Modern software development relies heavily on open source software vulnerability scanner solutions to identify security risks. However, many organizations using a vulnerability scanner open source struggle to detect real threats, as these tools often lack advanced risk assessment and prioritization capabilities. While an open source vulnerability scanner software used in cybersecurity helps uncover known vulnerabilities, it does not always provide exploitability analysis, supply chain security insights, or automated remediation options. As a result, security teams relying on an open source vulnerability scanner frequently deal with false positives, alert fatigue, and difficulty distinguishing high-risk vulnerabilities from low-impact ones.
To effectively manage software security, organizations need more than a traditional open source vulnerability scanner—they require a comprehensive security solution that includes real-time detection, reachability analysis, and intelligent risk prioritization. This is exactly what Xygeni’s vulnerability scanning platform provides.
How Open Source Vulnerability Scanner Software is Used in Cybersecurity
Organizations use open source vulnerability scanner software to find security flaws in external dependencies. These tools scan libraries, frameworks, and containerized environments, checking them against publicly available vulnerability databases such as:
While these scanners help find outdated or vulnerable dependencies, they often lack real-time threat intelligence. As a result, security teams using a vulnerability scanner open source struggle to sort threats by urgency, leading to alert fatigue and slower response times.
Where Open Source Vulnerability Scanner Software Used in Cybersecurity Falls Short
Security teams rely on open source vulnerability scanner software used in cybersecurity for different security tasks, but each has clear limitations:
- Software Composition Analysis (SCA): Finds vulnerabilities in open source dependencies but does not check whether the vulnerability can actually be used in an attack.
- Container Security: Scans Docker images and Kubernetes setups for misconfigurations but does not tell if attackers could take advantage of them.
- Network Vulnerability Scanners: Spot system-level weaknesses, but they do not give enough visibility into application dependencies.
- CI/CD Security Checks: Prevent the release of known vulnerabilities, but they do not detect supply chain attacks or hidden risks in dependencies.
Although a vulnerability scanner open source helps find security issues, these tools often produce too many alerts without ranking them by importance. This forces security teams to go through every issue manually, which slows down fixes and increases the chance of missing real threats.
To improve security workflows, organizations need solutions that go beyond a basic open source vulnerability scanner. They need tools with reachability analysis, exploitability scoring, and automated prioritization to make sure security teams focus on the biggest risks first.
The Limitations of Open Source Vulnerability Scanners
1. No Reachability Analysis
Most open source software vulnerability scanners find security issues but do not check if the affected code actually runs in the application. This leads security teams to fix vulnerabilities that pose no real risk and waste valuable time.
Example:
- A scanner detects a high-severity vulnerability in a library.
- However, if the application never calls the vulnerable function, there is no real danger.
- Security teams spend time and effort fixing an issue that does not impact production.
Without reachability analysis, organizations struggle to identify which vulnerabilities truly matter and where to focus their efforts.
2. Too Many False Positives Create Alert Fatigue
Many open source vulnerability scanner software used in cybersecurity produce hundreds of alerts but fail to separate critical vulnerabilities from minor issues. This overload leads to alert fatigue, making it harder for security teams to:
- Focus on the vulnerabilities that attackers can actually exploit.
- Avoid wasting time fixing issues that pose no immediate threat.
- Ensure that the most serious vulnerabilities are fixed first.
What’s missing? Smarter prioritization that ranks vulnerabilities based on real risk instead of just severity scores.
3. No Protection Against Supply Chain Attacks
Traditional vulnerability scanner open source tools only check for known vulnerabilities, but they do not detect malicious dependencies or supply chain attacks.
Some of the biggest threats they fail to catch include:
- Typosquatting & Dependency Confusion – Attackers upload fake versions of popular libraries, tricking developers into installing malicious code.
- Malware in Open Source Repositories – Some packages contain hidden backdoors, which standard scanners do not recognize.
- Zero-Day Threats – If a package is compromised before a CVE is published, traditional scanners will not detect the problem.
Example: A widely used NPM package is infected with malware.
- Traditional scanners do not flag it because no CVE has been assigned yet.
- Xygeni’s Early Warning System monitors open source repositories in real time and blocks malicious dependencies before they can spread.
To effectively manage security risks, organizations need solutions that go beyond a basic open source vulnerability scanner. They require proactive threat detection, real-time monitoring, and better prioritization to focus on the threats that truly matter.
How Xygeni Fixes the Gaps in Open Source Vulnerability Scanning
1. Detecting Vulnerabilities in Your Applications with SAST
Xygeni ensures that every line of code is free from security risks by detecting threats often missed by a vulnerability scanner open source. These include:
- Injection flaws, XSS, CSRF, buffer overflows, and memory management issues.
- Weak authentication and authorization mechanisms.
- Misconfigurations and potential information leaks.
