Managing vulnerabilities in modern applications is tough. With countless open-source dependencies and Infrastructure as Code (IaC), security teams get slammed with alerts. The problem? Most tools don’t tell you if a vulnerability is actually exploitable, which leads to alert fatigue, wasted time, and endless remediation backlogs. That’s where reachability analysis changes the game—it helps DevOps teams focus on the stuff that really matters. When you combine it with vulnerability prioritization, you get faster, more accurate remediation because false positives are filtered out. And that’s not all—a good reachability analyzer shows you which vulnerabilities are actually reachable, so your team can prioritize real risks and stay aligned with business goals.
In this guide, we’ll break down how reachability analysis works, why vulnerability prioritization is a must, and how Xygeni’s reachability analyzer can help reduce noise and zero in on the risks that actually matter.
How Reachability Analyzers Help Reduce False Positives
Traditional Software Composition Analysis (SCA) tools detect vulnerabilities by scanning your project’s dependency tree and comparing it to databases like the National Vulnerability Database (NVD). That sounds great—until you realize it’s missing something big. These tools don’t check if the flagged vulnerabilities are reachable in your app. Without that context, you’re left with tons of alerts but no idea which ones are real risks.
Here’s the key question reachability analysis answers:
Is the vulnerable code reachable by your application’s runtime execution?
If the answer is no, you can relax—it’s not an immediate problem. But if the answer is yes, it’s a reachable vulnerability that needs attention fast. This is what makes reachability analysis so powerful—it cuts through the noise, helping your team focus on what matters.
Types of Reachability Analysis Explained
Not all reachability analysis is created equal. Depending on how deep the analysis goes, it can give you different levels of accuracy and insight. Knowing which type you’re dealing with is key to making smart decisions and staying on top of actual risks.
1. Code-Level Reachability: Finding Vulnerabilities at the Code Level
Code-level reachability is the most detailed and accurate type of analysis. It checks your application’s call graph to determine if a specific vulnerable function is directly or indirectly invoked. This method is extremely precise, helping your team avoid no necessary noise by focusing on real execution paths.
How It Works:
- The tool scans your entire codebase and identifies whether your application calls a vulnerable method inside a dependency.
- If the method appears in any call chain, it gets flagged as reachable and demands immediate attention.
Example:
- Vulnerability: CVE-2014-6071 in jQuery affects the text() method when used with after().
- Code-Level Reachability Analysis: If your app doesn’t use after() with text(), the vulnerability is not reachable, and you can safely deprioritize it. However, if text() exists in your call graph, it becomes a critical risk that requires a quick fix.
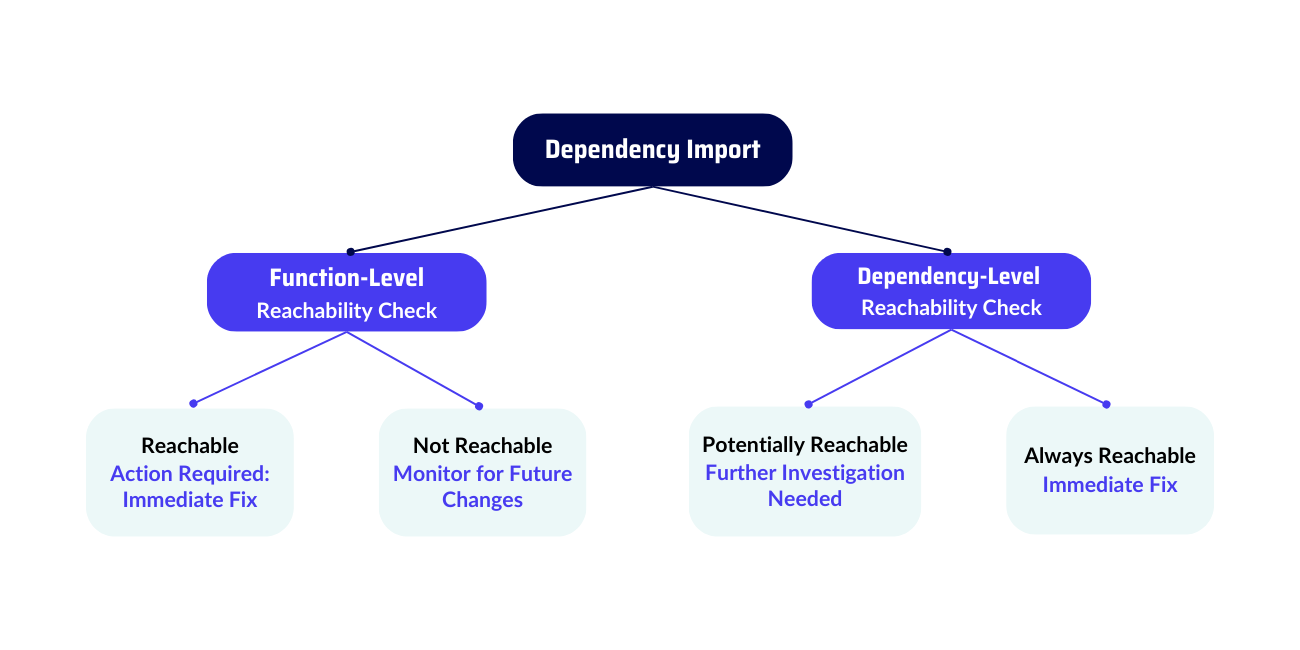
2. Dependency-Level Reachability
