Malicious code is one of the stealthiest and most damaging threats facing software teams today. It doesn’t always make a loud entrance—sometimes, it quietly slips into your pipeline through an open-source dependency or a misconfigured CI job. So, how can malicious code do damage, and which of the following may indicate a malicious code attack? More importantly, how can malicious code cause damage before it ever hits production?
This guide walks you through real-world cases, warning signs, and smart mitigation tactics you can implement today.
How Can Malicious Code Cause Damage? A Deep Dive with Real-World Examples
Understanding how malicious code can cause damage is key to building a secure software supply chain. In today’s CI/CD ecosystems, malicious code can:
1. Exfiltration of Secrets – How Malicious Code Causes Credential Leaks
What happens: Attackers steal sensitive data—like API keys, tokens, or passwords—stored in code, config files, or build environments.
Why it’s dangerous: It opens the door to cloud takeover, database access, and supply chain compromise.
Real Case: JarkaStealer malware in PyPI packages exfiltrated secrets through fake developer tools.
In other words, this type of attack leverages trust and convenience to harvest access credentials before anyone realizes what’s happened.
2. Injecting Backdoors or Rootkits
What happens: Code includes persistent, hidden entry points attackers can use later—even after you think the threat is gone.
Why it’s dangerous: It bypasses firewalls and allows long-term access.
Real Case: The XZ Utils backdoor embedded in Linux systems gave attackers SSH access with no credentials.
Moreover, this incident underscores how social engineering and insider threat can bypass even the best code review processes.
3. Silent Logic Changes – How Can Malicious Code Disrupt Your App?
What happens: Another example of How Can Malicious Code Do Damage is through subtle changes to business logic—skipping validations or weakening security checks.
Why it’s dangerous: These changes are often invisible to developers but catastrophic in production.
Real Case: UAParser.js on NPM was hijacked to install crypto miners, changing how it executed code under the hood.
As a result, even small logic changes in trusted libraries can cascade into major security gaps.
4. Exploiting Open-Source Package Trust
What happens: This is How Can Malicious Code Do Damage at scale. Malicious actors publish fake or hijacked packages that look legit—and devs unknowingly install them.
Why it’s dangerous: These attacks scale fast, affecting thousands of apps.
Real Case: Over 280 malicious NPM packages were used in a typosquatting campaign that funneled traffic through Ethereum smart contracts.
Consequently, this shows the critical need for real-time registry scanning and package reputation systems.
5. Wiping or Corrupting Data
What happens: Files are deleted, logs are erased, and databases are trashed to hide traces or cause chaos.
Why it’s dangerous: This is pure destruction—no ransom, no message—just downtime and data loss.
Real Case: HermeticWiper malware wiped systems in Ukraine using a fake software updater.
To emphasize, destructive attacks are not just theoretical—they are part of modern cyber warfare.
6. Disabling Key Services (Denial-of-Service)
What happens: Code consumes resources or crashes systems using logic bombs, recursion loops, or malformed inputs.
Why it’s dangerous: It takes down services during peak hours—or hides a deeper attack.
Real Case: Log4Shell exploits included DoS variants that crashed Java apps instantly.
For that reason, implementing circuit breakers and runtime monitoring is essential in today’s architectures.
TL;DR – How Can Malicious Code Cause Damage?
- Exfiltrate sensitive data – Steal passwords, tokens, and credentials from code or environments
- Alter system behavior – Quietly change app logic, bypass auth, or disable security controls
- Hijack build pipelines – Inject malware into artifacts or CI/CD processes
- Launch backdoors – Maintain stealthy access even after detection
- Destroy availability – Trigger crashes or Denial-of-Service in production
Which of the Following may indicate a Malicious Code Attack ?
Now that you understand how malicious code can cause damage, here’swhich of the following may indicate a malicious code attack in your environment:
1. Sudden or Suspicious File Modifications
- Changes to CODEOWNERS, .env, or shell scripts
- Modifications committed by new or untrusted users
- All of a sudden, test files behaving differently
2. Unexpected Package or Dependency Changes
- Transitive or newly added dependencies without discussion
- Odd version bumps in package.json or pom.xml
- Packages with no stars or documentation
To illustrate, attackers often release multiple fake libraries and wait for typos or autocomplete to do the rest.
3. Commit or Contributor Anomalies
- Unfamiliar contributors pushing critical changes
- Force-pushed commits erasing history
- CI/CD running at odd hours or from unknown IPs
What’s more, these are especially risky in OSS projects where anyone can fork, modify, and submit a pull request.
