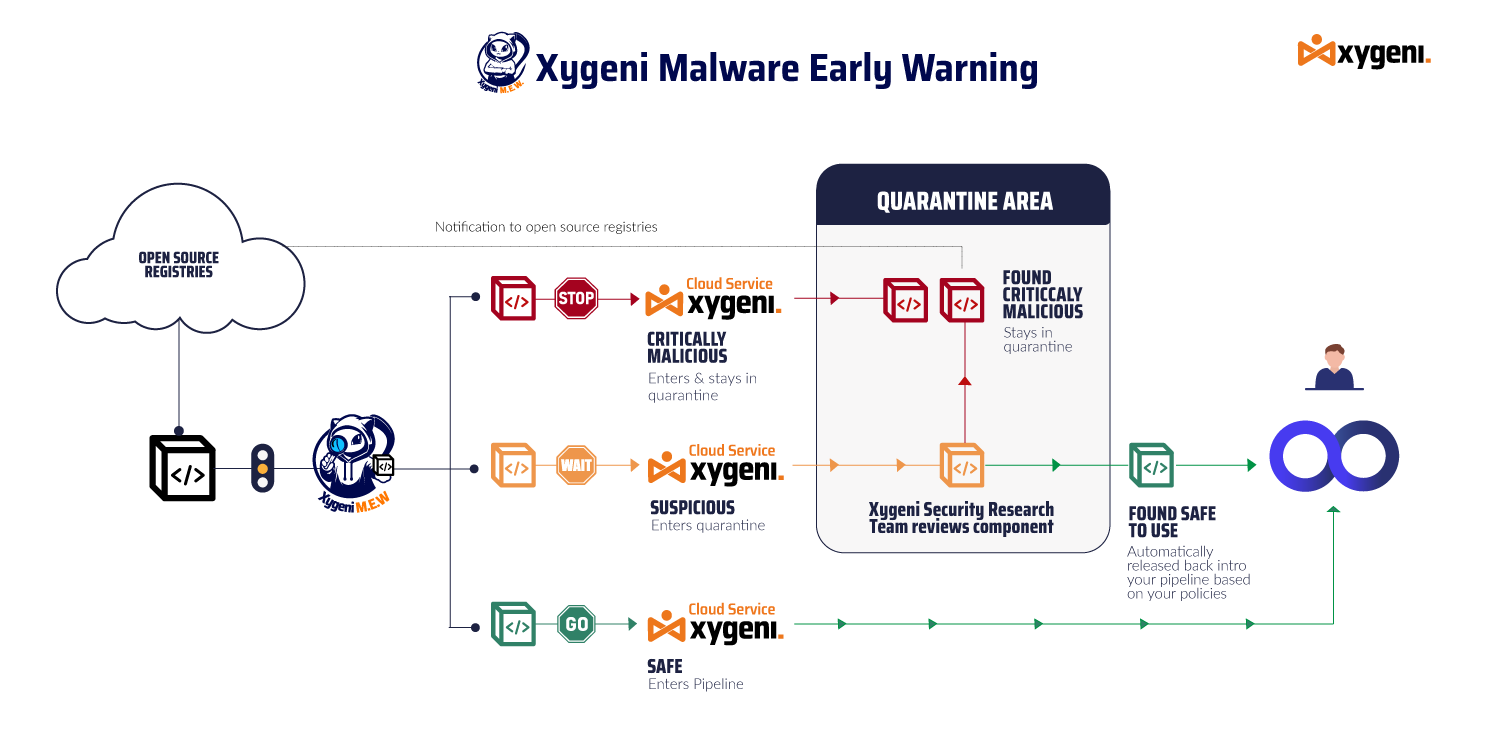
Malicious Code and malicious packages continued to infiltrate open-source ecosystems throughout 2025. Across weekly and monthly reporting, Xygeni researchers confirmed 3,180 malicious packages, including large-scale npm malware campaigns driven by automated multi-version publishing, DevTools impersonation, and supply-chain abuse targeting CI/CD pipelines and developer workflows.
