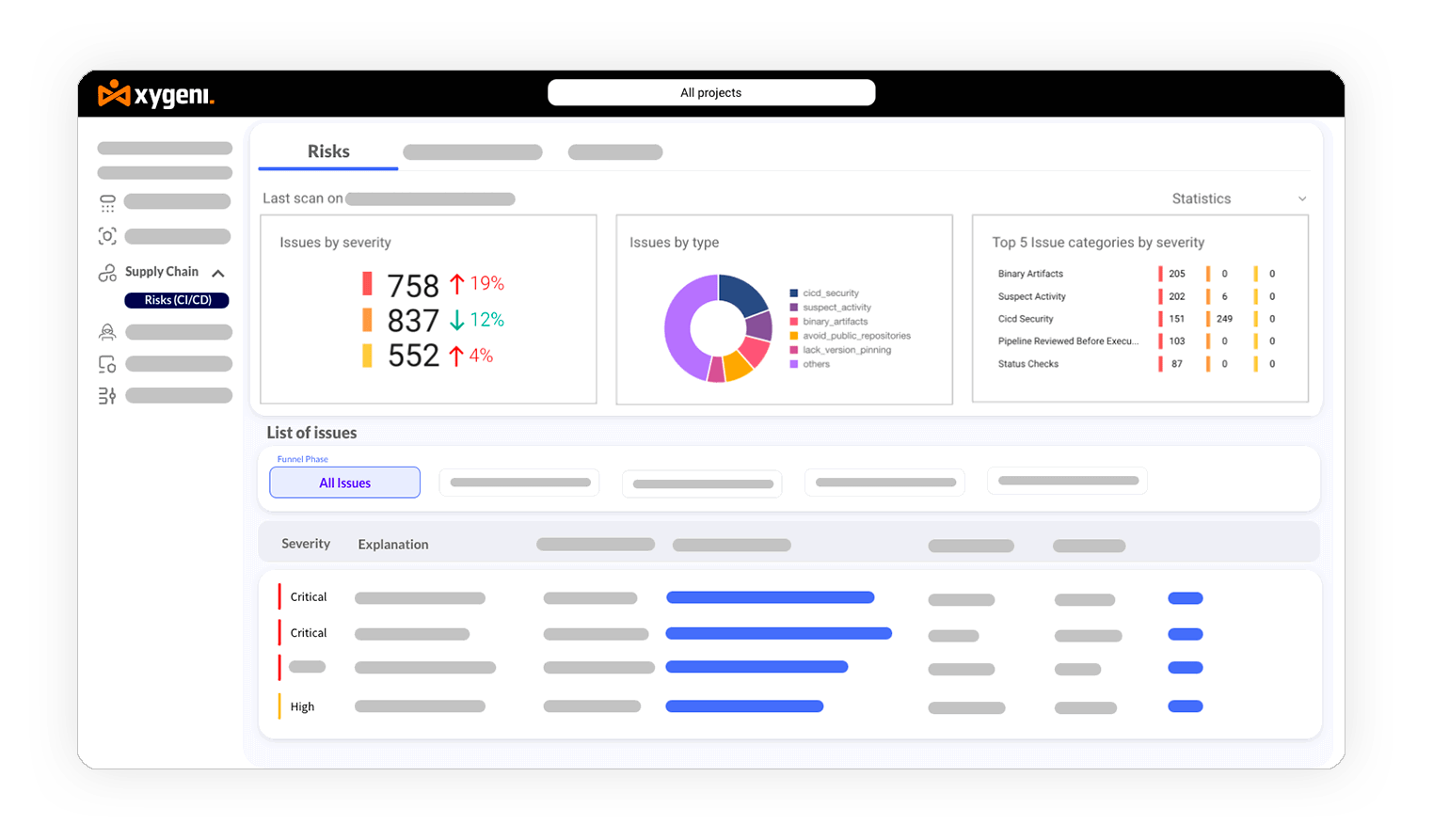
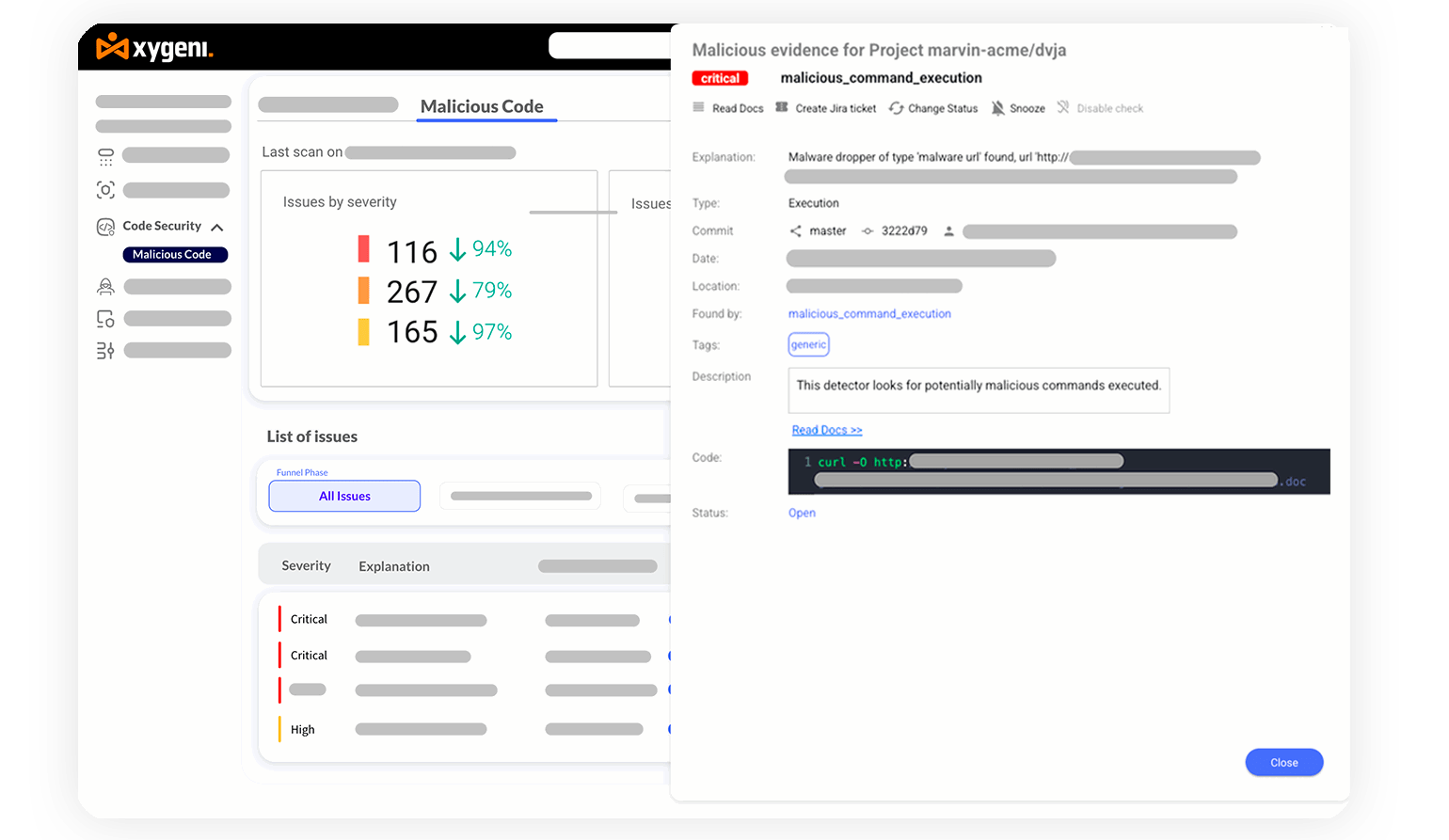
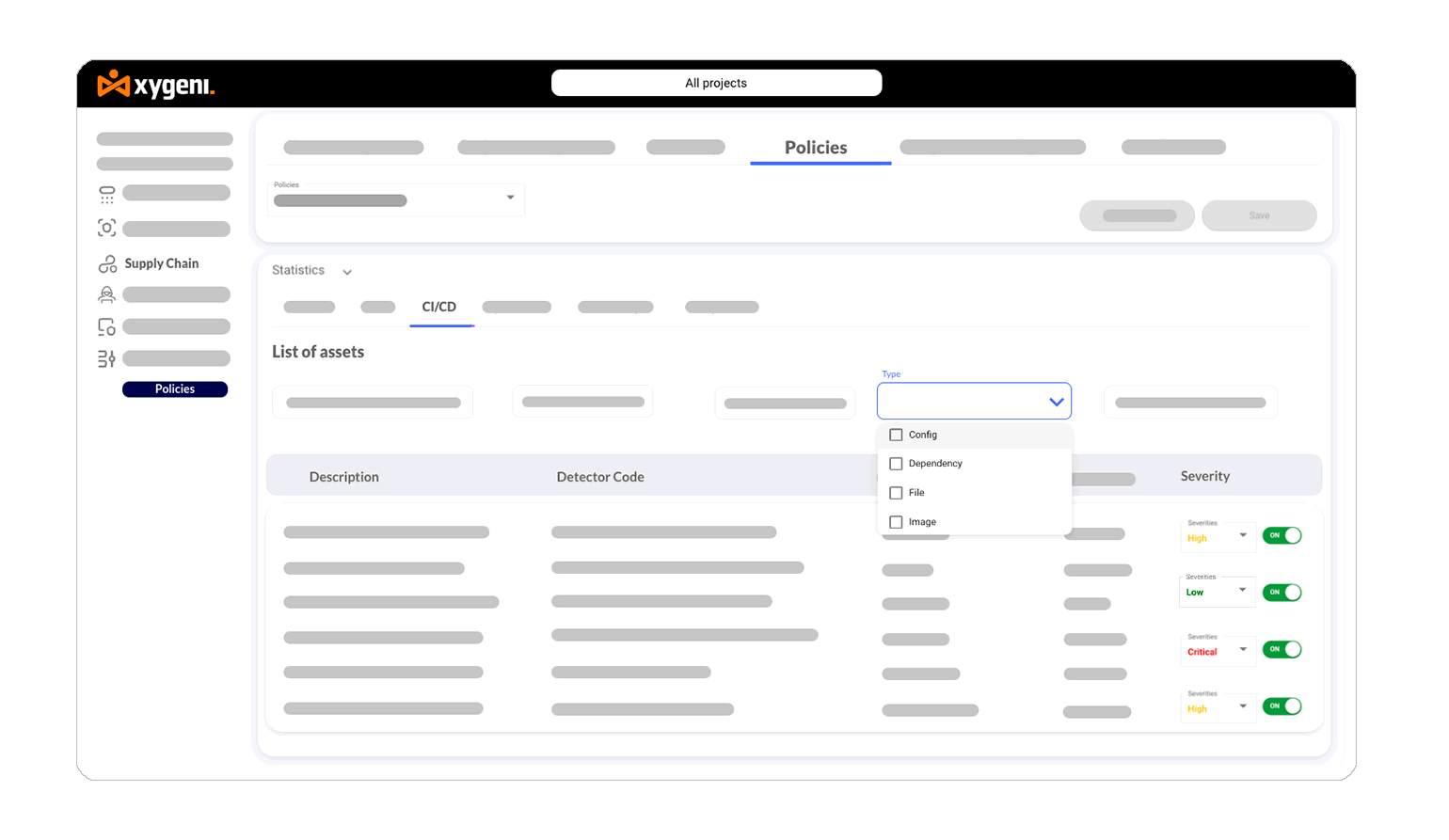
