Git is a powerful tool. Still, many developers only learn just enough to get by. At first, that might seem fine. However, once secrets leak, merge conflicts pile up, or someone pushes directly to main, things can go sideways quickly. Therefore, it is essential to go beyond the basics and adopt a secure, fast, and consistent workflow. This FAQ answers the most common questions developers ask about Git. Along the way, it highlights essential git best practices, explains key concepts behind git fast version control, and offers real-world advice on git security. Each section is designed to help you stop guessing and start shipping code with confidence.
What Is Git?
Why Git Fast Version Control Needs Smart Defaults
Git is a distributed version control system. In practical terms, it lets you track changes in your codebase, collaborate with teammates, and roll back when something breaks. Unlike centralized systems, Git works locally, you can run commands like git commit or git branch even without internet access.
At first glance, Git might seem like a tool just for tracking history. However, it is essential to modern development workflows. Git powers git fast version control, enabling teams to iterate quickly while keeping traceability. Moreover, Git underpins automation, CI/CD pipelines, and DevOps best practices across nearly every software project.
That said, Git is not just a productivity tool. It is also a security boundary. For instance, if someone accidentally runs git add . and commits a .env file, secrets like API tokens might get pushed to a remote repo. Attackers frequently scan public repositories looking for exposed credentials and sensitive config files.
To stay safe when using Git, remember these essentials:
- Use a
.gitignorefile to exclude sensitive or local files. - Require 2FA for all Git accounts (especially on platforms like GitHub or GitLab).
- Never commit secrets or credentials, scan them pre-commit when possible.
For advanced protection, tools like Xygeni scan your repositories continuously. They catch hardcoded secrets, detect vulnerable code before it merges, and even block unsafe workflows in your CI/CD pipeline, all without getting in your way.
Who Owns Git?
Git is not owned by a single company. It’s an open-source project maintained by a community of contributors, with development coordinated via the Git mailing list and hosted on git-scm.com. Originally created by Linus Torvalds in 2005, Git was designed to be a fast, distributed version control system that developers could trust, especially for managing the Linux kernel.
Although no one owns Git in a traditional sense, several organizations support its ongoing development, including GitHub, GitLab, and Bitbucket. They build their own platforms on top of Git while contributing back to the core.
What Does Git Stand For?
Technically, Git doesn’t stand for anything. It’s not an acronym. According to Linus Torvalds, who created Git in 2005, the name was chosen partly as a bit of British slang, “git” can mean a silly or unpleasant person, and partly because it was short, memorable, and didn’t already exist as a Unix command.
In his own words: “I’m an egotistical bastard, and I name all my projects after myself. First ‘Linux’, now ‘Git’.” Linus Torvalds
Funny origin aside, Git became one of the most essential tools in software development. It powers everything from open source projects to enterprise CI/CD pipelines. With Git, teams gain fast version control, decentralized collaboration, and the ability to track and revert changes precisely.
However, as Git adoption has exploded, so have the risks. Malware, secrets, and supply chain vulnerabilities can enter your repositories unnoticed. That’s why securing your Git setup with tools like Xygeni, which analyzes commits, scans dependencies, and enforces policies, is critical for modern DevSecOps workflows.
How to Use Git?
Git Best Practices to Use Git Securely and Effectively
Using Git effectively means more than just memorizing a few commands. It involves following git best practices, understanding how your changes flow through branches and remotes, and avoiding common mistakes that can lead to bugs or even security risks.
