What Are Software Composition Analysis (SCA) Tools and Why They Matter
Modern software depends heavily on open source libraries. In fact, recent studies show that more than 77 percent of code in applications today comes from open source components. This accelerates innovation but also creates new security and compliance challenges. That’s why SCA security tools have become essential to protect open source dependencies, reduce software supply chain risks, and keep applications safe from hidden vulnerabilities and malware. Even a single outdated library or overlooked dependency can expose critical risks in production.
That is why using the best software composition analysis tools has become essential for every development and DevSecOps team. These solutions help you identify and manage risks in your open source dependencies, protect against known and unknown threats, and keep your applications secure throughout the entire lifecycle.
Unlike older scanners that only list vulnerabilities, modern SCA tools analyze how open source libraries are used inside your code. They can tell if a vulnerable function is actually executed, if a fix may cause build errors, or if an open source package contains hidden malware. The result is a clearer, more accurate view of risk that helps teams focus on what truly matters.
Definition: What Are Software Composition Analysis Tools
Software Composition Analysis (SCA) tools are security solutions that identify, monitor, and manage open source libraries used in software projects. They detect security vulnerabilities, track license compliance, and help prevent supply chain risks in real time.
In simple terms, SCA tools give developers and security teams full visibility into their dependencies, showing what code they use, what risks exist, and how to fix them safely. They are now a key part of securing modern software and maintaining trust in open source ecosystems.
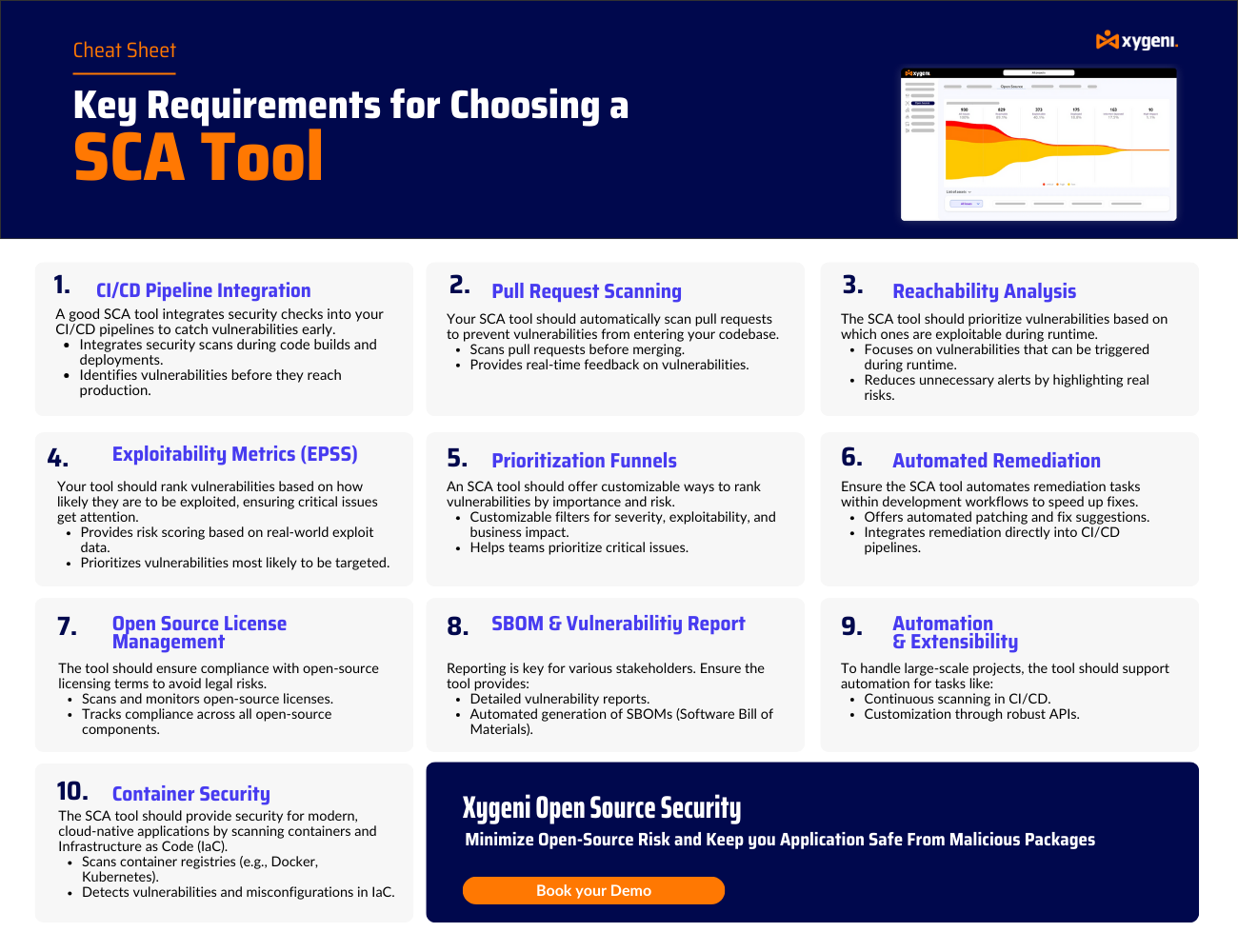
Essential Features to Consider in SCA Tools
Key Considerations for Choosing Software Composition Analysis Vendor
When selecting the best SCA tools for your team, it’s not just about finding vulnerabilities, it’s about choosing a solution that fits how you build and ship software. Software composition analysis tools vary greatly in functionality. Consequently, the right SCA tools should support your security goals without disrupting velocity or introducing friction.
To that end, here are the essential features to consider in SCA tools today:
1. Prioritization Funnels
