The fast-moving space of cybersecurity has made What is Software Composition Analysis (SCA) a crucial tech term. SCA is vital because it helps maintain security, licensing compliance, and the integrity of software applications. It automates the detection and remediation of open-source components with known vulnerabilities. But how did Software Composition Analysis tools come into being, and why has it become indispensable?
The Origins of Software Composition Analysis
What is Software Composition Analysis, and Why Was It Created?
What is Software Composition Analysis, and how did it come about? SCA emerged from the need to manage the increased use of open-source software (OSS) and the prevalence of third-party libraries in modern application development. As companies sought to speed up development cycles and reduce costs, they turned more quickly to these reusable components.
However, this shift introduced new problems, such as dealing with security vulnerabilities and licensing issues related to open source.
Developers had to maintain a manual inventory of these components before SCA was institutionalized. This was an error-prone and time-consuming process. The desire for a more systematic approach led to the development of tools and methodologies that could automatically scan, identify, and assess the risks of these components. Today, this approach is known as Software Composition Analysis.
Software Composition Analysis: The official definition
There are a few definitions out there from authoritative sources. All of these sources recognize the value of Software Composition Analysis in today’s cybersecurity world.
The Linux Foundation in its Open Guide to Evaluating SCA Tools, describes SCA as “a critical component of modern software development practices, aimed at identifying open-source components within a codebase, assessing their security vulnerabilities, and ensuring compliance with licensing obligations.” This definition highlights the comprehensive role that SCA plays in managing both security and legal risks in software development.
OWASP (Open Web Application Security Project), a non-profit organization dedicated to improving software security, describes SCA as a the process of identifying potential areas of risk from the use of third-party and open-source software and hardware components.”
NIST (National Institute of Standards and Technology), in its security guidelines, also emphasizes the importance of SCA in identifying and managing the risks associated with using third-party and open-source components within software applications. NIST’s guidelines are often used as a benchmark for cybersecurity practices across industries.
Defining Software Composition Analysis in Practical Terms
Now that we have covered how Software Composition Analysis came about and how industry leaders define it, let’s break it down in simpler terms and understand for real what is software composition analysis.
Software Composition Analysis is a security practice that helps organizations identify, assess, and mitigate risks related to open-source and third-party software components. It automates the process of scanning for vulnerabilities, checking for licensing issues, and securing the software supply chain.
Unlike traditional security measures that focus on custom code vulnerabilities, Software Composition Analysis looks beyond internally developed software. It ensures that every external dependency used in an application is secure, legally compliant, and free from known threats.
As organizations continue to rely on open-source software, Software Composition Analysis has become a fundamental component of modern DevSecOps strategies. It enables developers and security teams to maintain secure applications without slowing down the development process.
By integrating Software Composition Analysis tools into CI/CD pipelines, teams can automate security checks, detect vulnerabilities early, and avoid last-minute surprises before deployment. In an era where supply chain attacks are on the rise, having a robust Software Composition Analysis strategy is no longer optional—it is essential.
The Benefits of Software Composition Analysis
Detect and Solve Weaknesses: Software Composition Analysis tools continuously screen codebases for known vulnerabilities. They convey significant insights to enable engineers to address issues before they can be exploited.
Maintains License Compliance: Software Composition Analysis oversees the management of licenses for third-party components. This helps avoid legal hazards and ensures compliance with each component’s usage terms.
Advance Security Posture: When integrated into the SDLC, SCA can help reduce your attack surface. It also creates more challenging exposure targets for adversaries.
Why SCA is Essential in Cybersecurity
Today, Software Composition Analysis is more critical than ever. Software supply chain attacks have evolved, making third-party vulnerabilities just as dangerous as direct code exploits.
Attackers increasingly target widely used open-source components. These dependencies often serve as a weak link, providing an easy entry point into an otherwise secure application.
Without SCA, organizations leave their software exposed to silent but severe security risks. Securing third-party dependencies is no longer optional—it’s essential.
