Downtime caused by Distributed Denial-of-Service (DDoS) attacks poses a significant threat to businesses of all sizes, leading to lost revenue, reputational damage, and disruption of essential services. If you’re wondering what is a DDoS attack and how does it work, the answer is that these attacks overwhelm target systems with illegitimate traffic, preventing legitimate users from accessing critical resources. To effectively combat this growing threat, a clear understanding of DDoS attacks is essential.
Definition:
What is a DDoS Attack? #
A Distributed Denial-of-Service (DDoS) attack disrupts the availability of a server, network, or online service by overwhelming it with excessive traffic from multiple sources. This malicious flood of traffic, often orchestrated via a botnet, exhausts the target’s resources, leaving legitimate users unable to access it.
How Do DDoS Attacks Work? #
Distributed Denial-of-Service attacks exploit system vulnerabilities and resource limitations. Here’s how they typically work:
- Botnet Deployment: Attackers gain control of numerous devices, forming a botnet.
- Traffic Overload: The botnet floods the target with traffic using protocols like HTTP or UDP.
- Service Disruption: The target slows or crashes, leading to downtime.
Types of DDoS Attacks #
1. Volume-Based Attacks #
- UDP Floods: Overwhelm the target with User Datagram Protocol packets.
- DNS Amplification: Exploit DNS servers to amplify attack traffic.
- ICMP Floods: Use ping requests to exhaust resources.
2. Protocol Attacks #
- SYN Floods: Exploit the TCP handshake to overload the server.
- Ping of Death: Send oversized packets to crash systems.
- Smurf Attacks: Use spoofed ICMP packets to flood a network.
3. Application Layer Attacks #
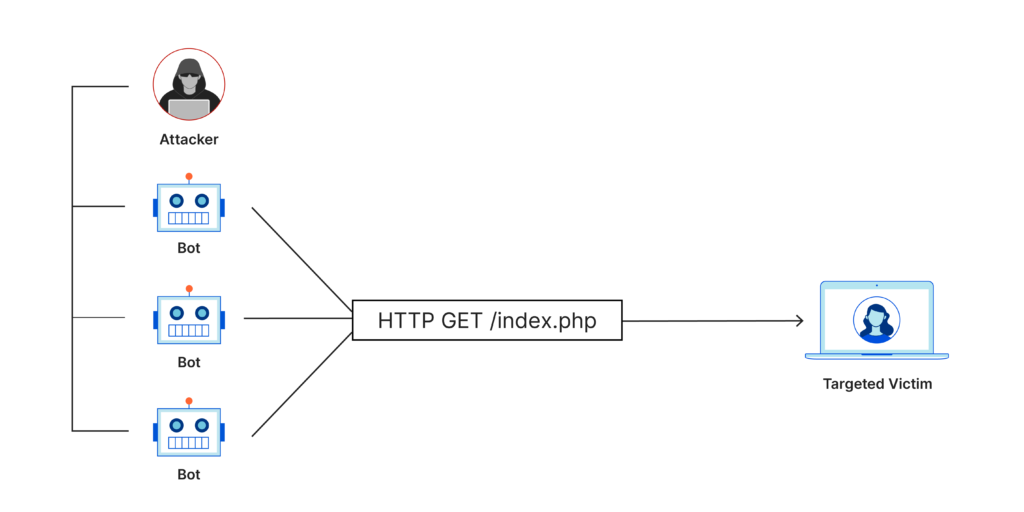
- HTTP Floods: Overload servers with HTTP requests.
- Slowloris: Exhaust resources by keeping connections open.
DDoS Attacks and Their Secondary Impacts #
- Diversionary Tactics: Attackers often use this types of attacks to distract IT teams while launching other attacks, such as ransomware or data breaches.
- Economic Loss: Prolonged downtime can cost businesses $218,000 per hour on average (Ponemon Institute).
- Industries at Risk: Sectors like finance, e-commerce, and healthcare are frequent targets due to their reliance on uptime.
How Xygeni Helps Prevent DDoS Attacks #
Xygeni’s Application Security Posture Management (ASPM) offers advanced capabilities for Distributed Denial-of-Service protection:
- Real-Time Monitoring: Detects unusual traffic patterns indicating Distributed Denial-of-Service activity.
- Anomaly Detection: Identifies and blocks irregular behaviors across network layers.
- Dynamic Risk Prioritization: Highlights vulnerabilities most susceptible to DDoS exploitation.
- SSCS for CI/CD Security: Protects CI/CD pipelines from being compromised and used to build botnets, stopping DDoS threats at their source.
Best Downtime caused by Distributed Denial-of-Service Mitigation Strategies #
Content Delivery Networks (CDNs): Distribute traffic across multiple servers, reducing pressure on any single system.
Blackholing: Redirects malicious traffic to a null route to isolate it.
Sinkholing: Sends attack traffic to a controlled environment for analysis.
Rate Limiting: Caps request volumes to prevent overloads.
Web Application Firewalls (WAFs): Blocks application-layer attacks.
FAQs #
Q1. What are common motivations for attackers targeting small businesses with DDoS attacks?
A: Small businesses often have weaker defenses. Motivations include ransom demands (ransom DDoS), disruption of competitors, or ideological reasons.
Q2. What are the best methods to mitigate DDoS attacks?
A: Effective Distributed Denial-of-Service mitigation requires a multi-layered approach combining several strategies:
- Key Techniques: Blackholing, sinkholing, rate limiting, and using tools like CDNs and WAFs.
- Comprehensive Solutions: Platforms like Xygeni’s ASPM offer proactive, integrated protection tailored to enterprise needs, ensuring layered defense against modern DDoS threats.
Q3. Can DDoS attacks target specific applications?
A: Yes, application-layer DDoS attacks like HTTP floods target specific services to exhaust resources and disrupt operations.
Protect Your Business from DDoS Threats #
Xygeni provides comprehensive Distributed Denial-of-Service protection with advanced features like real-time monitoring, anomaly detection, and CI/CD pipeline security. Ensure business continuity and maintain customer trust.
👉 Book a Demo Now to secure your organization today.