To begin with, the best SCA tools help teams focus on what matters most. They filter vulnerabilities based on exploitability, severity, and context. As a result, your developers waste less time on noise and more time fixing high-risk issues.
2. Reachability Analysis
Although some packages might contain CVEs, they aren’t always dangerous. Reachability analysis determines if the vulnerable code is actually executed at runtime. That way, you can focus only on threats that are exploitable.
3. Exploitability Metrics
Additionally, modern software composition analysis tools include exploitability metrics like EPSS and known attack vectors. This helps your team measure risk more accurately and respond faster to real threats.
4. Severity Scoring (CVSS)
Of course, CVSS scoring remains essential. It helps developers understand how critical a vulnerability is and how quickly it needs to be addressed. The best SCA tools display this data clearly within the developer workflow.
5. Contextual Analysis
Instead of flooding teams with raw CVE data, top software composition analysis tools provide actionable context. For example, they highlight affected components, relevant paths, and potential attack vectors. This gives your team better insight into each issue.
6. Automated Remediation
Also, the best SCA tools don’t just find problems, they help fix them. They suggest exact fixes or even create pull requests automatically. This saves time, shortens the fix cycle, and lets your team stay focused on building.
7. Seamless CI/CD Integration
Equally important, the tool must work inside your CI/CD environment. Whether you’re using GitHub Actions, GitLab, Jenkins, or Bitbucket, the tool should scan dependencies in real time, without slowing down the pipeline.
8. Policy Management
Not only should your team detect risks, but you should also be able to control them. Policy-as-code features allow you to define and enforce rules across repositories and pipelines, supporting governance and compliance.
9. Comprehensive Reporting
Finally, you need visibility. That’s why the best SCA tools include customizable reports for audits, security reviews, and executive dashboards, making it easier to track progress and prove compliance.
Best Software Composition Analysis Tools
Before diving into the details of each platform, the table below summarizes how the main software composition analysis tools (SCA tools) compare in terms of key capabilities such as exploitability scoring, license management, malware detection, and overall suitability for DevSecOps workflows.