SCA in the AppSec Landscape
Software Composition Analysis (SCA) is essential for application security. It strengthens existing security testing practices by addressing risks in third-party components.
Static Application Security Testing (SAST) identifies vulnerabilities in custom-written code. However, it does not analyze external dependencies. SCA fills this gap by scanning open-source and third-party libraries, detecting known and hidden vulnerabilities.
For example, in our blog post, “SCA vs SAST: Key Differences in Application Security,” we explain how these methods work together. SCA focuses on external code, such as open-source dependencies, while SAST examines internally developed code. Also, you can take a look at our SafeDev Talk edition on SCA or SAST – How They Complement Each Other for Stronger Security?
Together, SCA and SAST create a comprehensive security strategy. SAST helps prevent issues introduced by developers, while SCA secures applications against external threats.
How Software Composition Analysis Tools Works
To build secure software, teams need to understand what Software Composition Analysis (SCA) is and how it works. Modern applications depend on open-source and third-party components, making it essential to find vulnerabilities, manage risks, and ensure compliance.
Software Composition Analysis tools automate this process by helping teams detect, assess, and fix security threats in their software dependencies. Let’s go through how they work.
1. Discovering Components
The first step in Software Composition Analysis is finding all software dependencies. Modern applications use many open-source libraries, and some bring in nested dependencies that developers don’t always track.
SCA tools scan repositories, package managers, and build files to detect all direct and transitive (indirect) dependencies. After scanning, they create a Software Bill of Materials (SBOM)—a detailed list of components, versions, and sources.
With this visibility, teams know exactly what’s in their codebase before checking for security risks.
2. Detecting Vulnerabilities
Once the Software Composition Analysis tool maps dependencies, the next step is to find security risks. SCA tools check components against well-known vulnerability databases, such as:
- National Vulnerability Database (NVD) – A widely used government database.
- Common Vulnerabilities and Exposures (CVE) – A global list of known security flaws.
- GitHub Security Advisories – Reports from security researchers and package maintainers.
- Other security sources – Some tools also include private threat intelligence.
By matching component versions to known vulnerabilities, SCA tools alert teams early so they can fix security issues before releasing software.
3. Ensuring License Compliance
Many open-source components come with legal requirements. Some allow free use, while others restrict modification, redistribution, or commercial use.
Software Composition Analysis tools check each component’s license and flag issues, such as:
- Incompatible license terms – Some licenses (e.g., GPL) require proprietary software to become open-source.
- Attribution requirements – Some licenses require proper credit in documentation.
- Prohibited usage – Certain licenses block commercial or enterprise applications.
By checking license compliance early, teams avoid legal risks and conflicts with company policies.
4. Prioritizing Risks
Not every security issue requires immediate attention. Some vulnerabilities are critical, while others pose less risk. SCA tools rank security threats based on:
- Severity scores (CVSS, EPSS) – Measures how dangerous a vulnerability is.
- Exploitability – Shows if attackers are using the issue in real-world attacks.
- Business impact – Checks if the vulnerability affects critical software functions.
Some advanced Software Composition Analysis tools also use reachability analysis, which determines if the vulnerable code actually runs in the application. This reduces false positives and helps teams focus on real threats.
5. Continuous Monitoring
New vulnerabilities appear every day. A package that was safe yesterday may become a security risk tomorrow. One-time scans aren’t enough to keep software secure.
Software Composition Analysis tools monitor dependencies continuously by integrating into CI/CD pipelines and development workflows. They:
- Detect new vulnerabilities in existing components.
- Send real-time alerts when new security threats emerge.
- Automate security checks throughout the development process.
By monitoring dependencies at all times, teams fix vulnerabilities as soon as they appear, instead of waiting for periodic reviews.
6. Fixing Vulnerabilities with Remediation Guidance
Finding security issues is only half the job—teams also need a clear plan to fix them. SCA tools help developers resolve issues quickly by suggesting:
- Safer versions of dependencies – Upgrading to a patched release.
