Vulnerability scan is an essential part of a solid security strategy. As open-source software (OSS) makes up the majority of codebases—often as much as 90%—identifying and addressing vulnerabilities early is crucial to safeguarding your software supply chain. Xygeni enhances traditional vulnerability scanning by incorporating real-time malware detection and intelligent prioritization funnels, ensuring your team not only detects but also prioritizes and remediates the most critical security risks.
What is a Vulnerability Scan?
A vulnerability scan is a process that identifies weaknesses in your software, systems, and networks. It examines your codebases, configurations, and open-source dependencies to uncover security threats before attackers can exploit them. As OSS continues to dominate codebases, vulnerability scanning is critical to maintaining secure environments and protecting against breaches before they happen.
Why Xygeni’s Vulnerability Scanning Protects You Best
Xygeni Vulnerability Scan offers more than just detection. Our tools provide real-time threat blocking, smart risk prioritization, and seamless CI/CD pipeline integration, ensuring that security fits smoothly into your workflows and development processes. Here’s how Xygeni’s cutting-edge features enhance your vulnerability management:
Real-Time Malware Detection: Blocking Threats Before They Reach You
Minimize risks and protect your applications from malicious packages with Xygeni’s Early Malware Detection. Our comprehensive solution offers real-time monitoring of your dependencies, ensuring that threats are detected and mitigated before they can impact your software. By constantly scanning public repositories like NPM, Maven, and PyPI, Xygeni blocks malicious packages as soon as they are published, preventing them from infiltrating your systems.
Managing open-source components is crucial in today’s software development landscape due to the growing risks of vulnerabilities and malicious code. Xygeni’s Open Source Security solution dramatically reduces the risk of malware by scanning and blocking harmful packages at the point of publication. Our continuous monitoring covers multiple public registries, ensuring that all dependencies are thoroughly scrutinized for safety and integrity.
Xygeni’s powerful capabilities help your team maintain secure and reliable software projects by prioritizing critical issues and streamlining remediation processes, allowing you to focus on what matters most.
CVE Scoring and EPSS Integration: Prioritizing the Most Exploitable Vulnerabilities
Xygeni enhances CVE scoring with the Exploit Prediction Scoring System (EPSS) for a more comprehensive assessment of risk. While CVE scores assess a vulnerability’s severity, EPSS predicts its exploitation likelihood. This allows your team to prioritize based on both severity and real-world exploitability.
For example, CVE-2021-44228 (Log4j), which has a high CVE score, also carries a high probability of exploitation based on EPSS data. This combination helps you prioritize vulnerabilities that pose the greatest risk, ensuring your team focuses on the most dangerous threats first.
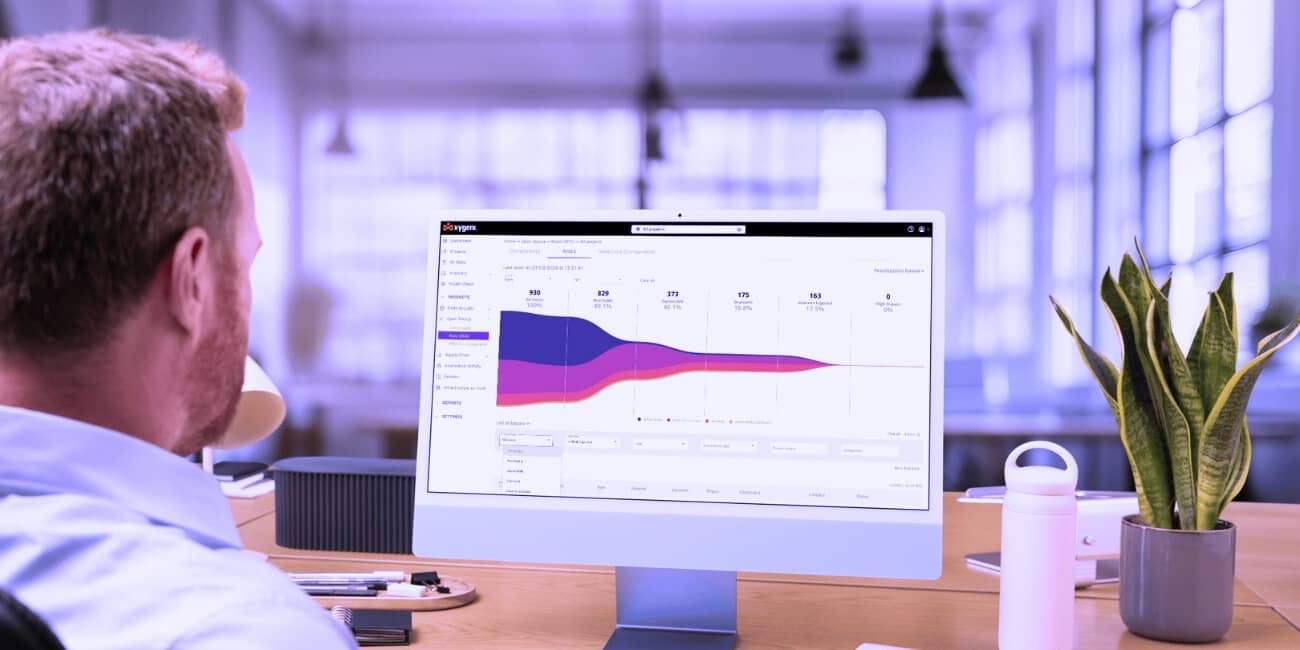
Prioritization Funnels: Focus on Fixing What Matters Most
Xygeni’s Prioritization Funnels simplify how you tackle a large number of security issues. These funnels let you filter and focus on the most critical vulnerabilities by applying custom prioritization criteria. Instead of wading through thousands of issues, Xygeni helps your team zero in on the ones that pose the greatest threat, such as reachable vulnerabilities or those that are actively deployed.