| Tool | Focus Area | Exploitability Scoring | License Management | Malware Detection | Best For |
|---|---|---|---|---|---|
| Xygeni | Complete software supply chain protection | ✅ EPSS and Reachability | ✅ Advanced | ✅ Yes, real-time behavior-based | Teams needing full SCA, malware defense, and CI/CD integration |
| Snyk | Developer-first vulnerability scanning | ⚠️ Limited | ✅ Basic | ❌ None | Developers seeking fast integration with IDEs and CI/CD |
| Black Duck | Deep open source and license compliance analysis | ⚠️ Limited | ✅ Advanced | ❌ None | Large enterprises requiring detailed license and policy management |
| Veracode | Enterprise compliance and AppSec integration | ❌ None | ✅ Advanced | ❌ None | Regulated organizations focused on governance and auditability |
| Sonatype Lifecycle | Policy automation and supply chain security | ✅ Partial reachability | ✅ Advanced | ❌ None | Teams needing automated governance across SDLC |
| JFrog Xray | Binary and container analysis | ⚠️ Basic | ✅ Advanced | ⚠️ Available in premium plans | Teams using JFrog ecosystem for artifact and container security |
| Checkmarx One | Unified AppSec platform with SCA | ✅ Exploitable Path Analysis | ✅ Advanced | ⚠️ Partial | Enterprises already using Checkmarx for static analysis |
| Semgrep Supply Chain | Lightweight, developer-focused SCA | ✅ Reachability-based | ✅ Basic | ❌ None | Small teams wanting fast, easy adoption |
| Mend.io | Open source risk detection and compliance | ⚠️ EPSS-based | ✅ Basic | ❌ None | Organizations seeking automated vulnerability and license alerts |
| OX Security | DevSecOps-native pipeline protection | ⚠️ Limited | ✅ Basic | ❌ None | Teams focused on securing CI/CD workflows end to end |
The Most Advanced SCA Tool for DevSecOps
Overview:
Xygeni SCA security tools make open source security easier for developers. Instead of just listing every known vulnerability, they help you focus on what really matters by checking whether the risky code is actually reachable, exploitable, or a real threat.
What’s more, Xygeni scans in real time, fits right into your CI/CD, and even catches hidden dangers like malware in dependencies. It also takes care of license risks and compliance, so you don’t have to chase them manually.
Put simply, Xygeni-SCA is one of the best SCA tools out there. It helps you secure your supply chain, fix issues fast, and stay focused on shipping code, without slowing you down.
Key Features:
- Remediation Risk Insights
Before applying a patch, Xygeni shows you the trade-offs: what’s fixed, what could break, and what new risks might be introduced. This way, you choose the smartest upgrade, not just the next version. - Advanced Vulnerability Detection
Integrated with NVD, OSV, and GitHub Advisories for complete visibility into open-source risks. As a result, teams get timely, accurate threat intelligence. - Prioritization Funnels
Customizable risk scoring based on severity, exploitability (EPSS), business impact, and reachability. Consequently, you focus on what truly matters. - Reachability & Exploitability Analysis
Detects which vulnerabilities are actually accessible during runtime and how likely they are to be exploited. Therefore, teams avoid wasting time on false alarms. - CI/CD & Pull Request Integration
Automatically scans during builds and pull requests to catch issues early, in other words, security checks happen without slowing delivery. - Automated Remediation
Suggests or applies fixes directly within developer pipelines, so that teams can resolve issues faster with minimal manual effort. - Real-Time Malware Detection
Blocks malware hidden in open-source packages using behavior-based analysis and early warning signals. In the meantime, this provides continuous protection. - License Compliance Management
Helps you track and comply with open-source licenses using OWASP best practices. Accordingly, it reduces legal risk and enforces policy. - SBOM & VDR Generation
Generates Software Bill of Materials and Vulnerability Disclosure Reports on demand to ensure transparency and meet compliance requirements.
Why Choose Xygeni?
- Exclusive Early Malware Detection → Xygeni is the only SCA tool with real-time, behavior-based malware scanning across open-source dependencies and DevOps workflows.
- More than just vulnerability detection → Includes malware protection, license governance, and automated remediation in one unified platform.
- Smarter prioritization → Combines EPSS, reachability, and business context to ensure your team focuses on the most critical risks.
- Built for developers → Seamless CI/CD integration, real-time scanning, and actionable fixes—all without disrupting delivery.
- Proactive supply chain defense → Detects typosquatting, dependency confusion, and zero-day threats before they hit production.
💲 Pricing*:
- Starts at $33/month for the complete all-in-one platform, no hidden fees or extra charges for critical features.
- Unlike other vendors, it includes everything: SCA, SAST, CI/CD Security, Secrets Detection, IaC Security, and Container Scanning, all in one unified plan.
