How Xygeni Supports the OWASP SAMM – Software Assurance Maturity Model
1. Introduction
The OWASP SAMM – Software Assurance Maturity Model provides a structured framework for assessing and improving software security maturity. It helps organizations implement best practices across the software development lifecycle (SDLC) while balancing security efforts with business objectives.
Xygeni accelerates OWASP SAMM adoption by integrating: Application Security Posture Management (ASPM), Software Composition Analysis (SCA), CI/CD Security, Infrastructure as Code (IaC) Security, Static Application Security Testing (SAST), Build Security, Secrets Management, and Anomaly Detection. These capabilities work together to provide real-time threat detection, automated policy enforcement, and risk-based prioritization. As a result, organizations can maintain continuous security across software development, deployment, and operations.
Moreover, this document explains how Xygeni supports organizations in achieving OWASP SAMM maturity. It covers key aspects such as automating security controls, making sure compliance, and mitigating risks across the SDLC.
2. OWASP SAMM Overview
2.1 The Five Business Functions of Software Assurance Maturity Model
The OWASP SAMM is structured into five business functions, each representing a critical aspect of software security. As a result, these functions serve as pillars for organizations to assess, improve, and mature their security practices across the software development lifecycle (SDLC).
Governance
Governance establishes security strategies, policies, compliance frameworks, and education initiatives to ensure a structured and measurable approach to software security. Moreover, it includes:
- Strategy & Metrics: Defining security objectives, measuring effectiveness, and aligning efforts with business goals.
- Policy & Compliance: Making sure adherence to internal security policies and external regulatory requirements.
- Education & Guidance: Raising security awareness and providing structured training across teams.
Design
The design function focuses on: threat identification, secure architecture, and defining security requirements early in the SDLC, which, as has been noted, aligns with the OWASP Software Assurance Maturity Model‘s emphasis on proactive security measures. Specifically, it includes:
- Threat Assessment: Evaluating security risks associated with applications and their environments.
- Security Requirements: Defining security expectations for software and third-party suppliers.
- Secure Architecture: Establishing resilient software architectures and secure technology management practices.
Implementation
Implementation ensures that security controls are embedded within the build, deployment, and defect management processes. In particular, this function emphasizes automation and secure software composition to reduce security risks. It includes:
- Secure Build: Enforcing security controls in CI/CD pipelines, managing dependencies, and preventing insecure code releases.
- Secure Deployment: Protecting application integrity during deployment and making sure secret management best practices.
- Defect Management: Systematically identifying, tracking, and remediating security defects.
Verification
Verification validates that security controls are correctly implemented and effective. As illustrated in OWASP SAMM, this function covers security testing methodologies, including:
- Requirements-driven Testing: making sure security controls meet specified security requirements.
- Security Testing: Conducting automated and manual security assessments to detect vulnerabilities.
Operations
The operations function ensures continuous monitoring, incident response, and operational security management to maintain software security throughout its lifecycle. To clarify, it includes:
- Incident Management: Detecting, responding to, and mitigating security incidents.
- Environment Management: Securing cloud and infrastructure configurations to minimize attack exposure.
- Operational Risk Management: Establishing continuous monitoring and risk prioritization for proactive security.
2.2 Understanding SAMM Maturity Levels
OWASP SAMM defines maturity levels (0-3) for each security practice,thus enabling organizations to improve their security posture progressively. The levels range from ad-hoc or non-existent practices (Level 0) to fully optimized and continuously improving security measures (Level 3).
Consequently, by aligning with OWASP SAMM’s business functions and maturity levels, organizations can measure their current security posture. Additionally, they can define clear improvement roadmaps and implement structured security enhancements to strengthen their software assurance efforts.
3. Xygeni’s Alignment
Xygeni aligns with OWASP Software Assurance Maturity Model five business functions by automating security enforcement, enabling data-driven risk prioritization, and strengthening incident management and governance.
- Governance: ASPM enhances risk visibility, policy enforcement, and compliance management, making sureorganizations measure and enforce security policies in accordance with OWASP SAMM security governance principles.
- Design: Dynamic threat assessment and risk prioritization focus remediation efforts on vulnerabilities based on exploitability, reachability, and business impact, directly supporting OWASP Software Assurance Maturity Model proactive risk management approach.
- Implementation:
- SCA, CI/CD Security, and SAST integrate security into software builds and deployments, making sure early vulnerability detection.
