The Exploit Prediction Scoring System (EPSS) is transforming how modern security teams handle threats. In the growing discussion about cvss vs epss, the shift is clear. While CVSS highlights severity, EPSS brings attention to real-world exploitability. This difference matters—because instead of reacting to every high-severity issue, teams can focus on what attackers are actually using. By using EPSS scoring, organizations improve how they manage vulnerabilities and fix the ones that pose real risks.
Every year, more than 20,000 new CVEs each year. Understandably, keeping up with all of them is tough. Many teams end up burned out, spending hours reviewing issues that may never lead to an attack. This results in wasted time, slow responses, and a growing list of tasks that never seem to get done.
That’s where epss vs cvss makes a real impact. EPSS shifts the focus from what might be risky to what is likely to be targeted soon. As a result, teams can act faster, reduce unnecessary work, and spend time fixing what truly matters.
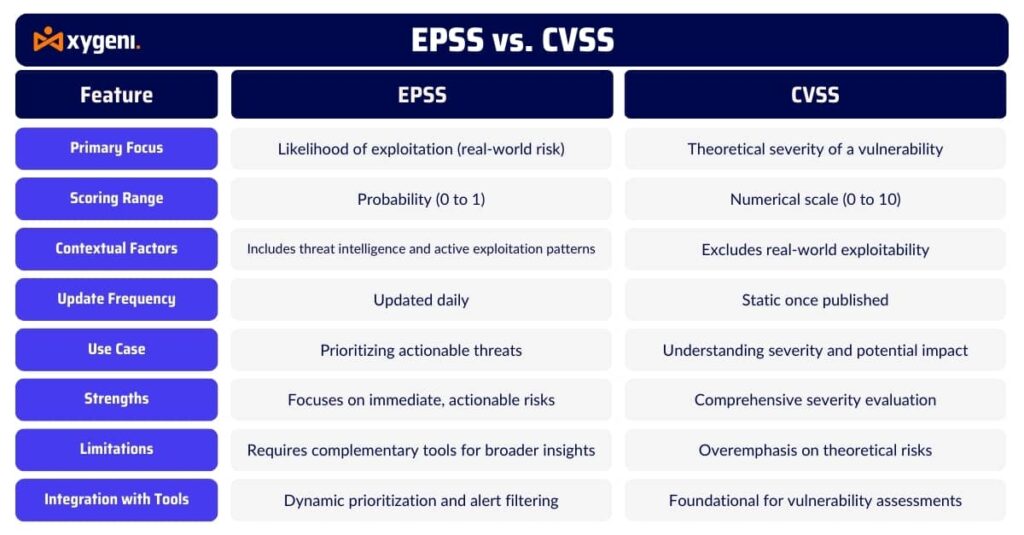
EPSS vs CVSS: Key Differences
When comparing cvss vs epss, the distinction lies in what each score tells you:
CVSS focuses on the potential severity of a vulnerability—how damaging it could be.
EPSS predicts the likelihood of exploitation in the real world—how likely it will be targeted.
While CVSS considers exploit complexity, user interaction, and impact, it does not factor in whether attackers are actively using the vulnerability. EPSS fills this gap by factoring in threat telemetry, exploit code availability, and attack patterns.
According to EPSS research, fewer than 2% of known vulnerabilities have a high EPSS score. In contrast, many critical CVSS issues remain no touched by cyber criminals. This highlights how EPSS score vulnerabilities help filter out noise, allowing teams to focus on credible, current threats.
Can EPSS and CVSS Work Together?
Absolutely—and they should.
EPSS and CVSS complement each other in a balanced vulnerability management strategy:
Use CVSS to assess how bad a vulnerability could be.
Use EPSS to assess how likely it is to be exploited.
This dual-layered approach supports smarter triage. For example:
A vulnerability with high CVSS + high EPSS → Fix it immediately.
High CVSS + low EPSS → Monitor closely, but deprioritize.
Low CVSS + high EPSS → Investigate; attackers might be chaining it with other flaws.
Accordingly, teams that compare epss vs cvss side-by-side gain a clearer view of what to remediate—and when.
Real-World Prioritization with EPSS
To illustrate, imagine your system flags two CVEs:
CVE-2024-99999
CVSS: 9.8 (Critical)
EPSS: 0.03 (Low exploitability)CVE-2024-12345
CVSS: 6.1 (Moderate)
EPSS: 0.86 (High likelihood of exploitation)
Which should you fix first? Many traditional workflows would prioritize the critical CVSS vulnerability. However, EPSS flips that script—you act on what’s actually being exploited, not just what could be dangerous.
This shift allows teams to reduce false positives, save time, and improve remediation speed.
Why EPSS Score Vulnerability Management Is a Game Changer
EPSS offers more than smarter patching—it enables security at scale:
Dynamic Scoring: EPSS updates daily, reflecting the latest exploit intelligence.
Scalability: It works across thousands of vulnerabilities, helping teams triage faster.
Objectivity: Built on public data and open models, EPSS is verifiable and transparent.
