In the software development environment, relying on basic SCA scanning tools leaves critical gaps in security. Most traditional SCA scan solutions simply check open-source components for known vulnerabilities. But what about emerging threats, malware infiltration, or risky dependencies that power modern applications? These tools often miss the real risks that can cause the most damage.
At Xygeni, we go further. We don’t just scan for vulnerabilities—we provide real-time protection and streamlined auto-remediation to fix issues fast and effectively. We cut through the noise and help your team focus on what matters, while our system takes care of the rest. Xygeni deeply integrates into your CI/CD pipelines, embedding security directly into your development process. You’ll not only know what’s wrong, but you’ll have the tools to fix it—quickly—keeping your software supply chain safe and secure.
What is SCA Scanning?
Software Composition Analysis (SCA scanning) is the process of finding and managing open-source components in a codebase to detect known vulnerabilities and licensing issues. SCA scan tools rely on databases like the National Vulnerability Database (NVD) to match components with reported vulnerabilities. While this traditional approach can be effective at highlighting existing risks, it has its limitations. To understand how SCA compares to other security testing methods, like Static Application Security Testing, check out our breakdown of the difference between SCA and SAST.
Xygeni fills those gaps by going beyond traditional SCA scanning tools. fills those gaps by going beyond the basics of SCA tools. We offer advanced capabilities like reachability analysis and real-time malware detection, so you can focus on vulnerabilities that truly matter while staying ahead of zero-day threats.
Streamlined Auto-Remediation is at the core of our platform. Instead of just highlighting issues, Xygeni SCA scanning actively resolves them—automatically and efficiently. When threats pop up, Xygeni kicks off fast, targeted fixes, so you don’t have to deal with a flood of security alerts. And because it integrates directly with your CI/CD pipelines, security doesn’t slow down your development.
We prioritize vulnerabilities based on contextual risk, and developers can apply fixes easily with minimal effort and interaction.
With Xygeni’s auto-remediation, your team can focus on building great software while we handle the security, making sure your software supply chain stays secure and agile.
Why SCA Scanning Needs to Evolve
Traditional SCA solutions often scan open-source components for vulnerabilities using extensive databases. However, they flood security teams with vulnerabilities that might never pose a real threat. Without the ability to prioritize exploitable risks, teams end up wasting valuable time and resources chasing non-issues.
Xygeni takes a smarter approach. Our platform leverages reachability analysis and exploitability based on EPSS (Exploit Prediction Scoring System) to focus on vulnerabilities that are not just present but are actually exploitable. By mixing real-world exploitability data with reachability insights, we help your team zero in on threats that truly matter. This ensures your security efforts are targeted, efficient, and focused on high-priority risks, improving productivity and cutting down on wasted effort.
How Xygeni Goes Beyond Basic SCA Scan
In the software development environment, relying on basic SCA scanning tools leaves critical gaps in security. Most traditional SCA scan solutions simply check open-source components for known vulnerabilities. But what about emerging threats, malware infiltration, or risky dependencies that power modern applications? These tools often miss the real risks that can cause the most damage.
At Xygeni, we go further. We don’t just scan for vulnerabilities—we provide real-time protection and streamlined auto-remediation to fix issues fast and effectively. We cut through the noise and help your team focus on what matters, while our system takes care of the rest. Xygeni deeply integrates into your CI/CD pipelines, embedding security directly into your development process. You’ll not only know what’s wrong, but you’ll have the tools to fix it—quickly—keeping your software supply chain safe and secure.
Xygeni doesn’t just scan for vulnerabilities. It offers a full suite of tools that ensure real-time protection, continuous monitoring, and advanced threat detection across your entire supply chain.
1. Real-Time Malware Detection SCA Scan
Traditional SCA Beyond SCA Scanning tools only detect known vulnerabilities, leaving you exposed to new threats. Xygeni tackles this head-on by targeting zero-day malware in open-source libraries. Our Early Warning System identifies malicious code as soon as it’s published, giving you the upper hand against emerging threats.
Key Benefits:
- Automated Blocking: Xygeni blocks suspicious packages from entering your system, keeping your software safe.
- Continuous Scanning: We scan major public repositories like NPM, Maven, and PyPI to ensure harmful code doesn’t get in.
- Instant Alerts: You receive real-time alerts when threats appear, letting your team to act quickly and minimize damage.
Xygeni’s proactive malware detection keeps your software safe from threats that basic SCA tools miss.
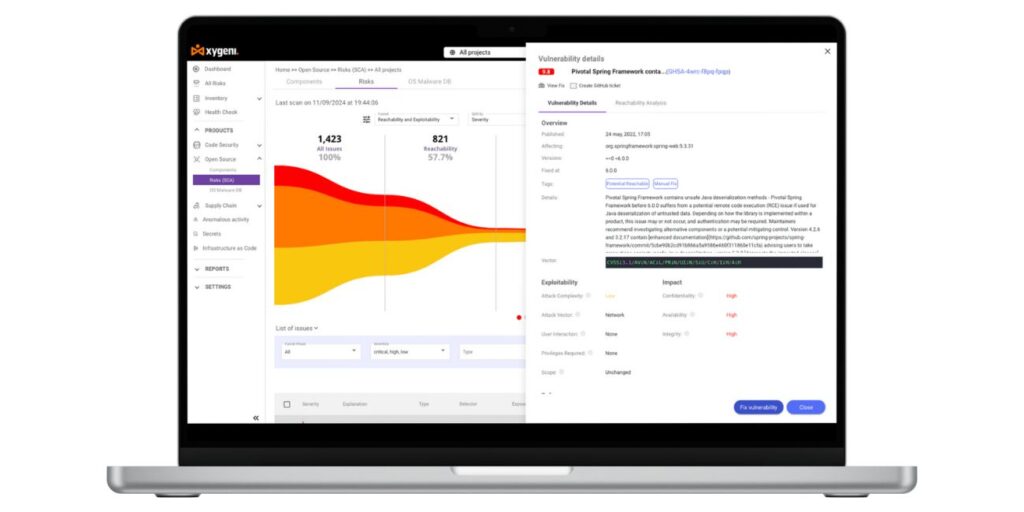
2. Reachability and Exploitability: Fix What Truly Matters
Most SCA tools bombard you with alerts, many of which cannot be exploited. Xygeni helps you cut through the noise by combining reachability analysis and exploitability metrics, focusing only on vulnerabilities that pose real threats.