- Build Security provides software attestations for integrity validation.
- Secrets Detection protects credentials across CI/CD pipelines and infrastructure configurations.
- Verification:
- Security Gates enforce Go/No-Go decisions, making suresecurity compliance before deployment.
- CI/CD Security enforces infrastructure hardening, reducing misconfigurations and configuration drift.
- ASPM Inventory makes sure to consistently apply security tools across pipelines.
- Operations: Anomaly Detection and Code Tampering Protection provide real-time incident monitoring, making surefast response to security threats and unauthorized modifications, in alignment with OWASP SAMM’s operational security principles.
The diagram below highlights the security practices that Xygeni can support.
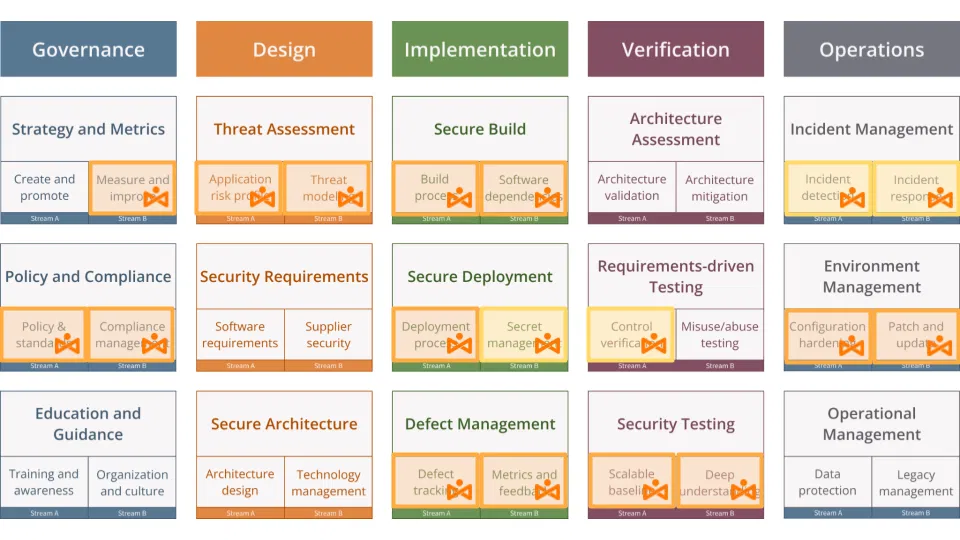
The following sections provide a detailed view of how Xygeni supports each OWASP Software Assurance Maturity Model business function, helping organizations advance their security maturity and maintain secure software development practices.
3.1 Governance
Xygeni strengthens security governance by providing visibility into risk trends, automating policy enforcement, and embedding security awareness into development workflows. Following the principles of OWASP SAMM, Xygeni ensures that organizations can track, enforce, and continuously improve their security posture through Strategy and metrics, Policy and compliance, and Education and guidance.
Strategy & Metrics
Understanding security trends and measuring remediation effectiveness are critical for aligning security efforts with business objectives. In addition, In line with OWASP SAMM, Xygeni’s Application Security Posture Management (ASPM) provides a centralized view of security risks, enabling organizations to track vulnerability trends, assess remediation effectiveness, and measure security improvements over time.
Moreover, Xygeni analyzes the exposure window, determining how long vulnerabilities remain open before resolution. As a result, Security teams can optimize response times, improve risk mitigation strategies, and enforce SLAs for security fixes by identifying remediation delays.
Furthermore, Security dashboards provide real-time KPIs, offering complete visibility into security program performance and enabling leadership to make data-driven decisions to enhance security posture.
Policy & Compliance
Automating compliance across development, build, and deployment pipelines is essential for governance. To achieve this, Xygeni automates policy enforcement, integrating security frameworks such as NIST, CIS, and OpenSSF into SDLC processes.
Security policies are enforced directly within CI/CD pipelines, preventing non-compliant builds and deployments from progressing. Consequently, compliance tracking provides real-time visibility into policy adherence, enabling organizations to identify and remediate gaps before they become risks. By applying risk-based enforcement, Xygeni prioritizes high-impact violations while reducing noise from lower-risk policy deviations, making sure security teams focus on what truly matters.
Education & Guidance
Building a security-first culture requires that security insights are accessible and actionable within development workflows. For this reason, Xygeni provides real-time security guidance, helping teams adopt best practices in accordance with OWASP SAMM, without disrupting productivity.
