What Is Dosfuscation? Why Developers Should Pay Attention
Here’s a quick threat snapshot: imagine reviewing a PR that looks like a small utility update. Buried inside, a contributor added what appears to be a harmless helper script. But on merge, it runs during the CI pipeline and triggers a loop that silently consumes all memory, crashing the build.
Dosfuscation is a type of internal denial-of-service (DoS) attack disguised using code obfuscation techniques. It combines logic designed to break execution, like infinite loops or memory bloat, with tactics that hide its real behavior, making it difficult to detect during reviews or audits. This isn’t an external hit; it’s already inside your code, waiting to blow up your build or production run.
Why care? Unlike traditional types of denial of service attacks that flood your servers with traffic, dosfuscation hides in plain sight, often passing code review or package audits. It’s a logic bomb baked into your pipeline.
Real example: An npm package contains a disguised infinite loop. It passes installs fine, but hogs memory in production until your app crashes. This demonstrates how dosfuscation, powered by obfuscation techniques, becomes a stealth variant of the most damaging types of denial of service attacks.
Typical DoS vs. Dosfuscation: Real Differences in Risk
Dosfuscation is a subtype of denial-of-service attacks. It differs from traditional types of denial of service attacks by executing internally via obfuscated code, not network traffic.
Picture this: You approve a PR in GitHub. Tests pass, build kicks off, then your runner hangs. You’re debugging a failing GitHub Actions job that keeps timing out. Turns out, a dosfuscated payload in a minor dependency introduced an infinite loop right in the postinstall script.
When developers think about denial of service, they usually picture an outside-in scenario, like a swarm of malicious requests hammering an API or botnets exhausting bandwidth. These are the classic types of denial of service attacks, and most of us are ready for them. We have WAFs in place, apply rate limiting, and build a scalable infrastructure that can absorb the blow.
Dosfuscation, however, doesn’t come from the outside. It’s wired directly into your codebase. It hides in dependencies, sneaks through CI pipelines, and waits until execution to blow things up. No amount of firewall tuning or DDoS mitigation will stop it because it never travels over the network; it’s already home.
This makes dosfuscation a particularly stealthy form of denial-of-service. It doesn’t announce itself with network noise. It kills from within, at build time, during runtime, or when a specific logic branch is hit. And because it’s buried in code using advanced obfuscation techniques, you won’t catch it unless you’re looking deep.
That’s why DevSecOps teams need to think beyond perimeter defenses. Application-layer security matters just as much. If your only focus is on keeping bad traffic out, you’ll miss the payload already living in your repo.
How Attackers Use Obfuscation to Hide DoS Logic in Code
You might see this in action when a workflow job starts taking much longer than expected, or worse, never finishes. One example involved a team running tests in a Docker container via GitHub Actions. A small JavaScript test helper had been added through a third-party module. It was obfuscated to disguise an infinite memory allocation loop that made the node process unresponsive.
Obfuscated DoS payloads often slip through unnoticed in CI workflows. For example, a GitHub Actions pipeline might run a seemingly harmless script that suddenly hangs the job due to an embedded infinite loop.
To make this real, here’s what a dosfuscated payload might look like in everyday code.
JavaScript Example: Hidden Infinite Loop
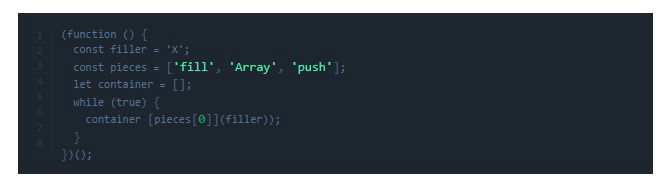
This fills memory indefinitely using disguised logic, eventually crashing the app.
Python Example: Obfuscated CPU Hog
import base64
exec(base64.b64decode("d2hpbGUgVHJ1ZToKICBhcCA9IFtdCiAgZm9yIGkgaW4gcmFuZ2UoMTAwMDAwMDApOgogICAgYXAucHVzaChzdHIoaSkp"))
This base64-encoded loop runs endlessly, hogging memory without appearing suspicious at first glance.
Where the Payloads Hide: A Real-World Dosfuscation Scenario
Dosfuscated payloads often hide in plain sight, inside third-party packages, open-source pull requests, or internal scripts reused without scrutiny. Attackers count on development speed and automation to slip through unnoticed, embedding logic bombs deep in your pipeline.
A real-world scenario helps illustrate how this happens:
You’re using GitHub Actions to run your CI workflow. Your .github/workflows/build.yml installs project dependencies. One of those is a transitive npm package, installed not by you directly, but as a dependency of a dependency. It claims to help with something trivial, like string manipulation.
But inside the package, hidden using obfuscation techniques, is a logic bomb. It might be an infinite memory allocation loop triggered during a postinstall script, or a runtime import in your tests. It remains dormant until execution, no warnings, no audit flags.
Suddenly, your CI runner crashes. CPU and memory spike. The job times out. Your build or deployment fails.
