In modern software development, 95% of vulnerabilities in open-source software come from transitive dependencies. These indirect connections introduce hidden risks that often go unnoticed. But what is a transitive dependency software? It’s an indirect link inherited through other packages, potentially exposing your application to security vulnerabilities. These unseen components can become weak points, making your software more vulnerable to cyberattacks. Understanding and securing this aspect of your software is crucial for maintaining a stable and protected environment.
Definitions:
What is Transitive Dependency? #
Is an indirect dependency that your project inherits from another package. For example, if your project relies on Library A, and Library A depends on Library B, Library B becomes a transitive dependency. These unseen dependencies can accumulate as each library or module brings its own set of dependencies, making your software harder to monitor and secure.
How Transitive Dependencies Work #
Let’s look at a simple example:
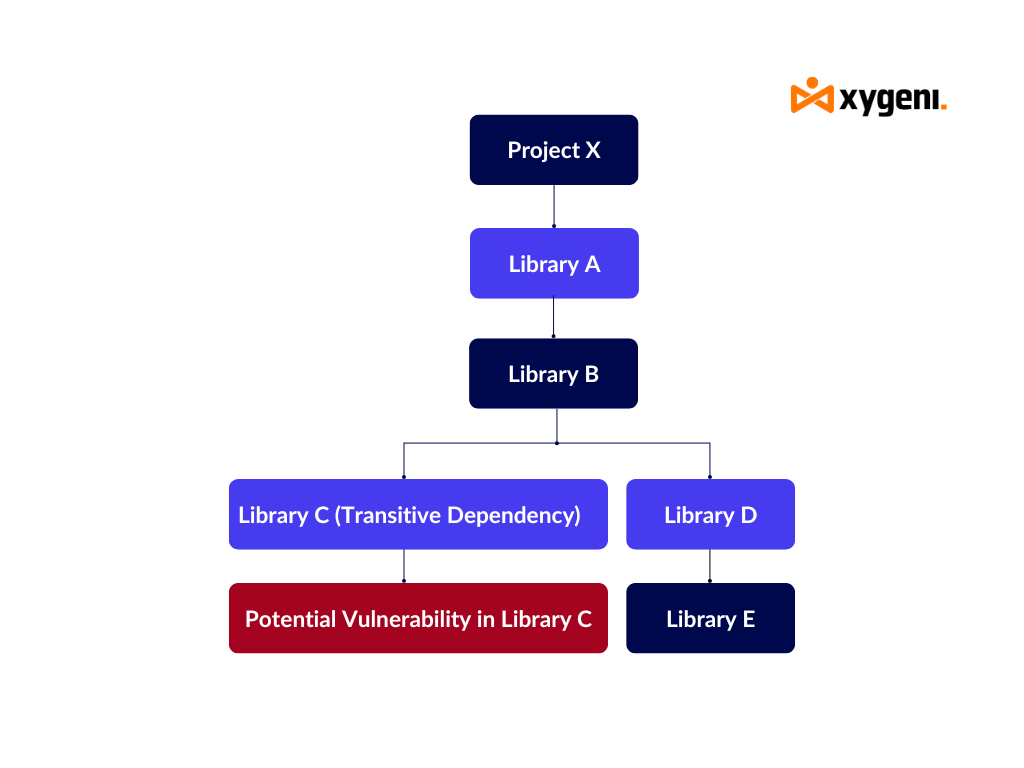
- Project X depends on Library A for basic functionalities like logging.
- Library A itself depends on Library B for additional utility functions.
- Library B uses Library C for configuration parsing.
In this scenario:
- Library C is a transitive dependency software of Project X through Library A and Library B.
- If Library C contains a vulnerability, it could potentially impact the entire project, even though Project X’s developers may not even be aware of Library C‘s existence.
- Let’s extend this:
- If Library C is outdated or maintained poorly, it might harbor vulnerabilities that have been patched in newer versions. However, because it’s buried within Library A‘s and Library B’s dependencies, it might be overlooked during security audits.
- Worse yet, attackers can exploit this “hidden” path by targeting vulnerabilities in widely used transitive dependencies that aren’t directly controlled by the developer.
