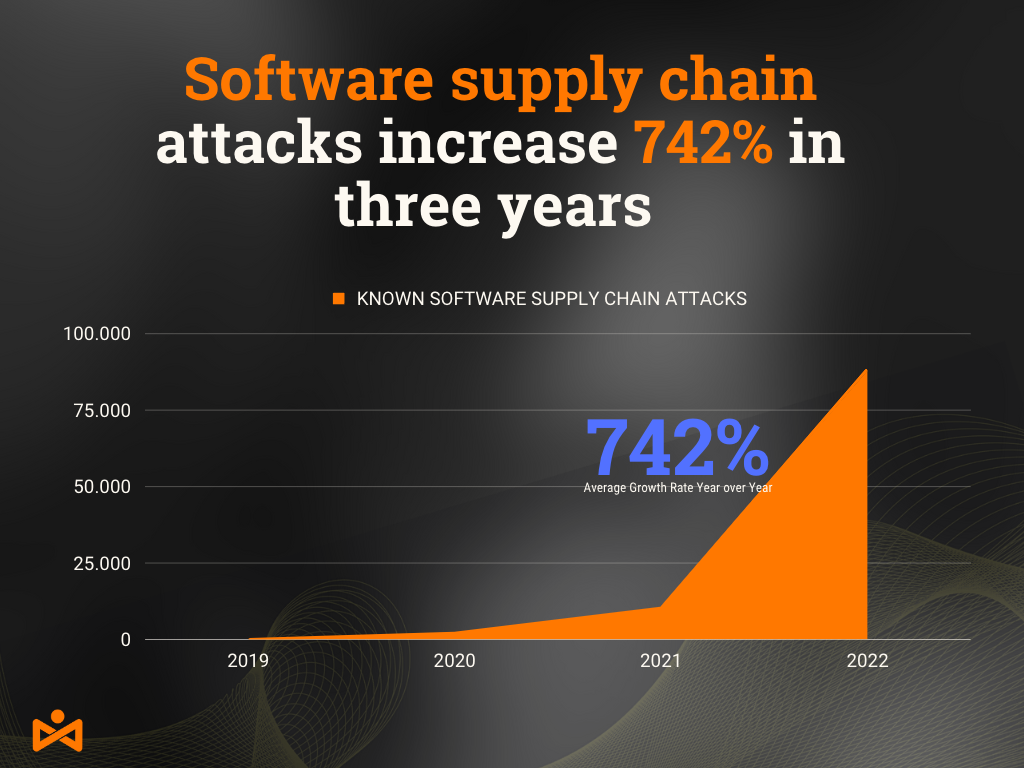
This complexity means numerous avenues exist for attackers, including open-source software repositories. According to GitHub, 85-97% of enterprise codebases come from open-source repositories. Npm and PyPI repositories have seen a 300% increase in attacks over the past four years.
For example, IconBurst is a prime illustration of today’s prevalent software supply chain attacks. Downloaded over 17,000 times, It was a powerful attack that occurred last year involving over 24 typosquatting packages on npm. Therefore, organizations must understand software supply chain attacks and take steps to secure their DevOps ecosystem.
New Approaches
Organizations seeking to secure their software supply chains must select the appropriate tools. However, most secure development and application security testing (AST) technologies do not comprehensively cover all supply chain threats.
While dynamic or static application security testing (DAST/SAST) is critical for SDLC, it fails to address software tampering or risks posed by compromised open-source and third-party libraries. Similarly, software composition analysis (SCA) can vet open-source components but often misses malicious modules and fails to provide complete security coverage.