- Moreover, there are no limits on repositories or contributors, no per-seat pricing, no usage caps, and no surprises.
2. Snyk SCA Tool

Overview:
Snyk is one of the most well-known Sca Security tools, widely favored for its developer-first approach and strong ecosystem integrations. From the start, it allows teams to detect and remediate vulnerabilities directly within their development environments, making it especially appealing for agile DevSecOps workflows.
However, although it is widely adopted, Snyk primarily focuses on SCA and lacks advanced capabilities such as reachability analysis, exploitability scoring, and real-time malware detection. As a result, its coverage may fall short for teams seeking more comprehensive open-source security.
Key Features:
- Developer-Centric Integration → Specifically works in IDEs, Git, and CI/CD pipelines to catch vulnerabilities as early as coding and pull requests.
- Risk-Based Prioritization → Combines EPSS, CVSS, exploit maturity, and reachability to create a dynamic risk score.
- Automated Fixes → Notably provides one-click pull requests with recommended patches and upgrade paths to speed up remediation.
- Continuous Monitoring → Consequently, tracks newly disclosed vulnerabilities across environments and keeps teams informed in real time.
- License & Compliance Management → In addition, supports governance policies and license enforcement through customizable reporting and automation.
Cons:
- No Malware Detection → Does not protect against unknown malware or supply chain attacks like typosquatting.
- Limited Supply Chain Coverage → Focuses only on known CVEs, with no anomaly detection or build integrity features.
- Pricing Grows Quickly → Since all products are sold individually, costs scale per contributor and feature, making it harder to manage budget in larger teams.
💲 Pricing*:
- Starts with 200 tests/month on the Team plan — however, SCA is not included and must be purchased as an add-on. It also cannot run independently without a base plan.
- Features sold separately — Snyk’s pricing is modular, requiring individual purchases for SCA, Container Security, IaC, Secrets, and others.
- Total cost scales per feature — pricing depends on the number of features selected, and all are billed together in the same plan.
- No public pricing for full coverage — you’ll need a custom quote. Consequently, costs increase rapidly as usage and team size grow.
3. BlackDuck by Synopsis SCA Tool

Overview:
Black Duck by Synopsys is one of the most established software composition analysis tools, specifically focused on identifying and managing risks in open-source and third-party code. To achieve this, it provides deep visibility across the software supply chain through a combination of scanning technologies and offers strong support for license compliance and SDLC integration.
Nevertheless, it can be heavy to manage for some teams and, more importantly, lacks developer-centric ease of use and real-time malware protection. Consequently, teams may face friction when trying to embed it seamlessly into fast-moving DevSecOps workflows.
Key Features:
- Comprehensive Component Analysis → Scans for vulnerabilities, license compliance, and quality risks across source code, binaries, artifacts, and containers.
- Multiple Scanning Techniques → Supports Dependency, Binary, Codeprint, and Snippet Analysis to detect even undeclared components.
- Risk Prioritization → Specifically leverages Black Duck Security Advisories to evaluate severity, impact, and context—enabling more informed remediation.
- Policy Management & Automation → Accordingly, allows enforcement of open-source usage policies across development, build, and deployment stages.
- SBOM Generation & Monitoring → Create, import, and monitor SBOMs with SPDX/CycloneDX support for transparency and compliance.
Cons:
- No Real-Time Malware Detection → Cannot proactively detect or block malware in open-source dependencies.
- Heavy Operational Overhead → Due to its depth, it can be resource-intensive to deploy, scale, and maintain across environments.
- Limited Developer Experience → Also lacks seamless IDE integration and developer-first UX, which may slow adoption and increase friction for engineering teams.
💲 Pricing*:
- Starts at $525/year per team member (Security Edition) — billed annually, with a minimum of 20 users.
- No flexibility — all users must be licensed equally across the organization.
- Supply Chain Edition requires custom pricing — needed for advanced features like binary scanning, snippet analysis, and SBOM automation.
4. Veracode SAST Tool

Overview:
Veracode’s Software Composition Analysis (SCA) is part of its broader application security platform. Specifically, it focuses on identifying vulnerabilities and license risks in open-source components, with a strong emphasis on enterprise compliance and policy enforcement.
