Infrastructure as Code security has changed how organizations set up and manage infrastructure, making automation easier and making sure reliability. However, without Infrastructure as Code best practices, IaC can create security risks, such as misconfigurations, compliance issues, and exposure to cyber threats. To reduce these risks, organizations must follow IaC security best practices that protect cloud environments from the start. Improving IaC security & IaC cyber security helps infrastructure stay strong, lowers attack risks, and applies security policies at scale.
What is IaC Security?
IaC security has changed the way organizations set up and manage infrastructure, making automation and consistency the standard. However, without Infrastructure as Code best practices, IaC can create serious security risks, such as misconfigurations, compliance issues, and exposure to cyber threats. Because of this, following IaC security best practices is essential for keeping cloud environments safe from vulnerabilities.
A well-planned IaC security approach does more than just automate deployments. It improves visibility, applies security rules, and prevents unapproved changes that could put cloud environments at risk. Moreover, adding IaC security & IaC cyber security into DevOps workflows allows teams to actively find vulnerabilities, protect sensitive data, and lower the risk of attacks caused by misconfigured infrastructure.
The National Institute of Standards and Technology (NIST) defines Infrastructure as Code security as the practice of managing and setting up IT infrastructure through code-based automation, making sure configurations stay consistent and easy to reproduce. Therefore, following Infrastructure as Code best practices helps companies reduce security gaps, meet compliance standards, and keep strong security policies throughout the setup process.
IaC Security Best Practices
The 2024 State of Infrastructure as Code (IaC) Report identifies security as one of the top challenges organizations face when managing cloud infrastructure. Because of this, companies must adopt Infrastructure as Code best practices to reduce risks from misconfigurations, compliance violations, and security vulnerabilities. Likewise, OWASP provides essential guidelines for integrating security best practices into the Software Development Life Cycle (SDLC), helping organizations mitigate risks from insecure configurations and flawed deployments.
Embed Security Checks Throughout the IaC Process
To strengthen IaC security, security controls should be embedded at every stage of the development pipeline. Rather than waiting for post-deployment audits, teams should scan IaC templates for vulnerabilities before deployment to catch security flaws early. By taking this preventive approach, organizations can significantly improve IaC cyber security and prevent misconfigurations from ever reaching production.
Ensure Infrastructure Immutability
One of the most effective IaC security best practices is making sure that infrastructure remains immutable after deployment. In other words, once a resource is provisioned, it should not be altered. By keeping immutability, organizations can:
- Reduce the risk of configuration drift, which often leads to security vulnerabilities.
- Prevent non authorized changes, making sure infrastructure remains consistent.
- Reinforce Infrastructure as Code security by limiting attack surfaces.
Version Control and Audit Trail
Version control plays a critical role in IaC security & IaC cyber security. Not only does it track every infrastructure modification, but it also ensures all changes are reviewed, logged, and approved. Additionally:
- Maintaining an audit trail allows teams to quickly roll back to secure configurations if security issues arise.
- Version control helps prevent non authorized modifications, reducing the risk of misconfigurations.
- Using Git and infrastructure versioning tools ensures traceability for all code and policy changes.
Enforce the Principle of Least Privilege (PoLP)
Restricting access rights is a critical Infrastructure as Code best practice that enhances IaC security best practices. By keeping the principle of least privilege (PoLP), organizations can:
- Minimize security risks by making sure only authorized users can modify the infrastructure.
- Limit excessive permissions, reducing the risk of accidental or malicious changes.
- Strengthen overall IaC security by applying strict role-based access controls.
Implement Continuous Monitoring and Static Analysis
To maintain IaC security best practices, organizations must integrate static analysis tools and continuous monitoring to identify vulnerabilities before deployment.
- Static analysis scans IaC scripts for security flaws, compliance violations, and misconfigurations.
- Real-time monitoring detects non authorized infrastructure changes, making sure security policies remain enforced.
- Automated tools such as Snyk, Checkov, or Terrascan help secure IaC templates before they go into production.
Container Image Scanning
Many Infrastructure as Code best practices extend beyond configurations to containerized environments, where insecure images pose security risks. Integrating container image scanning into IaC security best practices helps:
- Identifying outdated or vulnerable software within container images.
- Detecting hardcoded secrets and potential malware before images are deployed.
- Making sure secure configurations by scanning images with tools such as Dagda, Clair, Trivy, and Anchore.
By integrating container security into IaC workflows, teams can prevent misconfigurations that expose cloud environments to attacks.
CI/CD Pipeline Security and Consolidated Reporting
Embedding security into CI/CD pipelines is essential for IaC security best practices. This approach ensures:
- Automate security checks for every code change.
- Ensure compliance is continuously enforced, without relying on manual audits.
- Maintain a history of compliance to track and remediate security issues faster.
Tools like Jenkins, GitHub Actions, and GitLab CI/CD integrate security checks directly into development pipelines. Additionally, platforms like DefectDojo and OWASP Glue consolidate security insights into a single dashboard, making it easier to track and address vulnerabilities across infrastructure deployments.
