Open source is always a good idea after all, it’s how we build, collaborate, and innovate, right? From frameworks to CI tools, open source powers the software we deliver every day. But when it comes to security, is open source always the best option? Take vulnerability scanning, for example. Using an open source vulnerability scanner software used in cybersecurity seems like the obvious choice. It’s free, flexible, and integrates easily into your pipeline. The appeal is clear but is it enough to truly secure your DevOps workflows, end to end?
Let’s break it down.
Static Code Analysis with Open Source Tools: Is It Enough?
Example: Bandit (OpenStack)
Bandit is a lightweight open source software vulnerability scanner focused on Python code. It helps detect common security issues like hardcoded passwords, insecure function calls, and risky imports. While it’s simple to use, several limitations should be noted:
- It supports only Python, which limits broader adoption.
- It performs line-by-line checks, not deep taint or data flow analysis.
- It lacks prioritization, filtering, or remediation guidance.
In short, while Bandit is useful as a starter tool, teams scaling their DevSecOps pipelines will quickly run into its constraints.
Dependency Scanning: Alerts Without Context
Example: OWASP Dependency-Check
Many development teams rely on this tool to scan their third-party libraries for known CVEs. However, this open source software vulnerability scanner introduces several key limitations:
- Reliance on delayed vulnerability feeds like NVD.
- No distinction between exploitable and unused code paths.
- Flat output that lacks prioritization or remediation help.
As a result, many teams using this vulnerability scanner end up overwhelmed by alerts that don’t reflect real risk.
Secrets Detection: Reactive Instead of Preventive
Example: Gitleaks
Gitleaks scans Git repos for hardcoded secrets. It’s widely adopted and fast, but still reactive:
- It only alerts after secrets are already committed.
- False positives make alert management hard.
- It doesn’t monitor runtime or pipeline secrets.
Despite being a trusted vulnerability scanner open source, it can’t provide the proactive coverage that modern DevOps environments demand.
SBOM Creation: Lists with No Strategy
Example: Syft (Anchore)
Security teams use tools like Syft to generate software bill of materials (SBOMs) and track third-party components. Regulated workflows often rely on these tools to meet compliance requirements. However, they still come with several key limitations.
For instance, SBOMs are static and do not reflect changes during deployment. In addition, they fail to indicate which components pose actual risk or how severe the exposure may be. Moreover, these tools are often disconnected from modern CI/CD processes, which makes them less effective in dynamic DevOps environments.
As a result, even a well-regarded open source software vulnerability scanner may fall short when it comes to helping teams prioritize threats, act quickly, or demonstrate continuous compliance.
Open Source Vulnerability Scanner Software Used in Cybersecurity: What It Covers and What It Misses
Across the industry, teams rely on these scanners to support CI/CD, shift-left strategies, and early vulnerability detection. A typical open source software vulnerability scannerused in cybersecurity handles tasks like:
- Analyzing source code for insecure patterns.
- Checking dependencies for known CVEs.
- Scanning for exposed secrets in version control.
- Generating SBOMs for licensing and inventory.
However, when used in isolation, these tools leave gaps. They often lack integration, real-time monitoring, prioritization, or alignment with business risk. In contrast, unified platforms offer richer, more actionable protection.
Why Xygeni Is the Smarter Alternative to Any Vulnerability Scanner Open Source
Instead of managing five separate tools, what if you could strengthen your security posture using a single, integrated platform?