Dependency-level reachability takes a broader approach. Instead of analyzing individual functions, it checks whether your application uses the dependency itself. Although this method is less precise than code-level analysis, it’s useful for understanding potential risks from vulnerable components.
How It Works:
- The tool flags a dependency as potentially reachable if it’s imported into your code—even if the vulnerable function isn’t called.
Example:
- Library: Your project uses a logging library with a known vulnerability.
- Analysis: If you’re only using basic logging and not the advanced feature where the vulnerability exists, the risk is much lower. Still, it’s a good idea to monitor this dependency.
3. Always Reachable vs. Not Reachable
Always Reachable
A vulnerability is flagged as always reachable if it lives in a critical part of the dependency that runs every time your application starts. These are high-priority issues that must be fixed right away.
Example:
A vulnerability in an initialization method that executes at every application startup is always reachable and poses an inherent risk.
Not Reachable
On the other hand, a vulnerability is not reachable if there’s no direct or indirect call to the vulnerable function. Although it isn’t an immediate problem, you should keep an eye on it. Future code changes might introduce a path to the vulnerable code.
Example:
A vulnerability in a rarely used API endpoint may seem irrelevant if your app doesn’t call it. However, adding a new feature could non intentionally create a path to that vulnerable function.
Why These Types of Reachability Matter
- Code-Level Reachability delivers accuracy by detecting vulnerabilities directly invoked by your app.
- Dependency-Level Reachability ensures a broader layer of protection by monitoring the imported libraries.
- Always Reachable vulnerabilities should be fixed immediately, while Not Reachable vulnerabilities can reduce unnecessary alerts and help focus your remediation efforts.
By combining these approaches, you can reduce alert fatigue, focus on real risks, and maintain a proactive security posture.
Why Reachability Analysis Transforms Vulnerability Prioritization
1. Improved Prioritization
Prioritizing vulnerabilities based on reachability is more accurate than severity alone. A low-severity reachable vulnerability could be far riskier than a critical vulnerability that’s not reachable.
Example:
- A critical vulnerability in a rarely used feature might not require immediate remediation.
- Meanwhile, a low-severity vulnerability in a frequently used function could pose a much greater risk.
2. Reduces False Positives
By spotting which vulnerabilities can be reached and which can’t, reachability analysis cuts out unneeded alerts and helps your team focus on real risks.
3. Optimizes Developer Time
Less time chasing phantom vulnerabilities means more time spent fixing real issues. This keeps developers productive and reduces security-related frustrations.
4. Aligns with Business Objectives
Not every vulnerability is equally important. Reachability analysis lets organizations focus on the risks that matter most to the business, making sure they protect key services and sensitive data.
5. Adapts to Code Changes
Vulnerabilities that are not reachable today may become reachable as your code evolves. Continuous reachability analysis provides a real-time view of changing risks, letting you to act before a threat becomes exploitable.
