Modern attacks rarely happen without warning. Long before exploitation, threat actors leave digital traces: leaked credentials, cloned repositories, suspicious domains, or reused code snippets. Because of this, detecting these breadcrumbs early has become essential. That’s the idea behind open source intelligence (OSINT) and the reason the OSINT framework and a growing ecosystem of open source intelligence tools matter so much in cybersecurity today.
By learning how to collect, correlate, and automate OSINT, DevSecOps teams and CISOs can uncover hidden risks efficiently. As a result, they strengthen their software supply chain and respond to incidents before they escalate.
What Is OSINT? A Brief History and Definition
Open Source Intelligence (OSINT) refers to collecting and analyzing publicly available information to identify potential threats, vulnerabilities, and exposures. Originally, government and military agencies used this approach in the 1980s for political and defense research. Over time, cybersecurity experts realized that the same concept could apply to digital ecosystems, enabling early detection of attacks.
Security researchers soon learned that open data, domain records, public code repositories, or underground forums, could reveal attacker activity well before an actual breach occurred. In practice, OSINT now operates across every stage of the threat lifecycle, from reconnaissance to response.
Today, open source intelligence (OSINT) has become a vital part of modern threat intelligence and a trusted ally for developers who must protect their code, pipelines, and dependencies continuously. In other words, OSINT connects the dots between code visibility and threat awareness. However, because it relies on publicly available data, it can also generate noise, lack internal context, or surface signals that are hard to prioritize. As a result, both developers and CISOs need automated ways to filter, enrich, and act on OSINT insights faster , turning open data into meaningful defense.
OSINT uses public data from websites, code registries, and social platforms to detect indicators of compromise and prevent attacks before they reach production.
The Evolution of Open Source Intelligence in Cybersecurity
To begin with, understanding how OSINT evolved helps explain why it is now essential.
- Phase 1 – Early OSINT (Pre-Internet): Analysts gathered information from newspapers, broadcasts, and public records to interpret geopolitical events. At that time, intelligence collection was manual and slow. Nevertheless, it built the foundation for structured analysis.
- Phase 2 – Internet OSINT (2000 – 2010): With WHOIS databases, DNS records, and early search engines, investigators began mapping domains and tracking phishing infrastructure. In addition, the expansion of online communities created new channels to observe attacker behavior directly. Consequently, OSINT became faster, broader, and more collaborative.
- Phase 3 – Digital OSINT (2010 – Today): Modern intelligence now reaches into cloud services, social media, and developer platforms such as GitHub, npm, and Docker Hub. Moreover, automation, machine learning, and APIs enable large-scale correlation. As a consequence, OSINT has shifted from slow manual research to continuous digital monitoring, an ability now critical for AppSec and software-supply-chain protection. In practice, this evolution means detecting threats before they ever reach production.
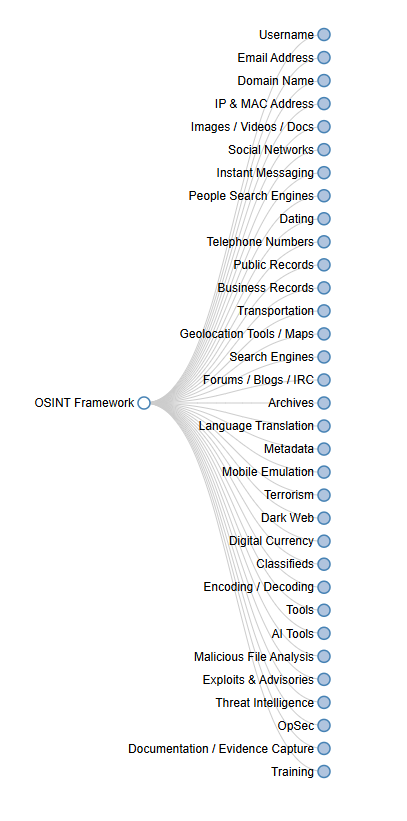
How the OSINT Framework Works
In simple terms, the OSINT framework serves as a structured index of tools and data sources grouped by categories such as domain intelligence, social networks, dark-web monitoring, and code analysis. By organizing information this way, analysts and developers can quickly locate the right open source intelligence tools for each task.