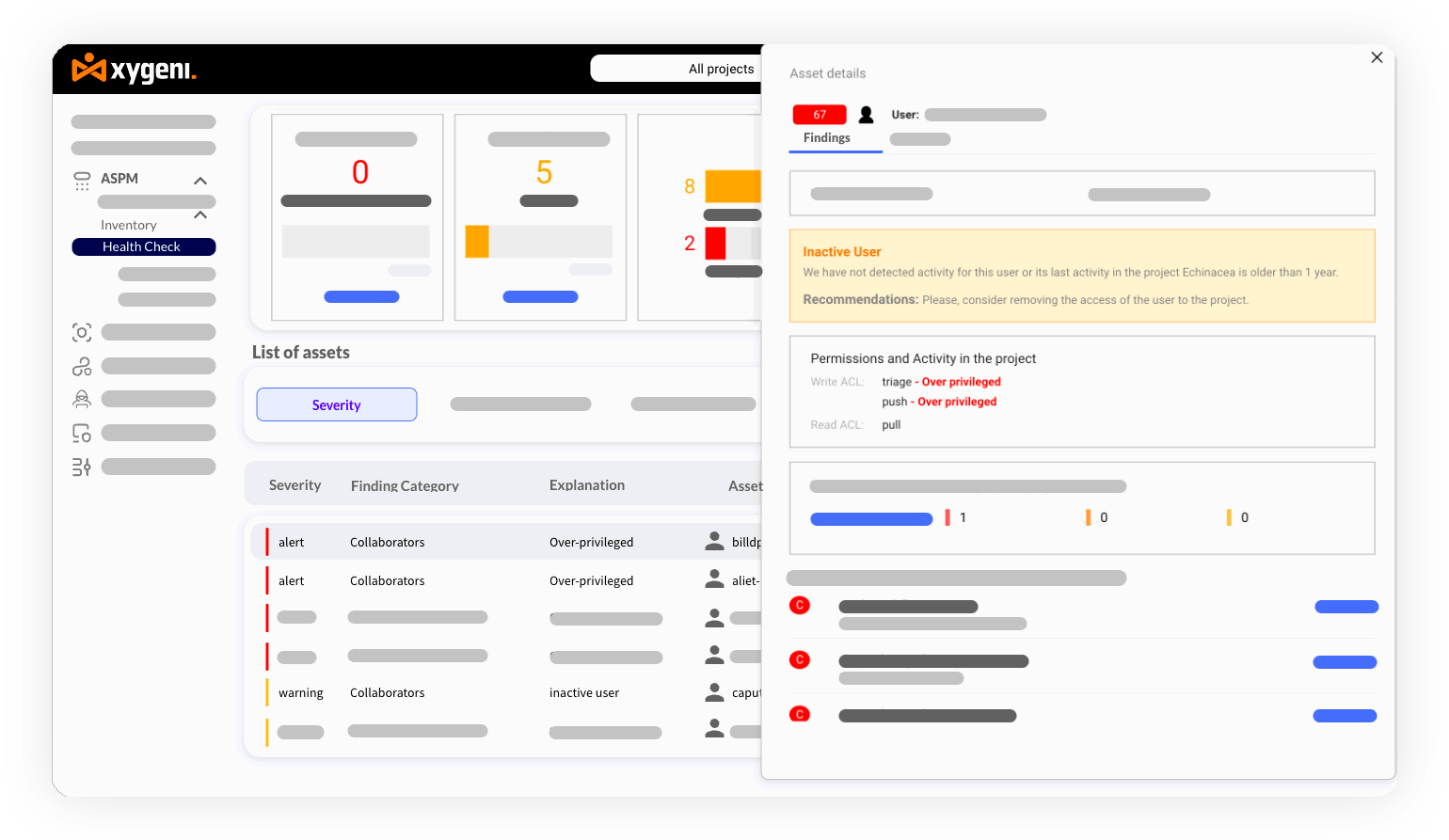
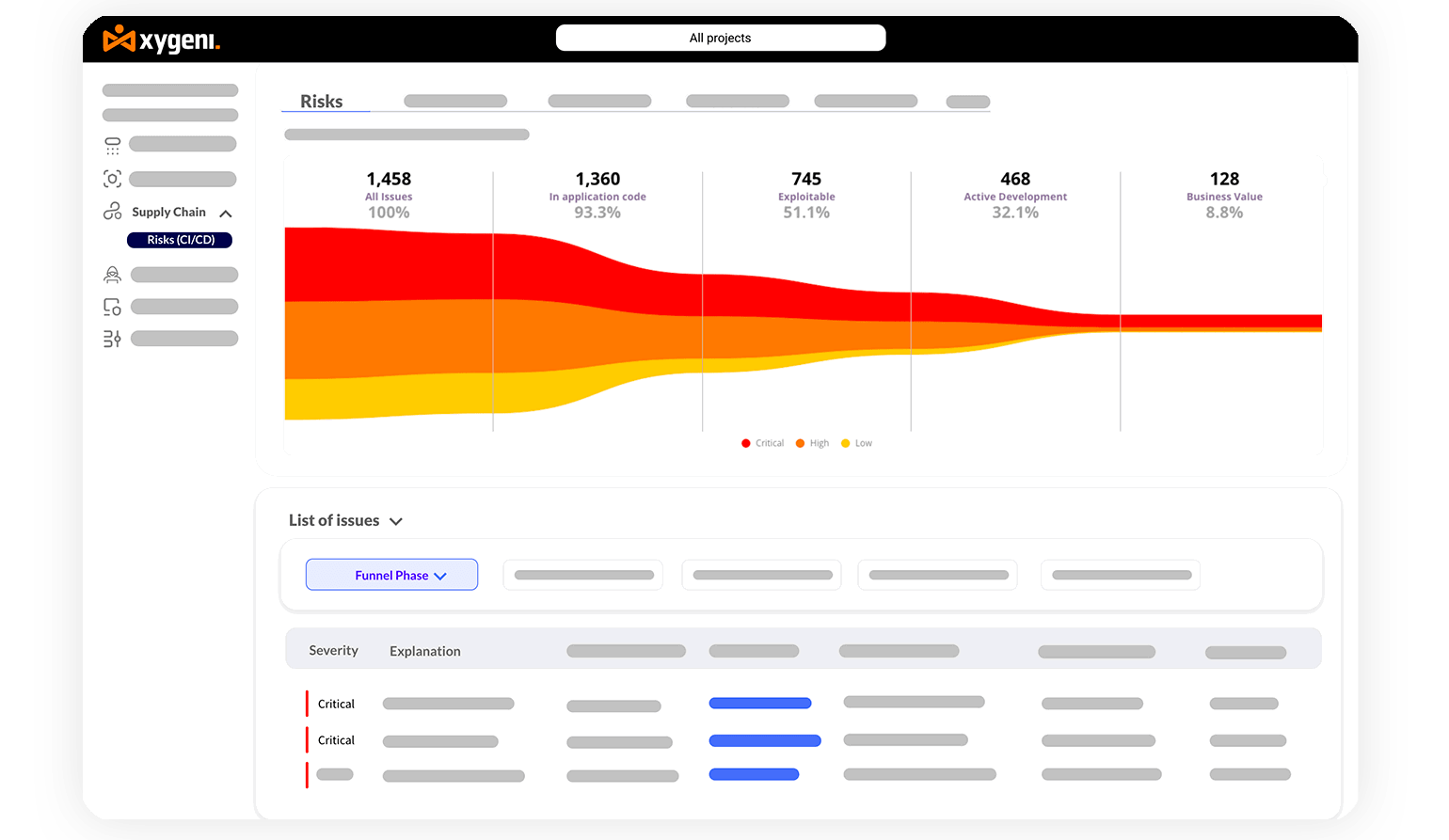
