Mastering Software Supply Chain Visualization: Enhance Security & Boost Efficiency
Table of Contents
Delve into software supply chain visualization and mapping essentials in this comprehensive guide. Discover how these crucial strategies boost security and operational efficiency in software development. Learn about the latest tools and practices in Supply Chain Mapping, DevSecOps, and Open Source Software Management for a robust, streamlined software lifecycle.
Embarking on a Visualization Journey: The What and Why
Imagine you’re navigating a complex maze with countless paths, hidden doors, and unforeseen traps. This scenario isn’t just a puzzle enthusiast’s dream; it’s a day-to-day reality for software development teams managing intricate supply chains. In the world of software development, the maze is your software supply chain, and the stakes are incredibly high—ranging from security breaches to operational inefficiencies.
But what if you had a map and a map view of this labyrinth? Mapping and visualizing your software supply chain isn’t just about drawing lines and dots; it’s about unveiling the hidden connections, exposing potential risks, and discovering the most efficient pathways for your projects.
In the following paragraphs, we dive into the vital role of mapping and visualizing your software supply chain. With insights from industry leaders and real-world examples, learn how these practices enhance security and streamline efficiency, ensuring your software development journey is safe and successful. Let’s embark on a journey to transform how you see and manage your software supply chain, turning complexity into clarity and challenges into opportunities.
Demystifying the Maze: The Critical Role of Visualization
The National Institute of Standards and Technology (NIST) underscores a critical aspect of modern cybersecurity – a vivid, detailed map of your software supply chain. It’s not just a technical nicety; it’s a cornerstone of your defense strategy. The complexity and opacity of the Software Supply Chains (SSC) pose significant security challenges, particularly in inventory and discovery aspects.
Navigating the Fog: Unveiling the Challenges in Visibility
Envision navigating through a fog-laden landscape. This is what tackling Software Supply Chain Security (SSCS) feels like when visibility fades into the background, obscured by the ever-growing complexity of SDLC ecosystems. According to a survey by the Cloud Native Computing Foundation, most technologists report facing unprecedented IT complexity, which creates a substantial amount of data noise.
This complexity makes it challenging to track the myriad components involved in a software project, leading to difficulties in identifying configuration and permissions issues and potential security vulnerabilities. Organizations need a clear view of the entire software supply chain to secure their applications effectively.
Organizations face the following intricacies and hurdles when attempting to protect their CI/CD security:
- Difficulty in Accurate Inventory: Accurately inventorying all components in a software supply chain is akin to finding needles in a haystack. As reported by the Linux Foundation, the average software application’s supply chain is so complex that most organizations need a clearer understanding of the various elements that constitute their software ecosystems. This gap in knowledge presents a significant barrier to securing the supply chain effectively.
- Challenges in the Discovery of Threats: Discovering vulnerabilities within the software supply chain is herculean. With new threats emerging daily, keeping pace with potential security breaches requires vigilance and advanced technological capabilities. The ever-evolving nature of these threats means that traditional vulnerability detection methods often need to be improved.
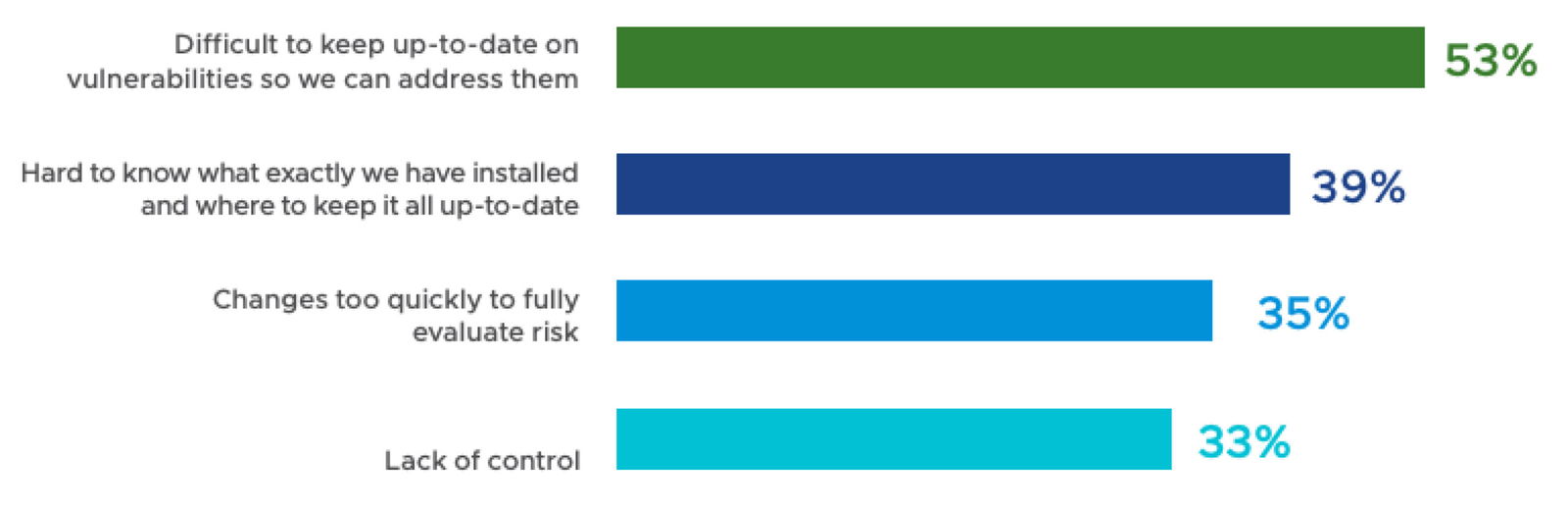