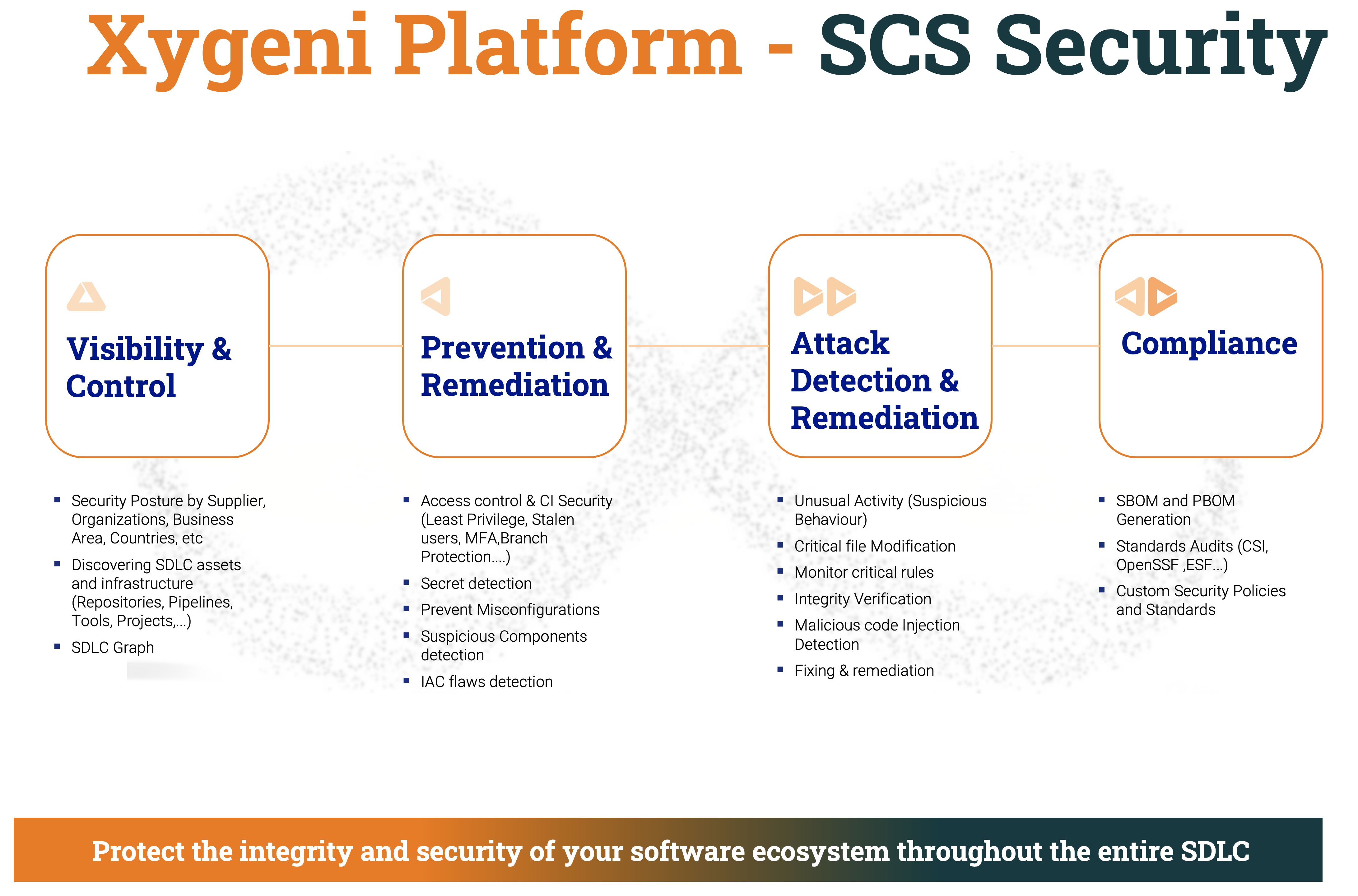
Therefore, modern tools like Xygeni that surpass these capabilities must be considered to provide developers with the necessary resources for success. Experts agree that change is essential, as current development teams need to be equipped for success.
A system of checks and balances should be implemented from the initial stages of software development to ensure software supply chain security. Even before writing the first line of code, it is crucial to consider the following preventive measures:
- Determining who will have access to the code, including internal and external parties
- Defining ownership over code approvals
- Establishing a chain of custody and version control
- Implementing basic security measures to prevent malicious code injection
- Creating mechanisms to respond to code alterations by bad actors
Failure to implement these steps can result in devastating attacks such as ransomware demands that affect your organization, partners, and customers.
Agile Methodologies
Agile methodologies revolutionized software development by emphasizing collaboration, flexibility, and customer satisfaction. This approach has enabled development teams to respond quickly to changing requirements and deliver high-quality software promptly. In an agile environment, development teams work in short sprint cycles, lasting a few weeks to a month. At the end of each sprint, the team delivers a working product increment.