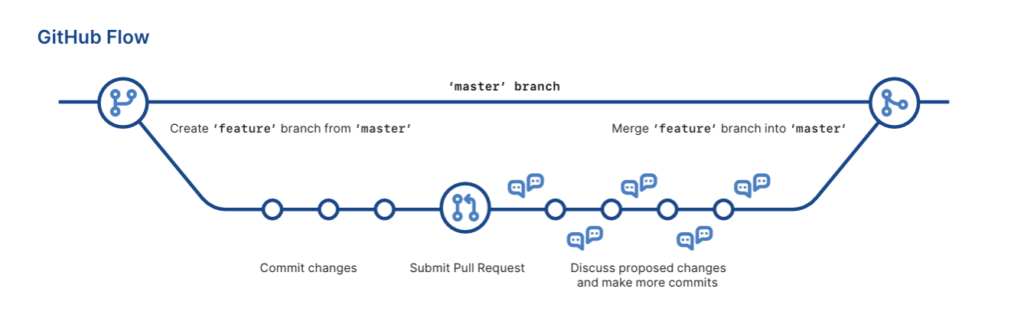
The Basic Git Workflow
To get started, the basic Git workflow typically includes:
1. Cloning a repo:
git clone https://github.com/your-org/your-repo.git 2. Creating a feature branch:
git checkout -b feature/cool-new-thing 3. Making changes and committing safely:
git add .
git commit -m "Add new feature safely and cleanly"
4. Pushing to remote:
git push origin feature/cool-new-thing
5. Opening a pull request (PR) to merge your changes into the main branch.
Apply Git Security at Every Step
Although these steps are standard, many developers unknowingly introduce risks. For example, committing a secret accidentally or pushing unreviewed code that breaks production.
Therefore, here are some security-focused improvements to apply immediately:
- Avoid
git add .unless you’re certain what you’re committing. Usegit statusfirst and add files selectively withgit add <file>. - Write meaningful commit messages. They improve traceability and help reviewers spot anomalies.
- Scan your commits before pushing. Use tools like Xygeni’s Git Guardrails to catch secrets, malware, and misconfigs pre-merge.
- Force PR reviews before merging. It’s one of the simplest ways to prevent risky code from entering your main branch.
Importantly, Xygeni integrates directly into your Git workflow. It scans every commit and PR to enforce your security policies without slowing you down. This keeps your repo secure while preserving git fast version control, fast, but safe.
What Is a Git Repository?
At its core, a Git repository is a versioned directory of your project that tracks every change over time. It includes all your source code, branches, tags, and commit history, and potentially a lot more than you expect.
So why does this matter for git security?
Because a Git repo is not just a history of your code. It might also contain:
- Sensitive configuration files like
.envorconfig.yml - Hardcoded secrets accidentally added during development
- Malware or typosquatted dependencies introduced via
package.json,requirements.txt, or other manifests
Therefore, understanding what lives in your repo is critical. It’s not just about keeping code clean, it’s about protecting your entire pipeline.
Example:
A common mistake is pushing a local .env file with secrets:
git add .env
git commit -m "add environment config"
git push
Even if the repo is private, those secrets can leak via forks or third-party integrations.
To avoid this:
echo ".env" >> .gitignore
- Set up pre-commit hooks or CI scanners like Xygeni to detect secrets before they reach your remote.
- Clean your history with
git filter-repoorBFGif something sensitive has already been committed.
When you push code, Xygeni scans the commit and your dependency files (like package.json or requirements.txt) for leaked secrets, malware, and known exploits , all before it reaches the PR stage.
This ensures that your git best practices and security hygiene are maintained, even as the project grows. Moreover, Xygeni supports scanning across GitHub, GitLab, Bitbucket, and other major platforms.
Ultimately, treating your Git repo as a security boundary, not just a code store, helps teams move faster without leaving critical gaps.
What Is Source Control?
Source control, also known as version control, is the practice of tracking and managing changes to your codebase. Tools like Git make this possible by recording who changed what, when, and why. But it’s not just about collaboration. In today’s DevOps pipelines, source control is also your first security checkpoint.
More importantly, developers rely on git fast version control to move quickly, branching, committing, and merging without delays. However, when security is overlooked, that speed can backfire.
Common Git Security Risks in Source Control
Attackers increasingly target source control systems like GitHub, GitLab, and Bitbucket. A single leaked token or misconfigured workflow can give access to your entire software supply chain. Therefore, git security is no longer optional, it’s essential.