This annual recap consolidates all confirmed malicious packages detected in 2025 and highlights the dominant threat families, attacker behaviors, and the evasion techniques used to bypass registry controls and traditional security tools.
2025: Year in Numbers
- 3,180 confirmed malicious packages across the year
- Sustained growth in npm malware activity
- Strong automation-driven publishing and repeated family re-uploads
- Highest-activity months: October, November, December
- Shift toward enterprise-style and DevTools impersonation
Together, these trends confirm that Malicious Code distribution via package ecosystems has become persistent, scalable, and industrialized.
Month-by-Month Highlights
January/March
Early waves of malicious packages driven by automated publishing and dependency-confusion-style payloads.
April/June
Expansion of typosquatting and version-inflation malicious code with near-identical clones of legitimate packages.
July/September
Lower volume but greater sophistication, especially CI/CD-oriented npm malware and telemetry-style impersonation libraries.
October/December — Peak Activity
Large coordinated waves of:
- multi-version malicious packages
- tooling- and parser-themed malware families
- massive automated version pumping
- recurring npm malware clusters
Key Threat Trends Observed in 2025
Automated Multi-Version Publishing
Throughout 2025, attackers relied heavily on automated pipelines that generated dozens of sequential malicious package versions with only minimal changes in their payloads. As a result, large multi-version clusters became one of the most consistent behavioral patterns of the year. Notable malicious families include let1x*, zero-ops, plugin-senna, vitor-js, and @ikarem/telemetry.
In practice, this strategy served three clear objectives:
first, to evade heuristic or pattern-based detection;
second, to artificially inflate package credibility through repeated version releases;
and finally, to overwhelm defenders and reduce the effectiveness of manual review processes.
Impersonation of Internal and Enterprise Tooling
In addition, many malicious packages deliberately mimicked private SDKs, admin tools, telemetry libraries, and CI/CD extensions. Because these names appeared legitimate and familiar, they blended easily into enterprise environments and developer workflows.
Representative examples include private-internal-sdk, baas-admin-sdk, stitch-ui-toolbox, and paypal-scripts-server-utils. Consequently, this trend confirms a clear strategic shift: attackers increasingly aim to compromise developer and automation environments, rather than targeting end users directly.
Version Inflation as an Evasion Tactic
Moreover, across several npm malware families, attackers repeatedly abused version-inflation techniques. This included exaggerated release numbers such as 99.x or 9999.x, rapid incremental patch sequences, and fake “internal release” versioning conventions. In essence, the goal was to bypass reputation-based trust models that rely on maturity, age, or publishing history.
Implications for Security and Engineering Teams
Taken together, these behaviors demonstrate a structural shift in supply-chain risk throughout 2025. Attacks are now persistent, automated, and operationalized, which means that traditional registry protections are no longer sufficient on their own. Furthermore, malicious packages increasingly target CI/CD workflows, build environments, and developer tooling, rather than application runtime layers.
Therefore, effective defense requires a combination of continuous monitoring, behavior-driven detection, and context-aware risk scoring. Likewise, remediation workflows should be embedded directly into development pipelines so that threats are detected and contained before they propagate across environments.
How We Detect Malicious Code in npm Malware and PyPI Malware
Xygeni uses multi-layered techniques to stop malicious code before it spreads. First of all, static code analysis detects obfuscation patterns, hidden payloads, and script abuse. In addition, behavioral sandboxing analyzes install hooks, runtime commands, and persistence tricks. Moreover, machine learning detection identifies zero-day npm malware and pypi malware variants missed by signature scanners. Finally, the Early Warning System monitors public repositories in real time, validates findings, and alerts DevOps teams immediately.
As a result, this combination ensures developers receive fast, actionable intelligence integrated directly into CI/CD workflows.
Why Developers Should Care About Malicious npm Packages
Modern threats rarely wait for runtime. For example, malicious npm packages often execute during installation, while pypi malicious packages hide token exfiltration or backdoors. Attackers:
- Flip private GitHub repos to public to replicate them.