Real-Time Reachability for Smarter Vulnerability Prioritization
Traditional prioritization methods rely primarily on severity, which isn’t always the best approach. Reachability-driven prioritization adds real-world context to your security strategy:
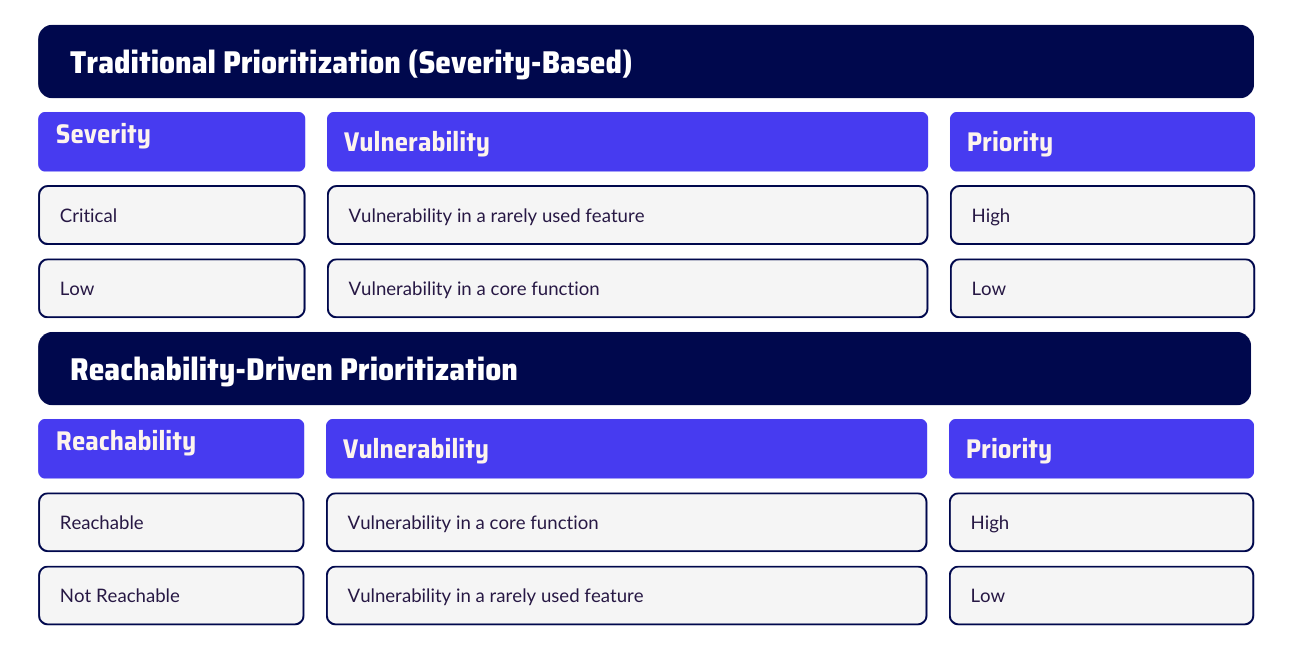
When it comes to vulnerability management, reachability-based prioritization offers a far more realistic and accurate risk assessment compared to traditional methods. Unlike severity-based models, which treat every critical vulnerability as urgent, reachability-driven prioritization focuses on actual exploitability. This approach ensures that security teams tackle real risks first, without wasting time on vulnerabilities that might never affect the application.
As a result, By focusing on reachable vulnerabilities, your team can make faster decisions and skip no necessary fixes. The main difference is ranking vulnerabilities based on how they’re actually used, not just how serious they seem.
Real-World Impact of Reachability Analysis
Organizations that adopt reachability analysis often experience dramatic improvements in both efficiency and security focus. Here’s what many teams achieve:
- 70% reduction in false positives, which significantly cuts unimportant alerts and enables security teams to focus on real risks.
- 30% faster remediation times, letting developers to concentrate on actionable vulnerabilities instead of sifting through noise.
- Higher developer engagement, creating a stronger security culture and building better collaboration between security and development teams.
Ultimately, reachability analysis improves accuracy and builds developer trust in security tools, making sure that teams remain engaged and aligned with long-term security strategies.
Conclusion: Reachability Analysis Transforms SCA
Reachability analysis transforms Software Composition Analysis (SCA) from a reactive tool that simply lists vulnerabilities into a proactive security management strategy. By focusing on exploitable vulnerabilities, organizations can reduce noise, save time, and significantly improve their security posture.
