Security can’t wait until the final testing phase. If you want to build secure, resilient apps, you need to think about security from day one. That’s where understanding what are the phases of the Software Development Life Cycle (SDLC) becomes critical. By embedding SDLC security into each phase, from planning and design to deployment and maintenance, you create a Secure Software Development Life Cycle (SSDLC) that reduces risk, cuts costs, and keeps your software ready for real-world threats. In this guide, we’ll walk through each phase of the SDLC and show you how to make security a built-in feature, not an afterthought.
Understanding SDLC and the Secure Software Development Life Cycle
The Software Development Life Cycle (SDLC) provides a structured approach for designing, building, testing, and deploying software. However, traditional SDLC often treats security as an afterthought. This is where the secure software development life cycle (SSDLC) comes in, integrating security into every phase to ensure your software is resilient against modern cyber threats.
SDLC Security: The Foundation of a Secure Software Development Life Cycle
According to the National Institute of Standards and Technology (NIST), security should be integrated across all phases of the Software Development Life Cycle, from planning to maintenance. By embedding SDLC security practices into the development process, teams can address vulnerabilities early, minimize risks, and avoid costly fixes later.
What are the Phases of Software Development Life Cycle and Their Security Requirements?
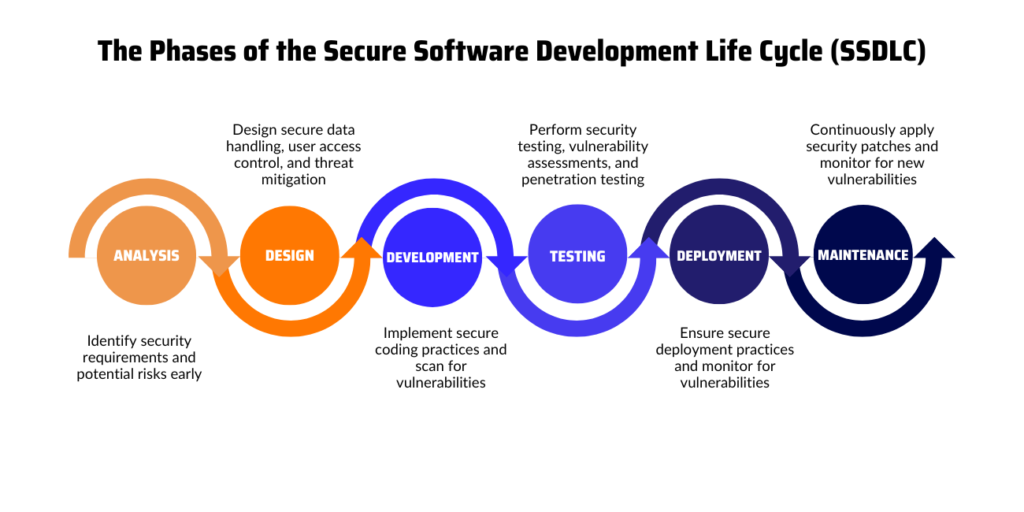
Every phase of the Software Development Life Cycle (SDLC) has unique security challenges. Knowing what are the phases of software development life cycle helps you integrate SDLC security into every step. By adopting a Secure Software Development Life Cycle (SSDLC), you can catch vulnerabilities early, reduce risks, and build better software.
Here’s how security fits into each phase of the software development life cycle and how Xygeni helps make it seamless:
1. Planning and Requirement Analysis
This phase forms the foundation of the project. Teams define the project’s scope, gather requirements, and assess potential risks. Understanding what are the phases of the software development life cycle starts with strong planning, and adding SDLC security at this stage prevents vulnerabilities later.
Security Focus: Threat modeling and gathering security requirements are key here. Tools like Xygeni’s Application Security Posture Management (ASPM) provide full visibility into potential risks by automating the discovery of software assets. At the same time, Xygeni’s Software Supply Chain Security (SSCS) ensures any third-party or open-source components meet security standards, reducing supply chain risks before development even starts.
2. Design
In the design phase, teams map out the system’s architecture and decide how the software will function. Critical security decisions, such as protecting sensitive data, controlling user access, and mitigating threats, take center stage.
