What is Threat Detection and Response (TDR) and Why Does It Matter?
As cyber threats become more sophisticated, organizations need proactive security strategies to protect their digital assets. This is where Threat Detection and Response (TDR) comes in. What is Threat Detection and Response? It is a cybersecurity process designed to identify, analyze, and respond to threats in real time. By combining threat detection with automated or manual response measures, TDR minimizes the impact of cyber attacks before they can exploit vulnerabilities.
TDR evolved from previous technologies like Intrusion Detection Systems (IDS), Security Information and Event Management (SIEM), and Endpoint Detection and Response (EDR). Companies like Cisco and Microsoft have helped develop TDR solutions, making them essential to modern cybersecurity strategies. By leveraging machine learning, behavioral analytics, and threat intelligence, TDR allows businesses to detect and respond to both known and emerging threats swiftly and effectively.
Definition:
What is Threat Detection and Response (TDR)? #
Threat Detection and Response (TDR) is a cybersecurity process designed to detect and respond to cyber threats in real-time. By continuously monitoring network traffic, endpoints, and system activities, TDR identifies suspicious behavior or potential attacks and takes immediate action to contain or neutralize these threats. TDR combines advanced detection techniques with automated or manual response measures to safeguard an organization’s digital assets.
Key Components of Threat Detection and Response #
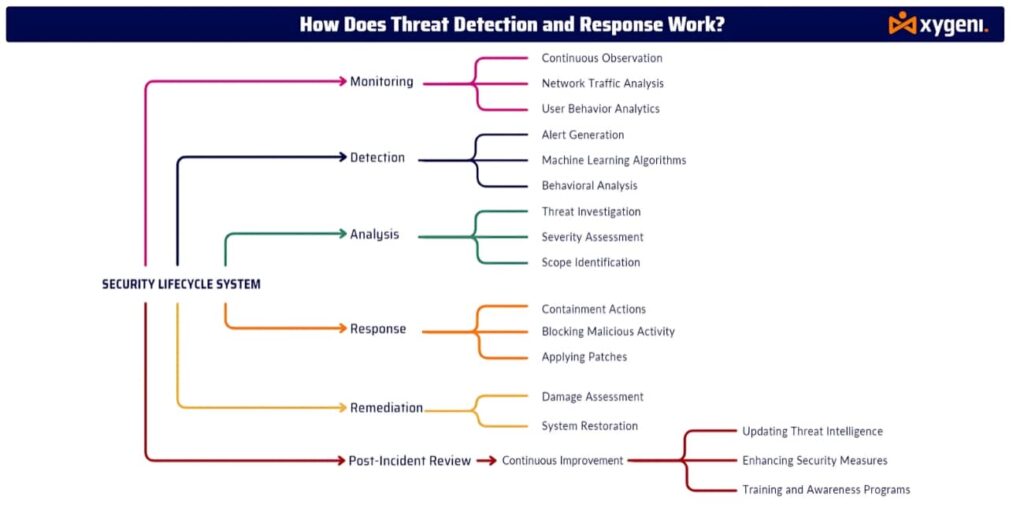
- Continuous Monitoring
TDR systems continuously monitor network traffic, endpoints, user behavior, and IT infrastructure for suspicious activities. This constant vigilance allows organizations to catch potential threats as they emerge. - Detection
TDR tools use a combination of behavioral analytics, machine learning, and threat intelligence to detect threats that may bypass traditional security measures. This includes identifying anomalies, unusual network traffic, and malware signatures. - Threat Analysis
Once the system detects a threat, security teams analyze the nature, source, and scope of the attack. They evaluate the potential impact and affected systems to determine the appropriate response. - Automated Response
TDR systems automatically respond to detected threats to minimize damage. They quickly isolate compromised systems, block IP addresses, or deploy patches without delay. For more complex threats, security teams can initiate manual responses. - Remediation and Recovery
After containing the immediate threat, organizations work on remediation—restoring affected systems, closing vulnerabilities, and improving security defenses to prevent future incidents. - Continuous Improvement
TDR platforms regularly update their detection algorithms with the latest threat intelligence and adjust response mechanisms to combat new and evolving cyber threats. This ensures organizations stay protected against emerging attack vectors.
How Xygeni Supports Threat Detection and Response #
Xygeni offers integrated Threat Detection and Response capabilities to provide comprehensive protection for modern software development and supply chains. Here’s how Xygeni enhances TDR:
- Anomaly Detection and Real-Time Monitoring
Xygeni’s platform continuously monitors CI/CD pipelines, detecting anomalies or unauthorized activities in real time. This ensures that your software development processes remain secure and free from cyber threats. - Secrets Security
Xygeni’s Secrets Security solution automatically detects and blocks the exposure of sensitive data like API keys, passwords, and tokens. By securing your software development environments, Xygeni helps prevent common attack vectors related to secret leaks. - Automated Incident Response
Xygeni automates threat remediation by isolating compromised systems or applying patches immediately upon detecting a threat. This stops threats from spreading across your infrastructure. - Continuous Improvement
By leveraging global threat intelligence feeds, Xygeni continuously updates its threat detection capabilities, ensuring that your organization stays ahead of evolving cyber threats.
Why is Threat Detection and Response Important? #
In a world where cyber threats are becoming more advanced and persistent, having a Threat Detection and Response system is crucial for every organization. The key benefits of TDR include:
- Early Detection: Identifying threats early helps prevent major security incidents.
- Proactive Response: Automating response actions reduces the time window in which cyber threats can cause damage.
- Reduced Impact: Fast detection and response help minimize the potential damage to your organization’s digital assets and reputation.
Book a demo today to discover how Xygeni can strengthen your organization’s Threat Detection and Response capabilities and keep your digital assets secure from evolving cyber threats. #

Frequently Asked Questions (FAQs) #
What is the difference between detection and response in TDR? #
Detection refers to the identification of suspicious activities or threats, while response involves taking action to contain or neutralize the threat, such as isolating systems or applying security patches.
How does TDR integrate with existing cybersecurity measures? #
TDR solutions often complement existing SIEM (Security Information and Event Management) platforms, providing a more proactive layer of defense by detecting and responding to threats in real-time.
What kind of threats does TDR handle? #
TDR can address a wide range of cyber threats, including malware, ransomware, phishing, zero-day exploits, and advanced persistent threats (APTs).
How does Xygeni’s TDR system work? #
Xygeni integrates TDR with real-time anomaly detection, secrets management, and automated response capabilities to provide end-to-end protection for software development environments and supply chains.ç