Xygeni’s Reachability Analyzer: Real-Time, Accurate Prioritization
At the heart of Xygeni’s approach is its reachability analyzer, which uses detailed code-level checks and real-time insights. Unlike traditional SCA tools that flag every possible vulnerability, Xygeni focuses only on the ones that truly matter. It does this by checking reachability, exploitability, and business context, helping security teams focus on what’s most important.
As a result, by combining real-time reachability analysis with smart focus, Xygeni cuts false positives by up to 70%. This helps teams focus on actual risks and fix issues faster.
How Xygeni’s Reachability Analysis Works
Xygeni doesn’t just identify vulnerabilities in third-party components; it goes deeper by analyzing how these components are used within your application. This enables you to differentiate between vulnerabilities that are simply present and those that are actively exploitable.
Key Features of Xygeni’s Reachability Analyzer:
- Call Graph Tracing: Scans direct and indirect call graphs across both direct and indirect dependencies, ensuring vulnerabilities are accurately traced throughout the full dependency tree.
- Continuous Monitoring: Updates in real-time as your code evolves, immediately flagging newly reachable vulnerabilities.
- CI/CD Integration: Identifies and prioritizes vulnerabilities at build time, making sure they’re addressed early and never reach production.
Contextual and Prioritized Vulnerability Management
Not all vulnerabilities carry the same risk. Xygeni’s Application Security Posture Management (ASPM) ensures vulnerabilities are sorted based on business context and exploitability, not just severity. This helps teams focus on risks that directly impact critical services or sensitive data.
Xygeni’s Context-Aware Prioritization Factors:
- Exploitability: Prioritize vulnerabilities with known exploits or active targeting.
- Business Impact: Focus on vulnerabilities that could disrupt essential operations or expose sensitive data.
- Reachability: Addresses vulnerabilities only if they are invoked at runtime within in-app-code execution. If a vulnerability exists but is never used by the application, it poses no immediate risk. This ensures remediation efforts focus only on real threats that affect production.
Continuous Monitoring and CI/CD Integration
Xygeni’s reachability analyzer does more than standard SCA tools by constantly checking public registries for malware and vulnerabilities. Its Early Warning System spots harmful code in open-source packages as soon as they’re published. Reachable vulnerabilities are dealt with right away, cutting exposure time and keeping your application safe.
Dependency Mapping and Visual Reachability
Xygeni goes beyond basic dependency detection, giving teams a clear view of how different components interact and whether they introduce security risks. Instead of blindly flagging every imported dependency, Xygeni checks if the application actively uses it, either by calling it directly in the source code or through another package.
Example:
A development team adds a third-party library to their project.
- If no part of the application calls any function from that library—not even through another dependency—then it doesn’t pose a security risk.
- Traditional security tools would still flag vulnerabilities in that library, wasting time on non necessary fixes. Xygeni, however, recognizes that unused dependencies aren’t real threats.
How Xygeni Evaluates Reachability at Different Levels
1. Code-Level Reachability: Spotting Real Risks
At the code level, Xygeni checks whether your application actually calls a vulnerable function, either directly or through another library. If no part of your code invokes it, the vulnerability isn’t reachable and doesn’t need immediate attention.
Example:
A development team uses a popular library that contains a vulnerable function.
- If the application never calls this function, the vulnerability remains inactive, so it doesn’t require remediation.
- However, if the function is actively used, then it’s a real risk that needs to be fixed quickly.
By focusing on real execution paths, Xygeni filters out false positives so security teams concentrate only on threats that matter.
2. Dependency-Level Reachability: Looking Beyond Imports
Most SCA tools assume that if a dependency exists in a project, then its vulnerabilities are a risk—but that’s not always true. Xygeni digs deeper by analyzing whether the application actually uses the dependency, either in its source code or through another package.
Example:
A development team adds a third-party library, but no part of the application uses it, and no other dependency calls it either.
- Even though the library contains vulnerabilities, they can’t be exploited because nothing in the application triggers them.
- Unlike traditional SCA tools that flag every imported package, Xygeni knows that unused dependencies don’t introduce real risks.