Contextualized remediation recommendations ensure developers understand and fix vulnerabilities efficiently, reducing back-and-forth between security and engineering teams. At the same time, To prevent insider risks and enforce security accountability, Xygeni tracks contributor roles and enforces least privilege access, making sure that sensitive operations are restricted to authorized users.
Governance’s Key Takeaways
- Full risk visibility with real-time security dashboards and exposure tracking.
- Automated compliance enforcement within CI/CD to prevent policy violations.
- Embedded security awareness through contextual remediation and least privilege controls.
3.2 Design
Xygeni enhances threat assessment by enabling structured risk evaluation, automated prioritization, and continuous monitoring. Specifically, In alignment with OWASP Software Assurance Maturity Model, Xygeni leverages ASPM’s prioritization funnels, reachability analysis, and exploitability scoring to help organizations systematically identify, assess, and manage security risks. As a result, decisions remain data-driven and aligned with business objectives.
Structured Risk Identification and Visibility
To begin with, Practical threat assessment begins with understanding the risk landscape. In the context of OWASP SAMM, Xygeni provides real-time vulnerability insights to classify risks based on their severity, exploitability, and impact. Furthermore, Security teams can track and monitor risk exposure through automated security dashboards, making sure that leadership has clear visibility into potential threats across the software supply chain.
By doing so, organizations establish a centralized view of security risks, organizations can measure the effectiveness of security programs and ensure that remediation efforts address high-priority vulnerabilities. This structured approach allows teams to move beyond ad-hoc risk management and adopt a systematic, scalable threat assessment process.
Automated Prioritization and Reachability Analysis
As security programs mature, organizations need a standardized risk management framework prioritizing real threats over theoretical vulnerabilities. Following OWASP SAMM guidelines, Xygeni automates this process by implementing customizable prioritization funnels that filter vulnerabilities based on business impact, compliance relevance, and exploitability.
In addition, reachability analysis ensures that vulnerabilities are prioritized based on whether they can actually be exploited in the organization’s specific environment. Instead of treating all security issues equally, Xygeni focuses remediation on vulnerabilities that pose the greatest real-world risk, reducing alert fatigue and enabling targeted security interventions.
Additionally, exploitability scoring enhances risk assessment by evaluating how likely a vulnerability will be used in real-world attacks. Security teams can allocate resources more efficiently, addressing critical risks before attackers can exploit them.
Continuous Optimization and Adaptive Risk Management
A potent threat assessment strategy evolves alongside the organization’s risk landscape. As outlined in the OWASP Software Assurance Maturity Model, Xygeni enables continuous refinement of prioritization funnels, enabling that security teams can adapt their risk posture as new threats emerge.
Moreover, Historical security metrics and remediation trends are leveraged to fine-tune risk reduction strategies, and the security investments yield measurable improvements. Over time, policy-driven enforcement aligns security decisions with business risk tolerance while security controls remain proactive rather than reactive.
Design Key Takeaways
- Intelligent risk prioritization focuses on vulnerabilities with real-world impact.
- Continuous threat assessment integrates exploitability, reachability, and business impact.
- Automated risk scoring and remediation guidance streamline security decision-making.
3.3 Implementation
3.3.1 Secure Build
Xygeni strengthens secure build practices by integrating automated security controls and dependency management and by building integrity validation directly into CI/CD pipelines.
In alignment with OWASP SAMM, Xygeni ensures that every build follows a repeatable, policy-driven, and verifiable security process through Software Composition Analysis (SCA), Static Application Security Testing (SAST), Secrets Management, and Build Security.
Additionally, CI/CD security validation consistently applies essential security tools across the pipeline, reducing risk exposure.
Consistency and Repeatability in the Build Process
A secure build process requires standardization, automation, and continuous validation. As has been noted, the OWASP Software Assurance Maturity Model highlights the importance of standardized build security. Accordingly, Xygeni enforces standardized build policies through CI/CD security validation, forcing every build to apply required security tools, such as SAST, SCA, and secrets scanning before proceeding.
Moreover, Xygeni establishes build attestations to verify software integrity, validate software provenance, and prevent tampered or unverified artifacts from progressing through the pipeline. For this reason, organizations achieve consistency and repeatability, reducing human error and improving overall software quality.
