Imagine a skyscraper, each floor built by different teams. One faulty beam installed by a single team can jeopardize the entire structure. This is the reality organizations face with software supply chains in today’s digital landscape.
As companies increasingly rely on intricate networks of suppliers and open-source components, the risk of malicious actors exploiting vulnerabilities has grown exponentially. The alarming rise in software supply chain attacks, such as the infamous SolarWinds and Kaseya breaches, highlights the critical need for robust security measures to safeguard both businesses and their customers from catastrophic consequences.
These attacks can have devastating effects, impacting everything from operational efficiency to customer trust. Just a handful of compromised releases can wreak havoc on an organization. As a result, software supply chain security has transformed from an afterthought to an absolute necessity for maintaining resilience and a healthy cyberspace within any digital enterprise.
Don’t let your organization fall victim to the next big supply chain attack. Empower yourself with the knowledge and skills to fortify your software supply chain by enrolling in our cutting-edge Certified Software Supply Chain Security Expert Course. With self-paced learning, browser-based lab access, and 24/7 instructor support via Mattermost, you’ll gain the expertise needed to protect your company and customers from potential disasters. Take action now and become a leader in software supply chain security – your organization’s future depends on it.
Take a Sneak Peek into the ‘CSSE’ Course:
Why Software Supply Chain Attacks Happen?
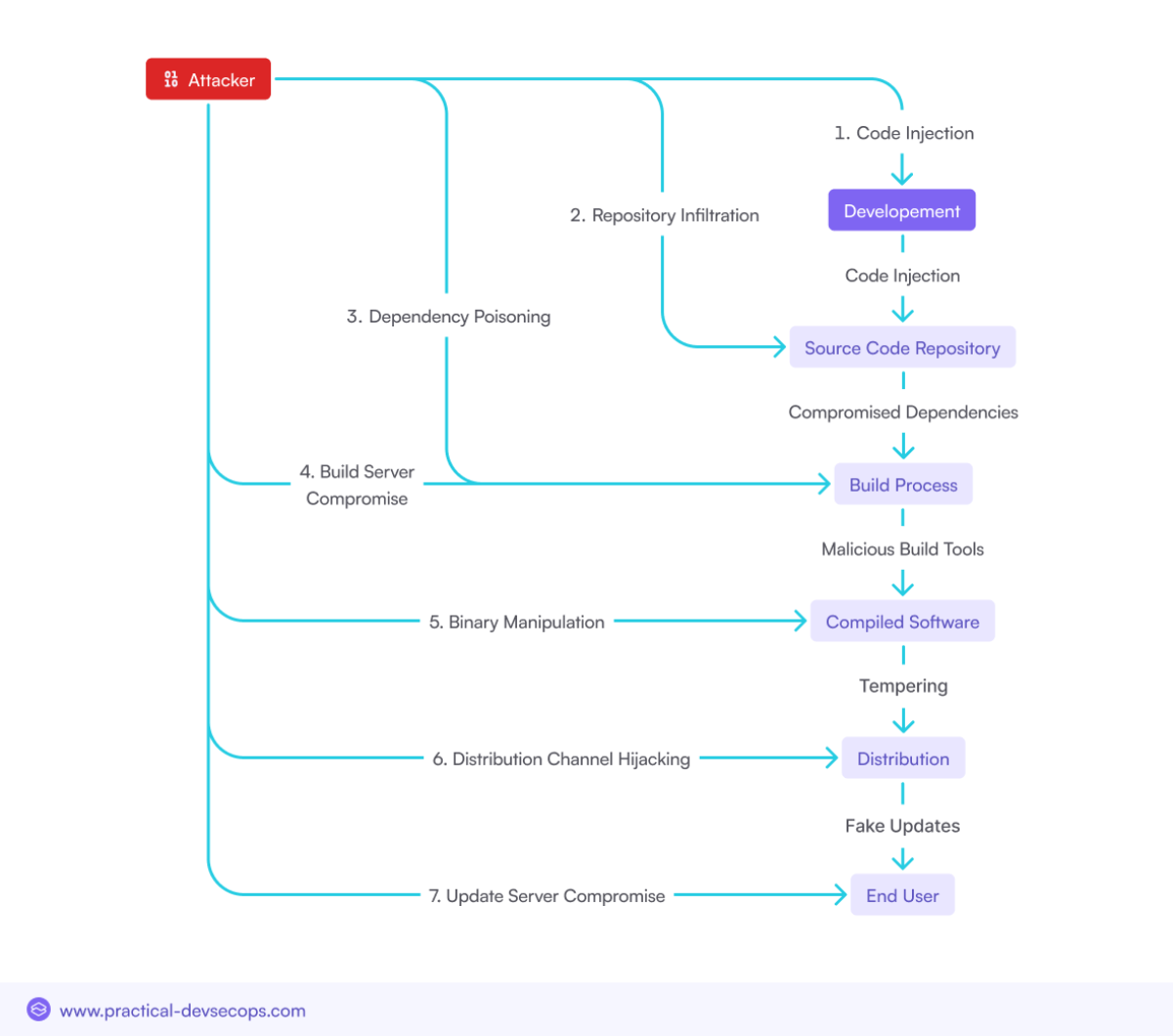
Software supply chain attacks have increased in significance over the years, jeopardizing organizations worldwide. These are attacks on the more insecure parts of the software development and distribution pipeline, targeted at badly secured systems in a very broad sense. This is the reason they happen:
- Bigger attack surface area: Contemporary software programs utilize many third-party components, raising the number of entry points for malicious cybercriminals.
- Hard to detect: Supply chain attacks typically use trusted sources, making them more challenging to identify than traditional malware.
- High Impact: An attacker could exploit a single part to compromise thousands of end-users, making these attacks highly appealing among cyber criminals.
- Poor security practices: Many companies lack stringent security measures to verify and monitor third-party software.
- Sophistication of threat actors: Advanced persistent threats (APT) and nation-state hackers are investing heavily in supply chain attack techniques.