- Navigating Open Source and Third-Party Components: The extensive use of open-source and third-party components in modern software development introduces another layer of complexity. While these components accelerate development and offer vast functionalities, they also introduce unknown risks. The 2020 “Open Source Security and Risk Analysis” report highlights that 75% of codebases contain open-source vulnerabilities, underscoring the need for stringent security measures. Cataloging and continuously monitoring these dependencies for new risks is crucial and overwhelming.
Concerns About the Security Risks of Open Source Software Deployed
Illuminating the Dark Corners: Security through Visibility
Compounding the challenge of visibility is the inability of DevSecOps teams to prioritize actions. Latest reports highlight that many engineers feel overwhelmed by the sheer volume of data and the number of potential vulnerabilities in their systems. This overload often leads to a paralysis of action, where teams cannot distinguish between critical and less critical vulnerabilities that require immediate attention. The lack of prioritization not only hampers timely remediation efforts but also drains resources and hinders the overall responsiveness of IT teams.
These two challenges – lack of visibility and difficulty in prioritization – are interrelated and often feed into one another. Limited visibility across the technology stack makes it difficult to understand which elements of the software supply chain are at risk. At the same time, the inability to prioritize actions can result from and contribute to this lack of clarity.
Together, they form a significant barrier to adequate software supply chain security, underscoring the need for solutions to cut through the noise and provide clear, actionable insights.
Clearing the Path: Streamlining Operations with a Clear View
Step beyond the realm of security, and you’ll find that visualizing your supply chain does more than safeguard – it’s like turning on a light in a dark room, revealing the fastest, most efficient pathways through your operations. It gives teams a bird’s-eye view of the development ecosystem, enabling them to identify redundant assets and unmaintained elements. This clarity is particularly beneficial in large-scale projects where multiple units and components intertwine.
Strategic Insights: Tools and Techniques for Better Visibility
Imagine having x-ray vision for your software supply chain. It’s more than just seeing the pieces; it’s about perceiving the hidden, intricate connections, transforming them into a mosaic of understanding and action. Some specific strategies and methodologies, along with the role of automated tools, that can significantly improve visibility into software supply chains are:
Implementing Comprehensive Asset Mapping Tools
To start, consider implementing tools that offer a detailed view of every component within the supply chain. It includes mapping out third-party dependencies, open-source libraries, and every CI/CD pipeline step.
These tools can seamlessly integrate into Continuous Integration/Continuous Deployment (CI/CD) pipelines, enabling continuous tracking and management of software components as they move through various development and deployment stages.
As a result, operations become more streamlined, and efficiency is enhanced as teams can ensure that only secure and up-to-date components are part of the final product.
Role of Automated Inventory Management
In traditional setups, keeping an up-to-date inventory of all software components, including third-party dependencies and open-source libraries, is a time-consuming and error-prone task.
Automated inventory management systems are pivotal in this quest for visibility. They are designed to meticulously catalog and track each component within the software supply chain. Imagine a system that automatically updates and records every new dependency or change in the software assets – this is what automated inventory management systems offer.
Automation significantly reduces the manual effort required for tracking and updating the inventory, ensuring that no component goes unnoticed. This process is crucial in identifying potential vulnerabilities that might otherwise be overlooked in a manual audit.