However, while it is well-integrated into the Veracode ecosystem, it ultimately lacks deeper exploitability context and developer-friendly automation features found in more modern software composition analysis tools. As a result, teams may find it harder to prioritize real threats or streamline remediation within fast-paced development environments.
Key Features:
- Integrated AppSec Platform → SCA works as part of Veracode’s comprehensive suite, thereby streamlining security efforts across static, dynamic, and open-source testing.
- Automated Scanning → Automatically detects vulnerabilities in open-source components, especially during scheduled or triggered code analysis.
- Detailed Reporting → Consequently, provides comprehensive reports on vulnerabilities and license compliance to support enterprise-level risk management.
- Policy Enforcement → Enables organizations to define and enforce security and compliance policies consistently across all pipelines.
Cons:
- No EPSS or Reachability Analysis → As a result, lacks vulnerability prioritization based on exploitability or runtime relevance.
- No Malware Detection → Cannot proactively identify or block malicious open-source components in real time.
- Less Developer-Friendly → Additionally, its platform-focused design may limit seamless integration with diverse development tools and workflows.
💲 Pricing*:
- Median contract value is $18,633/year — based on real customer purchase data.
- No all-in-one plan, however, SCA must be purchased alongside other Veracode solutions for full coverage.
- Custom quotes required, as a result, there is no transparent or self-serve pricing available.
5.Sonatype Nexus Lifecycle

Overview:
Sonatype Lifecycle is a powerful SCA tool built to help teams manage open-source security and governance throughout the entire software development lifecycle. To begin with, it offers useful features like automated policy enforcement, real-time risk detection, and tools that help developers fix issues quickly.
However, many of its key features require extra platform components. In addition, pricing is split across different modules, which makes it harder to understand the full cost upfront. As a result, teams looking for a simpler and more predictable solution might find it challenging to manage both setup and budget.
Key Features:
- Automated Governance → Enforces custom security and license policies throughout development, CI/CD, and deployment pipelines. In this way, organizations can maintain consistent standards across all teams.
- Real-Time Vulnerability Detection → Continuously monitors for known vulnerabilities and license risks across open-source components. As a result, teams gain faster awareness of emerging threats.
- AI-Driven Dependency Management → Automatically applies waivers and upgrades based on dynamic risk assessments. Moreover, this reduces manual effort and improves consistency.
- Prioritization Engine → Uses reachability and real-time signals to surface the most impactful threats for remediation. Consequently, developers can focus on what truly matters instead of sorting through noise.
- Developer Dashboard → Centralizes insights for developers inside their existing tools to improve adoption and reduce response time. Notably, this improves collaboration between security and engineering.
- SBOM Management → Offers export in SPDX and CycloneDX formats. However, full automation and compliance support may require additional components.
Cons:
- No real-time malware detection → As a result, it lacks proactive defense against malicious open-source packages that may compromise your pipeline.
- Modular platform requirements → In other words, core features only work if you add extra tools like IQ Server, SBOM Manager, or Firewall.
- Fragmented pricing model → Consequently, teams must purchase multiple licenses and add-ons, which increases both cost and setup complexity as you grow.
💲 Pricing*:
- Starts at $57.50/month per user; however, it also requires a separate IQ Server license, only available via custom quote.
- Additionally, there is no unified pricing, features like SBOM, Firewall, and Container Security must be purchased individually.
- As a result, the fragmented licensing model causes the total cost to grow based on tools, user count, and deployment setup.
6. Jfrog Xray SCA Tool

Overview:
JFrog Xray is a software composition analysis tool built to protect binaries, containers, and open-source packages. It integrates tightly with the JFrog platform, offering early detection and continuous monitoring throughout the entire SDLC. As a result, developers can catch risks early without changing how they work.
However, some of its most advanced features, such as malware detection and deep risk scoring, depend on proprietary systems. In addition, access to these features often requires purchasing extra modules. Consequently, teams may face added costs and complexity during setup.
Key Features:
- Recursive Scanning → Scans deep into binaries, containers, and open-source packages. As a result, you get complete visibility into vulnerabilities and license risks.
- Malware and Threat Detection → Uses internal threat intel to detect malicious components. Notably, this includes risks not listed in public CVE feeds.
