Introduction: Why Application Security Testing Matters
If you build software, security for software development isn’t just an add-on—it’s a must. As cyber threats evolve daily, application security testing plays a crucial role in catching vulnerabilities early, making sure safer software development. However, detecting issues is only half the battle. More importantly, how do you fix them? To answer this, we will explore different types of application security testing, best practices in security testing in software development, and remediation strategies that will help you ship secure code efficiently.
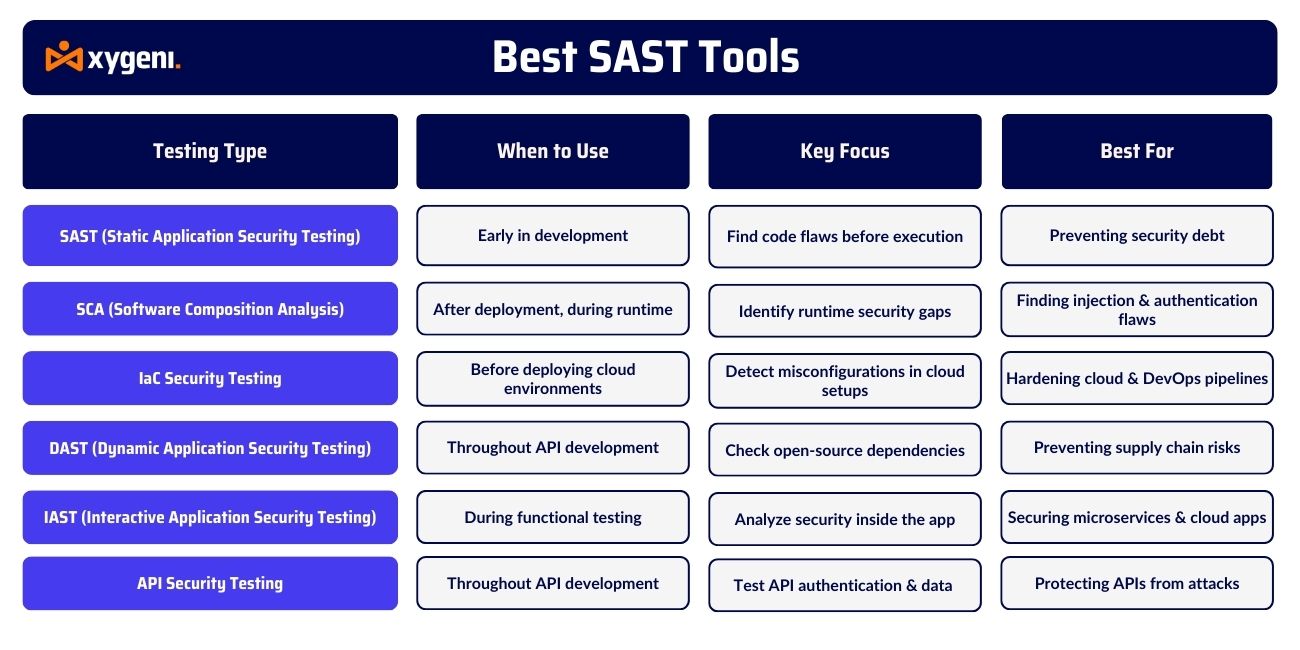
Types of Application Security Testing
Security for software development requires more than just a single testing approach. Securing applications isn’t a one-size-fits-all process. Instead, various application security testing methods help uncover vulnerabilities at different stages of the software development lifecycle (SDLC).
By layering these security approaches, teams can strengthen applications, reduce security risks, and prevent vulnerabilities before attackers exploit them. Each method plays a unique role in securing software, ensuring protection from code development to deployment.
Let’s take a closer look at the most effective types of application security testing and how they help teams build safer software.
1. Software Composition Analysis (SCA)
In addition to analyzing proprietary code, modern applications rely heavily on open-source libraries. While these components can be beneficial, they may introduce security risks. That’s where Software Composition Analysis comes in—it helps teams continuously monitor third-party dependencies for vulnerabilities and licensing issues.
When to Use: Continuously, across the SDLC.
