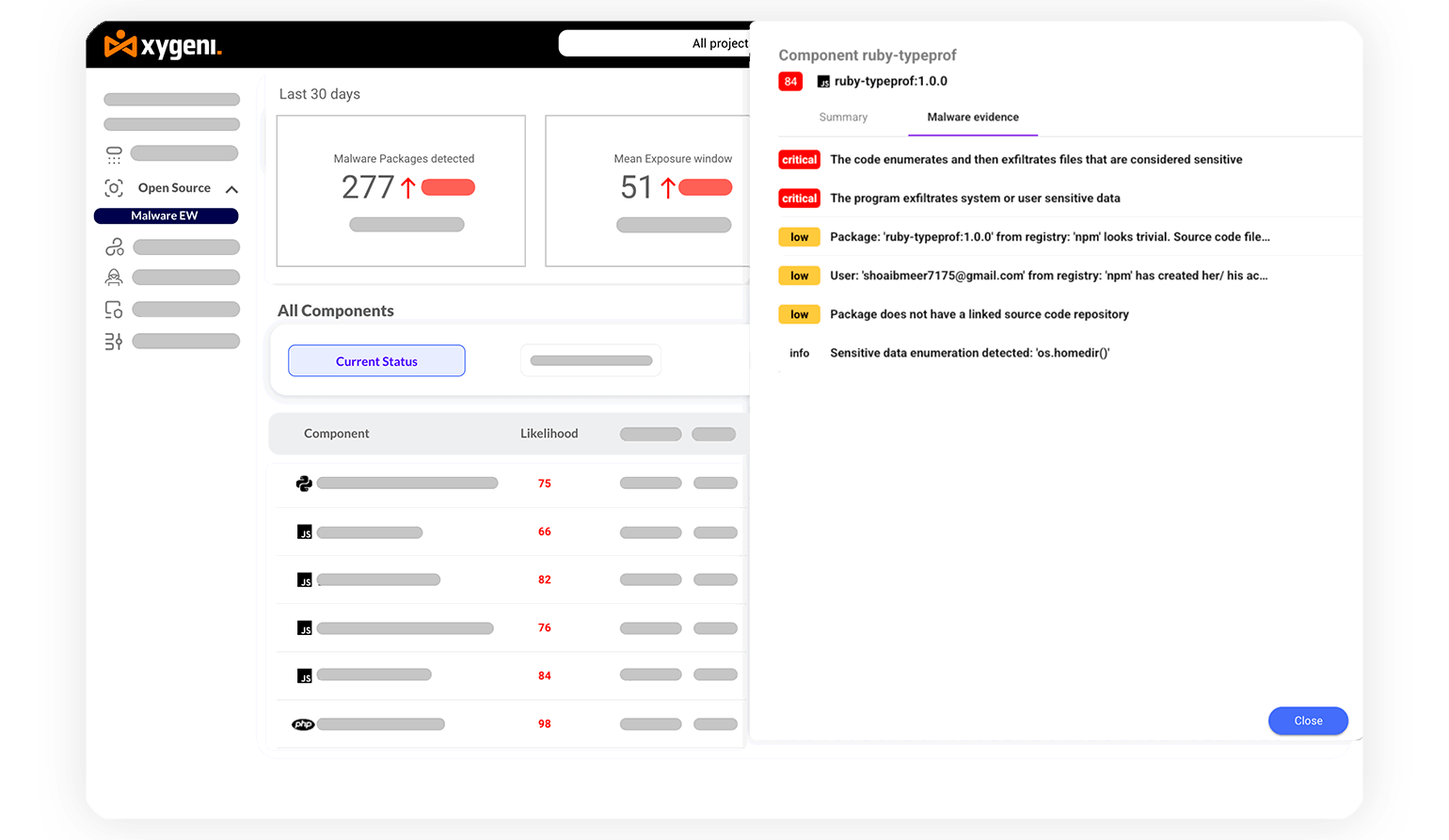
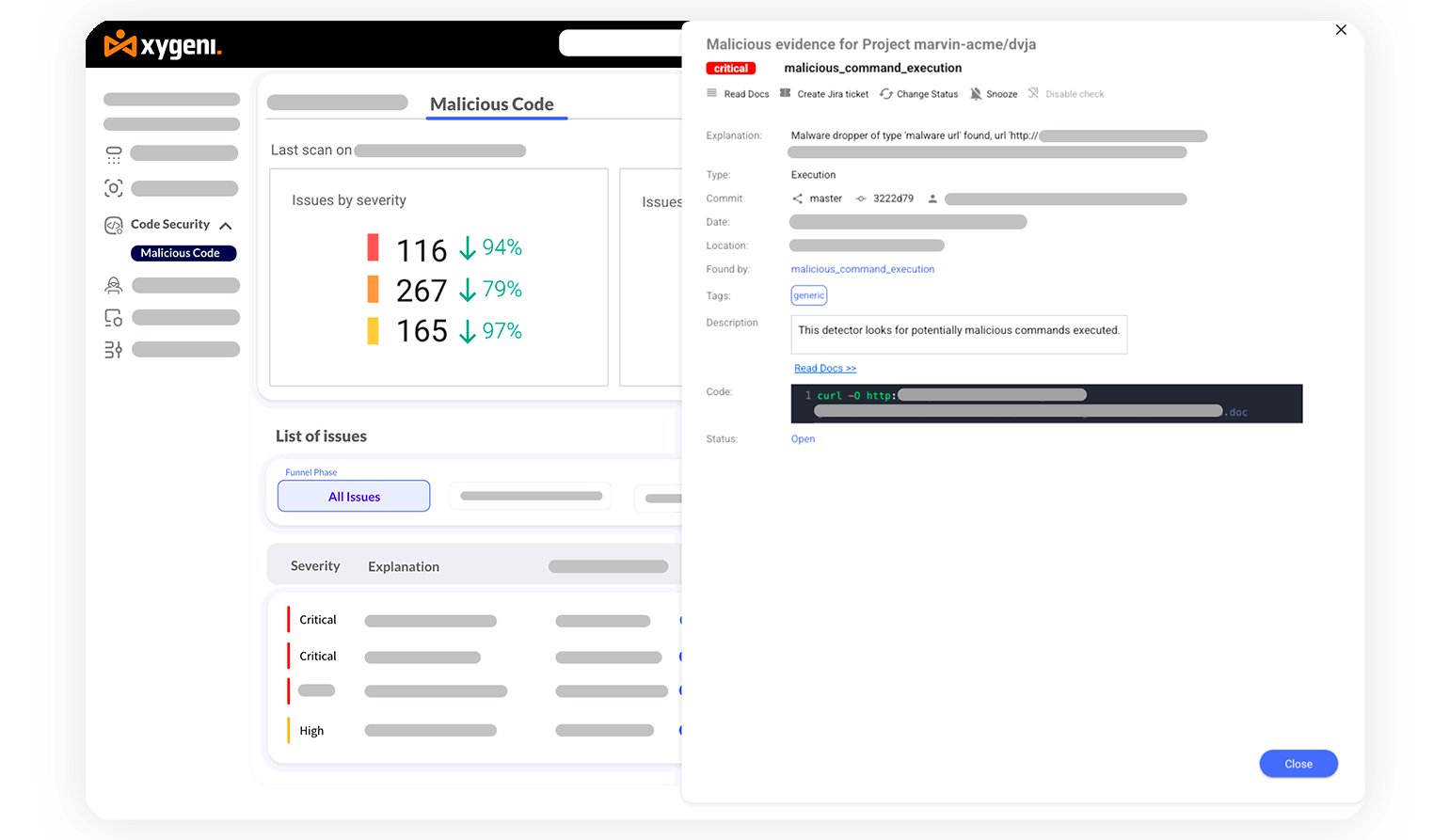
Identify backdoors, trojans, and hidden threats within your application source code, ensuring your codebase remains secure and trustworthy.