Additionally, some dependencies exist only in testing environments and never make it to production. Even if they contain vulnerable functions, they can’t be exploited since the application never executes them in a live environment.
By separating used from unused dependencies, Xygeni removes false positives, helping security teams focus on real risks instead of chasing no necessary fixes.
3. Always Reachable vs. Not Reachable: Prioritizing What Matters
Always Reachable
A vulnerability is always reachable if it exists in a critical part of a dependency that executes automatically every time the application starts. These vulnerabilities must be fixed immediately.
Example: A vulnerable function inside an application’s initialization process runs every time the app starts. Since this function always executes, the vulnerability needs immediate attention.
Not Reachable
A vulnerability isn’t reachable if there’s no execution path leading to it. However, security teams should monitor it, as future code changes could make it exploitable.
Example: A vulnerability in an API endpoint might not seem like a risk today. But if a new feature starts calling that endpoint, the vulnerability could become a real problem.
Why These Types of Reachability Matter
- Code-Level Reachability delivers accuracy by detecting vulnerabilities directly invoked by your app.
- Dependency-Level Reachability ensures a broader layer of protection by monitoring the imported libraries.
- Always Reachable vulnerabilities should be fixed immediately, while Not Reachable vulnerabilities can reduce unnecessary alerts and help focus your remediation efforts.
By combining these approaches, you can reduce alert fatigue, focus on real risks, and maintain a proactive security posture.
Why Reachability Analysis is Critical for SCA and Security Prioritization
Modern development teams rely heavily on Software Composition Analysis (SCA) to manage the security of open-source dependencies. However, the sheer number of vulnerabilities in third-party components can quickly overwhelm security teams. This flood of alerts leads to alert fatigue, wasted resources, and remediation backlogs. This is where reachability analysis changes the game—it helps organizations focus only on vulnerabilities that truly matter.
The Problem with Traditional SCA
Traditional SCA tools scan your project’s dependency graph and compare it to public databases like the National Vulnerability Database (NVD). While this offers broad coverage, it doesn’t answer a crucial question:
Is this vulnerability actually exploitable in your application?
Without this context, security teams end up with:
- Thousands of alerts that may not pose any real threat.
- High false-positive rates, leading developers to ignore alerts.
- Huge remediation backlogs, wasting time and resources.
Why Reachability Analysis is a Game-Changer
Reachability analysis adds the missing context by checking whether a vulnerable function is actually invoked in your app. This insight helps teams cut false positives and prioritize risks that really matter.
Key Benefits of Reachability Analysis
1. Improved Prioritization
Prioritizing vulnerabilities based on reachability is more accurate than severity alone. A low-severity reachable vulnerability could be far riskier than a critical vulnerability that’s not reachable.
Example:
- A critical vulnerability in a rarely used feature might not require immediate remediation.
- Meanwhile, a low-severity vulnerability in a frequently used function could pose a much greater risk.
2. Reduces False Positives
By distinguishing between reachable and unreachable vulnerabilities, reachability analysis eliminates unnecessary alerts and helps your team focus on real threats.
3. Optimizes Developer Time
Less time chasing phantom vulnerabilities means more time spent fixing real issues. This keeps developers productive and reduces security-related frustrations.
4. Aligns with Business Objectives
Not every vulnerability is equally important. Reachability analysis lets organizations focus on the risks that matter most to the business, ensuring they protect key services and sensitive data.
5. Adapts to Code Changes
Vulnerabilities that are not reachable today may become reachable as your code evolves. Continuous reachability analysis provides a real-time view of changing risks, allowing you to act before a threat becomes exploitable.