Typically, security teams follow a repeatable cycle when applying the framework:
- Collect data: Gather indicators from repositories, registries, or open feeds.
- Correlate signals: Link domains, hashes, or leaked credentials across multiple sources.
- Act fast: Prioritize remediation or automate alerts directly through CI/CD workflows.
In practice, the OSINT framework is not a single tool but a structured approach that organizes hundreds of open source intelligence resources. Instead of performing manual searches, security teams use this framework to combine data from various tools, such as SpiderFoot, Shodan, or TheHarvester, and transform scattered information into actionable insights.
For example, a DevSecOps engineer could automate this process by connecting APIs from different sources into their CI/CD environment. Consequently, potential leaks or exposed assets would trigger alerts automatically before deployment.
In summary, the OSINT framework offers a model for turning public intelligence into a repeatable, automated workflow, and this is precisely where Xygeni takes the concept further.
How CISOs and Developers Use Open Source Intelligence
For CISOs and Security Leaders
- Monitor brand exposure, leaked credentials, and cloned repositories.
- Cross-check OSINT findings with vulnerability databases to guide patch priorities.
- Correlate external intelligence with internal telemetry for accurate risk scoring.
- Report measurable results, such as closed exposures or reduced attack surfaces, to demonstrate ROI.
For Developers and DevSecOps Teams
- Scan commits for hard-coded secrets and tokens.
- Detect typosquatted or malicious dependencies in npm, PyPI, or Maven.
- Receive alerts when organization names or repos appear in external threat feeds.
- Integrate OSINT lookups into CI/CD pipelines for automated visibility.
Ultimately, OSINT gives every stakeholder a shared lens on the threat landscape, from executive dashboards to developer terminals.
Benefits of Open Source Intelligence for Security Teams
| Benefit | How It Helps |
|---|---|
| Early Detection | Identify exploits, leaks, or impersonations before attackers weaponize them. |
| Visibility | Map external assets beyond traditional scanners. |
| Correlation | Enrich alerts with external threat context to prioritize fixes. |
| Automation | Schedule OSINT lookups or connect APIs in pipelines. |
| Collaboration | Share verified intel with the wider security community. |
Key takeaway:
Open source intelligence adds visibility and speed, helping teams focus on real threats rather than noise.
Top Open Source Intelligence Tools and How Xygeni Applies Their Principles
Open source intelligence tools help security teams transform public data into actionable context. For example, tools such as Maltego, SpiderFoot, and Shodan have long supported analysts in mapping infrastructure and detecting exposed assets. However, these solutions usually require manual setup and continuous attention, which doesn’t scale in modern CI/CD environments.
- Maltego: Enables visual link analysis to map relationships between domains, IPs, and organizations.
- SpiderFoot: Automates scanning across hundreds of public sources and APIs.
- TheHarvester: Collects subdomains, emails, and banners — ideal for reconnaissance and asset discovery.
- Shodan: Scans the internet for exposed devices, open ports, and outdated software.
- Censys: Searches and analyzes internet-connected hosts and certificates at scale.
- Gitrob: Detects leaked secrets and tokens within Git repositories.
- TruffleHog: Finds high-entropy strings and leaked credentials across Git histories.
Together, these tools illustrate how OSINT reveals the same external visibility that attackers often exploit. Nevertheless, managing them individually can be time-consuming for developers who focus on speed and delivery.
How Xygeni Brings OSINT to DevSecOps
In contrast to traditional open source intelligence tools, Xygeni embeds those same intelligence techniques directly into development workflows. Instead of running separate scripts or dashboards, teams get continuous insights within their CI/CD pipelines, repositories, and IDEs.
Specifically:
- Xygeni’s Early Warning system monitors open registries (npm, PyPI, Maven) for malicious or typosquatted packages, following OSINT-style threat monitoring.
- Its Secrets Detection engine identifies exposed tokens and credentials in public code, the same principle behind Gitrob and TruffleHog, but fully automated.
- Anomaly Detection continuously correlates repository behavior, dependency changes, and workflow modifications to flag suspicious activity before an attack escalates.
- Through Reachability and Exploitability analysis, Xygeni prioritizes findings that truly matter, combining OSINT context with runtime visibility.
In addition, all this intelligence is enriched with external data sources, CVE information, and registry telemetry, creating a full feedback loop between open intelligence and internal security posture.
In short:
Xygeni transforms OSINT from a manual research model into an automated defense layer, delivering continuous, actionable intelligence directly inside DevOps pipelines.
Integrating OSINT Framework into DevSecOps Workflows
Manual intelligence gathering doesn’t scale. Therefore, integrating osint framework based automation within pipelines ensures that security intelligence updates itself as code changes.
Step-by-step integration example:
- Monitor repositories: Run secret-scanning hooks and dependency checks on every commit.
- Correlate findings: Forward results to SIEM, Slack, or Jira using contextual OSINT data.
- Set alerts: Trigger automated responses when new indicators match internal assets.
- Prioritize fixes: Combine SCA and SAST results with reachability and exploitability analysis for smarter remediation.
Moreover, Xygeni’s integrations make these steps seamless, removing the need for manual correlation or external dashboards. As a result, open source intelligence becomes part of every build, merge, and deployment by default.
Challenges and Ethical Considerations
Although OSINT is powerful, it must always be used responsibly. For this reason, teams should:
- Validate sources: Cross-check intelligence to prevent false positives.
- Respect privacy: Stay compliant with GDPR, CCPA, and internal security rules.
- Avoid over-collection: Gather only what’s needed for actionable security insights.
- Maintain integrity: Observe and analyze systems without unauthorized access.
Mini Case Study: Detecting a Leaked Token with OSINT Principles
- Week 1: A DevOps engineer enables Xygeni’s Early Warning integration to monitor GitHub for company references and potential leaks.
- Week 2: The system automatically flags a public repository exposing an AWS key used in a testing pipeline.
- Week 3: Through CI/CD automation, the token is revoked, a secure pull request replaces it, and the incident is logged for audit.
Outcome: The exposure window dropped from 24 hours to less than 15 minutes. In other words, OSINT-driven visibility combined with Xygeni automation turned a potential breach into a non-event.
As a result, this example demonstrates how applying OSINT principles inside DevOps pipelines gives teams the same awareness once limited to dedicated threat-intel analysts.
OSINT vs. Traditional Threat Intelligence
| Aspect | OSINT (Community Driven) | Traditional Feeds (Vendor Driven) |
|---|---|---|
| Data Source | Publicly available information | Proprietary or subscription-based data |
| Cost | Often free / open | Usually commercial |
| Update Frequency | Real-time via APIs and community | Periodic vendor updates |
| Customization | Fully adaptable for DevSecOps pipelines | Limited to vendor API |
| Scope | Broad — covers code, infrastructure, and social data | Focused on known malware or IOC feeds |
Therefore, OSINT complements, not replaces, traditional threat intelligence by filling visibility gaps and adding flexibility for development teams.
Conclusion: The Future of OSINT in AppSec
As the digital attack surface expands, context becomes as important as detection. The osint framework and modern open source intelligence tools provide that context by showing how your organization appears from an attacker’s point of view.
When combined with automation and correlation engines, OSINT delivers real-time awareness that traditional scanners cannot achieve. Meanwhile, modern intrusion detection and prevention systems protect what happens inside your environment, while OSINT protects everything visible outside it, from public code to forgotten domains.
In short, open source intelligence transforms passive monitoring into proactive defense.
About the Author
Written by Fátima Said, Content Marketing Manager specialized in Application Security at Xygeni Security.
Fátima creates developer-friendly, research-based content on AppSec, ASPM, and DevSecOps. She translates complex technical concepts into clear, actionable insights that connect cybersecurity innovation with business impact.