- Exfiltrate credentials and secrets using encoded payloads.
- Use obfuscated JavaScript loaders to deploy ransomware or botnets.
In fact, malicious open-source packages surged 156% in one year. Therefore, teams that rely only on delayed feeds or basic scanners fall behind.
What This Malware Report Tracks in npm and PyPI
This digest is the central hub for:
- Confirmed malicious npm packages
- Confirmed pypi malicious packages
- Behavior-based detections of malicious code
- Registry-confirmed incidents
- Weekly and monthly malware report summaries
- Historical changelog of all npm malware and pypi malware findings
In other words, it provides a single point of reference. The research team at Xygeni updates this page weekly with links to full technical analyses and GitHub IOCs.
How to Protect Against Malicious npm Packages and PyPI Malware
Because of this growing risk, organizations need more than basic dependency checks. Strong defenses against malicious npm packages and pypi malicious packages require both preventive controls and runtime enforcement:
Enforce Lockfile-Only Installs Against Malicious npm Packages
Use npm ci or pip install --require-hashes in CI/CD.
This ensures the exact dependency tree defined in lockfiles is used. As a result, attackers cannot slip in modified or typosquatted versions of malicious npm packages.
Pre-Install Scanning for npm Malware and PyPI Malware
Integrate Xygeni’s Early Warning Engine to scan npm malware and pypi malware before packages reach your environment.
Moreover, detect suspicious postinstall scripts, obfuscated loaders, or hardcoded C2 URLs.
Guardrails to Block Builds with Malicious Code
Set guardrails to fail builds automatically if confirmed malicious npm packages or pypi malicious packages are detected.
For example, break builds on packages with unpublished maintainers, obfuscation patterns, or IOC matches. Consequently, malicious code never passes unnoticed.
Generate and Validate SBOMs Against Malicious npm Packages and PyPI Malware
Create SBOMs (CycloneDX, SPDX) for every build.
Afterward, compare against known malicious npm packages and pypi malware feeds to track both direct and transitive dependencies.
Credential and Token Protection from npm Malware and PyPI Malware
Many malicious npm packages try to read .npmrc, .pypirc, or environment variables.
Therefore, run builds in hardened containers with minimal secrets exposed. Additionally, use secrets managers instead of environment variables to block malicious code abuse.
Monitor Registry and Maintainer Changes in Malicious npm Packages
Attackers often hijack abandoned projects.
In particular, watch for sudden maintainer swaps, unusual versioning jumps, or excessive publishes in npm malware and pypi malicious packages.
Developer Training on Detecting Malicious Code in npm and PyPI
Teach teams to spot red flags such as:
- Package names with typos (
reqeustinstead ofrequest). - Unusual
installorpreparescripts. - Recently created packages with suspiciously high version numbers.
Above all, this awareness helps detect malicious code early.
Runtime Anomaly Detection for Malicious npm Packages and PyPI Malware
Even if malware bypasses static checks, runtime detection in CI/CD can catch:
- Unexpected network connections.
- File system modifications outside expected directories.
- Persistence attempts across jobs.
Finally, this ensures npm malware and pypi malware threats are stopped even after installation.
By combining these controls, teams prevent malicious npm packages and pypi malicious packages from ever reaching production pipelines.
Try Xygeni’s Malware Detection Tools
Xygeni delivers:
- Real-time detection of malicious code, including backdoors, spyware, and ransomware.
- In contrast to basic scanners, analysis across npm, PyPI, Maven, NuGet, RubyGems, and more.
- Automatic build blocking when the malware report identifies risk.
- Exploitability insights, maintainer reputation checks, and anomaly detection.
Stay Informed
Our team updates this page every week. To receive alerts and detailed reports:
- Subscribe to our Newsletter
- Follow @XygeniSecurity on Linkedin
- Bookmark this page to track the latest npm malware and pypi malware threats