Visualization and Dashboard Tools for Clarity and Communication
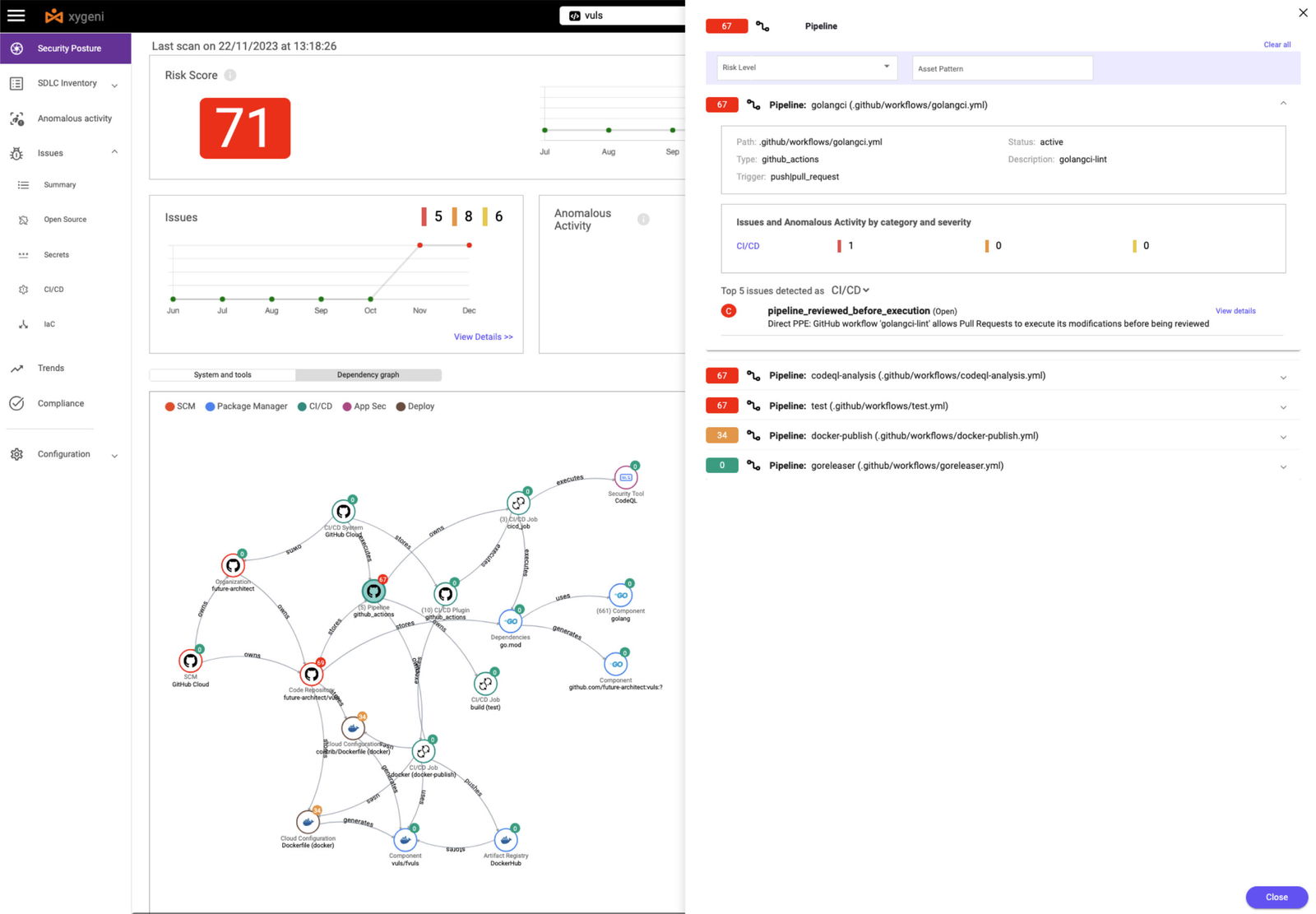
Visualization is not just about seeing; it’s about understanding. Tools like Xygeni provide an interactive visualization of the entire supply chain, enabling organizations to see the complete picture of their software development process.
SDLC inventory dashboards transform the complex web of the software supply chain into a clear, graphical representation that enhances understanding and fosters communication among team members, enabling a collaborative approach to managing the software supply chain.
The centralized interface for monitoring each component’s health and security status, streamles operations by quickly identifying redundancy, and obsolete and unmaintained elements that may hinder efficiency or pose security risks.
Prioritization Techniques in DevSecOps
The ability to effectively prioritize actions, especially in addressing critical vulnerabilities, is a skill that separates proactive teams from reactive ones. Prioritization in this context is not just about ticking off tasks on a list; it’s about strategically identifying which actions will significantly impact the security and efficiency of the software development process. Some techniques and frameworks that can aid DevSecOps teams are:
Risk-Based Vulnerability Prioritization
A fundamental approach in DevSecOps is risk-based vulnerability prioritization. This approach involves assessing each vulnerability based on its potential impact and likelihood of exploitation. Tools like those offered by Xygeni can automate this assessment, using advanced algorithms to analyze vulnerabilities in the context of the organization’s specific environment.