Here are some of the common risks:
- Stolen GitHub tokens used to clone or tamper with private repositories
- Unprotected main branches that allow direct risky commits
- Malicious contributors submitting pull requests with hidden payloads
- Workflows with write permissions exploited to inject malware
How to Apply Git Best Practices in Source Control
To keep source control secure without slowing down your work:
- Use two-factor authentication (2FA) across all dev accounts
- Set strict branch protection rules and require PR reviews
- Audit workflow permissions, avoid giving unnecessary write access
- Run scans for vulnerabilities, secrets, and misconfigs before merging
Why Use Xygeni?
Xygeni strengthens Git’s capabilities by layering in:
- CI/CD guardrails
- Workflow misconfiguration detection
- Secret scanning pre-merge
- Policy enforcement on PRs and merges
As a result, you can maintain git fast version control without sacrificing visibility or safety. Developers work just as quickly, but now every change is secured by automated checks.
When source control is hardened, it protects your entire pipeline, from commit to deploy.
How to Pull from Git?
The git pull command is probably one of the most used, and least understood, Git operations. It fetches changes from a remote repository and merges them into your current branch. Simple enough, right? However, behind that simplicity lies a potential source of bugs, broken builds, and even security issues.
To run it:
git pull origin main
This command grabs the latest changes from the main branch of your remote (usually GitHub, GitLab, etc.) and tries to merge them with your local code.
How to Pull from Git Without Breaking Git Security or Speed
From a security standpoint, blindly pulling code can be risky. Malicious actors can sneak harmful code, typo-squatted dependencies, or poisoned commits into public repos. In shared projects, even well-meaning teammates might push insecure changes by mistake. This is where git best practices become critical.
Also, when your team pulls frequently, it supports git fast version control, helping developers stay in sync, reduce merge conflicts, and ship faster. But if you’re pulling unsafe code, speed becomes your enemy.
Best Practices
To use git pull securely and efficiently:
- Review pull request diffs before merging or pulling, especially from external contributors
- Prefer
git fetch+git mergefor more control over what you’re integrating - Run tests locally before pushing pulled changes upstream
- Use signed commits and validate authorship if you’re working on sensitive projects
- Monitor your supply chain, packages pulled via automation (e.g., post-install scripts) can be dangerous
How Xygeni Helps
Xygeni adds guardrails that scan your code before it reaches production. For example:
- Automatically detects malware, secrets, and vulnerable code in remote changes
- Flags any tampering or inconsistencies in your repository history
- Applies policy checks on pull requests and merges, blocking unsafe code from being introduced
- Continuously monitors your CI/CD workflows to ensure attackers can’t exploit pull-based logic
With Xygeni, you can safely embrace git fast version control, pulling, merging, and deploying with confidence that every change has passed security checks.
How to Commit to Git?
Committing in Git is more than just typing git commit -m "fix stuff" and moving on. If you want git fast version control that scales with your team and avoids future headaches, your commits must be clear, meaningful, and secure.
How to Commit to Git Securely Using Git Best Practices
To create a commit, you typically run:
git add <file>
git commit -m "Describe what you changed"
The git add stage tells Git which changes to include. The git commit command snapshots those changes into your project history. Simple, right? However, following git best practices means going further:
- Write descriptive commit messages.
- Commit logically grouped changes.
- Avoid large, bloated commits that touch unrelated files.
Good commits make version control faster, cleaner, and easier to debug.
Git Fast Version Control Starts with Good Commit Hygiene
Here’s where git security comes into play. A careless commit can accidentally leak secrets, introduce vulnerabilities, or pull in malicious packages. Before committing:
- Double-check for
.envfiles, hardcoded tokens, or exposed credentials. - Validate your dependencies, are they safe, verified, and up to date?
- Exclude unnecessary files using
.gitignore(like logs, build artifacts, or credentials).
