
Identify and remediate security, maintenance, and licensing issues in application dependencies before deploying your software.
Detect suspicious code sections and patterns exploited by attackers upon publication of new and updated dependencies.
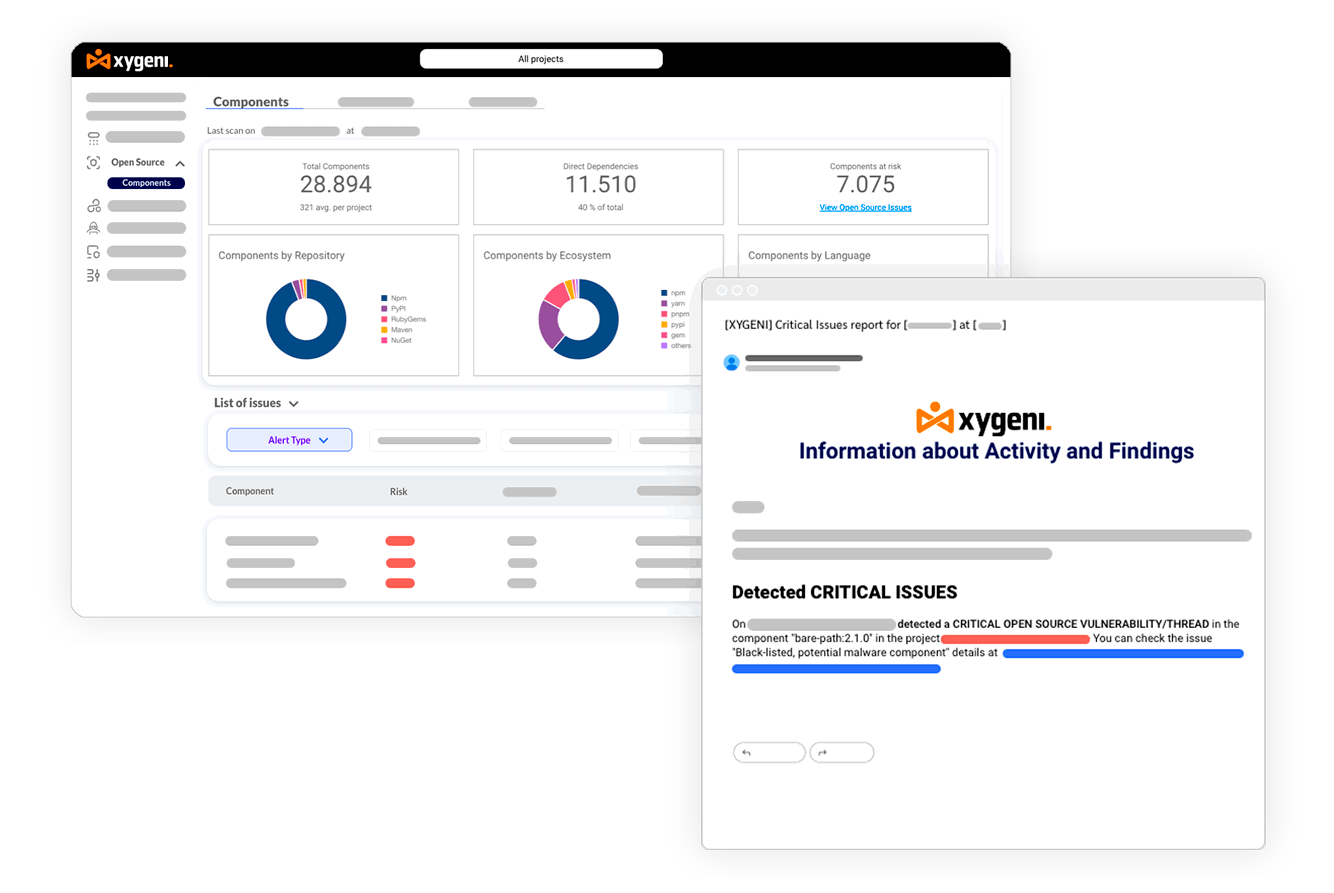
Prioritize vulnerabilities with the greatest business impact, and manage risks with context-based risk scoring and traceability from code to cloud.