Automating Security Controls in the Build Pipeline
Security automation is essential for detecting and remediating risks early in development. Following OWASP SAMM principles, Xygeni integrates SAST to detect vulnerabilities in code before deployment, addressing security issues at the earliest stage possible. Additionally, secrets scanning prevents the accidental exposure of credentials by continuously analyzing source code, configuration files, and build logs.
Furthermore, CI/CD security validation ensures that build environments and tooling follow security best practices. For example, Xygeni enforces least privilege policies and restricts unnecessary access. Consequently, security bottlenecks are eliminated while maintaining high development velocity through automated security checks within the pipeline.
Preventing Security Defects from Reaching Production
Unverified or insecure artifacts must never reach production. In alignment with OWASP SAMM, Xygeni enforces security gates that automatically fail builds containing critical vulnerabilities, exposed secrets, or compliance violations. By integrating security directly into CI/CD, only secure and compliant artifacts proceed to deployment.
Additionally, Xygeni integrates malware detection within the build process to further protect build integrity. By doing so, it identifies unauthorized modifications, supply chain attacks, or suspicious activity within CI/CD workflows. As a result, organizations mitigate risks by preventing security defects from entering production before they escalate into real-world threats.
Managing Software Dependencies with Security Controls
Modern applications rely heavily on third-party and open-source dependencies, making dependency security a critical aspect of secure builds. Xygeni enables automated software supply chain risk management, continuously tracking, validating and monitoring every dependency.
To illustrate, Software Bill of Materials (SBOMs) provide organizations with complete visibility into software components, helping security teams identify outdated dependencies, licensing violations, and potential risks. Real-time monitoring detects malicious packages, unauthorized modifications, and vulnerabilities, reducing exposure to supply chain attacks.
Automating Dependency Security Validation
Not all vulnerabilities require immediate remediation. Therefore, Xygeni’s SCA with reachability analysis ensures that security teams prioritize only the vulnerabilities that pose a real threat to the application. Instead of overwhelming teams with alerts, Xygeni automates risk assessment,thus enabling smarter decision-making.
To maintain strict security hygiene, Following OWASP SAMM guidelines Xygeni enforces automated security policies that flag and block risky dependencies during the build process, preventing insecure components from being introduced.
Security Gates and Remediation for Dependencies
To prevent supply chain risks, Xygeni implements security gates that block builds containing unapproved dependencies or high-risk vulnerabilities. Automated remediation workflows streamline dependency updates, and apply security fixes without disrupting development.
By analyzing dependencies for backdoors, hidden malware, or suspicious behavior, Xygeni applies zero-trust security principles to third-party code. As a result, the likelihood of supply chain compromise is significantly reduced.
Secure Build Key Takeaways
- Standardized security enforcement ensures all builds follow policy-driven security checks.
- Build attestation and dependency validation prevent tampered or vulnerable artifacts.
- Secrets scanning and malware detection safeguard software supply chain integrity.
3.3.2 Secure Deployment
Aligned with OWASP SAMM, Xygeni ensures secure, policy-driven deployments by automating security verification, compliance controls, and detecting unauthorized changes. By integrating CI/CD Security, Infrastructure-as-Code (IaC) Security, and Anomaly Detection, Xygeni prevents misconfigurations, unauthorized modifications, and credential exposure, making sure that only verified and secure applications reach production.
Automating Deployment Security and Enforcing Compliance
A secure deployment process requires continuous security validation at every stage of CI/CD. Following OWASP Software Assurance Maturity Model guidelines, Xygeni integrates security verification mechanisms within pipelines, making sure that all deployments comply with security policies and industry best practices.
Deployment configurations are automatically validated against predefined security policies, preventing misconfigurations that could introduce vulnerabilities. Following OWASP SAMM recommendations, CI/CD security validation consistently applies essential security checks—SAST, SCA, secrets scanning, and compliance enforcement—across all deployment stages, eliminating security blind spots.
Xygeni validates IaC templates and deployment scripts to protect cloud environments and infrastructure configurations, making sure that all infrastructure is provisioned securely and adheres to organization-wide security baselines. Security gates provide automated enforcement, blocking deployments that contain high-risk vulnerabilities, policy violations, or misconfigurations, making sure that only secure artifacts reach production.