You can also leverage out-of-the-box funnels like General Prioritization, CI/CD Prioritization, and IaC Prioritization. These funnels streamline decision-making, saving valuable time and resources.
CI/CD Pipeline Integration: Security Embedded at Every Stage
Security should never be an afterthought. Xygeni integrates directly with popular CI/CD platforms like Jenkins, GitHub Actions, and CircleCI, ensuring that vulnerability scans are automatically triggered during every build and deployment phase. This integration enables early detection and remediation, preventing vulnerabilities from slipping into production.
Pull Request Scanning: Catching Issues Before They Merge
Xygeni’s Pull Request Scanning scans for vulnerabilities in real time when new pull requests are created. It detects issues like SQL Injection or Cross-Site Scripting (XSS) before they merge into production. By catching these flaws early, your team resolves security risks without delaying release cycles or accumulating technical debt.
Reachability Analysis: Eliminate Noise and Prioritize Real Threats
Xygeni’s Reachability Analysis goes beyond standard detection by identifying vulnerabilities invoked during runtime. Instead of overwhelming your team with countless issues, Xygeni focuses on vulnerabilities that are actively exploitable in your environment.
By filtering out those that exist but are inaccessible during execution, Xygeni cuts through noise. This ensures your team concentrates on the most pressing security threats. This approach reduces false positives and minimizes alert fatigue.
Your team focuses on real risks, not low-priority issues. Xygeni ensures that your time and resources address critical vulnerabilities, preventing hidden threats from slipping through.
Automated Remediation: Fix Vulnerabilities Effortlessly
Security should support development, not hinder it. Xygeni’s automated remediation features allow your team to patch vulnerabilities directly through your CI/CD pipelines. As soon as Xygeni detects a vulnerability, it can automatically apply a patch, keeping your development moving without manual intervention. This automation reduces downtime and boosts productivity.
Open Source License Management: Ensuring Compliance with Confidence
In addition to scanning for vulnerabilities, Xygeni helps manage open-source licenses by ensuring your code remains compliant with OWASP best practices and other industry standards. This feature mitigates legal risks by identifying and addressing open-source license violations, keeping your software compliant and secure.
Why Choose Xygeni?
- Real-Time Malware Detection: Instantly detect and block malware before it infiltrates your software.
- CVE Scoring and EPSS Integration: Prioritize vulnerabilities based on both severity and exploitability, ensuring critical issues are addressed first.
- Customizable Prioritization Funnels: Filter out low-priority issues and focus on what matters most.
- Automated Remediation: Apply security patches automatically within your CI/CD pipeline, minimizing disruptions.
- CI/CD Integration: Seamlessly integrate vulnerability scans into every step of your development process.
- Stay Compliant: Ensure compliance with industry standards and reduce the risk of open-source license violations.
Protect Your Software with Xygeni’s Vulnerability Scanning and Real-Time Malware Detection Tools
Don’t wait for a breach to happen. With Xygeni’s vulnerability scanning and real-time malware detection tools, you can proactively detect and block threats before they strike. Focus on fixing the most critical risks and streamline your vulnerability management process with customizable prioritization funnels and automated remediation. Stay ahead of emerging threats and ensure your software remains secure and compliant.
Ready to protect your software? Request a demo today and learn how Xygeni Vulnerability Scan can transform your vulnerability management strategy.