one thing well, scanning for bugs or vulnerabilities. However, in modern DevOps environments, that’s no longer enough. You need a platform that secures every part of your software supply chain—from code to cloud.
What Makes Xygeni Different?
Xygeni is not just another security scanner. It’s an all-in-one AppSec platform that brings full-lifecycle protection, smart prioritization, and seamless developer integration—without slowing you down.
Complete Supply Chain Coverage
Xygeni watches over everything: your source code, open-source dependencies, CI/CD pipelines, secrets, Infrastructure as Code (IaC), and even production artifacts. Consequently, you gain complete visibility with zero blind spots.
Smart Prioritization with Real Risk Signals
Unlike basic scanners, Xygeni doesn’t overload you with noise. It combines reachability analysis, EPSS scoring, and anomaly detection to surface only the risks that are likely to be exploited.
Built-in Automation for Developers
Moreover, Xygeni fits naturally into developer workflows. From AutoFix pull requests to pre-commit secret detection, it helps secure every commit—without disrupting your velocity.
Malware and Secrets Protection
Xygeni scans public registries for hidden malware and blocks leaked secrets before they reach your repositories. As a result, your codebase stays clean and production-safe.
Compliance Without the Headaches
In addition, Xygeni helps you meet compliance requirements like DORA, NIS2, and ISO 27001 by generating SBOMs and Vulnerability Disclosure Reports (VDRs) automatically.
One Platform. One Workflow. Total AppSec Security Tools.
To sum up, Xygeni brings everything together—testing, remediation, monitoring, and compliance—into a single, unified platform. No tool sprawl. No alert fatigue. Just actionable intelligence, delivered when and where it matters.
Final Takeaways: Why Application Security Tools Must Work Together
Throughout this guide, we’ve explored how application security tools have evolved—from basic code scanners to integrated platforms that secure the entire software supply chain. Consequently, with threats targeting everything from source code to infrastructure, relying on just one tool isn’t enough.
Undoubtedly, effective application security testing tools, like SAST and DAST, catch issues early and reduce downstream risk. Meanwhile, modern AppSec tools—including SCA, secrets detection, and IaC scanning—cover the layers traditional scanners often miss.
However, the real value comes from combining them. Otherwise, tools that work in isolation leave gaps. Instead, platforms like Xygeni’s All-in-One AppSec solution unify these capabilities, delivering a continuous, developer-friendly security posture from commit to cloud.
Accordingly, security is stronger when everything works together.
- Build securely
- Ship confidently
- Stay ahead of compliance