How Reachability Analysis Enhances Security Prioritization
Traditional prioritization methods rely primarily on severity, which isn’t always the best approach. Reachability-driven prioritization adds real-world context to your security strategy:
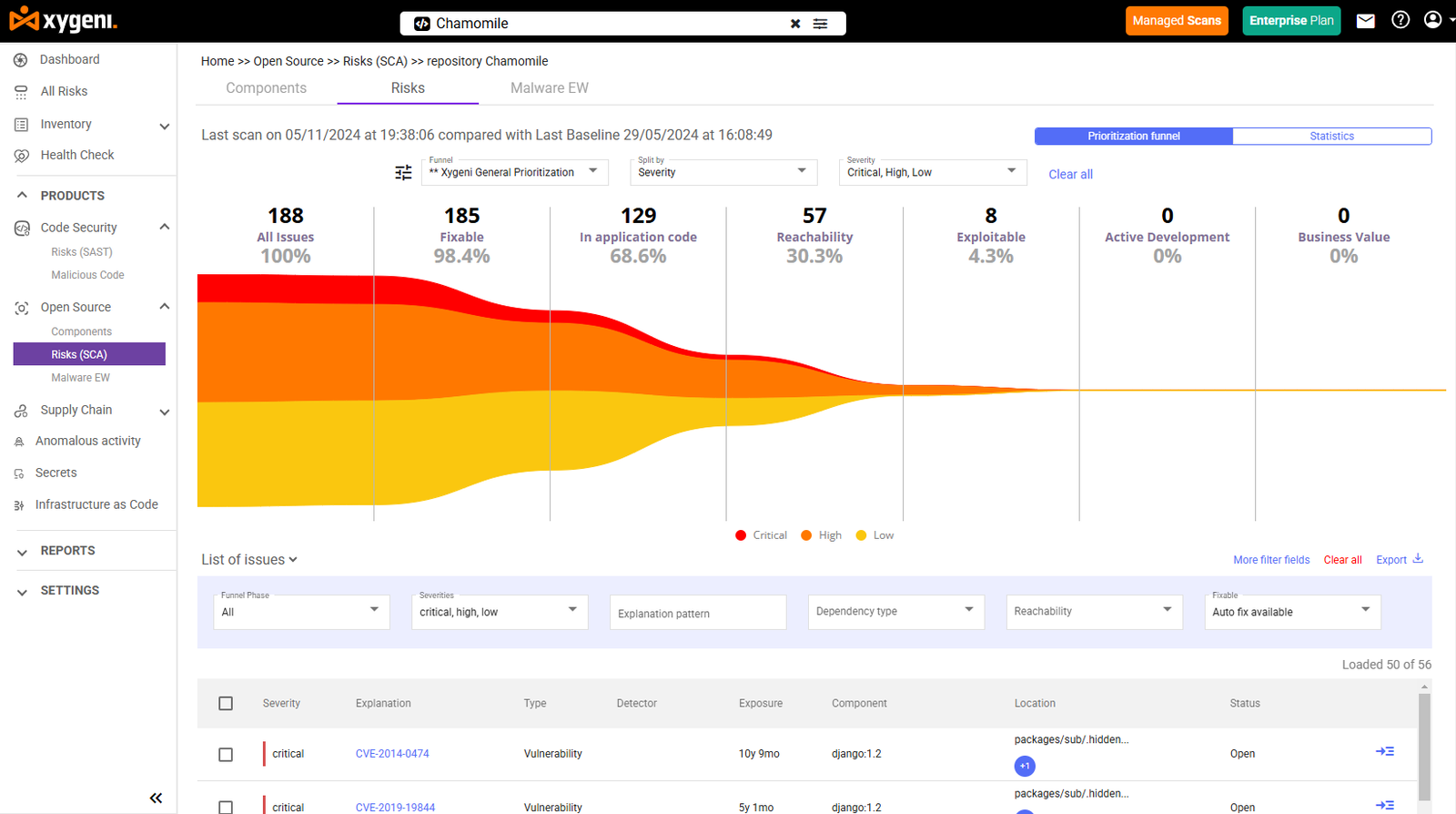
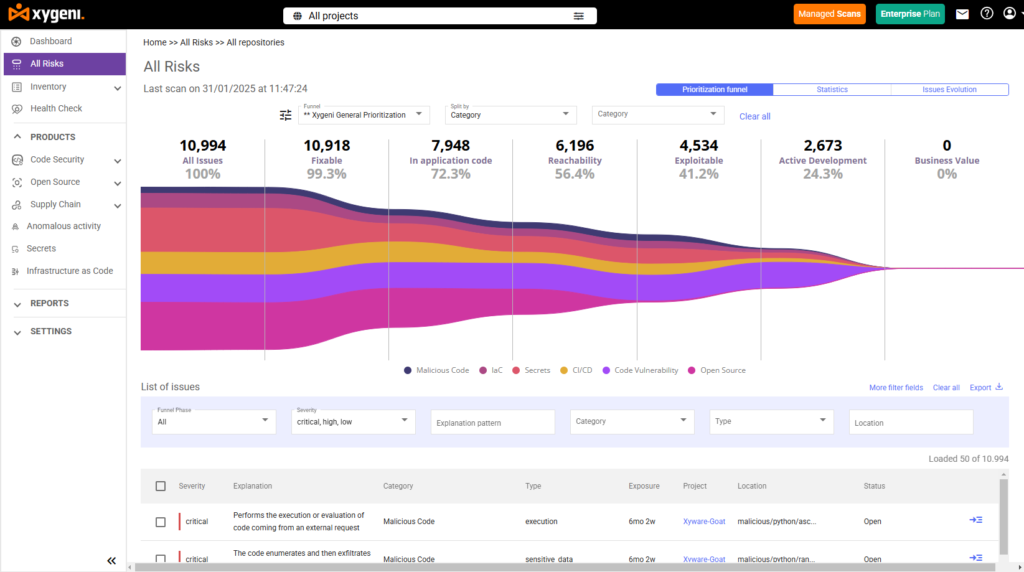
Handling thousands of vulnerabilities without proper focus can overwhelm any team. Xygeni’s reachability analyzer and Prioritization Funnels simplify the process by sorting large datasets and focusing on what matters most. Teams can drill down into reachability, business impact, and exploitability while customizing criteria to fit their unique needs.
In just a few steps, your team can transform thousands of alerts into a short, actionable list of critical vulnerabilities.
How Fintonic Reduced False Positives and Accelerated Remediation
Xygeni’s Prioritization Funnels offer predefined filters for SCA, SAST, IaC Security, CI/CD Security, and Secrets Management. These filters help teams quickly identify high-risk vulnerabilities while minimizing distractions.
How It Works (Real-World Example):
- Initial Dataset: 8,450 issues identified across multiple scans (SCA, CI/CD, IaC, Secrets).
- Step 1: Apply the Reachability Filter → Reduced to 1,200 reachable vulnerabilities.
- Step 2: Add the Business Impact Filter → Further narrowed to 329 actionable vulnerabilities.
Fintonic Use Case:
Fintonic, a leading financial services platform, faced similar challenges. Traditional SCA tools flooded their security team with thousands of alerts, most of which were no relevant. This led to alert fatigue, slow remediation times, and developer burnout.
By integrating Xygeni’s reachability analyzer and using Prioritization Funnels, Fintonic reduced false positives by 70% and cut prioritization time by 90%. As a result, their security team could focus on real risks, work more effectively, and build stronger trust in security processes.
