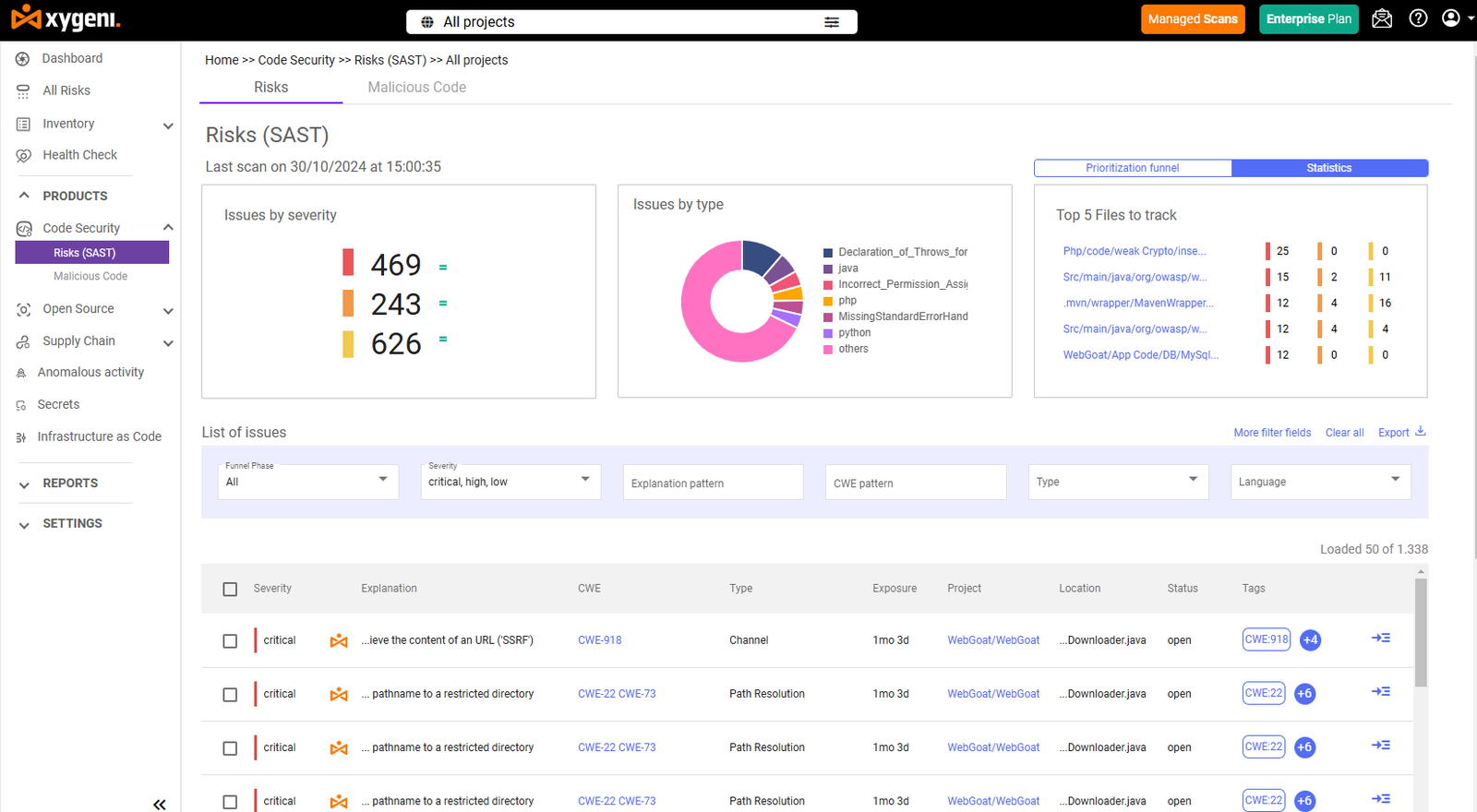
Keeping applications secure is more critical than ever. In 2024, over 54,000 new CVEs were published, a record-breaking number. This spike shows how fast the attack surface is growing, especially as modern apps rely more on open-source code and third-party packages. That’s why the sca vs sast debate isn’t just technical, it’s strategic. Instead of picking one over the other, security-minded teams use both. SAST catches bugs and flaws in your own code early. SCA tracks issues in dependencies before they land in production. Different tools, different layers, but together, they close real gaps.
In this guide, we break down the differences between sast and sca, how they work side by side, and how Xygeni unifies them into a single platform built for DevSecOps.
What Is SAST?
Static Application Security Testing (SAST) is like having an early warning system for your proprietary code. By scanning source code, bytecode, and binaries, SAST identifies vulnerabilities long before they become a problem. For example, it flags issues like SQL injection or cross-site scripting (XSS) while the code is still in development.
Key Benefits of SAST:
- Early Detection: Finds vulnerabilities early, saving time and money on fixes later.
- Comprehensive Coverage: Checks all custom code thoroughly, making sure nothing is missed.
- Real-Time Feedback: Guides developers as they write, making sure better code quality.
- Code Quality Improvement: Enhances security while improving maintainability.
Modern SAST tools are evolving fast. To stay effective, they must not only detect issues like SQLi or XSS, but also prioritize what’s actually exploitable and provide real-time guidance to developers. This is where tools like Xygeni stand out, but we’ll cover that in detail below.
What Is SCA?
Meanwhile, Software Composition Analysis (SCA) is all about managing risks in third-party and open-source dependencies. With modern applications relying heavily on open-source components—often as much as 90%—SCA becomes crucial for keeping track of vulnerabilities and licensing issues.
Key Benefits of SCA:
- Dependency Management: Keeps your Software Bill of Materials (SBOM) up-to-date.
- Vulnerability Detection: Flags issues using databases like NVD or OpenSSF.
- License Compliance: Helps comply with open-source licensing requirements.
- Proactive Alerts: Finds outdated components to avoid hidden risks.
By fixing vulnerabilities in external dependencies, SAST and SCA work well together to provide strong application security. Also, the comparison of SCA vs SAST shows how these tools support each other, addressing different parts of application security challenges effectively.
SAST vs SCA: Key Differences in Application Security
| Aspect | SAST | SCA |
|---|---|---|
| Primary Focus | Proprietary source code | Open-source and third-party dependencies |
| Timing | Best applied during the development phase | Continuous monitoring pre- and post-deployment |
| Vulnerability Types | Detects coding flaws (e.g., SQL injection, XSS) | Identifies known vulnerabilities in external libraries and packages |
| Scope | Analyzes custom code written in-house | Scans all direct and transitive dependencies in the codebase |
| Best Use Case | Securing proprietary applications | Managing risks in open-source and third-party software components |
| Impact on Development | Improves secure coding practices through real-time feedback | Ensures compliance and mitigates risks from unverified external sources |
As this comparison shows, SAST and SCA serve different but work well together. Using them together ensures no gaps in your security strategy.
Why You Need Both SAST and SCA
Instead of choosing between SCA vs SAST, leverage both to create a multilayered defense. Here’s why:
- Comprehensive Protection: SAST covers custom code, while SCA secures third-party dependencies.
- Reduced Attack Surface: Together, they eliminate weak spots in your applications.
- Efficiency: Streamlined workflows help resolve vulnerabilities faster.
For a deeper dive into building secure applications, explore this detailed OWASP Secure Coding Practices Guide, a valuable resource for DevSecOps professionals. Also, you can take a look at our SafeDev Talk episode on SCA vs SAST – How They Complement Each Other for Stronger Security?
Why SAST and SCA Matter in 2025: Modern Application Security Needs Context
Security teams today aren’t just patching bugs. They’re protecting critical pipelines, managing risk across open-source dependencies, and staying compliant with growing regulations.
In early 2025, over 80% of codebases contain known open-source vulnerabilities, according to industry reports. And with AI-assisted coding projected to account for 30–50% of new code in some orgs, it’s getting harder to track what’s secure and what’s not.
Meanwhile, regulations like NIS2, DORA, and new SEC rules are making security traceability a must, not just a nice-to-have.
Add high-profile supply chain attacks like xz Utils or ctx, and it’s clear: the old way of doing AppSec isn’t enough.
That’s why sca and sast aren’t optional. Used together, they give teams visibility into both proprietary and third-party risk. The key now is combining them into a workflow that developers actually use.
Xygeni: The Unified SAST and SCA Solution
Security teams often struggle to decide between SAST vs SCA, but the reality is both are essential. SAST vs SCA isn’t a competition, it’s a partnership. While SAST analyzes proprietary code for security flaws, SCA scans open-source and third-party components for known vulnerabilities.
Xygeni combines SAST and SCA into one unified platform, designed to fit into DevSecOps workflows. This approach ensures security throughout the entire development process, from analyzing custom code to managing open-source risks.
Proactive SAST: Securing Proprietary Code from the Start
Xygeni’s Static Application Security Testing (SAST) analyzes your proprietary code from the moment it’s written , scanning source code, bytecode, and binaries for critical security flaws.
Key threats detected include:
- SQL injection, cross-site scripting (XSS), and command injection
- Memory management errors like buffer overflows
- Insecure authentication logic and data exposure
- Obfuscated or malicious code such as ransomware, spyware, or backdoors
But what makes Xygeni different is not just detection, it’s prioritization.
Benchmark-Proven Accuracy
Xygeni-SAST was tested using the official OWASP Benchmark, where it achieved:
- 100% True Positive Rate in all major categories like SQLi and XSS
- A low 16.7% False Positive Rate, outperforming tools like CodeQL, Semgrep, and SonarQube
- Perfect scores in critical areas like weak encryption and insecure cookie detection
These results show that Xygeni catches real threats, and avoids wasting your team’s time on noise.
AutoFix and CI/CD Integration
To speed up resolution, Xygeni’s AI-powered AutoFix:
- Suggests secure code changes in real time
- Automatically generates pull requests with context-aware patches
- Runs directly inside your CI/CD workflows without blocking releases
This means your team fixes vulnerabilities early, before they hit production, without slowing down development.
Dev-Friendly by Design
- One-line CLI install
- Full SCM integration (GitHub, GitLab, Azure DevOps, Bitbucket, Jenkins)
- Output in JSON, SARIF, CSV, Markdown
- Custom rule support in YAML
- Inline PR annotations and guardrails
With Xygeni, SAST becomes a seamless part of your secure development lifecycle, from detection to remediation, with zero friction.
Intelligent SCA: Safeguarding Open-Source Dependencies
Modern applications rely on open-source more than ever, but with that comes risk. Recent studies show that 74% of codebases contain high-risk open-source components, and that 91% of those components are at least 10 versions behind. Without proper visibility and control, you could be shipping vulnerabilities straight into production.
Xygeni’s Software Composition Analysis (SCA) goes far beyond listing CVEs. It provides a real-time, intelligent layer of protection across your third-party ecosystem.
Advanced Detection Beyond CVEs
Xygeni scans all dependencies, direct and transitive, and flags:
- Known vulnerabilities using NVD, OSV, GitHub Advisory and others
- Outdated packages with missing patches
- Anomalous or malicious behavior in package install scripts
- Typosquatting, dependency confusion, and unscoped internal packages
- Suspect patterns linked to spyware, ransomware, and backdoors
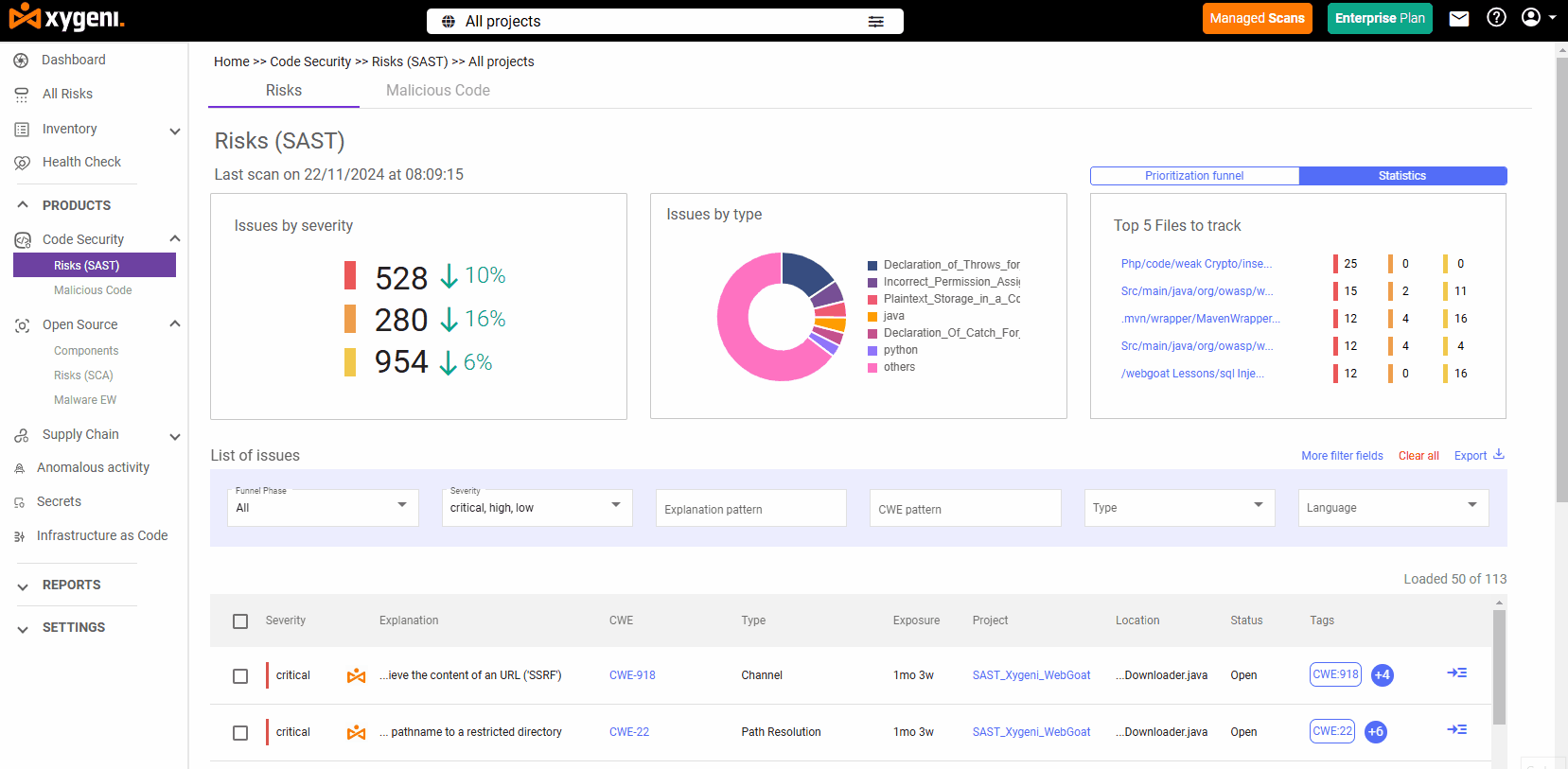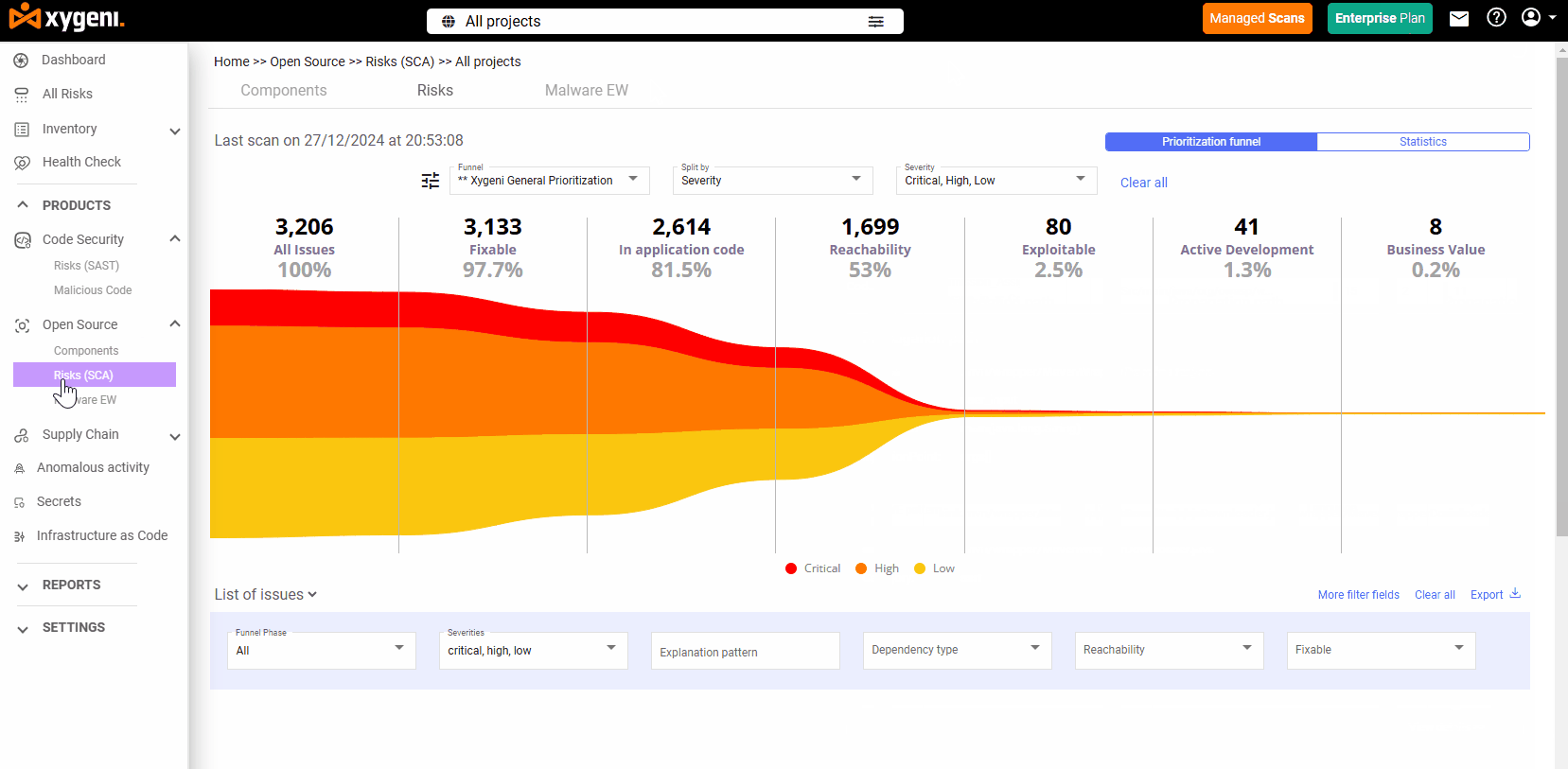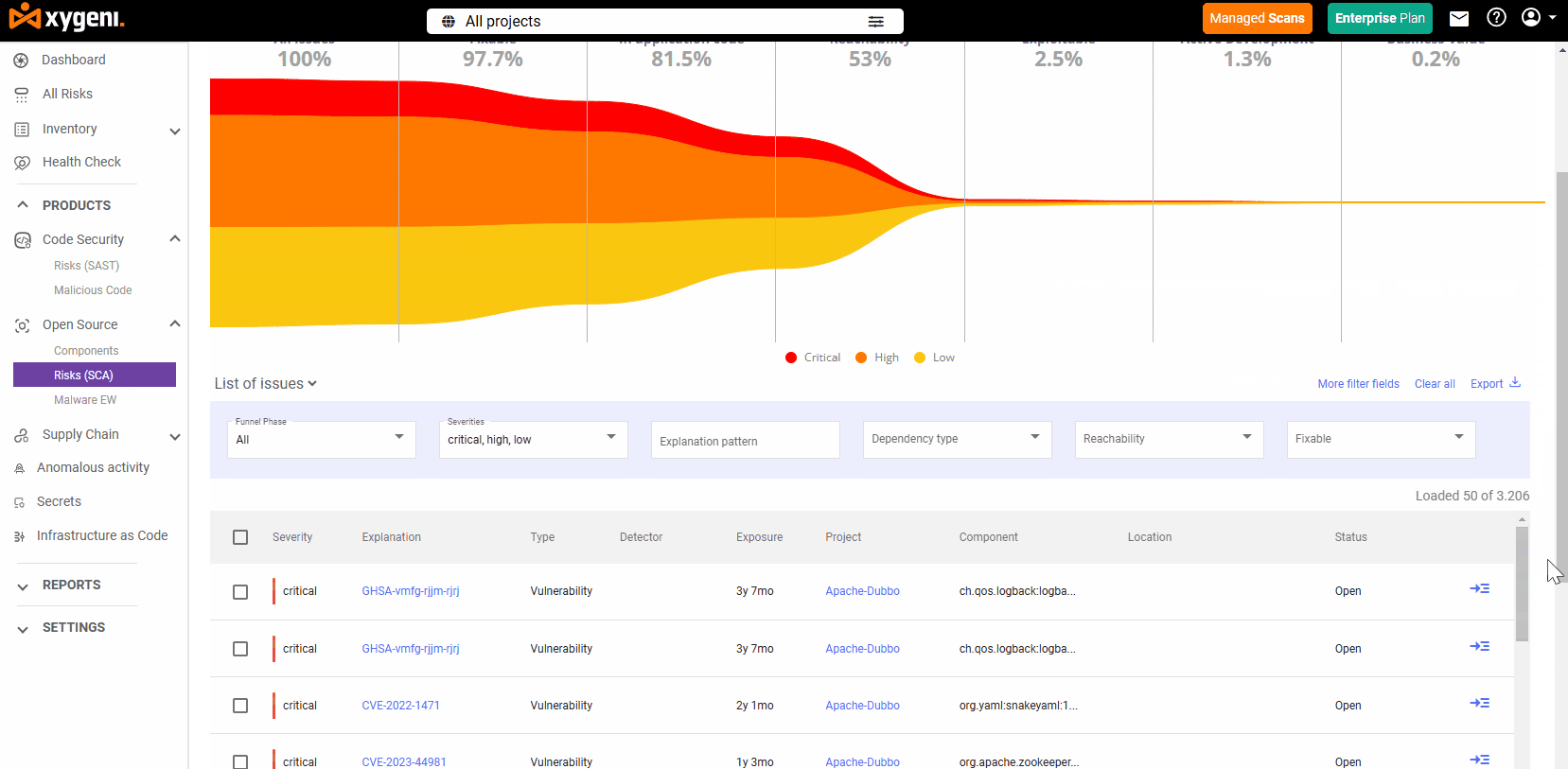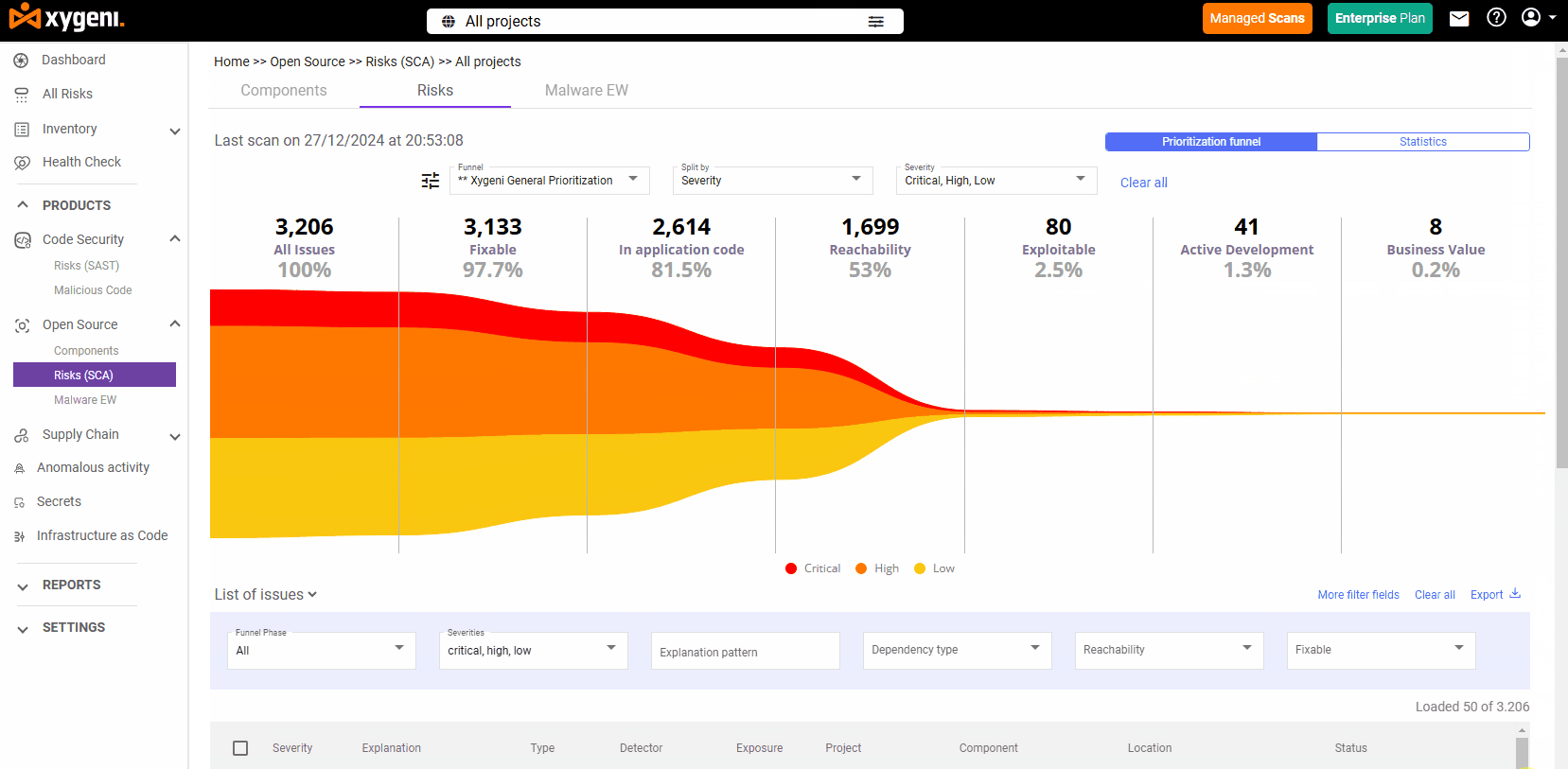
Reachability and Exploitability: Focus on What Matters
Instead of flooding you with alerts, Xygeni uses Reachability Analysis to show which vulnerabilities are actually used in your application:
- Tracks execution paths and call graphs
- Prioritizes vulnerabilities based on EPSS (Exploit Prediction Scoring System)
- Reduces false positives by up to 70%
- Distinguishes between reachable and unused code paths
This lets your team focus only on exploitable risks, saving time and cutting noise.
Auto-Remediation in CI/CD
Fixing vulnerable dependencies doesn’t have to be manual. Xygeni automates this process with:
- Instant fix suggestions directly in your workflow
- Bulk AutoFix: apply multiple dependency upgrades in one action
- Auto-generated pull requests with safe patch versions
- Full CI/CD integration for continuous protection
No more hunting through logs or juggling patch versions, just fast, targeted remediation where it counts.
Early Malware Detection for OSS
Xygeni continuously scans public registries (like NPM, PyPI, Maven) to detect:
- Malware-infected packages
- Zero-day threats
- Suspicious install scripts
- Behavior linked to spyware or backdoors
If something is flagged, Xygeni quarantines the threat, alerts your team, and even helps notify the registry to prevent further spread. You’re protected before malicious packages reach your pipelines.
Full Transparency and Compliance with SBOM
Need to prove what’s in your code? Xygeni automatically generates SBOMs in formats like SPDX and CycloneDX, and integrates Vulnerability Disclosure Reports (VDR) for complete traceability.
- Complies with EO 14028, NIST SP 800-204D, DORA, and FDA requirements
- Tracks license risks across all components
- Works via CLI or WebUI, fully embedded into your CI pipelines
This ensures you meet regulatory expectations while keeping your supply chain secure and auditable.
SAST vs SCA: Advanced Security Features That Set Xygeni Apart
When comparing sca vs sast, it’s not just about what they detect, it’s about how smartly they do it. Xygeni transforms traditional AppSec tools into a unified, intelligent system that eliminates noise and accelerates remediation.
Here’s how Xygeni’s SAST and SCA work together to deliver real security impact:
Exploitability and Reachability: Prioritize What’s Real
Most security tools flood teams with irrelevant alerts. Xygeni solves this with built-in exploitability analysis and reachability tracing:
- SAST findings are filtered by dataflow analysis to flag only exploitable flaws
- SCA vulnerabilities are ranked based on whether the vulnerable code is actually used
- Combined with EPSS scoring, your team sees what matters first, and nothing else
This dramatically reduces alert fatigue and cuts through the noise.
AutoFix: Remediation That Writes Itself
Xygeni speeds up security by eliminating manual fixes:
- AI-powered AutoFix generates pull requests for both SAST and SCA issues
- Patches are aligned with best practices and scoped to the real problem
- Bulk AutoFix applies multiple fixes in a single flow
- All changes are CI/CD-ready and developer-approved
Fixing vulnerabilities becomes a seamless part of the dev process — not a blocker.
Early Malware Detection in Dependencies
With malicious open-source packages rising over 300% year-over-year, malware detection is now a must in SCA tools.
Xygeni scans public registries in real time (NPM, PyPI, Maven) to detect:
- Typosquatting, dependency confusion, and suspicious scripts
- Backdoors, spyware, and ransomware in packages
- Zero-day threats before they hit your pipeline
If a threat is found, it’s blocked, quarantined, and traced, fast.
Compliance, SBOM, and VDRs: Built In
Xygeni automates key governance tasks with every build:
- Generates SBOMs in SPDX and CycloneDX formats
- Aligns with NIST SP 800-204D, DORA, EO 14028, and FDA guidelines
- Includes Vulnerability Disclosure Reports (VDRs) to track risks over time
- Integrates into your CLI or Web UI, no extra tooling needed
Compliance is no longer an afterthought. It’s continuous, transparent, and ready for audit.
One Platform, One Flow
Unlike fragmented tools, Xygeni delivers:
- Unified results for SAST and SCA in one dashboard
- CI/CD guardrails and policies that enforce shift-left security
- Real-time alerts with contextual remediation guidance
- Full traceability from vulnerable commit to resolved fix
Whether you’re securing proprietary code or your OSS supply chain, Xygeni covers it all, with less friction, fewer alerts, and faster results.
Security Isn’t Just Tooling. It’s Governance.
Application security isn’t just about catching vulnerabilities. In fact, it’s also about knowing who owns the risk, who fixes it, and how those actions align with your internal security policies.
As your organization grows, visibility alone won’t cut it. You need traceability. That means:
- Who added the vulnerable dependency?
- Who’s responsible for the fix?
- Is the remediation aligned with your security policies?
This is where proper tooling and governance come together. When you integrate SAST and SCA tools into your workflows the right way, they don’t just find problems. Instead, they help enforce security rules, assign responsibility, and speed up fixes with clear, automated flows.
Moreover, at scale, governance becomes the glue between detection and remediation. Without it, you just collect alerts. With it, you take real action.
That’s why Xygeni offers policy-based guardrails, custom team assignments, and full traceability across your secure software development lifecycle. You can see who introduced a risk, who owns the fix, and whether the change meets your governance model.
In short, security doesn’t stop at detection. It only becomes effective when your system makes it easy for the right person to act fast.
Ready to secure your development workflow with the right tools?
Explore our expert-curated lists to find the best solutions for your team:
- Top 10 Software Composition Analysis (SCA) Tools for DevSecOps Teams
Discover the best tools to manage open-source components and protect your software supply chain. - Top SAST Tools for DevSecOps Teams
Compare the leading static code analysis tools to detect vulnerabilities early in development.
FAQs About SCA vs SAST
What is the main difference between SCA vs SAST?
SAST examines proprietary code for security flaws, while SCA focuses on third-party and open-source components to identify vulnerabilities and license risks
Can SAST and SCA be used together?
Yes, using SAST and SCA together provides complete security by covering both proprietary and third-party code, minimizing overall risk.
What types of vulnerabilities does SAST detect?
SAST finds code issues, like SQL injection, buffer overflows, and cross-site scripting (XSS), before the application is deployed.
Why is SCA important for open-source security?
SCA helps teams manage risks in third-party dependencies, like old libraries, known security issues, and licensing problems.
Which is better: SAST or SCA?
Neither is effective on its own. SAST and SCA work together to provide comprehensive security for both custom and external code
What is Xygeni, and how does it integrate SAST and SCA?
Xygeni unifies SAST and SCA into one platform, making vulnerability management faster, smarter, and more efficient across the entire development lifecycle.