Automatically upgrade to vulnerability-free open source dependencies with intelligent pull requests.







By combining Reachability Analysis with EPSS (Exploit Prediction Scoring System), Xygeni filters out vulnerabilities that are not reachable in your code execution path. This ensures teams only focus on exploitable risks, cutting down alert fatigue significantly.
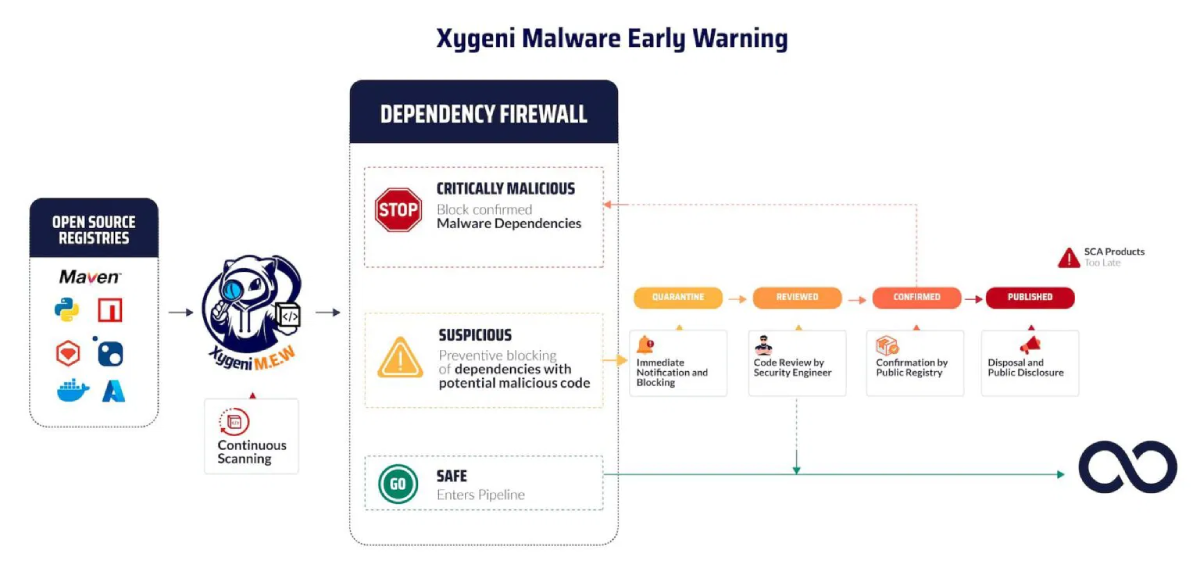
Xygeni continuously scans public registries like NPM, Maven, and PyPI in real-time. Using code behavior analysis, it automatically detects and quarantines zero-day malware before it enters your environment, acting as an early warning system against supply chain attacks.