- Alternative libraries – Replacing unmaintained or risky components.
- Security patches – Applying available fixes when upgrades aren’t possible.
Some advanced Software Composition Analysis tools even automate remediation by creating pull requests with fixes, reducing manual work and speeding up patching.
Xygeni’s Advanced SCA Solution
While traditional Software Composition Analysis (SCA) tools focus on basic vulnerability detection, Xygeni takes a more advanced approach. It integrates real-time threat intelligence, automated remediation, and reachability analysis to improve accuracy, reduce false positives, and enhance overall security posture.
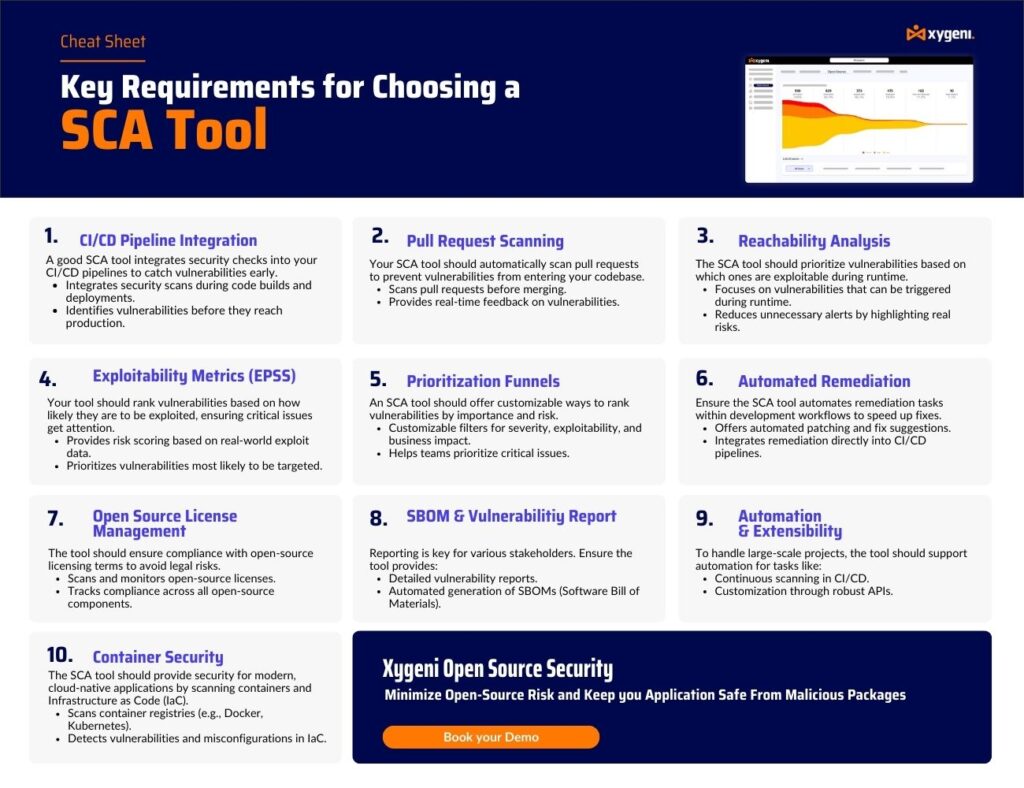
Why Choose Xygeni’s SCA?
- Real-Time Threat Intelligence – Instantly detects vulnerabilities instead of relying on periodic scans.
- Reachability Analysis – Determines if a vulnerability is actually used in execution, reducing false alarms.
- Automated Remediation – Generates pull requests with patches for immediate fixes.
- CI/CD Pipeline Integration – Embeds security checks seamlessly into DevOps workflows without disrupting development.
- License Risk Management – Analyzes and enforces compliance with open-source licensing requirements.
- Early Malware Detection – Blocks malicious open-source packages before they are installed, preventing supply chain attacks.