Tip: Integrate commit scanning into your workflow with a tool like Xygeni. It checks for secrets, typo-squatted packages, and misconfigs before the code reaches your main branch, all without interrupting your flow.
Is git clone Equal to a Pull Request?
Not even close. While both actions involve remote repositories, they serve completely different purposes:
git cloneis a command used to copy an entire remote repository to your local machine. It’s usually the first thing you do when starting to work on a new project.
git clone https://github.com/your-team/project.git
A pull request (PR) is a collaboration mechanism typically used on platforms like GitHub or GitLab. Once you’ve made changes in your local or forked repo, you open a PR to request merging those changes into a shared branch (like main).
Think of it this way:
git clone= “Let me grab a copy so I can start coding.”- Pull Request = “Here’s what I changed. Please review and approve it before we merge.”
Git Security Implications When Cloning Repositories
If you’re just cloning repos without verifying what’s inside, you might be importing:
- Malicious scripts
- Misconfigured workflows
- Poisoned dependencies
Likewise, pull requests can be a vector for injected vulnerabilities if not properly scanned.
That’s why fast version control isn’t just about speed, it also means secure decision-making. Tools like Xygeni:
- Analyze PRs for secrets, vulnerable code, and misconfigurations
- Enforce policy checks before merges
- Alert on unsafe contributions, even in cloned forks
Bottom line: Cloning is how you start; PRs are how you contribute. Securing both is part of git best practices that every DevOps team should follow.
How to Clone a Git Repository in Visual Studio Code?
Cloning a Git repository might seem simple, but it’s often where security issues quietly sneak in. If you care about git fast version control and clean workflows, the cloning step deserves more attention than just clicking “Clone.”
Git Best Practices When Cloning Repositories in Visual Studio Code
Here’s how to do it securely:
- Copy the repository URL from GitHub, GitLab, or Bitbucket. Make sure it’s from a trusted source, yes, even internal repos can be risky.
- Open Visual Studio Code.
- Go to the Source Control panel (icon on the left sidebar) or press
Ctrl+Shift+G. - Click “Clone Repository”, paste the URL, and press Enter.
- Choose a local folder to store the repo.
- VS Code will prompt you to open the cloned folder. Click “Open”.
- Before you start working, scan the repo for signs of trouble, such as exposed secrets, typo-squatted dependencies, or sketchy
.githistory. Even legit-looking projects might include risky scripts or misconfigurations.
Teams using automated scanners at this stage catch issues early and stay aligned with git best practices. It’s a small step that can save hours later.
By building this habit into your workflow, you boost both your project hygiene and your security posture, all without slowing down. That’s what modern git security should look like.
How to Check Current Branch in Git?
Knowing which branch you’re on should be second nature, especially when juggling multiple features, hotfixes, or release lines. Mistakes happen fast if you push or pull from the wrong branch. For teams focused on git fast version control, clarity beats chaos.
To check your current branch:
In your terminal, run:
git branch
The current branch will be highlighted with an asterisk (*), like this:
* main
dev
feature/login-fix
Alternatively, use:
git status
It shows something like:
On branch main
Your branch is up to date with 'origin/main'.Avoid Git Security Mistakes by Verifying Branches
Branch mistakes are more than just annoying, they’re a security risk. Accidentally merging or committing to the wrong branch can bypass reviews or inject unscanned code into production. This breaks the flow of git best practices and opens the door to risky changes slipping through.
Teams that enforce clear branching strategies and integrate scanning into pull requests can stop most issues before they escalate. Secure development doesn’t mean slow development, it means making your Git workflow smarter and safer from the start.
Is Git Secure?
Git Security Best Practices Every Team Should Know
Git, by itself, is just a version control system, it doesn’t magically secure your code. It’s fast, flexible, and powerful, which makes it a favorite for developers. However, that power comes with responsibility.
While Git supports features like signed commits and branch protections, it won’t stop you from pushing a secret key, misconfiguring access, or pulling in a vulnerable dependency. So, is Git secure? The short answer: it can be, if you use it right.