- SBOM and VEX Support → Generates SPDX and CycloneDX SBOMs with VEX annotations. In other words, it helps teams stay compliant and audit-ready.
- Operational Risk Policies → Blocks untrusted packages based on age, contributor activity, and usage trends. Consequently, risky components are excluded early.
- IDE and CI/CD Integration → Delivers real-time feedback directly in dev tools and pipelines. This way, security is enforced without slowing delivery.
- Security Research-Powered → Enriches CVEs with contextual insights from internal research. To that end, teams get better clarity on actual risk.
Cons:
- No exploitability scoring (e.g., EPSS) → Therefore, prioritization lacks runtime and reachability context.
- Tightly coupled to the JFrog ecosystem → Because of this, it’s ideal only for users already on JFrog; standalone use is limited.
- Advanced features require extra licensing → For example, capabilities like Advanced Security or Runtime Integrity are available only in top-tier plans.
💲 Pricing*:
- Starts at $960/month. SCA features are locked behind the Enterprise X tier.
- Additionally, core features like Package Curation and Runtime Integrity are sold separately.
- All in all, pricing is fragmented and grows quickly with add-ons and deployment scale.
7. Checkmarx One SCA

Overview:
Checkmarx One SCA provides software composition analysis as part of a broader application security platform. Specifically, it helps detect open-source vulnerabilities, license risks, and malicious packages, offering advanced features like exploitable path detection and SBOM generation.
However, it lacks built-in malware protection across the SDLC and doesn’t offer real-time, reachability-based prioritization. Moreover, capabilities that are typically unified in other platforms require separate modules here. As a result, its reliance on enterprise licensing and modular add-ons can significantly increase both complexity and cost for security teams.
Key Features:
- Exploitable Path Detection → Highlights which vulnerabilities are actually reachable during runtime. As a result, teams can prioritize what truly matters.
- Malicious Package Detection → Identifies weaponized open-source components. This way, supply chain threats are blocked before they reach production.
- Private Package Scanning → Scans proprietary and internal packages, even if they are not listed in public registries. Therefore, hidden risks don’t go unnoticed.
- License Risk Analysis → Flags open-source license issues with clear, actionable reports. In this way, legal and compliance risks are easier to manage.
- SBOM Generation → Exports SPDX and CycloneDX SBOMs in one click. Accordingly, it simplifies audits and supports regulatory requirements.
- AI-Generated Code Scanning → Analyzes AI-assisted code for hidden security risks and policy violations. Consequently, you stay in control—even when using generative code.
Cons:
- No real-time malware detection → Lacks continuous behavioral scanning for emerging threats.
- No native CI/CD or pipeline integration for SCA → Instead, it relies on broader Checkmarx platform integration, which adds setup overhead.
- Modular setup increases complexity → Full SCA coverage may require pairing with other Checkmarx solutions.
- Custom licensing only → Without self-serve pricing, budgeting and procurement become both less predictable and more time-consuming.
💲 Pricing*:
- Starts at enterprise-level pricing: reported deployments range from $75,000 to $150,000/year.
- No all-in-one plan, instead, SCA is one of many modular solutions; full coverage requires bundling multiple tools.
8. Semgrep SCA Tool

Overview:
Semgrep Supply Chain is a lightweight SCA solution designed for developers. It reduces alert fatigue using reachability-based prioritization and offers core features such as license compliance, SBOM generation, and actionable remediation.
However, it lacks critical protections for CI/CD pipelines, build systems, and malware threats. As a result, key stages of the software supply chain remain exposed, limiting its suitability for comprehensive AppSec programs.
Key Features:
- Reachability-Based Prioritization → Flags only vulnerabilities invoked at runtime.
- License Compliance Enforcement → As a result, it can block risky packages directly at the PR level to prevent violations from being merged.
- SBOM Generation → Supports CycloneDX with full dependency search.
- Developer-Centric UX → Integrates with IDEs, GitHub, GitLab, and popular CI/CD tools.
- Remediation Insights → For that reason, it highlights affected code lines and delivers step-by-step guidance to streamline fixes.
Cons:
- No CI/CD or Build Security → Therefore, it can’t secure pipelines, builds, or production artifacts.