The agile approach also promotes collaboration and communication among team members, breaking down silos and improving transparency. It helps to identify and address potential security risks early on, ensuring that security is integrated into every stage of the software development process. Agile teams can leverage security testing and automated security scans throughout the SDLC to identify and fix issues immediately, achieving very relevant benefits such as:
- Cost savings: It is less expensive to fix security issues in the early stages of the development process than after a product has been released and is in use. The later a security issue is discovered, the more costly it is to fix.
- Reduced risk of a security breach: By addressing potential security risks early on, the likelihood of a successful security breach is reduced, which protects sensitive information and prevents costly security incidents.
- Compliance: Many industries are subject to regulatory compliance requirements, such as SOC2, PCI, and ISO. Integrating security into the software development process can help ensure compliance with these regulations.
- Customer trust: Customers expect software products to be secure and reliable. Integrating security into the development process and demonstrating this practice increase customer trust and confidence in the product.
- Reputation management: By addressing potential security risks early and ensuring that security is integrated into every stage of the development process, companies manage their reputation and maintain customer trust and revenue by avoiding security incidents that damage their reputation.
Security Measures
Incorporating software supply chain security best practices and automated security scans throughout the software development life cycle (SDLC) is crucial for agile teams to promptly detect and address security issues. Some approaches that agile teams can use to integrate security testing into their development process should include:
- Managing control points throughout your software supply chain is crucial for achieving regulatory compliance and ensuring proper security. Organizations should implement standard controls such as identity and access approval, configuration management, access restrictions, auditing, and security testing to accomplish it. Organizations must set controls for who can make changes to code and configurations, approve merge requests, and scan applications for vulnerabilities. Protected branches and environments and licensed code usage are also essential. During an audit, you should have visibility into who changed what, where, and when, and who reviewed, approved, and merged it along the entire software development lifecycle.
- Inventory all the tools and access points your development team uses, including Infrastructure as Code (IaC) templates, code repositories, pipelines, and build tools. This step is critical because you can only secure what you know about. Once you have a comprehensive list of tools and access points, it’s time to re-evaluate your access controls. First, examine all your entry points along the software supply chain. For example, consider who has access to change IaC templates, as these templates can be a potential attack surface. Also, scan containers for security flaws and monitor APIs and orchestrators for unusual behavior. Standards such as the National Institute of Standards (NIST) and Secure Software Development Framework (SSDF) help get ideas on securing your software supply chain.
- Conduct Security Testing in Every Sprint: Agile teams can incorporate security testing into their sprint cycle by running regular security tests during each sprint. This can include manual testing, automated testing, and code reviews. By conducting security testing in every sprint, teams can identify and address potential security issues early in the development process, reducing the risk of introducing vulnerabilities in the software.
- Use Automated Security Scans: Agile teams can use automated security scanning tools to identify security issues in the codebase. These tools can scan code repositories searching for secrets or malware, detect vulnerabilities in open-source libraries, and identify misconfigurations in the infrastructure. By using automated security scans, teams can quickly identify and prioritize security issues for remediation.
- Implement Continuous Integration and Deployment (CI/CD): Agile teams can leverage CI/CD pipelines to automate the build, test, and deployment process. By integrating security testing and automated security scans into the CI/CD pipeline, teams can ensure that every code change is tested for security vulnerabilities. This can include static code analysis, dynamic security testing, and vulnerability scanning.
- Automating generating a software bill of materials (SBOM) involves creating a list of all the components in a codebase. Automating this process eliminates the need for time-consuming manual checks to ensure malicious software is not in your code. Automated SBOM generation provides visibility into dependencies across temporary structures, including package managers and containers. Developers can quickly address remediation activities by displaying SBOM vulnerabilities in the user interface. To make SBOMs more user-friendly and accessible, minimizing the number of tools required to review and process them is crucial. Incorporating SBOM into a secure end-to-end platform can protect against various attacks, including those targeting internal code, external sources, and the build process.
Conclusion
Organizations can and should create an agile and secure software supply chain by combining agile methodologies with security measures. This approach enables companies to respond quickly to changing requirements while ensuring that security risks are identified and addressed early.
In an agile and secure supply chain, security is not an afterthought. Still, it is integrated into every stage of the software development process, delivering high-quality software on time while protecting against cyber threats and data breaches.
Integrating security into every stage of the software development process and promoting collaboration and communication among team members is vital. By doing so, companies can stay ahead of the curve and in an advantageous position with minimized effort and very cost-effective.
Know more about Xygeni Platform, download Xygeni’s platform datasheet







