To achieve true source code security, development teams must adopt scanning tools and shift-left practices that prevent unauthorized use and stop threats before code ever reaches production. If you’re asking how can I prevent the use of my source code, the answer starts with visibility, guardrails, and real-time protection. By integrating reliable source code security scanning tools into your workflow, you can detect logic flaws, hardcoded secrets, and vulnerable dependencies early, ensuring that code integrity is never left to chance.
What Is Source Code Security and Why It Matters
If you write code, you’re responsible for more than just functionality. You’re also responsible for protecting it. Source code security is about ensuring that what you build stays safe, from commit to deploy.
In simple terms, it means preventing attackers from injecting vulnerabilities, stealing logic, or tampering with your repositories. But it goes deeper. It also covers everything from code integrity to shift-left practices that catch risks early.
After all, attackers rarely wait for production. They often strike when your guard is down, like when a hardcoded secret slips into a commit or a malicious dependency sneaks into a package.json.
That’s why secure development workflows must include:
- Early detection of flaws and secrets
- Protection against tampered dependencies
- Continuous source code security scanning tools that run in your CI/CD
In other words, source code security is not optional anymore. It’s essential for teams that want to build fast without opening the door to real threats.
Common Threats to Source Code Integrity (and How Attackers Exploit Them)
Protecting your source code is not just about writing clean logic. If you’re asking how can I prevent the use of my source code by unauthorized actors, the answer starts with understanding how attackers think. They often exploit weak points in your development lifecycle, not just your production code. These are the most common threats to source code integrity that every developer should address early.
1. Leaked Secrets in Commits
Tokens, API keys, and credentials often get committed by mistake. This happens frequently in .env files, debug scripts, or forgotten test cases. Once exposed, attackers can use these secrets to access cloud services or internal systems. They scan public repositories continuously and act fast when they find something useful.
2. Tampered or Hijacked Dependencies
Open source dependencies are a common entry point. Attackers can compromise maintainer accounts or publish malicious updates that appear legitimate. Without strict version pinning or behavioral scanning, your next build may import malware without warning.
3. CI/CD Pipeline Injections
CI/CD systems are prime targets. If your pipeline includes unsafe scripts, unverified third-party actions, or unpinned dependencies, an attacker can inject code that runs during the build. These attacks often bypass source code entirely and compromise your systems through insecure automation.
4. Insecure Pull Requests and Blind Merges
Risky code can hide behind clean syntax. If teams skip peer reviews or static analysis checks, dangerous logic can merge into production. Attackers then look for these flaws in deployed endpoints, especially in access control and authentication flows.
Best Practices to Prevent Unauthorized Use of Your Source Code
To reduce exposure and strengthen your source code security and code integrity, follow these best practices across your development lifecycle. If you’re wondering how can I prevent the use of my source code without permission, this checklist is your starting point.
1. Use Source Code Security Scanning Tools on Every Commit
Run SAST tools at each commit or pull request. Scan for logic flaws, secrets, and insecure functions before code reaches your main branch. Prioritize tools that offer actionable results with minimal false positives.
2. Enforce Branch Protection and Require Peer Review
Enable branch protection rules in your repository settings. Require at least one reviewer per pull request and block direct pushes to protected branches. This prevents unauthorized changes and ensures oversight.
3. Scan Dependencies with Reachability and Exploitability Checks
Use source code security scanning tools that go beyond CVEs. Choose an SCA engine that evaluates whether vulnerable dependencies are actually called in your code, and how exploitable those paths really are.
4. Rotate Secrets Automatically and Scan for Leaks
Keep all credentials and tokens in secure secret managers. Set automatic rotation policies and scan your full Git history, tags, and container layers for hardcoded secrets or accidental leaks.
5. Audit Your CI/CD Pipelines for Risky Behavior
Review your pipelines as code. Check for unsafe scripts, unpinned dependencies, and third-party actions that pull from unknown registries. Apply CI/CD guardrails that break the build on suspicious activity. Threat actors often exploit pipeline weaknesses, not just source code. This step protects the integrity of your entire delivery process.
Real-World Example: When Source Code Security Fails in the CI Pipeline
Let’s say a developer adds a popular-looking open source package during a routine update:
"dependencies": {
"net-utils-helper": "1.2.3"
}
At first glance, everything seems safe. No CVEs are listed. The version is pinned. The repo looks legit.
However, what the developer misses is this:
- The package contains a postinstall script that silently sends the system’s
SSH_PRIVATE_KEYto a remote server. - The script only activates inside a CI environment, checking for
CI=truein the environment variables. - Static analysis tools fail to flag the package, since it doesn’t match any known CVE signatures.