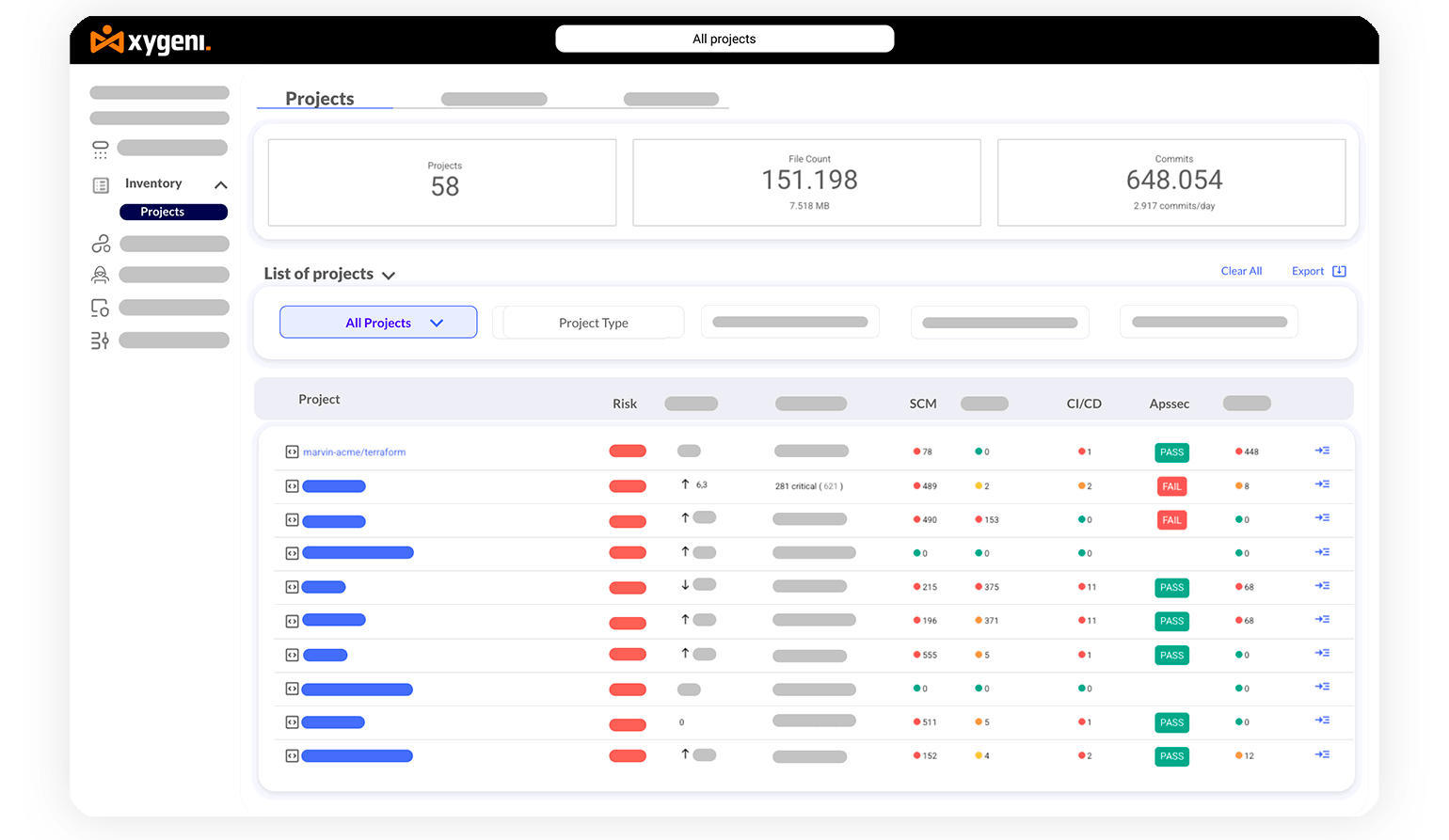
Block supply chain attacks by maintaining continuous oversight of DevOps workflows and pipeline configurations.
Safeguard CI/CD pipelines from OWASP Top 10 threats, ensuring robust protection against malicious commands and vulnerabilities.
Secure your CI/CD infrastructure by enforcing MFA, branch protections, and other critical safeguards to eliminate misconfigurations.