- No Malware Detection → Consequently, it cannot identify malicious packages in your software supply chain.
- Fragmented Feature Set → Requires separate purchases for Code, Supply Chain, and Secrets modules.
- Costs Scale Fast → In effect, contributor-based pricing increases rapidly with team size.
💲 Pricing*:
- Starts at $40/month per contributor per product.
- No all-in-one platform: must buy each product separately to cover the full SDLC.
- License lock-in: all contributors must be licensed equally across all modules.
9. Mend.io SCA Tool

Overview:
Mend.io SCA is part of a complete AppSec platform built to find and fix open-source vulnerabilities, license issues, and supply chain threats. In particular, it offers reachability analysis and smart prioritization to help you focus on real risks, not just raw CVE counts.
However, most core features are only available with a premium license. As a result, teams looking for flexibility may need to pay for the full suite, which can raise overall costs and limit adoption.
Key Features:
- Reachability Analysis → Flags only the vulnerabilities that are actually exploitable in your code. Therefore, teams don’t waste time on low-risk issues.
- EPSS-Based Risk Prioritization → Combines CVSS severity scores with exploit data to rank the threats that matter most. Consequently, developers can fix what’s urgent first.
- License Compliance Alerts → Spots problematic open-source licenses early and supports real-time enforcement. In this way, you reduce legal and operational risks.
- SBOM Generation → Produces machine-readable SBOMs in SPDX and CycloneDX formats. To that end, it helps you stay compliant and audit-ready.
Cons:
- No Malware Detection → Lacks proactive scanning for malicious open-source packages, leaving gaps in supply chain protection.
- Limited Exploitability Context → While it includes EPSS, Mend SCA doesn’t provide runtime-level reachability or in-depth function traceability.
- Restricted Custom Policy Automation → Less granular automation for vulnerability blocking or pre-merge enforcement compared to more specialized platforms.
- Heavy Dependence on Platform Integration → SCA features are tightly coupled with Mend’s full suite, limiting flexibility for teams using other tools in their SDLC.
💲 Pricing*:
- Starts at $1,000/year per contributing developer — includes SCA, SAST, container scanning, and more.
- Extra charges apply for Mend AI Premium, DAST, API Security, and support services, consequently, advanced protection adds significantly to the base price.
- No usage-based flexibility, as a result, cost scales steeply with team size and feature adoption.
10. OX Security SCA Tool

Overview:
OX Security SCA is designed to secure open-source dependencies using DevSecOps-native workflows. Notably, it introduces innovative ideas like the Pipeline Bill of Materials (PBOM), which brings visibility beyond traditional SBOMs. In addition, it automates remediation tasks, helping teams manage vulnerabilities more efficiently throughout development and into production.
However, it still lacks some critical features. For example, it does not offer deep exploitability analysis, real-time malware detection, or rich runtime context. As a result, security teams may find it difficult to prioritize real threats. This means more alert fatigue, more manual triage, and potentially weaker protection across the software supply chain.
Key Features:
- PBOM Visibility → Goes beyond standard SBOMs by offering pipeline-level insight. Therefore, teams get a clearer view of supply chain risks.
- Automated Risk Remediation → Detects and fixes issues across both development and post-production environments. This helps reduce response time and operational overhead.
- CI/CD & Dev Tools Integration → Connects with your existing pipelines and developer tools. In this way, it minimizes disruption while keeping workflows secure.
Cons:
- No Malware Detection → Cannot detect malicious packages or backdoors in OSS dependencies.
- Shallow Reachability Analysis → Lacks runtime exploitability tracing and fine-grained function-level insights.
- Limited Market Maturity → As a newer vendor, integration depth and community support are still evolving.
💲 Pricing*:
- Custom quote required:Therefore, no public pricing or self-service plan is available.
- Lack of transparent pricing and unclear SCA-only offering. As a result, the total cost is difficult to estimate.
Quick Summary
- Xygeni: Complete SCA protection with reachability analysis, exploitability scoring, and real-time malware detection across CI/CD pipelines.
- Snyk: Developer-friendly tool for fast vulnerability scanning and remediation in IDEs and pipelines.
- Black Duck: Enterprise-grade visibility into open source libraries and strong license compliance control.