- Software development automation (e.g.CI/CD pipelines): Unfortunately, automating software delivery with a continuous integration/continuous deployment (CI/CD) pipeline introduces vulnerabilities if not properly secured.
Different Types of Software Supply Chain Attacks
Malicious Code Injection
Attackers infiltrate the software development process to inject malicious code into the final product. This code can be designed to steal data, enable unauthorized access, or create backdoors for future exploitation.
Compromised Dependencies
Many software projects rely on third-party libraries and packages. Attackers compromise these dependencies by introducing malicious updates, which then propagate through the supply chain to end-users.
Supply Chain Hijacking
This involves taking control of legitimate software distribution channels, such as update servers or package repositories, to distribute malicious software or updates to users.
Secure Your Software Supply Chains Now! Download our essential e-Book guide.
Most Recent High-Profile Software Supply Chain Attacks
Major Software Supply Chain Attacks (2020-2024)
The past few years have witnessed several significant software supply chain attacks, each highlighting the vulnerabilities in our interconnected digital ecosystem:
3CX Supply Chain Attack
The 3CX desktop app, utilized by many thousands of businesses around the world, was breached via what is described as an advanced supply chain attack.
My take: This hack was the result of attackers embedding their malicious code into a real software update being distributed as an official part of the development process.
Impact: The attack compromised tens of thousands of individuals by enabling unauthorized access to sensitive data, including voice communications. The breach revealed a flawed software developmental process and concerns regarding third-party software dependencies.
SolarWinds Attack
The SolarWinds attack compromised the Orion software supply chain. Attackers infiltrated SolarWinds’ network in September 2019 and by March 2020 had injected malicious code into Orion updates. These compromised updates were distributed to over 18,000 customers, allowing attackers to spy on various organizations’ IT systems.
My Take: This breach exposes critical vulnerabilities in supply chain security, demonstrating how third-party suppliers can become gateways for widespread cyber espionage. It underscores the urgent need for organizations to reassess their security measures, particularly regarding external vendor software and services.
Impact: The attack inflicted significant financial damage, with affected organizations losing an average of 11% of annual revenue (up to 14% in the US). It also catalyzed improved information sharing and cybersecurity practices across private and public sectors, prompting a reevaluation of supply chain security protocols.