Security Focus: Secure architecture design and updating threat models. Xygeni’s Infrastructure as Code (IaC) Security scans cloud and system architectures for misconfigurations, ensuring security flaws don’t get embedded into your design. Additionally, Xygeni’s Secrets Security helps safeguard sensitive information like API keys, credentials, and passwords throughout this stage.
3. Development
This is where the actual coding happens, making it one of the most vulnerable phases for introducing security risks. Poorly written code or insecure components can create significant issues if not addressed early.
Security Focus: Secure coding practices, static application security testing (SAST), and software composition analysis (SCA). Xygeni’s ASPM actively monitors the code during development, flagging risks in real-time so developers can fix issues as they arise. Auto-Remediation, part of Xygeni’s Open Source Security suite, automatically resolves vulnerabilities in open-source components before they reach production. Meanwhile, Real-Time Malware Detection protects dependencies and third-party libraries, while Secrets Security ensures no sensitive data accidentally makes its way into the codebase.
4. Testing
In the testing phase of the software development life cycle, teams validate functionality and check for vulnerabilities. Thorough testing ensures no security risks make it to production.
Security Focus: Dynamic application security testing (DAST), penetration testing, and vulnerability scans. During this phase, Xygeni’s ASPM uses exploitability metrics to highlight the most critical risks, helping teams prioritize fixes efficiently. Real-Time Malware Detection continues to scan for threats in third-party components, while SSCS anomaly detection monitors for unusual behavior that could signal hidden vulnerabilities.
5. Deployment
This phase releases the software into the production environment. Teams must ensure the deployment process is secure to avoid introducing new risks during the transition.
Security Focus: Secure configurations, post-deployment vulnerability scans, and intrusion prevention systems. In addition, Xygeni’s Open Source Security suite ensures that third-party components remain secure even after deployment. Furthermore, Auto-Remediation fixes vulnerabilities in live environments without manual intervention. Meanwhile, SSCS continuously scans for new threats, keeping your production environment secure.
6. Maintenance
The job doesn’t end after deployment. Ongoing maintenance addresses new vulnerabilities, applies patches, and ensures the system stays secure against evolving threats.
Security Focus: Vulnerability management, patch management, and continuous monitoring. Xygeni’s ASPM provides real-time security monitoring to quickly detect and resolve emerging issues. Coupled with Real-Time Malware Detection, Xygeni helps protect your software against new risks in third-party components, ensuring long-term security.
The Benefits of a Secure Software Development Life Cycle
Adopting a Secure Software Development Life Cycle (SSDLC) isn’t just about making your software secure—it’s about working smarter and building better applications. By integrating SDLC security practices into every phase of development, teams gain a range of benefits:
- Reduce Vulnerabilities: Catching security issues early helps prevent major risks from reaching production.
- Lower Costs: Fixing vulnerabilities during development is far cheaper than patching them post-release.
- Improve Security Posture: SSDLC builds resilience into your software, preparing it for evolving threats.
- Achieve Compliance: Meet security standards like GDPR, HIPAA, and PCI DSS without last-minute scrambling.
How the Secure Software Development Life Cycle (SSDLC) Transforms Software Security
Understanding what are the phases of the software development life cycle is the first step to creating secure and reliable software. When you adopt a Secure Software Development Life Cycle (SSDLC), you make security a core part of your development process. From planning and design to maintenance, adding SDLC security into every phase helps your team catch vulnerabilities early, lower costs, and stay ahead of evolving threats.
Xygeni makes SSDLC adoption straightforward. Application Security Posture Management (ASPM) gives you real-time insights into risks so your team can fix issues quickly. Software Supply Chain Security (SSCS) keeps third-party and open-source components safe. With Auto-Remediation, you resolve vulnerabilities instantly and keep your focus on building great software.
Take the Next Step
By focusing on SDLC security and shifting to an SSDLC approach, your team builds software that not only works but also stays secure against modern threats. Embedding security at every stage makes compliance easier and reduces expensive fixes later. Ready to level up your process? See how Xygeni can help secure every phase of your software development life cycle and make development safer and more efficient.