These chains of indirect connections grow longer and more complex in larger software projects, increasing the potential attack surface and making security oversight more difficult. Attackers can exploit these hidden paths by targeting vulnerabilities in commonly used but less visible components.
Why Transitive Dependencies Matter #
- Hidden Vulnerabilities:
Transitive dependencies introduce unseen vulnerabilities because they aren’t directly controlled or scrutinized by developers.These risks are often left unchecked, making them prime targets for cyberattacks. - Increased Complexity and Risk:
Managing indirect software connections adds layers of complexity. Each additional layer increases the risk of outdated or insecure code entering your project. For instance, you may patch a vulnerability in Library A, but if Library C remains exposed, your project is still at risk. - Regulatory Compliance:
Regulatory frameworks like NIST’s SBOM require organizations to maintain visibility over all software components, including transitive dependencies. Failing to track them can lead to compliance failures. Comprehensive monitoring is critical to meeting these standards.
How to Manage Transitive Dependencies #
- Identify Transitive Dependencies:
Use tools like Xygeni’s Software Composition Analysis (SCA) to map your entire dependency tree, including both direct and transitive dependencies. This transparency provides a clear view of the packages your project relies on, reducing risks. - Fix Vulnerabilities:
After identifying vulnerabilities, Xygeni’s platform offers guidance on patching or upgrading vulnerable packages within your transitive dependencies. Proactive remediation ensures these hidden issues don’t escalate into major security threats. - Remove Unnecessary Dependencies:
By analyzing your components graph, Xygeni helps identify and remove redundant or unnecessary transitive dependencies. This reduces your attack surface and simplifies security updates.
Securing Transitive Dependencies with Xygeni #
Real-Time Monitoring and Malware Detection: #
Xygeni’s Open Source Security (OSS) platform continuously scans both direct and transitive dependencies for vulnerabilities. It detects malicious packages in public registries like NPM, Maven, and PyPI, quarantining affected packages before they compromise your system. Xygeni’s alerts notify your security team in real time.
Context-Aware Vulnerability Prioritization: #
Not all vulnerabilities are equally critical. Xygeni’s Application Security Posture Management (ASPM) prioritizes vulnerabilities based on factors like exploitability, reachability, and potential business impact. This ensures your team focuses on the most dangerous vulnerabilities first.
Complete Dependency Mapping: #
Xygeni’s Dependency Mapping provides a comprehensive visual representation of how all your components interact. This detailed mapping informs decisions about patching, upgrading, or removing unnecessary dependencies.
Code-Level Protection: #
Xygeni’s Code Security solution scans for malicious code within your application, ensuring even code introduced through transitive dependencies is threat-free. It detects threats like backdoors and ransomware before they enter production, complementing your existing static analysis tools (SAST).
Secure Your Project with Xygeni #
So, now you know what is transitive dependency. With Xygeni’s real-time monitoring, proactive threat detection, and comprehensive security tools, you can protect every layer of your software stack. Contact us today to book a demo and secure your supply chain!
Book a demo today to discover how Xygeni can transform your approach to software security.

Frequently Asked Questions #
Partial dependency occurs when a non-primary attribute is functionally dependent on part of a composite primary key, rather than on the whole key, leading to redundancy.
Use tools like Xygeni’s Open Source Security platform to detect and fix vulnerabilities in the software packages your project relies on. These tools provide automated guidance on how to patch or upgrade affected components before they escalate into security risks.
Analyze your dependency tree to see which package introduces it. Update or refactor your code to eliminate it without breaking functionality. Xygeni’s platform helps visualize and manage these relationships.
Use Maven’s command mvn dependency:tree to check for transitive dependencies. This command displays a full hierarchy of your project’s dependencies. Xygeni integrates with Maven to provide deeper security insights.
In order to safely upgrade transitive dependencies, you can start by using tools to map your dependency tree. Then you will be able to identify which package needs updating. Tip: always backup your code before making changes. Try standard update commands first. If that doesn’t resolve the issue, override or pin the specific version in your configuration files. If necessary, you can install the dependency directly. Finally, you only have to run tests to make sure nothing breaks, document the change, and keep monitoring for new vulnerabilities.