This method ensures that vulnerabilities posing the most significant risk to the application and the organization are addressed first, allocating resources more effectively and reducing the window of opportunity for exploitation.
Implementing the CVSS and other Frameworks
The Common Vulnerability Scoring System (CVSS) offers a standardized framework for rating the severity of vulnerabilities. By adopting this framework, DevSecOps teams gain a common language and understanding of the severity of different threats and vulnerabilities. Considering additional frameworks, such as the Exploit Prediction Scoring System (EPSS), can significantly enhance this approach. EPSS predicts the likelihood of exploiting a vulnerability, providing a forward-looking dimension to vulnerability management.
Xygeni’s integration with CVSS, augmented by EPSS insights, facilitates a more dynamic and predictive approach to vulnerability prioritization. This combination enables an objective assessment that considers vulnerabilities’ severity and exploitability, ensuring that prioritization is grounded in current and future risk potential.
Adopting a Shift-Left and Other Best Practices Approach
A ‘shift-left’ approach in software development emphasizes integrating security early in the SDLC. This approach ensures that security tests and checks are part of the development process. By prioritizing security from the beginning, teams can prevent many vulnerabilities from ever making it into the final product, significantly reducing the load on the later stages of vulnerability management.
A shift-left approach naturally leads to a set of best practices that not only complement the proactive nature of the shift-left methodology but also reinforce the overall security posture throughout the entire software development life cycle:
- Collaborative Decision-Making: Encouraging collaboration between development, operations, and security teams to ensure a holistic view of vulnerabilities and their impact.
- Continuous Learning and Adaptation: Staying updated with the latest security trends and adapting prioritization strategies accordingly.
The Value of Enhanced Observability in Software Supply Chain Management
Software Supply Chain inventory and observability is not a luxury but a necessity in today’s software development world. It empowers organizations to protect themselves against sophisticated cyber threats, streamline operations, and enhance collaboration across various departments. Such a comprehensive observability framework brings to organizations value from several perspectives:
Enhanced Security Posture from Inception to Execution
First and foremost, full-stack observability with Xygeni fundamentally strengthens application security throughout the software lifecycle. It analyzes security signals across all software development and deployment phases, significantly improving vulnerability management and enforcement of security controls. This proactive approach enables organizations to identify and rectify security coverage gaps, automate SDLC security guardrails, and protect against emerging software supply chain threats, thereby markedly reducing application risk.
Achieving Rapid Risk Reduction and Improved Departmental Synergy
The improved visibility and security coverage across applications, pipelines, and teams that tools such as Xygeni offer lead to rapid risk reduction. Automated security guardrails minimize the window of exposure. Furthermore, enhanced graphical representation and holistic views foster reduced friction between departments. Better communication and understanding across development, operations, and security teams facilitate a more collaborative and cohesive working environment.
Operational Optimization and Cost Efficiency
Moreover, adopting full-stack observability optimizes business operations and drives cost efficiencies. Automation provides organizations with a substantial reduction in time and resources spent on discovering and prioritizing tasks, with reports indicating more than a 65% decrease in time spent on these tasks and security teams being 40% more productive. These efficiencies reduce operational costs and free up valuable resources for other strategic initiatives.
Looking Ahead
Integrating AI and Machine Learning in software supply chain management tools will likely become more prevalent as we look to the future. These technologies promise even greater insights, predictive analytics, and automation capabilities, further enhancing the ability to manage complex software ecosystems.
The Role of Xygeni
Platforms like Xygeni are at the forefront of this evolution, offering tools and solutions that address current challenges and adapt to future trends. Their role in transforming how organizations approach software supply chain management is undeniable – from enhancing security and compliance to boosting operational efficiency and agility.
Engage with Your Software Supply Chain Like Never Before
Are you ready to transform the way you manage your software supply chain? It’s time to move beyond the challenges of visibility and complexity. Embrace the power of mapping and visualization tools to secure your software ecosystem, streamline your processes, and stay ahead in a rapidly evolving digital world.
🔍 Discover and Implement: Explore the tools and strategies discussed in this guide. Which ones resonate with your current needs? Start small if you need to, but start now. Every step towards better visualization is a step towards enhanced security and efficiency.
💡 Share Your Insights: Have you had experiences with software supply chain visualization? What worked and what didn’t? Your stories can enlighten others in the community. Comment below or contact us; let’s start a conversation that matters.
🚀 Stay Ahead: The world of software development is constantly changing. Don’t get left behind. Subscribe to our newsletter for the latest insights, trends, and software supply chain management updates. Stay informed, stay secure, and stay efficient.
Your journey to a clearer, more secure, and more efficient software development process begins today. Take the first step. Let’s chart a course to success together.
Watch our Video Demo