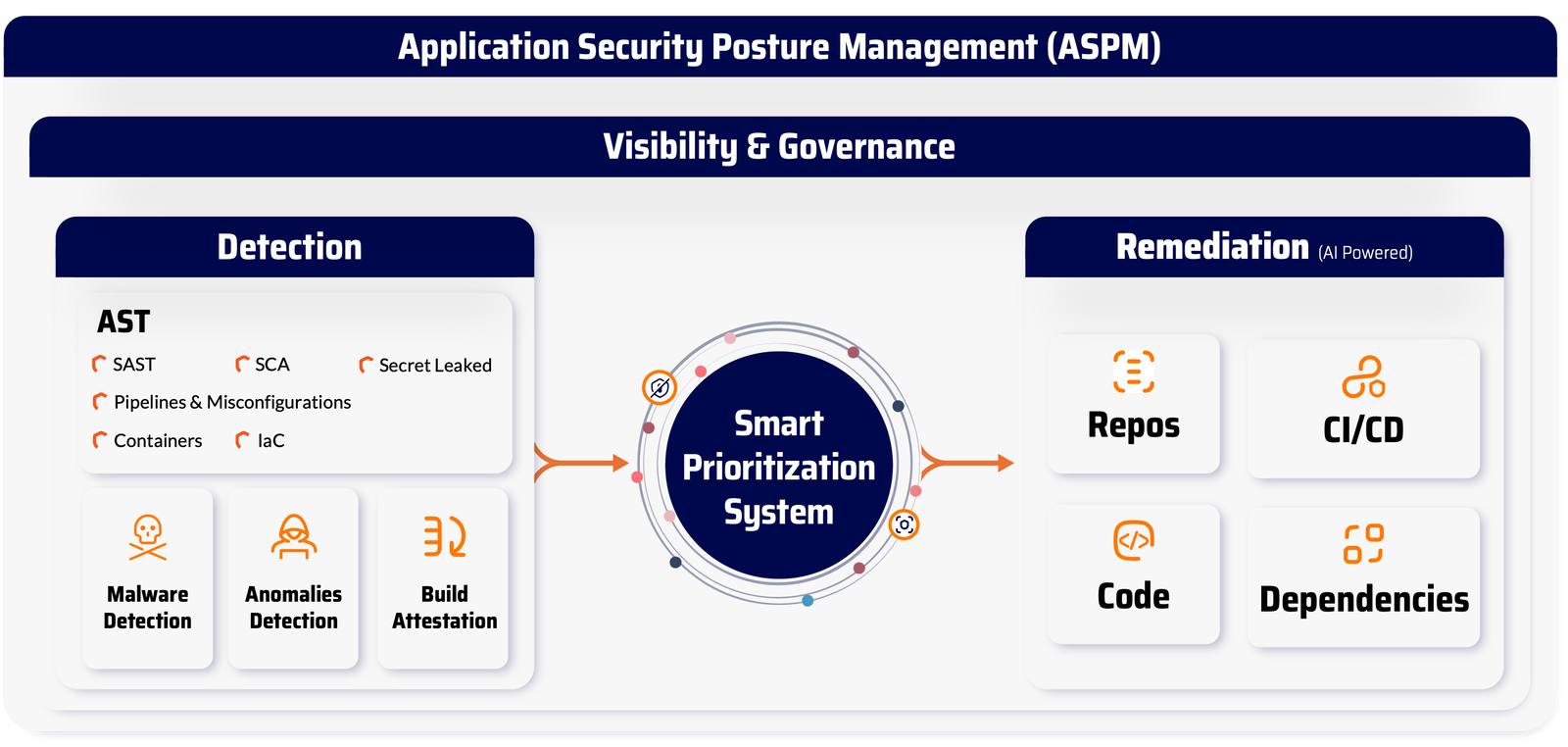
Xygeni replaces the fragmented patchwork of open source tools with a unified, developer-friendly solution. In contrast to juggling multiple scanners for code, dependencies, secrets, and SBOMs, Xygeni provides everything you need in one place.
For example, you get:
- SAST: Deep static code analysis with 0% false positives in critical vulnerabilities (OWASP Benchmark validated)
- SCA: Advanced dependency scanning with reachability analysis, EPSS scoring, and malware detection
- Secrets Detection: Pre-commit scanning with intelligent validation to prevent sensitive data leaks
- SBOM Management: Live, auto-updated SBOMs enriched with real-time risk exposure and compliance data
- CI/CD Integration: Continuous scanning of code, pull requests, and pipelines without disrupting developer flow
- Exploitability Metrics: Prioritize based on real-world exploitability instead of just severity ratings
- Automated Remediation: Fix issues faster using actionable guidance and smart issue routing
- License Management: Maintain compliance with open source licenses across your software supply chain
As a result, Xygeni delivers significantly more value than any typical vulnerability scanner open source, all while reducing the time and cost of managing fragmented tools.
Final Thoughts: Are Open Source Vulnerability Scanner Software Used in Cybersecurity Enough?
To summarize, an open source vulnerability scanner software used in cybersecurity offers important baseline protection. However, these tools often lack prioritization, integration, and full coverage of the modern software development lifecycle.
Consequently, if you need accurate, automated, and actionable security from code to deployment, Xygeni is the smarter option.
Book your free demo and discover how secure-by-design becomes achievable with Xygeni.