Make Git Secure in Practice
To actually secure your Git workflow, follow these git best practices:
- Set up branch protection rules and require pull request reviews.
- Never commit secrets or tokens. Use
.gitignoreand scan your commits. - Review your repository access regularly, don’t give everyone admin rights.
- Sign your commits with GPG for integrity.
- Run pre-commit hooks or CI scans to catch risky changes before they land.
Security in Git isn’t a toggle you flip, it’s a habit. When you treat Git as part of your attack surface, not just a tool, you start building real git security into every step. And the best part? These habits don’t slow you down. In fact, they make your team faster and more confident, delivering git fast version control without risking what matters.
Git Best Practices for Secure and Fast Version Control
To maintain a healthy and secure codebase, your Git workflow needs more than just convenience shortcuts. These git best practices are designed to improve team collaboration, enforce git security, and support git fast version control without slowing you down.
Use Clear and Atomic Commits
Each commit should reflect one logical change. This simplifies code reviews, rollbacks, and change tracking. Avoid committing large chunks of unrelated updates.
Never Commit Secrets
Always check for .env files, access tokens, or credentials before pushing. Use .gitignore to exclude sensitive files and apply automated scanning tools to catch exposed secrets early.
Enforce Branch Protection Rules
Protect main branches by requiring pull requests, approvals, and status checks. This ensures unreviewed or risky code never reaches production.
Review Dependencies and Scan for Vulnerabilities
Pin your dependencies and avoid untrusted packages. Use automated tools to scan your repository for vulnerable or malicious libraries before they’re merged.
Sign Commits
Enable GPG commit signing to verify the identity of contributors. This step adds an extra layer of git security and prevents tampered commit histories.
Monitor Access and Permissions
Review who has access to your repositories and what level of control they have. Limit write access where possible and remove inactive collaborators regularly.
Automate Pre-Merge Scans and Policy Checks
Use CI/CD tools to validate every pull request for secrets, misconfigurations, and risky patterns. Automating these checks is critical for maintaining git fast version control at scale.
Clean Up and Rebase
Before pushing, squash fix commits or cleanup changes. This keeps your history readable and reduces noise during collaboration.
How Xygeni Helps Enforce Git Security
Security doesn’t have to slow you down, especially in Git. Xygeni layers invisible protection into your workflow so you can commit, branch, and merge without worrying about what might slip through.
Catches Secrets Before They Spread
Accidentally commit a .env file? It happens. Xygeni flags secrets like API tokens or cloud credentials in real time, whether they’re in a fresh commit, a buried config, or a Docker layer. You get alerted before they hit production, with optional auto-revoke and remediation workflow.
Blocks Risky Dependencies at Commit Time
You shouldn’t need to reverse-engineer package.json after a build fails. Xygeni scans your dependencies during commit and flags malware-laced packages, typosquats, or outdated libraries, and tells you which ones are actually exploitable, not just vulnerable.
Flags Dangerous CI Configs Automatically
CI/CD is where small misconfigs become big incidents. Whether you’re tweaking .github/workflows or updating a Jenkins job, Xygeni reviews your pipeline configs for risky patterns, like permissive tokens, unsafe scripts, or shell injection, and stops unsafe code before it runs.
Notifies You of Suspicious Repo Activity
Xygeni monitors your SCM activity continuously. It flags force pushes to protected branches, removed access controls, or unusual commit patterns, then shows you exactly what changed, who changed it, and when.
Applies Smart Guardrails on PRs and Merges
You define what’s acceptable, Xygeni enforces it. Whether it’s blocking PRs with secrets, failing builds with exploitable dependencies, or applying security policies repo-wide, Xygeni applies those guardrails consistently and silently across teams.
With Xygeni, you don’t need to memorize security rules, they’re embedded into your Git workflow by default.
No context-switching. No interruptions. Just fast, secure commits that are ready to ship. Want to see how this looks in your own workflow? Try Xygeni on your Git repo, no credit card needed.