4. CI/CD Build Pipeline Red Flags
- New build steps inserted without PR description
- Credentials passed as plaintext in logs
- Unexpected test failures
On the other hand, these may be normal in early development—but only if they’re properly reviewed and documented.
5. Secrets or Credentials Leaking
- Git history reveals keys or tokens
- Secrets appear in debugging logs or test dumps
Before you go live, make sure secrets scanning is part of every commit and PR workflow.
TL;DR – Which of the Following May Indicate a Malicious Code Attack?
- Unexpected changes in key files –
CODEOWNERS,Dockerfile, or.envfiles suddenly modified - Unusual CI/CD pipeline activity – New or altered build steps, scripts, or job behavior
- Unknown commit authors – New contributors pushing high-privilege or unreviewed changes
- Suspicious open-source packages – Recently published or poorly maintained dependencies in use
- Secrets exposure in version control – API keys, tokens, or credentials committed by mistake
- Anomalous repository access – Irregular logins, role changes, or contributor anomalies
Stop the Damage: How to Prevent Malicious Code in Your Software Supply Chain
The good news? You’re not alone in this fight.
Xygeni gives your team the unified tools they need to detect, stop, and recover from malicious code threats—before they ever reach production. As attacks evolve in complexity and scale, scattered security tools fall short. You need integrated protection embedded into every stage of the software development lifecycle.
That’s where Xygeni comes in—built to secure your code, pipeline, and open-source components from a single platform.
Here’s how Xygeni helps you stay ahead:
- Real-Time Anomaly Detection
Catch suspicious file changes, contributor behavior, and pipeline drift the moment they happen. - Secrets Security
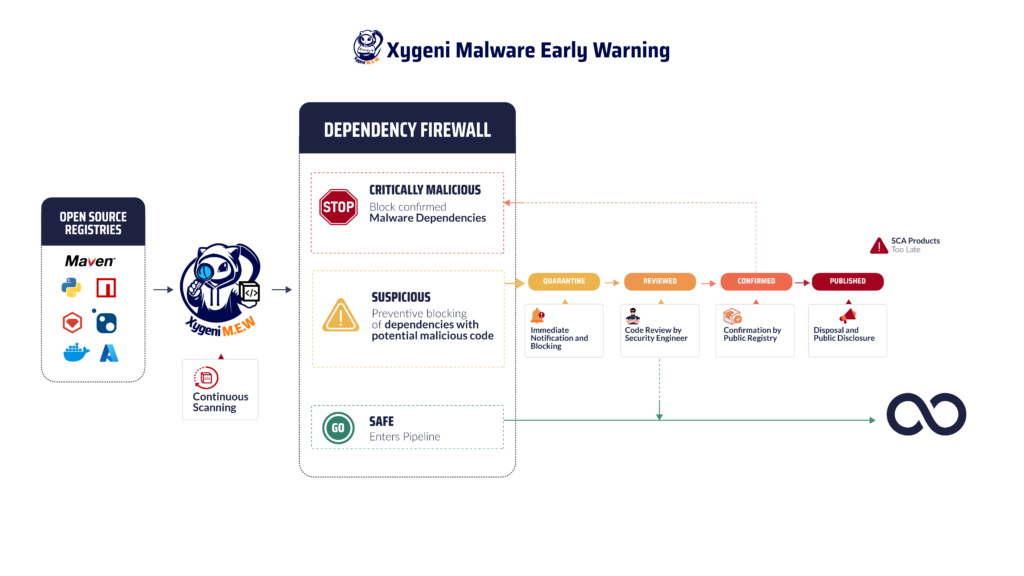
Automatically prevent secrets from entering your repositories, even before a commit is finalized. - Malware Early Warning
Scan public registries in real time and block malicious packages with behavior-based detection. - Code Tampering Detection
Get visibility into unauthorized changes to critical files, with commit-level context and alerting. - Build Integrity & Attestation
Ensure that every artifact is authentic, tamper-proof, and traceable—all the way from source to production. - Platform-Wide Prioritization
Use exploitability metrics like EPSS, reachability, and business context to filter out the noise and focus on what truly matters.
Key Takeaways
Unlike siloed point solutions, Xygeni consolidates protection across your SDLC into one powerful, developer-friendly platform. This gives your team real-time insight, contextual risk prioritization, and automated workflows—all without sacrificing speed or efficiency.
So, how can malicious code do damage? By exploiting your pipeline, your trust in open source, and the speed of DevOps itself. which of the following may indicate a malicious code attack ? Any of the red flags above.
You don’t need multiple tools to defend against these risks—you need one smart, unified platform.
Try Xygeni free today and protect your software supply chain from the inside out. Start Your Free Trial →