How It Works:
- Reachability Analysis: Xygeni identifies whether vulnerable code is invoked in your application’s execution path. This ensures that only vulnerabilities that can be exploited are prioritized for remediation.
- Exploit Prediction: By integrating the Exploit Prediction Scoring System (EPSS), Xygeni predicts how likely a vulnerability will be used in real-world attacks. This advanced scoring helps your team focus resources on vulnerabilities that pose the greatest risk.
This combined approach helps your team focus on vulnerabilities that truly matter, reducing false positives and alert fatigue.
3. Context-Aware Prioritization: Tailoring Security to Your Environment
Fixing vulnerabilities one by one can be a waste of time. Xygeni’s context-aware prioritization helps organizations assess vulnerabilities within the broader context of their software environment and business impact.
Key Features:
- User-Defined Attributes: Customize prioritization by setting attributes such as business impact, whether the application is legacy, internet-exposed, or in active development. This allows you to prioritize vulnerabilities based on the specific needs and priorities of your organization.
- Dynamic Prioritization Funnels: Xygeni’s funnels apply multiple criteria to filter issues based on factors like exploitability, reachability, and more. These stages ensure your team only focuses on issues that pose a real threat, optimizing remediation efforts.
These intelligent prioritization features empower security teams to address the highest risks first, improving overall security posture while reducing unnecessary workload.
4. Auto-Remediation: Swift Fixes for Open Source Vulnerabilities
Xygeni SCA Scanning simplifies the remediation of open-source vulnerabilities with auto-remediation capabilities, ensuring critical issues are addressed before they pose a risk. Xygeni helps developers quickly fix security issues with little trouble by adding direct solutions to the scan results.
How It Works:
- Automatic Fixes: Xygeni flags vulnerabilities with available fixes and suggests direct updates to the manifest files.
- Automatic Pull Requests: Once an issue is flagged, Xygeni automatically opens a pull request, enabling teams to quickly merge fixes into their codebase via platforms like GitHub. This streamlines the remediation process, letting teams to address vulnerabilities without manual intervention.
- Continuous Monitoring: After remediation, Xygeni continues to scan for any new vulnerabilities to ensure persistent protection.
These features enable teams to patch vulnerabilities quickly and accurately, mitigating the risk of exploitation.
5. Seamless CI/CD Integration
Teams can patch vulnerabilities quickly and accurately with these features, mitigating the risk of exploitation. Xygeni SCA scanning integrates directly into your CI/CD pipelines, making sure that no vulnerable code ever makes it into production.
Key CI/CD Features:
- Automated Security Gates: Add security checks at every stage of the CI/CD process to stop risky code from deploying.
- Branch Protection: Only secure, reviewed code gets merged into production, ensuring high standards of security throughout.
- Build Attestations: Xygeni supports Supply Chain Levels for Software Artifacts (SLSA) attestations and in-toto attestation, giving you a clear chain of trust for each build. This ensures full transparency and integrity in your software’s journey from development to deployment.
With Xygeni, security is baked into your development workflow.
6. Compliance and SBOM: Full Transparency
With regulations like DORA and NIS2 becoming stricter, compliance is more important than ever. Xygeni helps you stay compliant with real-time SBOM generation and detailed vulnerability reports.
Compliance Benefits:
- One-Click SBOM Generation: Instantly generate SBOMs in formats like SPDX or CycloneDX to meet regulatory requirements.
- Real-Time Vulnerability Reports: Stay compliant with up-to-date reports based on standards like DORA.
- Vulnerability Disclosure Reports (VDR): Ensure transparency across your software supply chain by documenting every vulnerability and the steps taken to address it.
Xygeni ensures that your software meets today’s strictest security regulations.
Xygeni – Your Partner in Software Security
Basic SCA tools are no longer enough to secure modern software environments. With Xygeni, you get real-time malware detection, reachability analysis, contextual risk prioritization, and deep integration with your CI/CD processes. These features empower you to secure your software supply chain against changing threats and maintain compliance with the latest regulations. Take control of your software security and try our tool now!
Xygeni isn’t just another SCA tool, it’s a proactive security partner for modern development. With real-time malware detection, reachability analysis, and intelligent context-aware prioritization, Xygeni goes far beyond basic SCA scanning. Our platform secures your software supply chain from end to end, integrating seamlessly into CI/CD workflows to block emerging threats before they cause harm. Trust Xygeni to turn traditional SCA scan limitations into a strategic advantage, keeping your code safe, agile, and future-proof.
Contact us today for a demo and see how Xygeni can transform your approach to making sure the software supply chain.