How Xygeni Enhances Each SCA Stage
- Better Component Discovery – Performs real-time scans across multiple public registries to provide full visibility into software dependencies.
- More Accurate Vulnerability Detection – Cross-references vulnerabilities from multiple databases to eliminate security gaps.
- Smarter Risk Prioritization – Uses exploitability metrics to help security teams focus on vulnerabilities that pose real threats.
- Stronger Compliance Controls – Automates license checks, ensuring compliance with company policies and regulatory standards.
- Proactive Remediation – Provides automated suggestions and generates patching pull requests to accelerate vulnerability fixes.
With Xygeni’s enhanced Software Composition Analysis, organizations gain continuous security monitoring, precise risk management, and efficient remediation workflows. This ensures open-source dependencies remain secure, compliant, and optimized for development speed.
Strengthening Security with Software Composition Analysis
Modern software development relies on open-source components more than ever. While these components accelerate development and reduce costs, they also introduce security vulnerabilities and compliance risks if not properly managed.
Software Composition Analysis (SCA) provides a proactive solution by helping teams:
- Identify all software components and dependencies to ensure full visibility.
- Detect vulnerabilities early using real-time threat intelligence.
- Ensure compliance with open-source license requirements.
- Prioritize the most critical threats instead of wasting time on false positives.
- Monitor dependencies continuously to catch new security risks as they emerge.
- Fix security issues efficiently through guided remediation or automated fixes.
By integrating SCA into development workflows, organizations can stay ahead of threats, maintain compliance, and secure their software without slowing down development.
Looking for an advanced SCA solution? Request a free trial today to see how Xygeni can help secure your software.
Frequently Asked Questions (FAQs)
1. Which applications need an SCA scan?
Any software that uses open-source or third-party components should run an SCA scan. This includes:
- Web and mobile applications – Many modern frameworks, such as React, Django, and Spring Boot, rely on open-source libraries.
- Enterprise software and SaaS platforms – These applications often integrate external dependencies to extend functionality.
- CI/CD pipelines in DevOps workflows – Continuous integration environments frequently introduce new dependencies that need security checks.
- Cloud-native and containerized applications – Microservices architectures depend on open-source components, making SCA critical.
- APIs, backend services, and IoT devices – These systems use third-party packages, which must be monitored for vulnerabilities.
Since open-source libraries evolve constantly, scanning regularly ensures that security risks and compliance issues are addressed before they become a problem.
2. What is SCA scanning?
SCA scanning automates security checks for open-source dependencies. It plays a vital role in securing software by performing the following tasks:
- Identifying all software components to ensure full visibility.
- Detecting known vulnerabilities by matching components against security databases.
- Checking for license compliance to prevent legal and policy violations.
- Prioritizing security risks based on severity, exploitability, and business impact.
- Providing remediation steps or even automating fixes to accelerate patching.
By integrating SCA scanning into CI/CD workflows, organizations can detect and fix security risks early, before they impact production.
3. How is Software Composition Analysis (SCA) used in DevOps?
In a DevOps environment, speed and security must go hand in hand. SCA integrates directly into CI/CD pipelines, allowing teams to:
- Automate security checks before deploying new code.
- Prevent vulnerable dependencies from being introduced into the codebase.
- Ensure open-source license compliance without manual tracking.
- Provide real-time remediation suggestions so developers can quickly apply fixes.
By embedding SCA early in the DevOps process, teams can shift security left, catching risks before they reach production.
4. How often should I run an SCA scan?
Since new vulnerabilities appear daily, scanning once is not enough. The best approach is continuous monitoring, where SCA scans run automatically within CI/CD workflows. This ensures teams receive instant alerts when new vulnerabilities affect existing dependencies, allowing for fast remediation.
5. Can SCA tools fix vulnerabilities automatically?
Yes, some advanced SCA tools automate remediation by generating pull requests that update dependencies or apply security patches. This reduces manual effort, allowing developers to fix vulnerabilities faster without disrupting workflows.