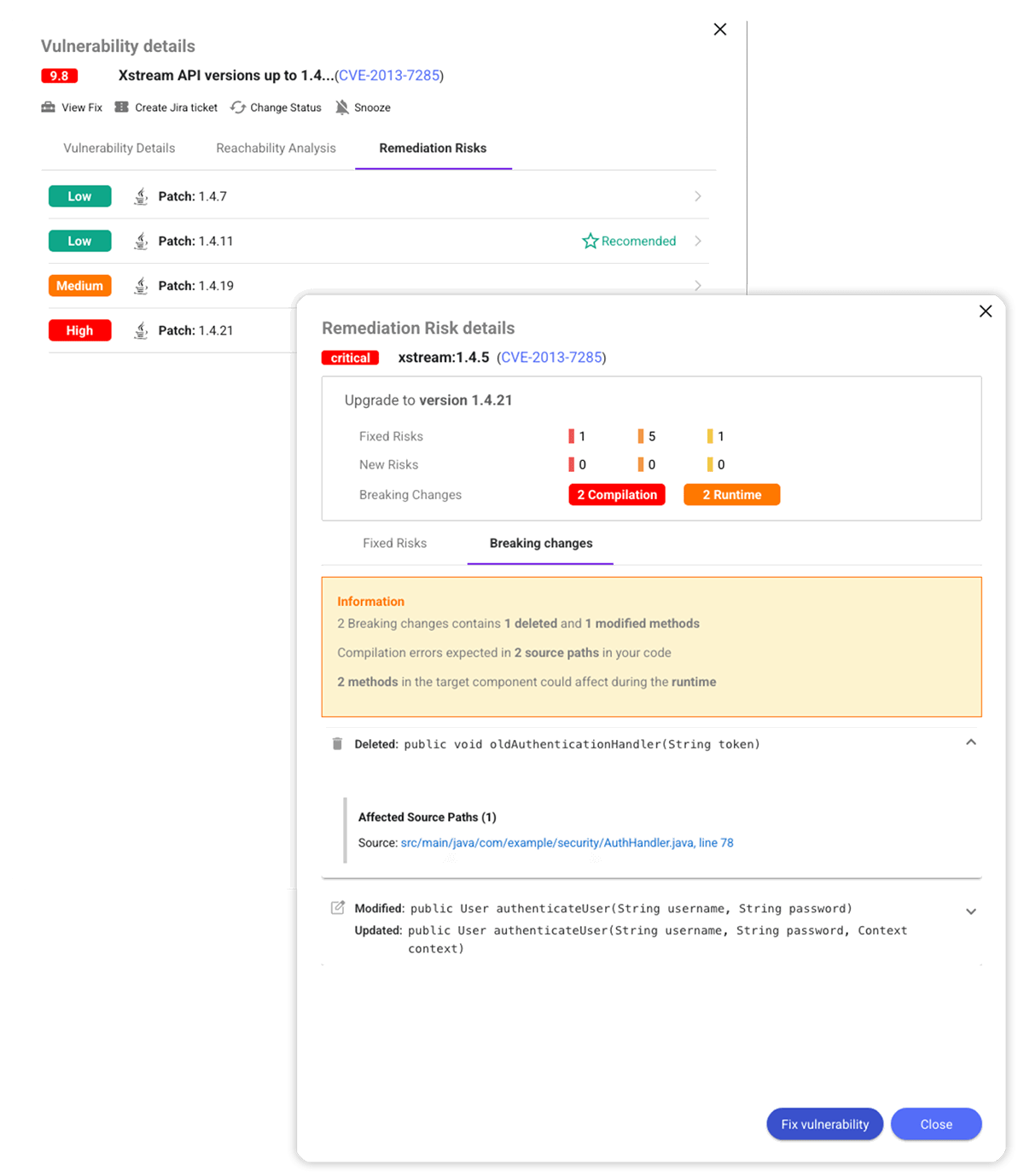
Xygeni provides a side-by-side comparison of patch options, showing not only the vulnerabilities fixed but also any new risks or breaking changes an upgrade might introduce. This ensures developers can choose the safest remediation path without disrupting application stability.
Yes. Xygeni generates Software Bill of Materials (SBOMs) in SPDX and CycloneDX formats, alongside Vulnerability Disclosure Reports (VDR). This ensures full compliance with global regulations like US Executive Order 14028, NIST guidelines, and EU Cybersecurity strategies.
Traditional tools only look for known vulnerabilities (CVEs). Xygeni goes further by detecting malicious code behaviors, such as typosquatting, dependency confusion, and suspicious scripts, protecting your supply chain from zero-day malware before it is even reported.