- Veracode: Integrated AppSec platform focused on policy enforcement and governance for large organizations.
- Sonatype Lifecycle: Automated policy management and supply chain visibility with deep dependency tracking.
- JFrog Xray: Advanced binary and container scanning, best suited for teams already using the JFrog ecosystem.
- Checkmarx One: Unified AppSec solution with exploitable path detection and modular enterprise coverage.
- Semgrep Supply Chain: Lightweight and reachability-based SCA for small teams needing fast adoption.
- Mend.io: SCA platform combining reachability and EPSS scoring to help prioritize and fix open source risks.
- OX Security: DevSecOps-native tool with pipeline-level visibility and automated remediation across workflows.
Why Xygeni-SCA Is the Smarter Choice
Xygeni SCA security tools are built for how modern teams develop today. They don’t just flag outdated packages. Instead, they add real-time threat intelligence, smarter prioritization, and hands-free automation, making sure that security flows naturally with your development, not against it.
Here’s how Xygeni raises the bar for Software Composition Analysis tools:
Early Malware Detection
Xygeni detects malicious packages before they reach your codebase. This includes typosquatted dependencies and supply-chain threats such as dependency confusion. As a result, you prevent issues early and keep your pipeline clean.
Reachability and EPSS Scoring
Instead of overwhelming your team with irrelevant alerts, Xygeni focuses on what’s actually exploitable in your code. Consequently, you reduce noise and focus only on the vulnerabilities that matter most.
Auto Remediation in Pull Requests
Xygeni automatically suggests the safest fix or even opens a pull request for you. Therefore, your team can remediate faster without disrupting their normal workflow.
Remediation Risk and Breaking-Change Detection
Xygeni goes beyond traditional patching by analyzing how each update affects your codebase. Its remediation engine compares versions line by line to detect breaking changes, deleted methods, and API modifications before you merge.
Every suggested fix is classified by Low, Medium, or High risk, showing you the safest path forward. This way, you can decide confidently which patches to apply — balancing security, stability, and development speed.
Know Before You Patch
Before committing to any update, Xygeni explains exactly what each patch does. You’ll see which CVEs it fixes, whether it introduces new risks, and if it could affect compilation. This transparency helps you act with confidence and avoid unnecessary rework.
Understand Code-Level Impact
Xygeni highlights deleted or modified methods, affected files, and possible build errors before you merge. As a result, you avoid compilation failures and keep even critical paths stable.
CI/CD-Native by Design
Xygeni fits into your existing workflows with zero friction. It works with GitHub Actions, GitLab, Jenkins, Bitbucket, and others. Above all, it integrates easily without slowing anything down.
SBOM and License Guardrails
Xygeni generates SPDX or CycloneDX SBOMs automatically and applies license compliance rules in real time. Because of this, you stay audit-ready and compliant throughout the development lifecycle.
All in all, Xygeni SCA security tools help you fix what matters, avoid what breaks, and ship secure code with confidence. You don’t just scan for problems, you solve them intelligently.
Final Thoughts
Why the Right Software Composition Analysis Tool Matters for Open Source Security
Open source is everywhere, it powers nearly every modern application. But with that speed and flexibility come risks: hidden vulnerabilities, license violations, and even supply chain attacks. That’s why picking the right Software Composition Analysis (SCA) tool isn’t optional anymore. It’s essential.
Still, not all SCA security tools are built to meet the demands of real-world development. Some flood teams with false positives. Others miss the real threats, like malware hidden in packages, exploitable flaws, or vulnerabilities that actually run in your code. As a result, security and engineering teams end up wasting time on noise, while dangerous issues make it to production.
This is where Xygeni-SCA stands out.
It goes beyond basic scans and focuses on what truly matters: prioritizing reachable, exploitable vulnerabilities, blocking malicious packages, and helping you fix issues fas, without slowing your team down. With smart automation and deep CI/CD integration, it supports secure development without getting in the way.
In short, if you want open source security that’s accurate, developer-first, and ready for today’s software supply chain threats, Xygeni-SCA is the smarter choice.
Disclaimer: Pricing is indicative and based on publicly available information. For accurate and up-to-date quotes, please contact the vendor directly.