Verifying Deployment Integrity and Detecting Unauthorized Changes
OWASP Software Assurance Maturity Model emphasizes the importance of deployment integrity, Xygeni implements deployment attestations to ensure that only trusted and untampered software enters production. These attestations verify the provenance and integrity of software artifacts, preventing the introduction of unverified components or compromised code into live environments.
Xygeni continuously monitors deployment processes to detect unauthorized modifications, identifying anomalous changes in pipeline configurations, infrastructure settings, and deployment workflows. This proactive anomaly detection reduces the risk of insider threats, misconfigurations, and supply chain attacks, preventing unauthorized changes from affecting production environments.
CI/CD workflows are continuously tracked for deviations from security policies, making sure that every deployment follows authorized and secure processes. If deviations are detected, Xygeni flags the issue, providing detailed security insights and automated mitigation recommendations to restore compliance.
Preventing Secrets Exposure in Deployment Pipelines
Sensitive credentials such as API keys, access tokens, and encryption secrets must remain protected throughout deployment. The OWASP Software Assurance Maturity Model recommends secure secret management, and Xygeni enhances secrets security by detecting and mitigating credential leaks in deployment environments before they can be exploited.
Xygeni scans files, pipelines, configuration scripts, and environment variables for embedded secrets, preventing accidental exposure across SCM, CI/CD workflows, and infrastructure configurations. SCM history audits enable security teams to identify previously committed secrets that remain accessible, making sure they adequately handle legacy credentials.
Xygeni validates detected secrets to prioritize remediation efforts, distinguishing between active and inactive credentials. Security teams can quickly contain real risks by focusing on valid, exploitable secrets instead of chasing false positives.
If a valid secret is exposed, Xygeni enables automated remediation by:
- Security playbooks trigger revocation, rotation, or custom mitigation actions, neutralizing compromised credentials.
- Systems block deployments containing exposed secrets, preventing the release of compromised applications into production
- Providing detailed audit logs of detected secrets and remediation actions, making sure compliance with security policies and regulatory requirements.
Secure Deployment Key Takeaways
- Automated security validation ensures compliant deployments in CI/CD.
- Infrastructure-as-Code (IaC) scanning prevents misconfigurations before production.
- Real-time anomaly detection flags unauthorized changes and security deviations.
3.3.3 Defect Management
Aligned with OWASP Software Assurance Maturity Model (OWASP SAMM), Xygeni enhances defect management by automating security issue tracking, prioritizing vulnerabilities based on actual risk, and integrating remediation workflows. By leveraging Application Security Posture Management (ASPM), Prioritization Funnels, and CI/CD Security, organizations can identify, categorize, and resolve security defects efficiently. As a result, they reduce exposure to exploitable risks and compliance violations.
Tracking and Managing Security Defects
Without a doubt, a fragmented view of security issues can lead to missed vulnerabilities, inconsistent remediation, and ineffective risk management. To address this, Xygeni provides a centralized view of security defects, consolidating findings from SAST, SCA, IaC security, and CI/CD security scans into a single risk management interface.
Furthermore, by correlating security issues across multiple sources, Xygeni ensures that security teams gain complete visibility into application risks, avoiding duplicate alerts or oversight of critical defects. Defects are categorized based on business impact, exploitability, and technical severity, allowing organizations to prioritize meaningful fixes while reducing alert fatigue.
Moreover, Xygeni facilitates issue lifecycle management to streamline remediation efforts. It enables teams to track, assign, and resolve defects internally or via external ticketing systems such as Jira and messaging platforms like Slack. This ensures security issues are appropriately managed within existing development workflows, improving coordination between security and engineering teams.
Automated Prioritization and Risk-Based Defect Handling
Without structured prioritization, security teams face overwhelming alerts that do not present immediate threats. OWASP Software Assurance Maturity Model (OWASP SAMM) recommends risk-based vulnerability management, and Xygeni addresses this by integrating Prioritization Funnels, allowing organizations to filter security defects based on real-world risk factors such as reachability, exploitability, and business impact.
To ensure efficiency, Xygeni prioritizes vulnerabilities that are actively exploitable in production environments. In this way, security teams focus on the most critical threats while deprioritizing issues with minimal or no real-world risk. In addition, automated policy enforcement ensures that deployments are blocked if unresolved critical defects are detected, preventing high-risk vulnerabilities from reaching production.