How It Works: Scans open-source dependencies for known vulnerabilities and outdated components.
Best For: Preventing supply chain attacks and ensuring compliance with security standards.
2. Static Application Security Testing (SAST)
First and foremost, catching security flaws early in development is critical. SAST allows developers to identify vulnerabilities before the code is even executed, making sure that issues are resolved before they become costly problems.
When to Use: Early in development (shift-left security).
How It Works: Scans code before execution, detecting vulnerabilities in source, bytecode, or binaries.
Best For: Identifying code-level flaws before deployment.
3. Infrastructure as Code (IaC) Security Testing
With the rapid adoption of cloud environments, securing infrastructure configurations is just as important as securing application code. IaC security testing ensures misconfigurations are detected and corrected before deployment.
When to Use: Before deploying cloud environments.
How It Works: Scans Terraform, CloudFormation, Kubernetes, and Docker files for security risks.
Best For: Ensuring secure cloud-native applications and DevOps pipelines.
4. Dynamic Application Security Testing (DAST)
Unlike SAST, which analyzes static code, DAST takes a different approach by testing applications while they run. By simulating real-world attacks, DAST identifies security gaps that only appear during execution.
When to Use: After deployment, during runtime.
How It Works: Attacks the app like a hacker would, detecting security weaknesses in a live environment.
Best For: Finding injection attacks, authentication flaws, and misconfigurations.
5. Interactive Application Security Testing (IAST)
Some vulnerabilities can slip through both static and dynamic testing. To bridge the gap, IAST provides real-time security analysis during application execution, allowing teams to detect vulnerabilities dynamically while preserving code context.
When to Use: During functional testing.
How It Works: Uses real-time analysis inside the application to identify security risks.
Best For: Microservices, containerized apps, and cloud-native applications.
6. API Security Testing
As APIs become the backbone of modern applications, they are increasingly targeted by cyberattacks. API security testing ensures that endpoints remain protected from misconfigurations and no authorized access.
When to Use: Throughout API development.
How It Works: Scans for weak authentication, improper configurations, and data exposure.
Best For: Preventing API-related security threats and data leaks.
Best Practices in Security Testing for Software Development
Securing applications isn’t just about running tests—it’s about making security a natural part of the development process. By following these best practices, teams can catch vulnerabilities early, automate security checks, and focus on fixing real threats without slowing down development.
1. Shift Security Left
Security should start early in the development lifecycle, not after deployment.
- Run SAST and SCA scans as soon as code is written to prevent security issues from reaching production.
- Give developers actionable feedback so they can fix vulnerabilities before they become major risks.
2. Automate Security in CI/CD Pipelines
Security should work at DevOps speed, not slow it down.
- Integrate SAST, DAST, and SCA into your CI/CD pipelines to scan every code commit automatically.
- Use policy-based controls to stop insecure code from getting deployed.
3. Secure Your Dependencies
Modern applications depend on open-source software, which can introduce hidden security risks.
- Automate SCA scanning to detect vulnerable third-party libraries before they become a problem.
- Remove outdated dependencies and apply patches as soon as they become available.
4. Prioritize Vulnerabilities by Risk
Not all vulnerabilities are equal—focus on fixing what actually matters.
- Use EPSS scoring and reachability analysis to prioritize exploitable risks over minor issues.
- Reduce alert fatigue by filtering out low-impact security warnings.
5. Monitor for Anomalies in Real Time
Security threats don’t stop when code is deployed—continuous monitoring is key.
- Use real-time anomaly detection to track unauthorized changes in CI/CD pipelines and cloud configurations.
- Catch and fix security drifts before they lead to a breach.