Artifact Signing for Integrity and Provenance
To ensure the integrity of IaC configurations, organizations should implement artifact signing as part of their Infrastructure as Code best practices. This approach:
- Prevent tampering between build and runtime.
- Verify the authenticity of infrastructure components before deployment.
- Use open-source tools like TUF (The Update Framework) to implement secure signing mechanisms.
Artifact signing ensures that only trusted, validated infrastructure configurations are used, reducing the risk of supply chain attacks on IaC deployments.
Why These IaC Security Best Practices Matter
By following these Infrastructure as Code best practices, organizations can:
- Prevent security misconfigurations that expose cloud environments to attacks.
- Improve IaC security & IaC cyber security through proactive risk mitigation.
- Automate security enforcement with static analysis and CI/CD security integration.
- Ensure cloud infrastructure remains compliant, resilient, and tamper-proof.
Embedding security into IaC from the start is the only way to maintain control, prevent breaches, and ensure that infrastructure remains secure throughout its lifecycle.
Xygeni’s IaC Security: All-in-One Platform for Infrastructure as Code Best Practices
As organizations increasingly adopt Infrastructure as Code (IaC) to automate cloud infrastructure, security risks continue to grow. Without IaC security best practices, misconfigurations, exposed secrets, and vulnerable dependencies create serious security gaps. Consequently, companies must integrate IaC cybersecurity measures to protect cloud environments from the start. With this in mind, Xygeni provides an all-in-one platform that ensures infrastructure remains resilient, compliant, and secure from code to cloud.
Detecting and Preventing Cloud Misconfigurations in IaC Security
Without a doubt, misconfigurations remain one of the leading causes of cloud security incidents. Because of this, security teams need tools that identify and mitigate risks before deployment. That is why Xygeni continuously scans Terraform, CloudFormation, Kubernetes, Bicep, and ARM templates, making sure cloud environments follow Infrastructure as Code best practices. By automating security enforcement, Xygeni enables organizations to:
- Prevent misconfigured storage, excessive IAM permissions, and exposed security groups.
- Ensure compliance by blocking risky infrastructure configurations.
- Reduce manual security reviews, improving efficiency while keeping IaC security best practices.
Secrets Security: Protecting Sensitive Data in IaC
Hardcoded credentials in IaC scripts expose cloud environments to non authorized access. As a result, organizations must take extra precautions to secure their infrastructure. To address this challenge, Xygeni’s secrets security solution ensures that sensitive data stays protected by:
- Scanning repositories for hardcoded secrets before deployment.
- Blocking insecure commits in CI/CD pipelines to prevent credential leaks.
- Alerting security teams in real time to mitigate threats before they escalate.
By integrating IaC security best practices, organizations eliminate a critical security risk that attackers frequently exploit.
Comprehensive IaC Framework Support for Enhanced Security
To improve security across multi-cloud and hybrid environments, Xygeni offers broad framework compatibility. Accordingly, Xygeni supports:
- Terraform – Secures provisioning across AWS, Azure, and GCP.
- Kubernetes & Docker – Detects vulnerabilities in Kubernetes configurations and containerized environments.
- Bicep & ARM Templates – Identifies misconfigurations in Microsoft Azure.
- CloudFormation – Automates security policies for AWS infrastructure.
Because Xygeni secures multiple frameworks, organizations gain consistent security across diverse cloud infrastructures.
Automated Security Policy Enforcement in IaC Workflows
Since manual security checks take a lot of time, adding IaC security best practices into development pipelines is essential. To make the process easier, Xygeni automatically applies policy enforcement by:
- Detecting vulnerabilities, misconfigurations, and compliance violations before deployment.
- Blocking security risks in CI/CD pipelines, preventing insecure infrastructure from reaching production.
- Providing instant feedback to developers, helping them fix misconfigurations early.
This way, security teams can enforce IaC cyber security measures without disrupting development workflows.
Container Image Scanning for IaC Cyber Security
Because many IaC deployments rely on containerized environments, insecure images often introduce hidden risks. Therefore, container image scanning plays a crucial role in ensuring IaC security best practices. Xygeni integrates advanced scanning to:
- Analyze Docker images for outdated software and vulnerabilities.
- Detect malware, misconfigurations, and security weaknesses in containerized environments.
- Block the deployment of insecure images by making sure Infrastructure as Code security best practices are followed in CI/CD pipelines.
By integrating container security into IaC workflows, teams prevent misconfigurations that expose cloud environments to attacks.