Streamlining Remediation and Continuous Improvement
Fixing security defects efficiently requires seamless integration with developer workflows and automation to reduce manual effort. As part of OWASP SAMM’s continuous security improvement principles,Xygeni accelerates security defect resolution by directly embedding actionable security guidance into CI/CD pipelines. Thus, developers receive contextual remediation recommendations without disrupting their workflows.
Furthermore, to eliminate repetitive manual tasks, Xygeni automates remediation actions, triggering playbook-driven fixes for common vulnerabilities. This reduces the time and effort required to address security issues, allowing teams to focus on complex, high-impact threats.
To sum up, Xygeni tracks remediation efficiency, measuring time-to-fix and overall risk reduction trends. This enables organizations to continuously refine their security posture, identify process bottlenecks, and improve response times, making sure that security defects are managed proactively rather than reactively.
Defect Management Key Takeaways
- Centralized security issue tracking eliminates fragmentation in vulnerability management.
- Prioritization Funnels ensure teams focus on exploitable, high-impact risks.
- Automated remediation workflows accelerate security defect resolution.
3.4 Verification
Xygeni strengthens verification processes by embedding Requirements-Driven Testing and Security Testing into development workflows. By automating security enforcement in CI/CD, prioritizing vulnerabilities based on risk, and integrating security validation at every stage, Xygeni ensures that security becomes an integral part of software delivery rather than a last-minute checkpoint.
Requirements-Driven Testing
Since, security tests must be defined and systematically applied across all stages of development. OWASP SAMM emphasizes structured security validation, and Xygeni ensures that security requirements are automatically enforced by integrating checks into CI/CD pipelines.
As a result, Every build undergoes validation through static application security testing (SAST) for code vulnerabilities, software composition analysis (SCA) for dependency risks, secrets scanning to prevent credential exposure, and infrastructure-as-code (IaC) security checks for configuration validation.
Furthermore, security gates act as enforcement mechanisms, automatically blocking builds if security tests are missing or fail predefined policies. Xygeni tracks test coverage across applications, making sure all components are continuously validated against security requirements.
Organizations identify gaps and immediately receive automated recommendations to close them. Xygeni ensures the consistent application of security tests, eliminating inconsistencies and blocking untested software from reaching production.
Scalable Baseline for Security Testing
For this purpose, Automated security testing must remain consistent and scalable to keep up with fast development cycles.
Automated security testing must stay consistent and scalable to match fast development cycles. Xygeni aligns with OWASP Software Assurance Maturity Model guidelines. It integrates automated security scans at every CI/CD stage. This approach allows teams to detect vulnerabilities as early as possible.
Moreover, Xygeni also prevents security regressions by automatically tracking fixed vulnerabilities and making sure they do not reappear in future versions. This regression testing helps teams maintain security improvements over time. By embedding security testing directly into CI/CD, Xygeni eliminates manual bottlenecks and ensures security validation happens without disrupting development.
Deep Understanding and Risk-Based Prioritization
Not all vulnerabilities pose the same level of risk. OWASP SAMM recommends a risk-based approach to security validation, and Xygeni aligns with this methodology by making sure that high-impact components receive deeper scrutiny. Security teams enrich scans with business impact assessments, helping them focus on exploitable, reachable vulnerabilities relevant to the application.
Since prioritization is dynamic, it is continuously refined as threats evolve. If an exploit emerges in the wild or a vulnerability becomes more critical, its priority is adjusted automatically, triggering immediate revalidation and security enforcement.Thus, this risk-aware approach allows security teams to allocate resources where needed, balancing automated testing with targeted manual reviews.
Integrated Security Testing in Development Workflows
Security testing must be seamlessly integrated with developer workflows to be effective. Accordingly, Xygeni ensures that detected vulnerabilities can be assigned to developers via integrations with ticketing systems like Jira and messaging platforms like Slack. Security findings are directly linked to remediation workflows, allowing teams to act on them before deployment.
Verification Key Takeaways
- CI/CD-integrated security gates enforce compliance before code reaches production.
- Automated and risk-driven security testing detects vulnerabilities early.
- Continuous security validation prevents regressions and improves test effectiveness.
3.5 Operations
Xygeni strengthens operations security by enabling real-time anomaly detection, secure infrastructure management, and automated vulnerability remediation. Through Incident and Environment Management, Xygeni ensures that security incidents are detected and mitigated swiftly while keeping application environments hardened and up to date.