Codecov Bash Uploader Attack
In 2024, a supply chain attack successfully carried out resulted in the modification of Bash Uploader provided by a popular tool to upload code coverage to Codecov. This is the script that a lot of developers used to send coverage reports up to Codecov, and this altered version was capable of beaming out environment variables — such as tokens or keys.
My Take: Many projects were left open to their secrets being exposed, possibly impacting many thousands of people. This attack highlighted that best security practices should be followed for development environments and how dangerous it is to depend on out-of-box scripts.
Impact: The attack led to widespread secret rotation, eroded trust in third-party tools, increased scrutiny of CI/CD pipelines, and attracted regulatory attention. It spurred industry-wide changes in code coverage tool design, caused financial losses, and accelerated the adoption of advanced security measures like SBOM and integrity verification.
Kaseya VSA Supply Chain Attack
Bad actors built upon the tactics used in the 2021 Kaseya VSA attack and went after the remote monitoring and management software once again, this time in 2024. They used a zero-day vulnerability to distribute their ransomware through the software’s update mechanism.
My Take: This assault led to significant ransomware exposures in hundreds more companies, and small and medium-sized enterprises (SMEs). Following an investigation, it was discovered to have caused severe operational disruptions and financial damage, further underscoring the risk posed by supply chain attacks against key infrastructure.
Impact: The 2021 Kaseya VSA attack caused widespread ransomware infections, primarily affecting SMEs. It resulted in substantial financial losses, data breaches, and prolonged service disruptions. The incident prompted stricter regulations on managed service providers, accelerated the adoption of zero-trust architectures, and highlighted the critical need for robust software supply chain security measures.
PyPI and NPM Package Poisoning
A series of package poisoning attacks affected the Python Package Index (PyPI) as well as Node. Hackers published packages that appeared to be genuine but included underlying malware. The idea was that these packages would be downloaded by developers and tamper with their projects.
My Take: This attack exploits trust in open-source ecosystems, revealing a critical weakness in the software supply chain. It demonstrates the need for enhanced verification in package repositories and automated security checks in development pipelines. The incident challenges the current open-source model and suggests a need for improved oversight or community-driven security measures.
Impact: The attacks affected thousands of developers and potentially exposed hundreds to thousands of their applications to compromise. This incident emphasized that open-source software security ecosystems require good faith and security vigilance.
Tactics, Techniques, and Procedures (TTPs) Used
Typical characteristics of these attacks, often with common tactics, techniques, and procedures (TTPs), include:
- Advanced Persistent Threats (APTs): APT attackers typically operate below the radar for an extended period to accomplish their goals. They let attackers exploit vulnerabilities before they have been patched out, which can prevent traditional security measures from identifying the attacks.
- Phishing and Social Engineering: Attackers often utilize phishing as an initial means of entry, whether it be credential harvesting or the initiation of malicious code via endpoint.
Emerging Trends in Software Supply Chain Attacks
Increasing Use of Open-Source Software Security Implications
The widespread adoption of open-source software brings both benefits and risks. While open-source components can accelerate development and reduce costs, they also introduce vulnerabilities if not properly managed. The increasing use of these components has expanded the attack surface, making it easier for attackers to introduce malicious code into widely used libraries and frameworks.
Rise of Supply Chain Ransomware Attacks
Ransomware attacks have evolved to target software supply chains, where attackers compromise the software delivery process to spread ransomware to multiple organizations simultaneously. This trend is particularly concerning given the cascading effects that can result from a single successful attack.
Targeting of Software Build and CI/CD Pipelines
The software build process and Continuous Integration/Continuous Deployment (CI/CD) pipelines are becoming prime targets for attackers. By compromising these pipelines, attackers can introduce malicious code that is automatically integrated into software products, which are then distributed to end-users.
Exploitation of Software Vulnerabilities and Misconfigurations
Attackers continue to exploit vulnerabilities and misconfigurations in software components. This includes exploiting known vulnerabilities in open-source libraries or misconfigurations in cloud environments, which can provide a foothold for deeper attacks within the supply chain.