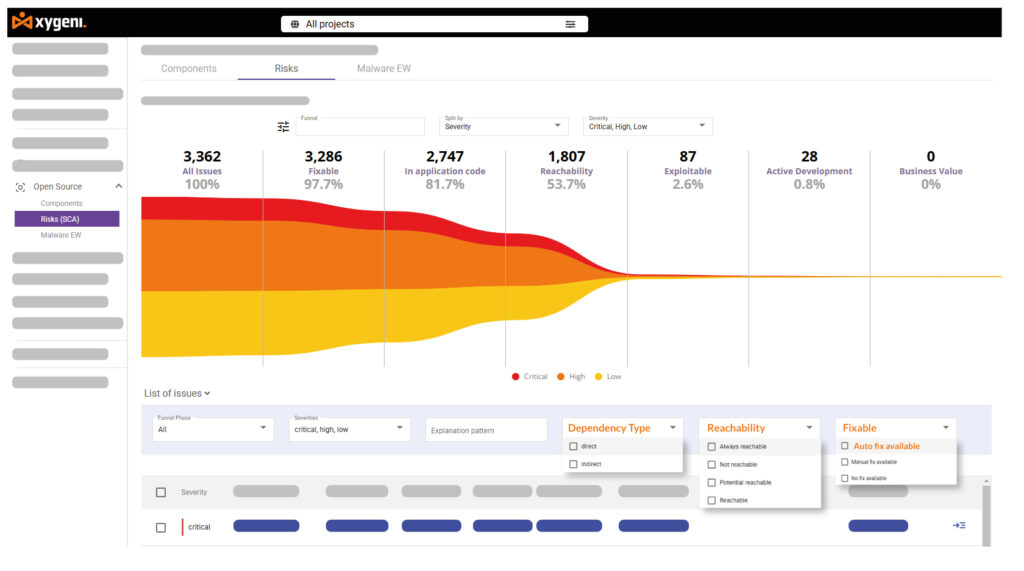
What Is EPSS and Why It Matters
Not every vulnerability is a real threat, and security teams can’t fix everything at once. The Exploit Prediction Scoring System (EPSS) helps prioritize vulnerabilities based on real-world exploitability, making sure teams focus on the most likely attacks.
- How It Works: Instead of treating all vulnerabilities the same, EPSS assigns a risk score based on actual exploit trends. As a result, teams can fix critical issues first before attackers take advantage of them.
- Why It’s Useful: With thousands of new vulnerabilities appearing daily, EPSS filters out non necessary alerts so teams can focus on high-risk issues instead of spending time on minor threats.
- How Xygeni Uses It: To improve EPSS, Xygeni makes sure reachability analysis is included, providing teams to fix only exploitable vulnerabilities while avoiding low-impact alerts.
By using EPSS, Xygeni helps security and DevOps teams fix the right issues—faster and smarter.
Xygeni Application Security Testing Tools
At Xygeni, we believe security should empower development, not slow it down. Our Application Security Testing solutions are built for speed, accuracy, and seamless DevOps integration. Here’s what makes Xygeni stand out:
- Best-in-Class SAST – Detect vulnerabilities before code runs and fix security issues early to reduce technical debt.
- Intelligent SCA – Monitor open-source dependencies in real-time, preventing supply chain attacks.
- Effortless DevOps Integration – Works with Jenkins, GitHub Actions, GitLab CI/CD, Bitbucket Pipelines, and Azure DevOps for automated security scans.
- Smart Prioritization, Not Noise – EPSS scoring and reachability analysis ensure teams fix what matters, not false alerts.
- Faster Fixes with Automation – Remediation guidance speeds up resolution, keeping developers productive.
With Xygeni, teams build secure software without complexity—so they can ship faster, with confidence.
Conclusion: Smarter Security for Application Security Testing
Security for software development isn’t just about finding vulnerabilities—it’s about fixing them efficiently without slowing down releases. Using the right Types of Application Security Testing and best practices in security testing for software development, teams can make security a seamless part of their workflow.
To simplify security without compromise, teams should:
- Integrate security early to prevent vulnerabilities before they become costly.
- Automate security in CI/CD pipelines to catch issues before deployment.
- Monitor dependencies with SCA to avoid supply chain risks.
- Focus on real threats using EPSS and reachability analysis.
- Test APIs and infrastructure continuously to prevent security gaps.
At Xygeni, security keeps up with DevOps—fast, efficient, and built for modern development teams.
Want to secure your software without roadblocks? Contact Xygeni today and level up your security strategy.