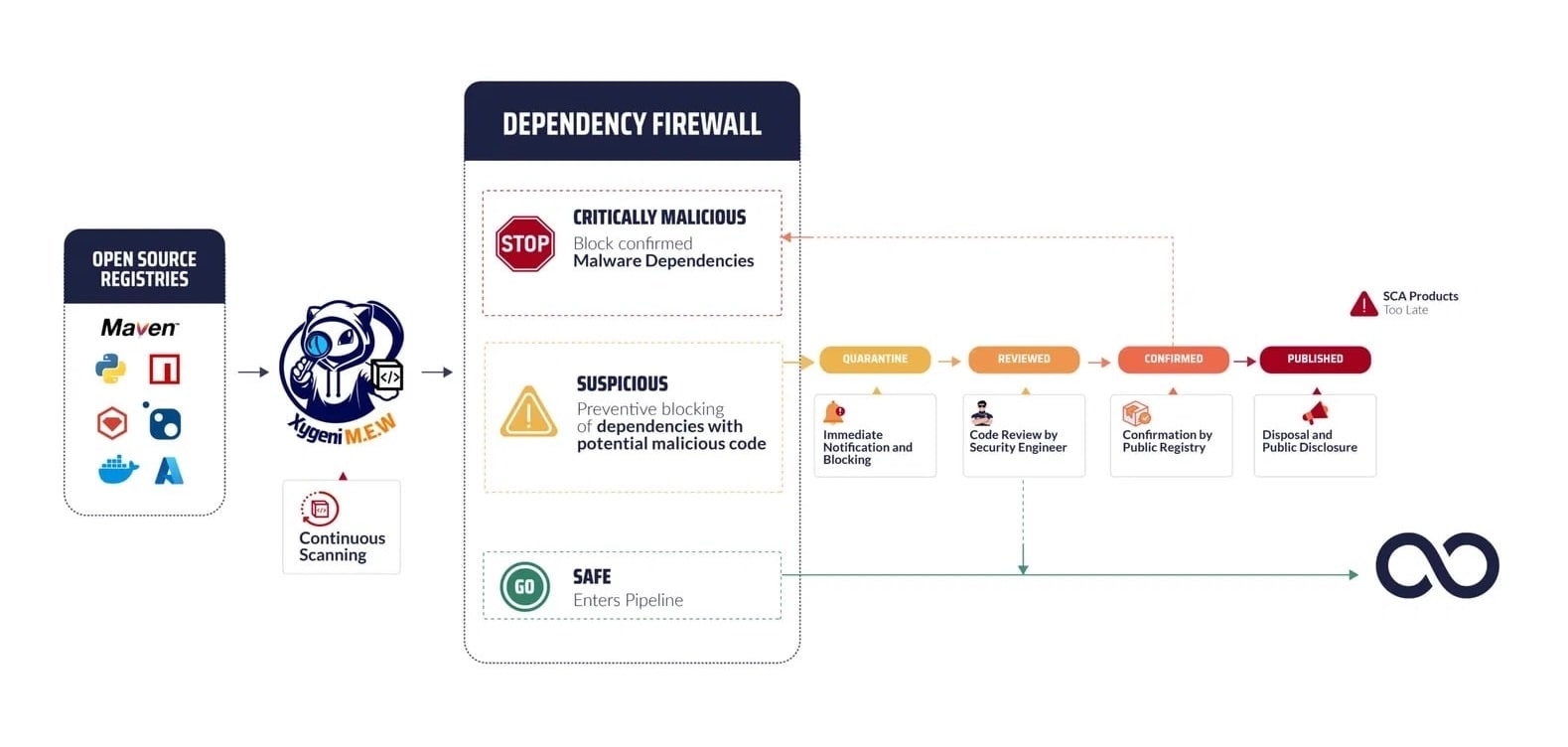
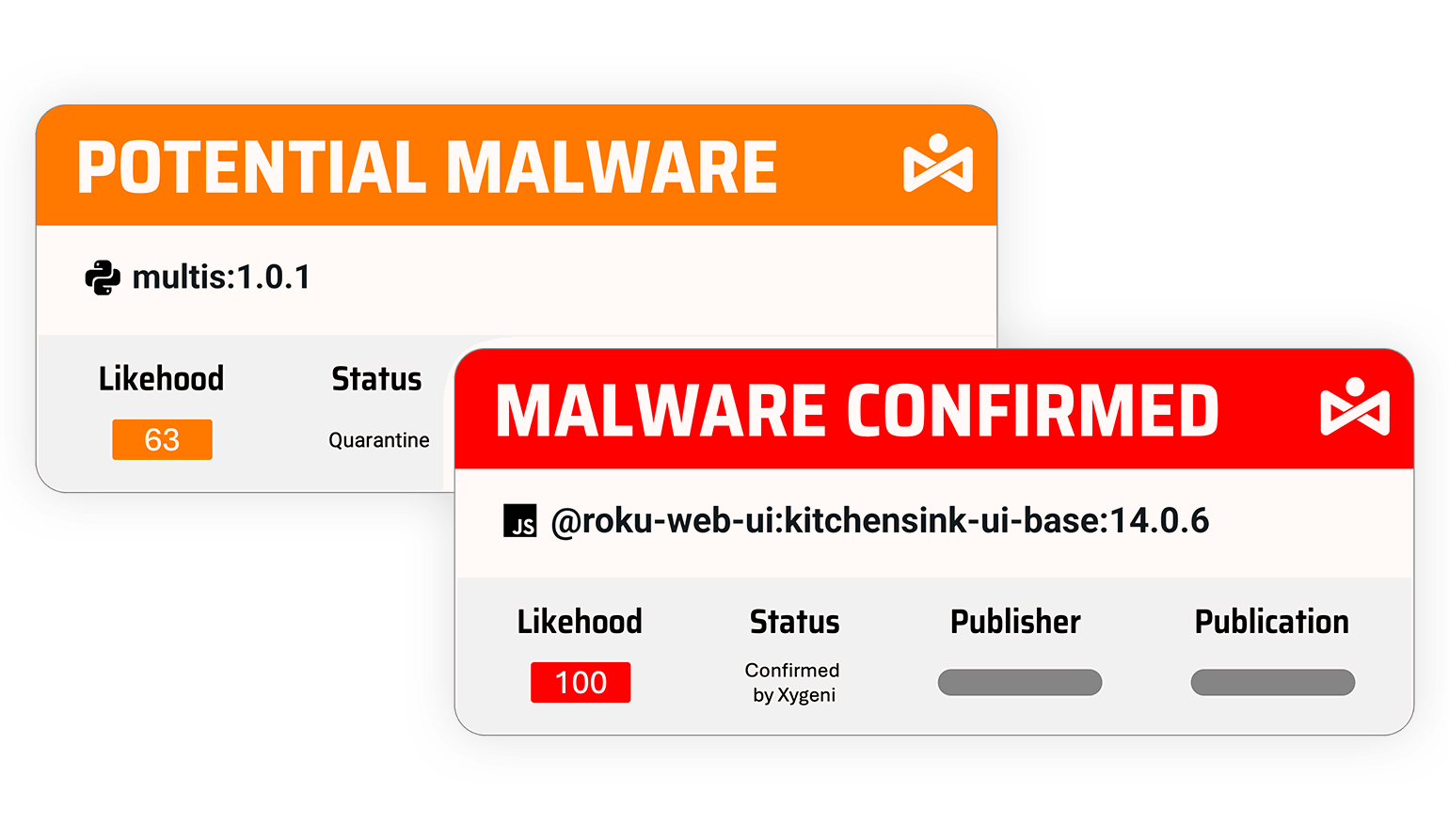
Detect and prevent malicious packages in open-source components, safeguarding your software supply chain from infiltration at the earliest stages.
Detect and block reverse shell commands, malicious providers, and malware downloads in pipelines, IaC files, and DevOps workflows, ensuring end-to-end security.