Why Xygeni’s Reachability Analysis is a Game-Changer
Noise Reduction
Traditional security tools generate overwhelming alerts, most of which are irrelevant. Xygeni’s reachability analyzer filters out vulnerabilities that aren’t exploitable, reducing alert fatigue and helping your team focus on real threats.
Enhanced Accuracy
Combining code-level reachability analysis with real-world context, Xygeni reduces false positives by up to 70%. This helps your team move faster, eliminating hours of manual triage and enabling faster remediation.
Continuous Monitoring and Adaptability
As your application evolves, previously unreachable vulnerabilities may become exploitable. Xygeni’s continuous monitoring keeps your team ahead of new risks by updating the call graph in real time and flagging threats as they emerge.
Integration with Xygeni’s Full Security Suite
Xygeni’s reachability analyzer integrates seamlessly into your entire security stack, providing comprehensive protection across multiple domains:
- SCA: Continuous monitoring of open-source dependencies.
- CI/CD Security: Real-time vulnerability detection at every build stage.
- SAST: Prioritize vulnerabilities in proprietary code.
- IaC Security: Detect and remediate misconfigurations before deployment.
Ready to Experience Xygeni’s Reachability Analyzer in Action?
If you’re ready to cut through the noise and focus on real risks, Xygeni’s reachability analyzer is here to help:
- Request a Personalized Demo to see how Xygeni fits into your workflow.
- Read Our Guide to Prioritization Funnels for practical tips on smarter vulnerability management.
- Start a Free Vulnerability Assessment and discover how reachability analysis can boost your team’s efficiency.