What a Source Code Security Scanning Tool Should Do
This is where modern source code security scanning tools like Xygeni come in:
- They scan the exact version added not just the name.
- They analyze the package behavior, including install scripts, file access patterns, and network calls.
- They detect malicious intent, even if the package has no reported CVEs.
- They block the build in the CI pipeline before the compromised dependency runs.
Result
- The backdoor never executes.
- The secret never leaks.
- The team avoids a supply chain compromise.
This example highlights why relying only on CVEs or manual checks is no longer enough. To protect code integrity and prevent malicious code from entering your pipelines, you need smarter tools with behavioral analysis and real-time CI/CD enforcement.
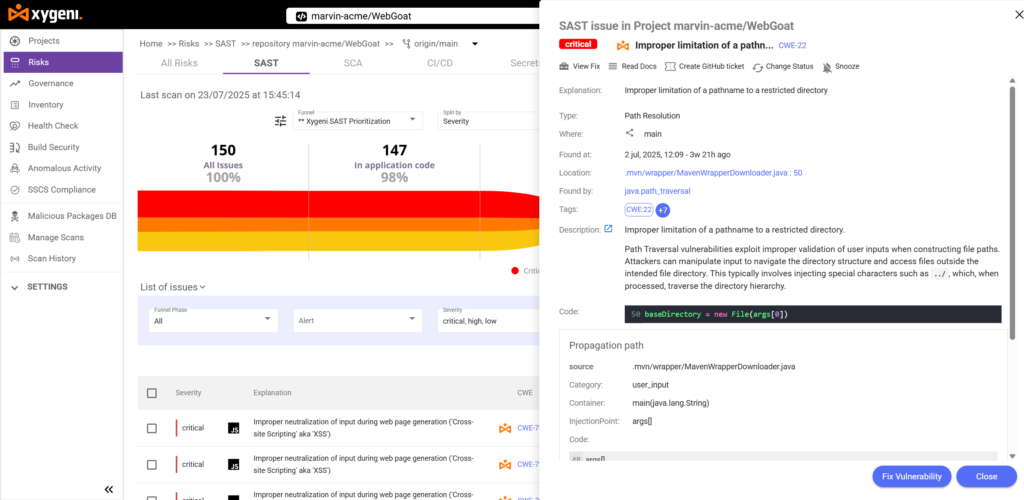
How Xygeni’s SAST Secures Source Code from the Inside Out
Most SAST tools slow down development or bury teams in false positives. Xygeni takes a different approach. It delivers developer-first static analysis that focuses on what really matters: exploitable flaws in real code paths.
Here’s how Xygeni protects your source code from the inside out:
- Scans Every Pull Request in Real Time
Xygeni analyzes code the moment a PR opens. It traces execution flows, identifies vulnerable patterns, and highlights issues before they reach the main branch. - Follows Actual Data Flows
Rather than checking for generic patterns, Xygeni tracks input from sources to sinks. This ensures it only flags vulnerabilities that are truly reachable and relevant. - Gives Developers the Full Picture
Each issue includes CWE tags, severity levels, exploitability context, and file locations. That way, developers can understand and fix problems without extra guesswork. - Provides Fixes Without Losing Control
When possible, Xygeni suggests an AutoFix directly in the pull request. Developers review the patch, approve it, and stay fully in charge of what gets merged. - Prevents Risky Fixes From Introducing New Bugs
If a patch introduces new vulnerabilities or creates functional risks, Xygeni alerts the team before changes are merged. - Stops Unsafe Merges Automatically
You can define security policies that block merges when critical flaws are detected. This protects your codebase while keeping workflows smooth.
With Xygeni, your team gets fast, accurate, and context-aware static analysis. You find real threats early, fix them with confidence, and maintain code integrity without slowing down your releases.
Conclusion: Build Fast, Stay Secure, Own Your Code
Source code security is no longer optional. If you’re wondering how can I prevent the use of my source code without permission, the answer lies in visibility, automation, and early intervention. Attackers no longer wait for production. They exploit mistakes in pull requests, tampered packages, and misconfigured pipelines.
That’s why modern teams embed source code security scanning tools into their development workflows. Tools like Xygeni give developers real-time protection from logic flaws, malicious dependencies, leaked secrets, and CI/CD exploits, all without slowing down delivery.
To build fast and stay secure, you must shift left. Integrate security scanning into every commit, every merge, and every build. That way, your team keeps control of the code, the risks, and the release. Most importantly, you stop threats before they ever reach production.
Now is the time to harden your source code from the inside out.
Ready to get started? Explore Xygeni’s free trial