This isn’t just a hypothetical. Incidents like this have been observed in the wild. They demonstrate how dosfuscation leverages trust in your toolchain, exploiting automated workflows, fast merges, and indirect dependencies.
Where do these payloads typically hide?
- Third-party packages: especially from npm, PyPI, or Maven.
- Open-source PRs: with sneaky logic masked as helpful updates.
- Internal scripts: reused snippets with no proper validation or review.
Attackers use obfuscation to delay detection, counting on shallow code reviews and automated dependency updates to do the rest.
How to Detect Dosfuscation in Your Code and Dependencies
Use Static Analysis to Find Weird Logic
Use tools that:
- Detect obfuscation techniques like scrambled control flow or string reconstruction.
- Flag logic that’s way too complex for simple modules.
- Highlight function or script patterns resembling types of denial of service attacks.
Scan Dependencies with More Than Just Version Checks
Don’t stop at checking version numbers:
- Look inside the actual code.
- Prioritize reviewing recent package updates.
- Search for encoded strings, hidden logic, or Dosfuscation markers.
Manually Review Suspicious Pull Requests
Watch for:
- Overly complex changes in simple updates.
- Obscure or unreadable logic in new code.
- PRs introducing known obfuscation techniques.
Dosfuscation gets in when everyone assumes “it’s just a tiny change.”
How to Prevent Dosfuscation from Hitting Your CI/CD
In CI environments like GitHub Actions, GitLab CI, or CircleCI, prevention is about setting up controls that detect and block obfuscated payloads early. For example, enforce PR reviews for all workflows containing shell scripts or install hooks, and monitor .yml pipeline configs for unverified third-party actions.
CI/CD is a dosfuscation playground. Here’s how to lock it down:
- Add static scanners to every PR and build.
- Only use packages from trusted, verified sources.
- Track build resource usage; spikes might mean hidden logic.
- Match every dependency against a checked SBOM.
- Prohibit the usage of common obfuscation techniques without documented justification.
No more “install and hope.” Prevention means having guardrails built into your workflow. Catching dosfuscation early prevents the most disruptive types of denial of service attacks.
Xygeni’s Role: Catching Dosfuscation Before It Hits Production
Xygeni helps DevSecOps teams stop dosfuscation before it causes downtime by embedding security intelligence throughout your development workflow. It specializes in detecting obfuscation techniques and enforcing policy-based guardrails that prevent stealthy denial-of-service attacks from reaching production.
In PR Reviews
Xygeni scans code diffs to identify signs of obfuscation like:
- Use of eval or similar dynamic execution methods.
- Base64 or hex-encoded strings meant to hide logic.
- Suspicious control flow, such as unnatural loops or convoluted logic branching.
These patterns trigger real-time alerts during pull request reviews, whether in first-party or third-party code, helping security reviewers catch dosfuscation early.
During Dependency Analysis
Xygeni analyzes not just package metadata, but the actual source of new or updated dependencies. It detects embedded obfuscated logic inside helper functions or postinstall scripts, flagging high-risk packages even if they appear legitimate on the surface.
At Build Time in CI/CD Pipelines
Xygeni monitors CI jobs for anomalies in behavior. If a build suddenly consumes unusual CPU or memory, Xygeni traces the spike to specific code or packages recently introduced. It automatically correlates runtime behavior with static findings to catch hidden DoS payloads before they disrupt delivery.
As a Policy Enforcement Layer
You can configure Xygeni to block risky patterns outright, such as:
- Prohibiting dependencies that include base64-encoded code or eval
- Requiring manual approval for all post-install scripts
- Enforcing zero-tolerance rules for obfuscated control flow in PRs or CI jobs
With Xygeni, security becomes proactive. It gives teams visibility, early warnings, and policy-level enforcement against the kinds of obfuscation techniques dosfuscation relies on. By embedding Xygeni in every stage, PRs, dependency scans, and CI runtime, you catch the threat before it becomes a postmortem.
So, Dosfuscation Turns Your Code Against You
Dosfuscation isn’t just a theoretical risk; it’s a real and growing attack vector that turns your development process into a weapon. It thrives in the gaps between rapid releases, automated installs, and dependency chains too complex to manually audit. This is not just a security issue; it’s a software engineering challenge. Obfuscated denial-of-service payloads bypass traditional defenses by embedding themselves directly in code, where firewalls and traffic filters can’t reach.
For developers, the takeaway is simple: If you write code, approve pull requests, or manage CI/CD pipelines, you are the front line. Secure builds aren’t just about clean code; they require visibility, scrutiny, and policy-backed protections at every step of the pipeline.
Move beyond checklists. Integrate obfuscation detection into your workflow. Watch for base64 strings, strange logic, or unexpected spikes in CI resource use. Validate not just what you install, but what it does. Treat pipeline configurations like production code. Automate guardrails. Flag what looks odd, even if it “works.”
Because dosfuscation doesn’t shout. It waits. And if you’re not looking for it, it will slip through.









