From 2019 to 2022, the average annual increase in software supply chain attacks exceeded 700%, a growing trend whose economic impact is expected to surpass 80 billion dollars in 2026. Recognizing the severity of this issue, the National Security Agency (NSA) and the Cybersecurity and Infrastructure Security Agency (CISA) released crucial guidelines to secure CI/CD environments, addressing the rising threat of the so called malicious cyber actors (MCAs) exploiting vulnerabilities.
These guidelines specifically focus on preventing the exposure of secrets within CI/CD pipelines and offer specific insights.
What are the most Critical CI/CD security threats?
As the NSA guidelines states, securing a CI/CD environment requires recognizing and defending against various types of security threats that can impact CI/CD operations. Here are some common risks found in CI/CD pipelines, along with the OWASP Top 10 CI/CD Security Risks:
- Insuficient Flow Control Mechanisms: This risk refers to the lack of proper controls to manage the flow of data and tasks in the CI/CD pipeline. Without these controls, unauthorized changes could be introduced into the pipeline, leading to potential security vulnerabilities.
- Inadequate Identity and Access Management: This risk involves not properly managing who has access to the CI/CD pipeline and what they can do. Without proper identity and access management, unauthorized individuals could gain access to the pipeline and introduce malicious changes.
- Dependency Chain Abuse: This risk refers to the potential for attackers to exploit vulnerabilities in the dependencies used by your software. If these dependencies are not properly managed and secured, they could provide an avenue for attack.
- Poisoned Pipeline Execution: This risk involves attackers potentially introducing malicious code into the CI/CD pipeline. This could lead to the execution of malicious code in the production environment.
- Insufficient PBAC (Pipeline-Based Access Controls): This risk refers to the lack of proper access controls based on the pipeline. Without these controls, unauthorized individuals could access sensitive parts of the pipeline.
- Insufficient Credential Hygiene: This risk involves not properly managing and securing credentials used in the CI/CD pipeline. If these credentials are compromised, it could provide an attacker access to the pipeline.
- Insecure System Configuration: This risk refers to potential security vulnerabilities due to
improperly configured systems in the CI/CD pipeline. Attackers could exploit these vulnerabilities. - Ungoverned Usage of 3rd Party Services: This risk involves using third-party services without proper oversight and control. These services could introduce security vulnerabilities if they are improperly managed and secured.
- Improper Artifact Integrity Validation: This risk refers to the lack of proper validation of artifacts produced by the CI/CD pipeline. Without proper validation, malicious or compromised artifacts could be introduced into the production environment.
- Insufficient Logging and Visibility: This risk involves insufficient logging and visibility into the
activities in the CI/CD pipeline. It could be difficult to detect and respond to security incidents without proper logging and visibility
Worst threat scenarios and how to remediate them
Attackers acquire a developer’s credential to access a Git repository:
- Minimize the use of long-term credentials.
- Use two-person rules (2PR) for all code updates.
- Secure user accounts & implement least privilege policies.
- Implement network segmentation and traffic filtering
- SSCS tools such as Xygeni automatically detect misconfigurations in these areas and enforce the application of secure corporate policies.
Supply Chain compromise of an application library, tool or container image in a CI/CD pipeline:
- Restrict untrusted libraries and tools & analyze committed tools.
- Implement EDR tools and auditing.
- Keep CI/CD tools, software and operating systems up-to-date.
- Xygeni platform automatically updates its scanning capabilities in each scanning to detect the latest malicious components that could impact your software release.
Compromise of a CI/CD environment that modifies configurations or inject malicious dependencies:
- Analyze committed code & integrate security scanning in CI/CD.
- Implement SBOM and SCA & implement EDR tools.
- Add signatures to CI/CD config and verify it.
- Xygeni capabilities in analyzing the full set of assets involved in the software development, build and delivery enable the detection of any threat during the CI/CD process and generate the SBOM as evidence for your audit and customers.
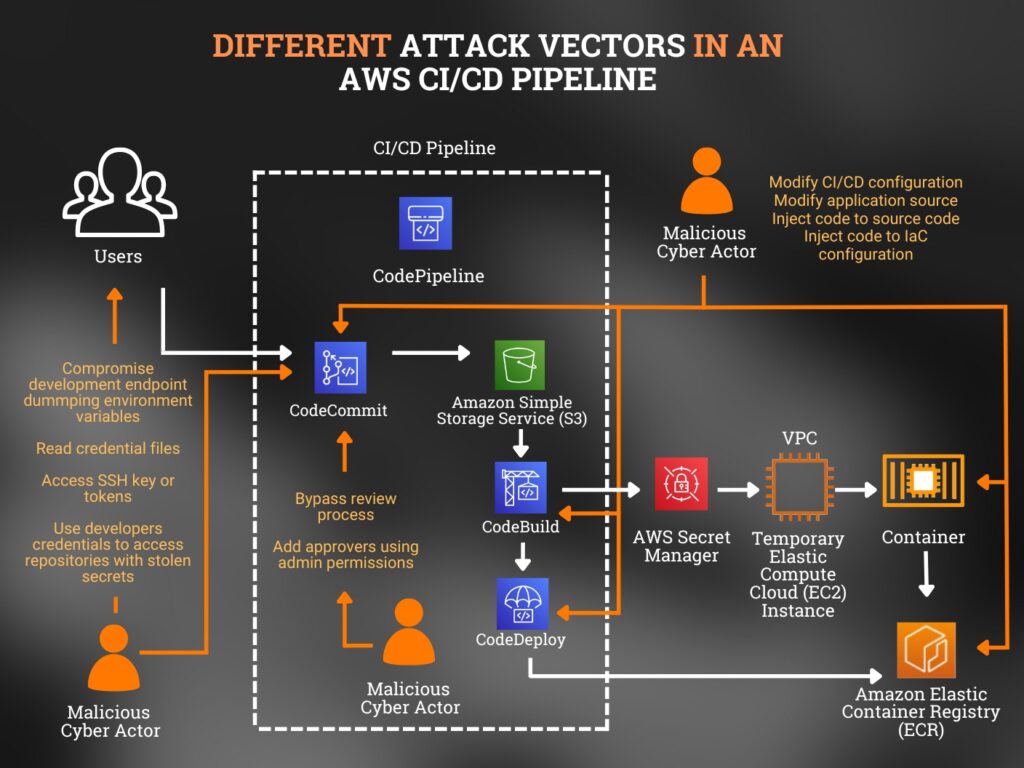
The following image shows different attack vectors using the example of a CI/CD pipeline. These attack vectors are very similar to the ones used in other CI/CD attacks.
Enabling a Genuine Zero Trust Approach:
NSA active hardening Strategies
This guideline list several strategies that could be used to enhance the protection of the Software Supply Chain. Here you can find a brief of the most important ones:
Adopt NSA-recommended cryptography
Using outdated and weak cryptographic algorithms poses significant risks to CI/CD pipelines. It could lead to the exposure of sensitive data, data leaks, compromised authentication, and insecure sessions.
Exploiting these vulnerabilities, malicious actors could bypass the CI/CD pipeline and compromise the software supply chain. To mitigate these risks, the NSA and CISA recommend implementing and configuring robust cryptographic algorithms, such as those specified by the National Institute of Standards and Technology (NIST), when setting up cloud applications and services.
Minimize long-term credential usage
When it comes to human authentication, always prioritize identity federation and security tokens that are resistant to phishing attacks. These measures should be employed to obtain temporary SSH and other keys.
Similarly, for software-to-software authentication, minimising the use of software-based long-term credentials whenever possible is advisable.
Detectors from tools like Xygeni support the detection of any type of credential and secrets in tens of formats along the entire software supply chain: code, pipelines, IaC configurations, etc.
Add signatures to CI/CD configuration and always verify them
Throughout the CI/CD process, regardless of the development stage, it is crucial to ensure that the code is consistently and correctly signed, with the signature being verified.
If the signature fails to validate, to investigate the cause of the validation issue thoroughly.
Mitigate password risks through Multi-Factor Authentication (MFA)
It could also be complemented with role-based access control (RBAC). Nowadays, MFA is commonly used in all kinds of services. It helps to enforce security, while it is applied for both internal and external users.
Following the principle of least privilege, RBAC ensures that users are granted only the necessary permissions required to carry out their specific tasks.
Corporate policies should consider this today’s mandatory configurations. Automated compliance and auditing capabilities of SSCS tools enforce all of them across the entire DevOps infrastructure.
Implement least-privilege policies for CI/CD Access
It is crucial to give access to developers only to the pipelines and components that are directly relevant to their assigned tasks.
Implementing separation of duties is crucial, where developers responsible for checking in source code do not require the privilege to update the build environment. Likewise, engineers overseeing builds do not need read-write access to the source code. For a more detailed guide on implementing security controls, refer to NIST SP 800-53.
Use Two-Person rule (2PR) for code updates
Adhering to the practice of two-person rules not only promotes code quality but also reduces the likelihood of successfully introducing malicious code if a developer’s credentials are compromised.
SSCS tools like Xygeni, usually include a specific check determining whether the project requires code review before pull requests (merge requests) are merged.
This check follows the current Open SSF security standard.
Secure user accounts and secrets
Auditing user accounts and configuring access controls based on the principles of least privilege and separation of duties is critical.
Additionally, secure handling of secrets, tokens, and credentials within the CI/CD pipeline is paramount.
Never transmit secrets in plaintext anywhere in the pipeline, ensuring they are never embedded in software that can be reverse-engineered.
Maintain a comprehensive record of all third-party and open-source components in the codebase by implementing a software bill of materials (SBOM):
The SBOM assists organizations in understanding potential code vulnerabilities and prevent using outdated and unauthorized components. Compliance with regulations, such as FDA requirements for medical devices, may mandate using SBOMs.
Other essential measures during the development process
To identify vulnerabilities, it is crucial to integrate security scanning into the CI/CD pipeline easily. Integration should be considered easy at any step: in the workstation (before the upload), in a commit, or in the nightly build using guard rails.
Maintain Up-to-Date Software, Operating Systems, and CI/CD Tools: Regularly update CI/CD tools, as they may contain bugs and vulnerabilities. Utilize centralized patch management systems, including software integrity and validation processes for operating systems and software updates.
Restrict Untrusted Libraries and Remove Temporary Resources: Only use software, tools, libraries, and artifacts from trusted and secure sources to minimize threats to the CI/CD pipeline. Always ensure its configuration is appropriate to prevent potential code execution or the introduction of backdoors. It is also important to remove unnecessary applications and protect endpoints.
Know more about Xygeni Platform, download Xygeni's platform datasheet