Policy Impact: As noted by FIRST.org, EPSS is already influencing national-level remediation policies (e.g. DHS BOD 19-02).
Moreover, EPSS score vulnerability management helps defenders focus their effort where it counts most—toward threats that actually pose danger.
EPSS vs CVSS Is Not Either-Or—It’s Better Together
At Xygeni, we believe cvss vs epss isn’t a battle—it’s a partnership. Both scoring systems serve different, yet equally valuable, roles in vulnerability management. That’s why Xygeni uses EPSS and CVSS together to build a complete, context-aware prioritization model that’s practical, fast, and effective.
For every vulnerability, Xygeni shows:
CVSS severity to understand potential impact.
EPSS score to evaluate the likelihood of exploitation.
Reachability analysis to confirm if the vulnerable code actually runs.
Contextual data like asset sensitivity and business relevance.
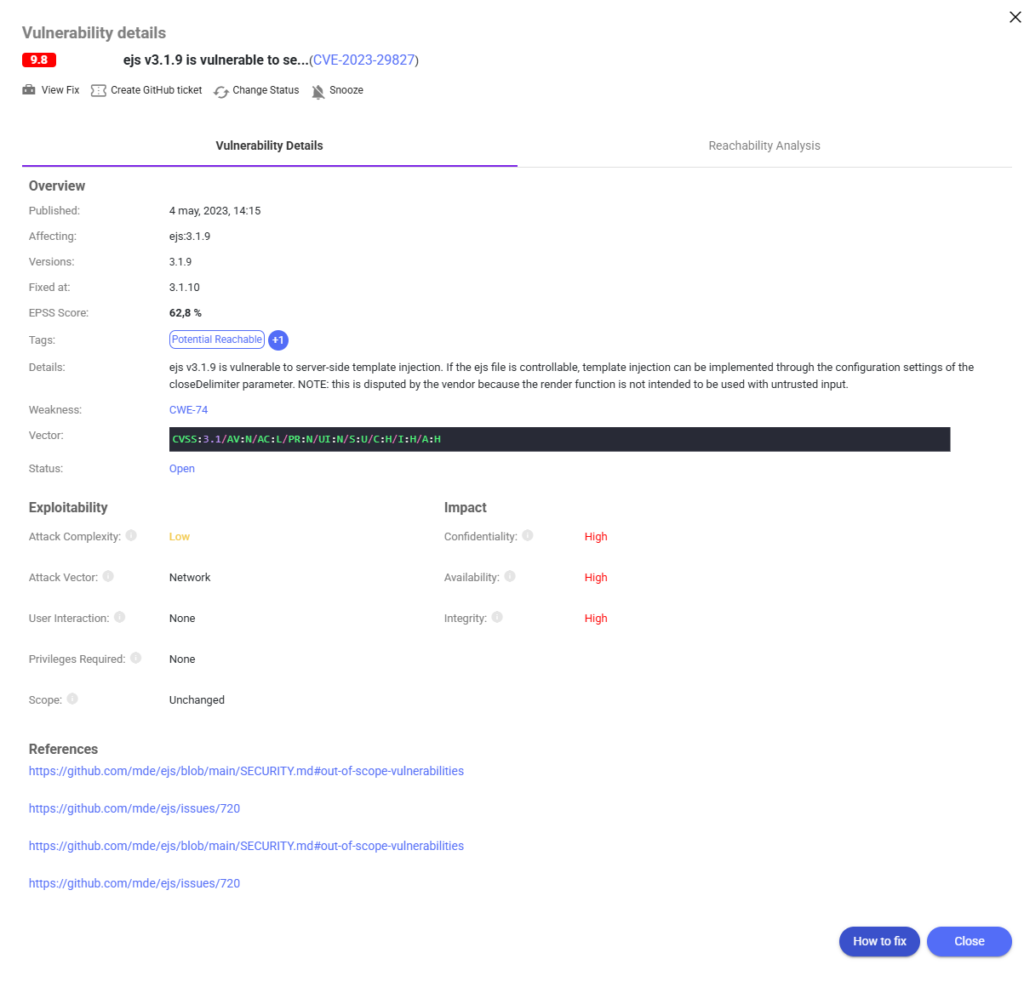
Let’s take CVE-2023-29827 as an example. This is a server-side template injection issue affecting ejs v3.1.9. On paper, it has a CVSS score of 9.8, indicating critical severity. But with an EPSS score of 62.8%, it also has a high probability of being exploited soon.
Xygeni displays all this data in one place—severity, exploitability, reachability, CWE weakness, and version status—so teams can instantly see why it matters and what to do next.
Instead of reacting to every CVSS 9.8 vulnerability, Xygeni’s platform shows whether:
It’s reachable in your codebase
It has high exploitability in the wild
It affects business-critical assets
This layered visibility helps reduce alert fatigue, minimize wasted effort, and direct remediation to the risks that truly matter.
When EPSS scoring is combined with CVSS severity and runtime context, prioritization becomes proactive—not reactive. Xygeni turns noise into insight, guiding security decisions with the clarity DevSecOps teams need to move fast and stay safe.