Incident Management
Security incidents often go undetected for long periods, allowing attackers to exploit vulnerabilities and cause damage. Xygeni significantly reduces this risk by integrating anomaly detection and code tampering protection, making sure early identification of security threats and unauthorized modifications.
Real-Time Incident Detection
Xygeni enhances incident detection with real-time monitoring of software development environments. It continuously analyzes activities across CI/CD pipelines, source code repositories, and deployed applications.
The anomaly detection system identifies unauthorized access attempts, unusual file modifications, and deviations from normal activity patterns. This proactive approach minimizes dwell time and ensures organizations detect security incidents before they escalate.
Code Tampering Detection
Guaranteeing application integrity is crucial to preventing security breaches. Additionally, Xygeni’s code tampering detection actively monitors for unauthorized changes to source code, build artifacts, and deployment scripts.
If an attacker attempts to modify application logic or inject malicious payloads, Xygeni immediately alerts security teams. This allows organizations to gain full visibility into attempted exploits and respond before attackers compromise software.
Automated Incident Response
Xygeni streamlines incident response through automated workflows and integrations with security orchestration tools. Security teams can seamlessly link detected threats to incident response platforms, guaranteeing structured handling through:
- Automated containment actions
- Forensic analysis
- Playbook-driven responses
By automating threat detection and response, Xygeni helps organizations contain threats swiftly and minimize operational impact.
Operations Key Takeaways
- Real-time anomaly detection minimizes incident dwell time.
- Code tampering protection prevents unauthorized modifications.
- Automated response workflows streamline incident containment and recovery.
Environment Management
Securing operational environments requires not only consistent enforcement of hardened configurations but also rapid remediation of vulnerabilities. Therefore, Xygeni ensures that CI/CD pipelines enforce security baselines across all infrastructure and development environments, reducing exposure to misconfigurations and outdated software.
Moreover, configuration hardening is automated through CI/CD security validation, making sure that all infrastructure components, including build environments, cloud configurations, and runtime dependencies, adhere to security best practices. At the same time, Xygeni continuously monitors infrastructure-as-code (IaC) templates, deployment scripts, and security policies to detect deviations from established baselines. Consequently, Xygeni flags any misconfigurations as security defects, preventing insecure configurations from reaching production.
Furthermore, patching and updating is accelerated through automated remediation capabilities, making sure that vulnerabilities in application dependencies and infrastructure components are addressed on time. In addition, Xygeni integrates risk-based prioritization into vulnerability management, making sure that critical security patches and updates are applied first. Organizations can automate remediation workflows, link security defects to issue tracking systems, and enforce patch compliance within CI/CD pipelines.
Environment Management Key Takeaways
- CI/CD-driven configuration hardening ensures secure infrastructure baselines.
- Automated patching and remediation accelerate vulnerability resolution.
- Continuous compliance monitoring keeps environments secure and up to date.
4. Conclusion
In summary, Xygeni simplifies OWASP OWASP Software Assurance Maturity Model implementation by integrating automated security enforcement, risk-based prioritization, and continuous monitoring into the software development lifecycle (SDLC). By embedding security controls into governance, design, implementation, verification, and operations, organizations can systematically improve their security posture without disrupting development speed.
As a result, by implementing OWASP SAMM with Xygeni, organizations achieve:
- Continuous risk tracking and compliance automation through real-time visibility, policy enforcement, and security governance.
- Strategic risk prioritization and threat assessment with dynamic risk scoring, exploitability analysis, and targeted remediation workflows.
- Automated security enforcement across builds and deployments, making certain of secure artifact attestations, dependency validation, and CI/CD security integration.
- Robust security validation and real-time verification through Security Gates, automated security testing, and ASPM-driven compliance enforcement.
- Proactive incident management and infrastructure security, leveraging real-time anomaly detection, code tampering protection, and automated remediation workflows.
Furthermore, with automated risk prioritization, security-driven enforcement, and integrated monitoring, Xygeni enables organizations to streamline SAMM adoption and ensure software security maturity scales efficiently alongside business growth.
Consequently, organizations achieve immediate improvements in governance, security testing, compliance automation, and risk mitigation, reducing exposure to software supply chain attacks, misconfigurations, and operational threats with Xygeni.
Ultimately, OWASP SAMM adoption becomes streamlined, measurable, and scalable, allowing security and development teams to enhance security maturity without slowing innovation.
Additional Resources
For further insights into software security best practices and OWASP SAMM implementation, explore the following resources:








