Ensuring application security has never been more critical. As of August 2024, internet users worldwide discovered 52,000 new Common IT Security Vulnerabilities and Exposures (CVEs). This reflects a sharp increase from 2023, which saw a record-breaking 29,000 CVEs reported in a single year. In this context, comparing SAST vs DAST is essential for understanding how to address these escalating threats. Knowing what is SAST and DAST, and how they protect against vulnerabilities, is critical for organizations seeking to secure their applications. This article explores DAST vs SAST, their unique benefits, and why SAST is the superior choice for modern application security.
What is SAST and DAST? Understanding the Basics
What is SAST, and Why Does It Matter?
Static Application Security Testing (SAST) is a white-box testing technique that scans source code, bytecode, or binaries to identify vulnerabilities. Unlike DAST, which tests running applications, SAST analyzes the code before deployment, catching issues early. Understanding what is SAST and DAST helps organizations make informed decisions about securing their applications effectively.
SAST is particularly effective at identifying critical vulnerabilities, such as SQL injection, buffer overflows, and cross-site scripting (XSS). By integrating SAST into CI/CD pipelines, developers can receive real-time feedback, reducing the chances of vulnerabilities making their way into production.
The value of SAST is amplified when integrated into the development phase, as 37% of organizations already do. This early integration aligns security with development workflows, enabling real-time feedback that accelerates remediation and fosters secure coding practices.
Key Features of SAST:
- Proactive Detection: Finds vulnerabilities before applications are deployed.
- Integration-Friendly: Embeds into CI/CD pipelines, providing real-time feedback to developers.
- Cost-Effective: Fixing vulnerabilities during coding is far cheaper than addressing them post-deployment.
What is DAST, and How Does It Work?
In contrast to SAST, Dynamic Application Security Testing (DAST) evaluates applications in their running state. This black-box testing method simulates external attacks to uncover vulnerabilities, such as authentication flaws or misconfigured APIs. When considering what is SAST and DAST, DAST’s runtime focus complements SAST’s early-stage security, although SAST often provides greater cost and time savings.
Key Features of DAST:
- Runtime Testing: Simulates real-world attack scenarios.
- Black-Box Approach: Operates without access to source code.
- Focus on Runtime Risks: Detects issues arising from environment-specific misconfigurations.
While valuable for identifying runtime vulnerabilities, DAST has notable limitations, especially for early-stage security.
SAST vs DAST: Key Differences Explained
To understand what is SAST and DAST, it’s important to compare how they differ in timing, access, and the vulnerabilities they address. These differences can help organizations choose the right tool for their application security needs.
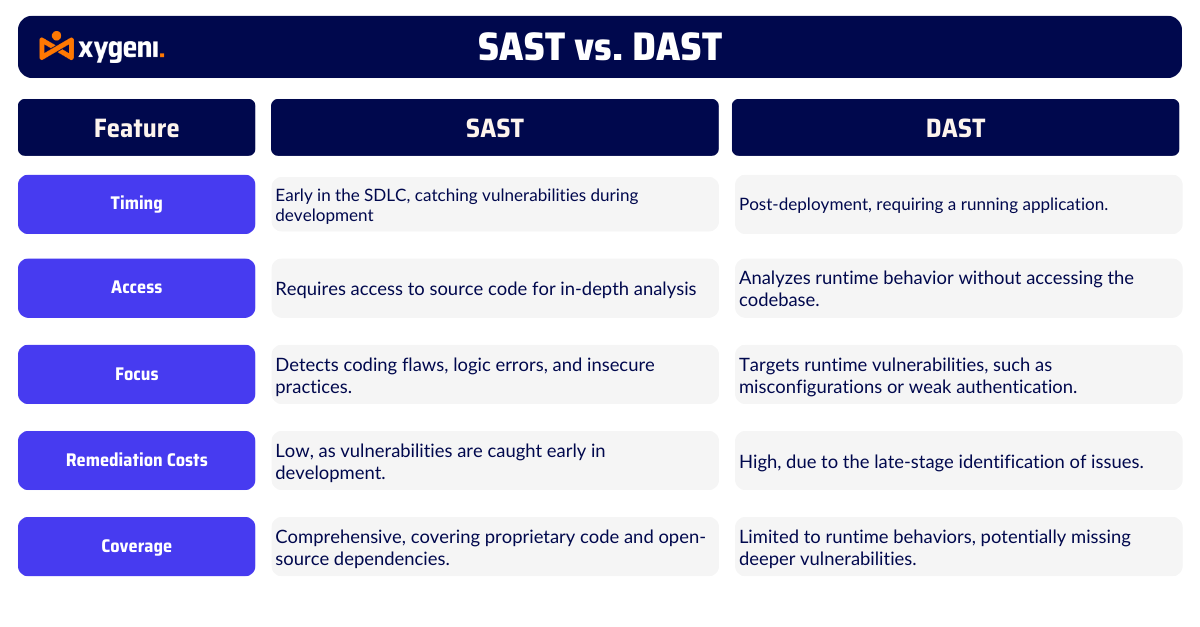
Timing
One major difference between DAST vs SAST is when they are used in the software development process. SAST works early, during the coding and building phases. This approach, often called “shift-left,” helps developers catch vulnerabilities before the application is deployed. Early detection means faster fixes and lower costs. In contrast, DAST is used later, usually after the application is running in staging or production. While DAST can test how the application responds to real-world attacks, finding and fixing issues at this stage is often more time-consuming and expensive.