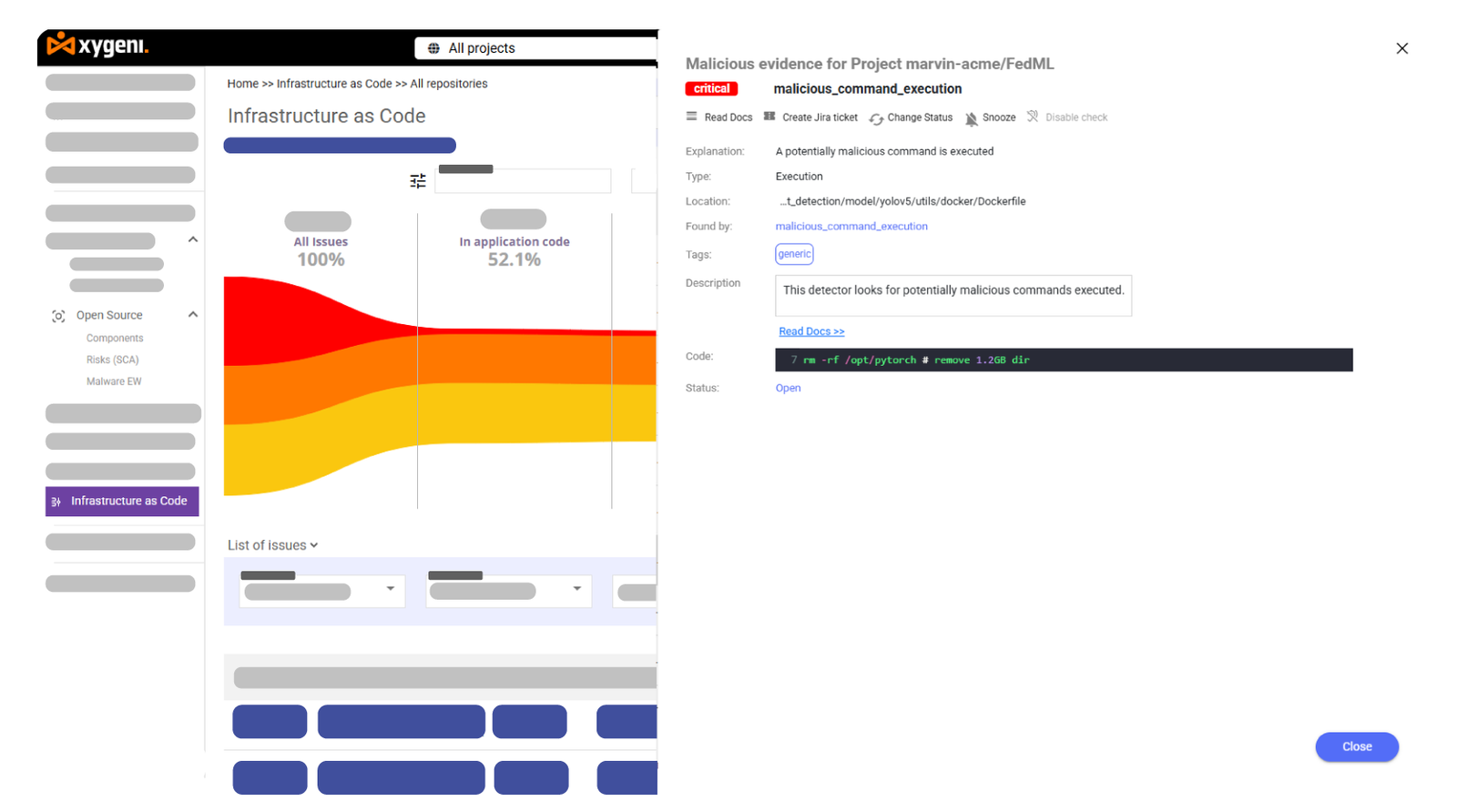
Preventing Malicious Commands and Supply Chain Attacks in IaC
Traditional IaC security tools often miss malicious commands and supply chain threats hidden within infrastructure scripts. However, Xygeni strengthens security by:
- Detecting non authorized commands that introduce backdoors.
- Blocking dependency confusion and malicious package injection.
- Preventing tampering with infrastructure settings by verifying artifact integrity.
As a result, organizations eliminate hidden attack vectors before they impact infrastructure security.
Continuous Monitoring and Real-Time Threat Protection
To go beyond standard vulnerability detection, Xygeni provides real-time security insights. In particular, Xygeni enables security teams to:
- Identify high-risk vulnerabilities through reachability analysis.
- Monitor infrastructure changes to detect non authorized modifications.
- Use threat intelligence to prevent attacks before they escalate.
By adding IaC security best practices, teams can keep improving security and reduce risks before deployment.
Why Xygeni is the Best Choice for IaC Security
Unlike traditional IaC security tools, Xygeni provides:
- Automated enforcement of Infrastructure as Code best practices to prevent misconfigurations.
- Advanced secrets security to eliminate the risks of exposed credentials.
- Container image scanning to secure cloud-native applications.
- Full support for Terraform, Kubernetes, Docker, Bicep, and CloudFormation.
- Continuous monitoring with real-time security insights for cloud environments.
Secure Your Infrastructure with Xygeni’s IaC Security Best Practices
Because security risks evolve constantly, organizations must integrate Infrastructure as Code best practices into their development processes. For this reason, Xygeni delivers an all-in-one platform for IaC security & IaC cyber security, making sure cloud environments stay protected from development to deployment.
With automated security policies, continuous monitoring, and malware detection, Xygeni helps organizations apply IaC security best practices to eliminate security risks before they impact production.
Protect your cloud infrastructure today. Contact us to learn how Xygeni secures Infrastructure as Code best practices from development to deployment.