Open-Source Software Security Challenges
Benefits and Risks of Using Open-Source Software
The advantages of open-source software security are plenty, showing flexibility, creativity, and even cost control. The risks, however, are substantial:
- Lack of Formal Support: Many open-source projects do not include any form or level of formal support, leaving organizations bare in case security issues arise.
- More Open Exposure: Key observation: Due to the publicity of these projects, if there is a vulnerability, it is not only visible to everyone but also to attackers.
- Dependent on Third-Party Maintainers: Security relies heavily on the watchful eye and backing of others within that open-source community, or those individual maintainers who may not always prioritize security.
Malicious Packages in Open-Source Repositories
It’s a dangerous trend: the rise of malicious packages within repositories like PyPI, NPM, and RubyGems. Attackers are uploading what appear to be valid packages, with embedded malicious code that can then be pulled into software projects.
Strategies for Open-Source Software Security in the Supply Chain
To mitigate these risks, organizations should:
Implement SCA: SCA tools can help you work on the identification of open-source components and management, allowing your organization to rely on only vetted and secure dependencies, thus reducing risks.
Implement Strong Vetting Processes: Organizations should evaluate components before they include them in their systems to scrutinize the code and identify any already-known vulnerabilities.
Community Involvement: The open-source community can help organizations remain aware of security announcements, as well as contribute to the betterment of software they are dependent on.
CI/CD Pipeline Security in Software Supply Chains
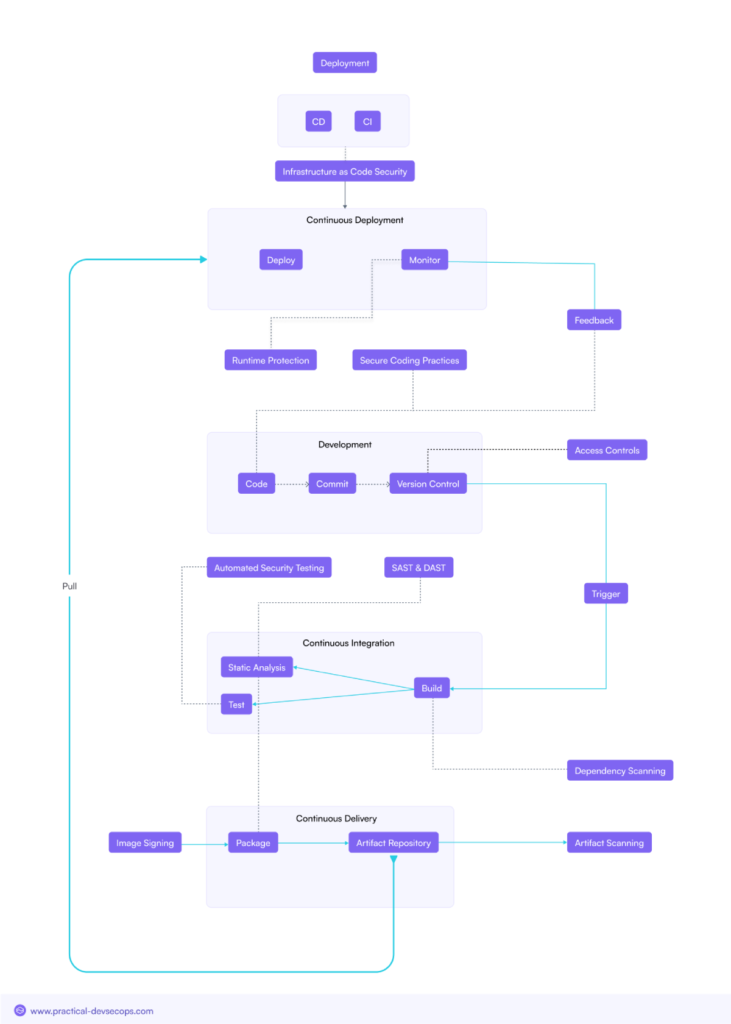
Importance of Securing CI/CD Pipelines
CI/CD pipelines are integral to modern software development, enabling rapid delivery of code changes. However, their critical role also makes them a prime target for attackers. Securing these pipelines is essential to preventing the introduction of vulnerabilities into the software products they generate.