Access
Another key difference DAST vs SAST is how these tools access the application. SAST needs access to the source code, bytecode, or binaries. This “white-box” approach allows it to dig deep into the internal structure of the application. On the other hand, DAST is a “black-box” testing tool. It doesn’t require access to the code and instead tests the application from the outside, simulating how an attacker might interact with it. While this is useful for runtime testing, DAST can miss deeper code-level issues that SAST is designed to catch.
Analysis Method
The way SAST vs DAST analyze applications also sets them apart. SAST looks at the internal logic and structure of the application to detect coding issues, even if they don’t cause immediate problems at runtime. DAST, however, focuses on how the application behaves when it’s live, identifying runtime vulnerabilities like misconfigurations or broken authentication. Both approaches are valuable, but SAST is better at finding flaws before they become bigger problems.
Cost of Remediation
Fixing security issues during development is much cheaper than after deployment, which is why many organizations rely on SAST. By addressing vulnerabilities early, teams can avoid costly delays and rework later in the process. DAST, while effective for runtime testing, often finds issues after the application is live, making fixes more disruptive and expensive.
Coverage
SAST offers broad coverage, scanning not just proprietary code but also open-source dependencies to uncover vulnerabilities across the entire application stack. In comparison, DAST focuses solely on runtime behaviors. This means it might miss deeper, code-level issues that could lead to security gaps. For organizations looking to address vulnerabilities comprehensively, SAST is essential.
Why SAST is the Better Choice for Application Security
Now that we’ve outlined the differences between SAST vs DAST, it’s clear that SAST is better for most organizations. Its proactive approach enables early detection and resolution of vulnerabilities, saving time and significantly reducing costs.
Additionally, with the rise in open-source vulnerabilities, SAST becomes even more critical. Open-source components are widely used, yet many are outdated or poorly maintained. SAST scans these dependencies alongside proprietary code, ensuring a secure foundation for your applications.
DAST vs SAST: Adapting to Modern Threats
The rapid expansion of the application security market reflects the urgency of adopting proactive tools like DAST vs SAST. As open-source vulnerabilities grow, SAST addresses threats early, helping organizations comply with regulatory frameworks like NIS2 and DORA.
How Xygeni’s SAST Solution Strengthens Application Security
To address the growing complexity of modern applications, Xygeni’s SAST solution offers a robust, flexible approach. Designed to integrate seamlessly into CI/CD pipelines, Xygeni provides real-time feedback to developers, ensuring vulnerabilities are identified and resolved early.
Key Features of Xygeni’s SAST Solution:
- Comprehensive Scanning: Detects coding errors, logic flaws, and vulnerabilities in proprietary and open-source code.
- Real-Time Feedback: Embeds security directly into the development workflow, accelerating remediation.
- Open-Source Protection: Scans dependencies to address risks from third-party libraries.
- Enhanced Code Quality: Encourages secure coding practices, improving maintainability.
Choose SAST for Proactive Security
In the debate of SAST vs DAST, SAST stands out as the better and more proactive choice for application security. Using SAST during development helps find and fix vulnerabilities early, making it cheaper and easier to keep applications secure. With Xygeni’s SAST solution, organizations can protect their software and stay ahead of growing security threats.
Book a demo today to see how Xygeni can help secure your applications from code to deployment.