Since traditional open source software vulnerability scanner tools only scan known issues, Xygeni goes further. It blocks vulnerabilities and malware before they reach production, using secure guardrails that prevent exploits at the source.
2. Expanding Open Source Security Beyond CVEs with SCA
Most open source vulnerability scanner software used in cybersecurity focuses only on known CVEs. However, Xygeni takes a broader and proactive approach:
- Detecting risky packages even if they have no assigned CVE.
- Identifying and fixing license risks that could impact compliance.
- Continuously tracking and updating new vulnerabilities before deployment.
- Performing reachability analysis on dependencies, ensuring only vulnerabilities that are actually used in runtime are flagged as critical.
3. Auto-Remediation for Open-Source Dependencies
Most open source vulnerability scanner software used in cybersecurity only detects security risks but does not provide automated fixes. As a result, security teams must manually review and patch vulnerabilities, which slows down remediation efforts and creates bottlenecks in development.
Xygeni eliminates this challenge by offering auto-remediation capabilities. Instead of just flagging risks, Xygeni:
- Automatically upgrades vulnerable open-source dependencies.
- Suggests safe, pre-tested replacements for risky components.
- Generates intelligent pull requests, allowing developers to apply fixes instantly.
By integrating directly into CI/CD workflows, Xygeni ensures that security patches do not disrupt development pipelines. This reduces manual workload, shortens remediation times, and keeps applications secure without slowing innovation.
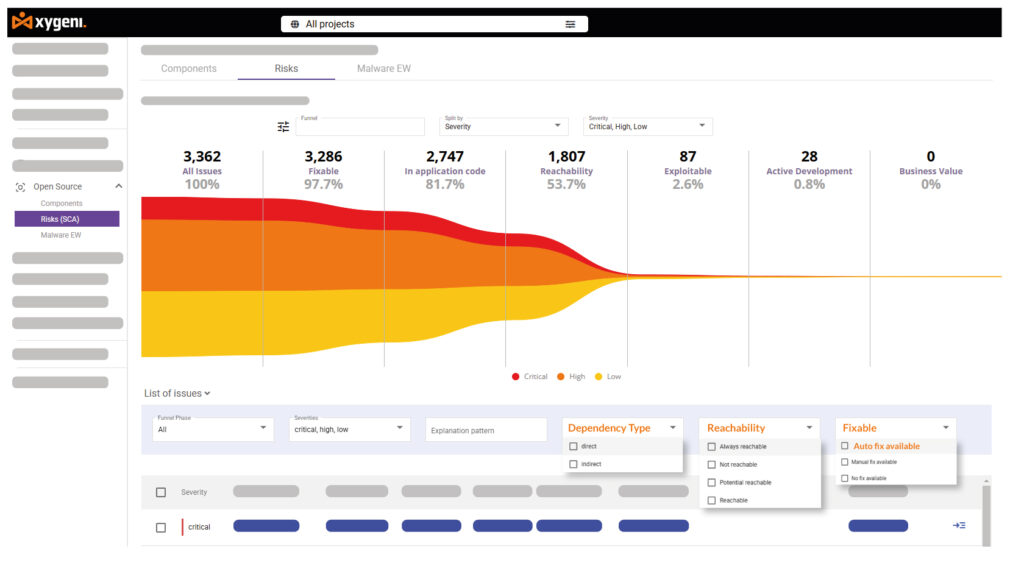
4. Prioritization Funnels: Cutting Through the Noise
Traditional vulnerability scanner open source solutions overload security teams with unfiltered alerts. However, Xygeni makes risk prioritization faster and more accurate by:
- Filtering thousands of alerts into a focused list of top threats.
- Reducing developer fatigue by up to 90%.
- Speeding up remediation by focusing on vulnerabilities that can actually be exploited.
This context-aware prioritization ensures security teams spend time fixing real risks rather than chasing false positives.
5. Securing the Entire Software Supply Chain
Xygeni goes beyond a typical open source software vulnerability scanner by preventing attacks before they happen. It:
- Blocks typosquatting, dependency confusion, and malware-infected libraries.
- Scans for malicious dependencies as soon as they appear.
- Integrates security checks directly into CI/CD pipelines to catch threats earlier.
With Early Warning Systems, Xygeni prevents zero-day threats and ensures organizations stay protected against emerging risks.
Conclusion: Open Source Scanners Alone Are Not Enough
Relying only on an open source software vulnerability scanner leaves serious security gaps that attackers can exploit. Organizations need a more complete approach:
- SAST to secure every line of custom code.
- SCA to detect vulnerabilities beyond CVEs.
- Prioritization Funnels to focus on real threats first.
Xygeni delivers all of this, ensuring that applications remain secure, compliant, and free from vulnerabilities before deployment.
Ready to secure your applications from code to cloud?