Common Attack Vectors Targeting CI/CD Pipelines
- Compromised Build Servers: Attackers target build servers, injecting malicious code during the build process.
- Malicious Code Injection: Code injected at any stage of the CI/CD pipeline can propagate through to production, affecting end-users.
- Supply Chain Hijacking: Attackers gain control of distribution channels within the CI/CD pipeline, allowing them to deliver compromised software to customers.
Best Practices for Securing CI/CD Pipelines
In securing CI/CD pipelines, organizations must follow best practices that include:
Code Signing: Digitally signing all code verifies its origin and integrity.
Secure Build Environments: Isolate build environments to prevent unauthorized access and limit the scope for the introduction of malicious code.
Artifact Signing and Verification: Sign and verify all build artifacts so that only legitimate, unaltered software is being deployed.
Strategies for Mitigating Software Supply Chain Risks
Comprehensive Software Supply Chain Security Program
For B2B enterprises, focus on defense against the latest software supply chain threats. This program should encompass all aspects of software development, procurement, and distribution, with a focus on continuous monitoring and improvement.
Risk Assessments and Prioritization
Conducting thorough risk assessments is critical to identifying and prioritizing the most critical software components. By understanding where the greatest risks lie, organizations can allocate resources more effectively and mitigate potential threats before they are exploited.
Secure Software Development Practices
- Secure Development Lifecycle (SDLC): Deploying security in every phase of the application lifecycle.
- Secure Coding: keeping code secure and making sure it’s written with security in mind. All new code must be tested to find out if there are any vulnerabilities, either when produced or before deployment.
Supply Chain Risk Management Processes
Effective supply chain risk management involves:
– Vendor Risk Assessments: Evaluating the security practices of vendors and suppliers to ensure they meet organizational standards.
– Third-Party Monitoring: Continuously monitoring third-party components for vulnerabilities and potential threats.
Software Composition Analysis (SCA) Tools
SCA tools are invaluable for identifying and managing open-source components within the software supply chain. These tools can detect outdated or vulnerable dependencies, helping to mitigate the risk of exploitation.
Secure Software Delivery and Deployment
If we take it one step further, it becomes clear that when development is important to security, then delivering and deploying the software securely becomes the top priority.
Code Signing: Allows verification of code source before deployment.
Artifact Check: Make sure that the artifacts generated during the build are damage-free and as expected before deployment.
Secure Updates address the vulnerabilities in ecosystems that they both expose and provide an update path to keep pace with emerging threats by providing a secure mechanism for updating, so other PCs cannot deceive it as well.
Incident Response and Recovery Plans
Finally, organizations must be prepared to respond to and recover from software supply chain attacks. This includes establishing incident response plans that outline the steps to take in the event of an attack, as well as recovery plans to restore normal operations as quickly as possible.
Relevant Regulations and Industry Standards
A range of regulations and industry standards have been developed to guide organizations in securing their software supply chains. These include:
- NIST SP 800-161: Guides managing supply chain risks in federal information systems.
- ISO/IEC 20243: The Open Trusted Technology Provider Standard, which addresses security in the ICT supply chain.
- CMMC (Cybersecurity Maturity Model Certification): A framework that standardizes cybersecurity practices across the defense industrial base.
Conclusion
Now more than ever, the issue of software supply chain security is incredibly important in an increasingly digital world. Given that software supply chains now face increasing complexity, the risks have also increased. Organizations can remain protected and safeguard their customers from the devastating results of supply chain attacks by understanding how these threats operate, coupled with adequate security strategies.
Organizations must review their security posture at regular intervals and take a proactive stance in risk mitigation, right from securing CI/CD pipelines to managing open-source components and complying with industry regulations. This will enable them to forge a more trusted chain and withstand the increasingly sophisticated threats of the digital age.
Ready to secure your software supply chain against rising threats? Join thousands of security professionals who have enhanced their security skills with Practical DevSecOps certifications. Sign up today and upgrade your security skills.











